



CYFIRMA Research and Advisory Team would like to highlight ransomware trends and insights gathered while monitoring various forums. This includes multiple – industries, geography, and technology – that could be relevant to your organization.
Type: Ransomware
Target Technologies: MS Windows
Introduction
CYFIRMA Research and Advisory Team has found LucKY_Gh0$t Ransomware while monitoring various underground forums as part of our Threat Discovery Process.
LucKY_Gh0$t Ransomware
Researchers have recently identified a new variant of the ransomware named LucKY_Gh0$t.
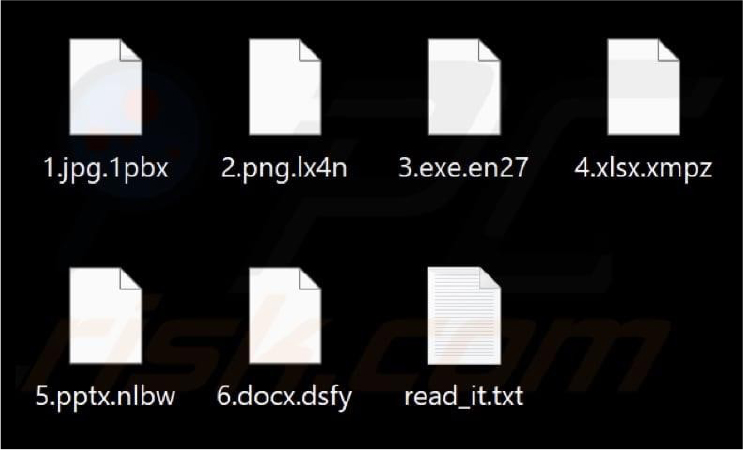
This ransomware variant is derived from the Chaos ransomware family. Upon infecting a system, it encrypts and renames files, appending a random four-character extension to them. Additionally, it alters the desktop wallpaper and delivers a ransom note in a file named “read_it.txt.”
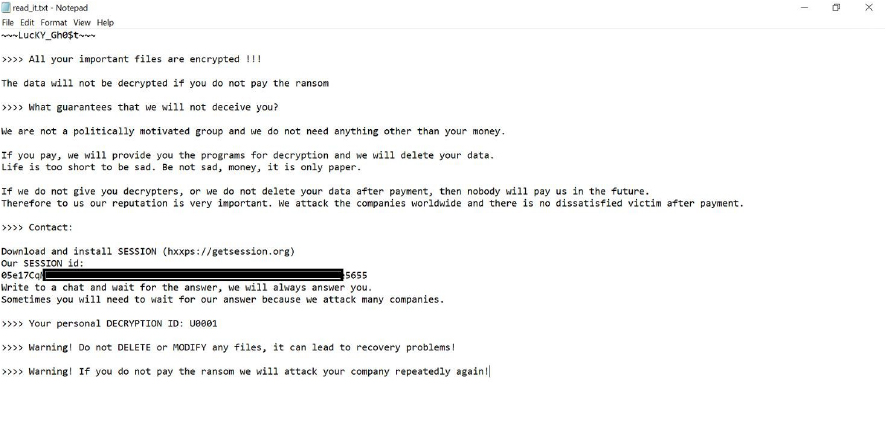
LucKY_Gh0$t’s ransom note informs victims that their files have been encrypted and demands payment for decryption. It assures that decryption programs will be provided upon payment but warns that failure to comply will lead to repeated attacks on the victim’s organization.
The note provides detailed instructions for contacting the attackers via the Session messaging service and includes a unique decryption ID for reference. Additionally, it cautions victims against modifying or deleting any files, as this could hinder the decryption process

Following are the TTPs based on the MITRE Attack Framework
| Tactic | ID | Technique/ Sub-Technique |
| Execution | T1129 | Shared Modules |
| Persistence | T1176 | Browser Extensions |
| Persistence | T1547.001 | Boot or Logon Autostart Execution: Registry Run Keys / Startup Folder |
| Persistence | T1574.002 | Hijack Execution Flow: DLL Side-Loading |
| Privilege Escalation | T1547.001 | Boot or Logon Autostart Execution: Registry Run Keys / Startup Folder |
| Privilege Escalation | T1574.002 | Hijack Execution Flow: DLL Side-Loading |
| Defense Evasion | T1027 | Obfuscated Files or Information |
| Defense Evasion | T1036 | Masquerading |
| Defense Evasion | T1070.004 | Indicator Removal: File Deletion |
| Defense Evasion | T1140 | Deobfuscate/Decode Files or Information |
| Defense Evasion | T1222 | File and Directory Permissions Modification |
| Defense Evasion | T1497.001 | Virtualization/Sandbox Evasion: System Checks |
| Defense Evasion | T1562.001 | Impair Defenses: Disable or Modify Tools |
| Defense Evasion | T1574.002 | Hijack Execution Flow: DLL Side-Loading |
| Credential Access | T1003 | OS Credential Dumping |
| Discovery | T1010 | Application Window Discovery |
| Discovery | T1012 | Query Registry |
| Discovery | T1033 | System Owner/User Discovery |
| Discovery | T1057 | Process Discovery |
| Discovery | T1082 | System Information Discovery |
| Discovery | T1083 | File and Directory Discovery |
| Discovery | T1087 | Account Discovery |
| Discovery | T1497.001 | Virtualization/Sandbox Evasion: System Checks |
| Discovery | T1518 | Software Discovery |
| Lateral Movement | T1080 | Taint Shared Content |
| Collection | T1005 | Data from Local System |
| Collection | T1115 | Clipboard Data |
| Collection | T1185 | Browser Session Hijacking |
| Impact | T1486 | Data Encrypted for Impact |
| Impact | T1490 | Inhibit System Recovery |
Relevancy and Insights:
ETLM Assessment:
CYFIRMA’s Analysis of the available data suggests that LucKY_Gh0$t ransomware poses a significant risk across various regions. Future iterations may feature enhanced encryption algorithms, advanced evasion techniques, and broader industry targeting. With increased sophistication in persistence methods and potential use of zero-day exploits, vigilance and robust cybersecurity measures are essential to effectively mitigate these evolving threats.
Sigma Rule
title: Drops script at startup location threatname:
behaviorgroup: 1
classification: 7 logsource:
service: sysmon product: windows
detection:
selection: EventID: 11 TargetFilename:
– ‘*\AppData\Roaming\Microsoft\Windows\Start Menu\Programs\Startup\\*.vbs*’
– ‘*\AppData\Roaming\Microsoft\Windows\Start Menu\Programs\Startup\\*.js*’
– ‘*\AppData\Roaming\Microsoft\Windows\Start Menu\Programs\Startup\\*.jse*’
– ‘*\AppData\Roaming\Microsoft\Windows\Start Menu\Programs\Startup\\*.bat*’
– ‘*\AppData\Roaming\Microsoft\Windows\Start Menu\Programs\Startup\\*.url*’
– ‘*\AppData\Roaming\Microsoft\Windows\Start Menu\Programs\Startup\\*.cmd*’
– ‘*\AppData\Roaming\Microsoft\Windows\Start Menu\Programs\Startup\\*.hta*’
– ‘*\AppData\Roaming\Microsoft\Windows\Start Menu\Programs\Startup\\*.ps1*’
– ‘*\AppData\Roaming\Microsoft\Windows\Start Menu\Programs\Startup\\*.wsf*’
condition: selection level: critical
(Source: Surface web)
IOCs:
Kindly refer to the IOCs section to exercise controls on your security systems.
STRATEGIC RECOMMENDATION
MANAGEMENT RECOMMENDATION
TACTICAL RECOMMENDATION
Type: Stealer | Objectives: Data theft, Data exfiltration | Target Technologies: macOS, Browsers, Cryptocurrency wallets.
CYFIRMA collects data from various forums based on which the trend is ascertained. We identified a few popular malware that were found to be distributed in the wild to launch cyberattacks on organizations or individuals.
Active Malware of the Week
This week “Banshee” is trending.
Banshee
Researchers discovered a new version of the Banshee macOS stealer, linked to Russian- speaking cybercriminals targeting macOS users. Undetected for over two months, this variant surfaced after the original version’s source code was leaked on dark web forums, sharing similarities in functionality. A notable difference is its use of a string encryption algorithm, similar to Apple’s XProtect antivirus. While XProtect binaries decrypt YARA rules for detection, Banshee leverages this algorithm to decrypt critical strings vital to its operations, including executed commands, browser names and paths, extension IDs, wallet details, and command-and-control (C&C) information. Distributed through malicious GitHub repositories, Banshee targeted macOS users while Windows users faced Lumma Stealer. Priced at $3,000, Banshee operated as a “stealer-as-a-service,” promoted on Telegram and dark web forums. Following the source code leak on November 23, 2024, its creator shut down operations, yet threat actors continue to spread the updated version via phishing websites, underscoring the persistent threat it poses.
Banshee’s Advanced Anti-Analysis Techniques
Banshee’s core functionality remains largely unchanged, but the updated version incorporates advanced anti-analysis techniques to evade detection. One key method involves creating child processes to confuse debugging tools, starting with the fork() function to spawn a child process while terminating the parent. Before exiting, the parent process shuts down any open terminal sessions to further obscure its activity. The child process then runs in the background, mimicking a legitimate system service to blend in with normal operations. In a series of steps, additional child processes are created, with one attempting to gain special permissions to the root directory. If unsuccessful, the malware halts its activity; if successful, it ensures silent operation by redirecting all input, output, and error streams to prevent any visible traces of malicious behavior. Following this, Banshee retrieves system directories to steal user and browser data, storing the information in a temporary folder it creates specifically for this purpose. Unlike previous versions, the updated Banshee no longer checks for the Russian language, removing a safeguard that previously stopped it from running in certain regions. This change highlights the malware’s evolution toward broader targeting.
Capabilities of Banshee
Banshee is a fully operational stealer designed to collect a variety of sensitive data, credentials from multiple browsers including:
It also targets browser extensions, particularly those related to cryptocurrency wallets, and a Two-Factor Authentication (2FA) extension called authenticator.cc— Authenticator. All stolen data is stored in a temporary directory, which is randomly named to avoid detection. Interestingly, some of these targeted extensions appear to no longer exist, suggesting they may have been repurposed from previous malware campaigns. In addition to browser data, Banshee goes after cryptocurrency wallet information, including:
The malware also collects system information such as hardware and software details, external IP addresses, and macOS passwords by tricking the user into entering them via a pop-up. The collected system information is stored in a separate directory for later exfiltration. Banshee also targets keychain passwords and uses AppleScript to grab files from the infected machine, storing them in a designated folder. If the AppleScript execution fails, it will retry up to 30 times, each time attempting to reset permissions by executing the command. After collecting the necessary files, the malware shows a failure message to the user, making them think that the software is not functioning properly.
The stolen data is then prepared for exfiltration: it is zipped, XOR encrypted with a campaign ID, and base64 encoded. A JSON file is created containing this encrypted content, which is then sent to the command and control (C&C) server via a POST request. The server infrastructure has evolved over time, with initial versions using the Django framework for communication. Later developments replaced Django with FastAPI, making the server setup stealthier by hiding the admin panel behind a relay server. This setup strengthens the malware’s ability to evade detection and disrupt efforts.
GitHub Campaigns Distributing Banshee Stealer
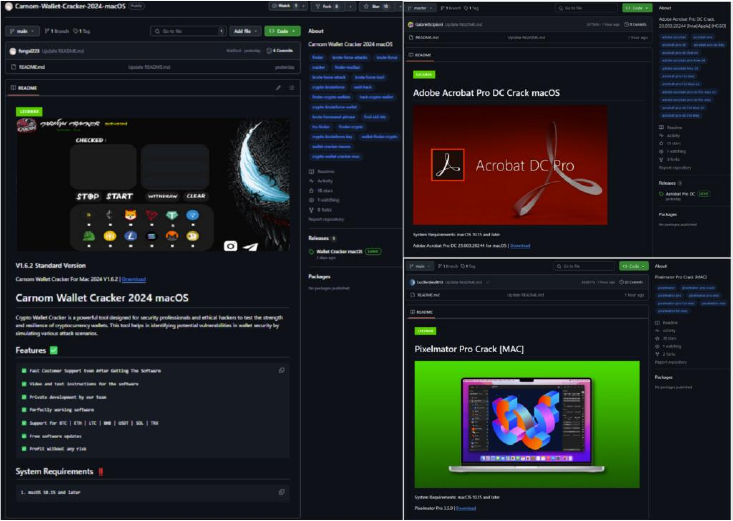
Expanding on its capabilities, Banshee’s distribution methods demonstrate its adaptability. Researchers identified several repositories distributing a new version of Banshee Stealer, specifically targeting macOS users. These repositories often disguised as offering cracked software—mainly for Adobe or other image/video editing tools—distributed the malware across three distinct waves. The first wave occurred between October 18 and 21, with nine repositories that gained 10 to 30 stars, appearing more legitimate. A smaller second campaign took place around October 31, followed by a third wave around November 3, using a similar number of repositories and stars. Initially, these repositories were empty or benign, but after about two weeks, malicious activity began.
The first campaign only targeted macOS users, distributing files that included Software_Installation_Tool.v3.2.zip, containing Setup_V3.2.dmg, and Setup_V3.0.dmg with the same file hash. The malware’s campaign ID was linked to a command-and-control (C&C) server, where stolen information was received.
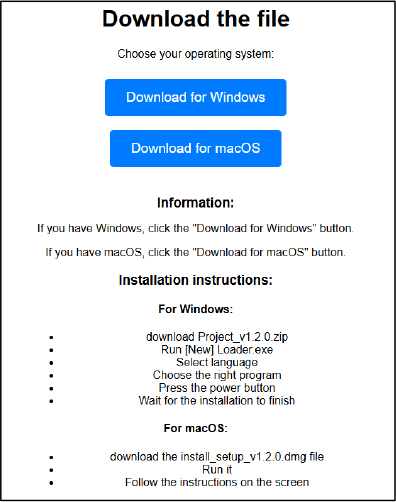
The second campaign targeted both macOS and Windows users. It involved repositories redirecting victims to GitHub.io page containing two malicious archive links—one for Lumma Stealer (Windows) and another for Banshee Stealer (macOS). The campaign ID and C&C server remained the same as the first campaign. As of December 10, these repositories continued to spread malware without detection.
The third campaign also targeted both Windows and macOS. The macOS version of the malware came in Soft.Install.v1.4.zip, which contained Installer.dmg, while the Windows version used ExtraModes_v1.6.zip. The C&C server communicated with the same infrastructure as the second campaign. This campaign used both Lumma Stealer (for Windows) and Banshee Stealer (for macOS), with almost all repositories being created before the malware was pushed. Each release contained two archives—one for Windows and one for macOS.
Banshee Stealer’s Latest Campaigns
Researchers discovered several new versions of the Banshee Stealer, including one that introduced string encryption on September 26. Since then, more than 26 campaigns have been observed, with three of them distributed via GitHub. These campaigns were not limited to GitHub, as other distribution methods were also identified. Despite the variety of techniques used, the filenames of the stolen files consistently impersonated popular software, including Chrome, TradingView, Zegent, Parallels, Solara, CryptoNews, MediaKIT, and Telegram. By analyzing the collected samples, researchers identified two major clusters based on their distribution methods. One cluster involved a specific command and control (C&C) server, which likely distributed most of the campaigns using filenames like “Setup,” “Installer,” and “Update.” The second cluster contained campaigns with linked C&C servers that maintained consistent software names, simplifying the process of tracking the origin of the malware.
A recent campaign from the second cluster, observed on December 3, targeted macOS users with a fake chat application on a phishing website. The website provided a malicious download link only for macOS users, while Windows or Linux users were not shown the link. The malicious file, disguised as a legitimate application, was downloaded from a suspicious URL. Despite the Banshee stealer-as-a-service business reportedly closing, threat actors continue to use updated versions of the malware to target macOS users in ongoing campaigns.
INSIGHTS
ETLM ASSESSMENT
From the ETLM perspective, CYFIRMA anticipates that as macOS continues to gain market share, now comprising 15.1% of the global PC market with over 100 million users, the threat of Banshee stealer is expected to grow. Many macOS users still mistakenly believe their systems are immune to malware due to the platform’s Unix-based architecture and historically smaller target profile for cybercriminals. However, as attackers focus more on this expanding user base, Banshee’s ability to steal sensitive data, such as browser credentials, cryptocurrency wallets, and system information, poses a significant risk. With more individuals relying on macOS for work and financial transactions, the malware’s evolving capabilities, distributed through platforms like GitHub and phishing sites, will continue to increase the vulnerability of organizations and employees to data theft. To mitigate the growing risks, businesses will need to strengthen their security frameworks to account for this emerging threat targeting macOS users.
IOCs:
Kindly refer to the IOCs Section to exercise controls on your security systems.
YARA Rules
private rule macOS_binary
{
meta:
descr = “MacOS file format” condition:
uint32(0) == 0xFEEDFACE or uint32(0) == 0xFEEDFACF or uint32(0) == 0xBEBAFECA
}
rule banshee_macOS
{
meta:
descr = “Banshee MacOS stealer, encrypted strings version”
sha256 = “ce371a92e905d12cb16b5c273429ae91d6ff5485dda04bfedf002d2006856038” strings:
// x64
$x64_code_str_decr1 = {80 E1 ?? (48| 49) 89 (DE| F0| FE) (48| 49) D3 (EE| E8) (40| 44) 30 ?? 48
83 C2 08}
$x64_code_str_decr12 = {0B 09 7D 92 2B 25 CB 9A 4C 01 40 39 8B 01 0B 4A 4B 15 00 38}
$x64_code_str_decr2 = {48 89 ?? 48 D3 [1-2] 30 ?? 48 83 C1 08 48 FF C?}
$x64_code_str_decr3 = {81 30 [4] C6 40 04 00}
$x64_code_str_decr4 = {2B 25 C8 9A 4C 01 40 39 8B 01 0B 4A 4B 15 00 38 08 21 00 91}
$x64_code_campid = {88 14 08 8A 54 31 02 48 FF C1 48 83 F9 1D}
$x64_code_gen1 = {C6 40 09 00 31 C9 8A 14 08}
$x64_code_gen2 = {88 14 31 8A 54 30 02 48 FF C6 84 D2}
$x64_code_gen3 = {72 00 77 00 [30] 00 3B 00 00}
// Arm
$arm_code_str_decr1 = {0B 09 7D 92 2B 25 CB 9A 4C 01 40 39 8B 01 0B 4A 4B 15 00 38 08 21 00 91}
$arm_code_str_decr2 = {2B 25 C8 9A 4C 01 40 39 8B 01 0B 4A 4B 15 00 38 08 21 00 91}
$arm_code_campid = {6C 01 09 8B 0A 69 29 38 8A 05 40 39 29 05 00 91 3F 79 00 F1}
$arm_code_gen1 = {1F 24 00 39 08 00 80 D2}
$arm_code_gen2 = {72 00 77 00 [30] 00 3B 00 00} condition:
macOS_binary and 6 of ($x64_code*) or all of ($arm_code*)
}
(Source: Surface Web)
STRATEGIC:
MANAGEMENT:
TACTICAL RECOMMENDATIONS
Key Intelligence Signals:
Chinese State-Sponsored RedDelta Targets Taiwan, Mongolia, and Southeast Asia with Modified PlugX Malware Campaign.
SUMMARY
Between July 2023 and December 2024, a Chinese state-sponsored group targeted countries including Mongolia, Taiwan, Myanmar, Vietnam, and Cambodia, using an adapted infection chain to distribute a customized backdoor known as PlugX. The group employed various spearphishing techniques, leveraging themes such as political events, national holidays, and international meetings to lure victims. The group notably compromised the Mongolian Ministry of Defense in August 2024 and the Communist Party of Vietnam in November 2024. Additionally, attempts to target the Vietnamese Ministry of Public Security were observed, though no successful compromise was detected. The group expanded its targeting to other nations, including Malaysia, Japan, the United States, and others, between September and December 2024.
In late 2023, the group altered its initial infection method by using Windows Shortcut (LNK) files delivered via spearphishing. By 2024, the infection chain evolved further to utilize Microsoft Management Console Snap-In Control (MSC) files. The most recent tactic involved prompting victims to load an HTML file hosted on Microsoft Azure through spearphishing links. Cloudflare’s content distribution network (CDN) was consistently used to obfuscate command-and-control traffic, making detection difficult.
The group’s operations align with Chinese geopolitical priorities, primarily focusing on Southeast Asia, Mongolia, and Taiwan. The group’s activities suggest a return to its historical focus on regions seen as threats to Chinese power. Mitigations to counter the group’s efforts include using detection tools, keeping software updated, filtering email for malicious attachments, and ensuring network defenses are robust. The group is expected to continue evolving its methods in response to geopolitical shifts.
Relevancy & Insights:
The threat actor’s past attacks have largely focused on regions critical to Chinese strategic interests, such as Taiwan, Mongolia, and Southeast Asia, aligning with its ongoing geopolitical objectives. In 2022, the group targeted European organizations, marking a shift in focus, but returned to its historical priorities in 2023 and 2024. Previous operations saw similar tactics, like the use of tailored spearphishing campaigns and malware to compromise governmental and diplomatic entities. For instance, the group previously used malware like PlugX in targeted attacks against Mongolian and Taiwanese organizations, mirroring its current approach. The group’s evolving infection chain, from LNK files to MSC and HTML file exploits, reflects its adaptive methods, ensuring persistence in bypassing defenses while maintaining consistent regional targets. This continued focus on sensitive political environments highlights the actor’s long-term strategic goals.
ETLM Assessment:
The threat actor is a Chinese state-sponsored group, RedDelta, known for targeting governments, diplomatic entities, and organizations linked to Chinese strategic interests. Historically, it has focused on Southeast Asia, Taiwan, and Mongolia, and more recently, expanded its targets to other regions such as the United States, Brazil, and Australia. The group primarily targets government and diplomatic sectors, as well as NGOs, activists, and religious organizations. Its attack methods include spearphishing, exploiting both social engineering and technical vulnerabilities.
RedDelta has evolved its tactics, moving from using Windows Shortcut (LNK) files to Microsoft Management Console Snap-In Control (MSC) files and, most recently, HTML files hosted on Microsoft Azure. It uses Cloudflare to mask command-and-control traffic, complicating detection.
The group’s malware of choice is PlugX, a customized backdoor, which has been consistently used since its earlier attacks. Given its adaptation to detection evasion, RedDelta is expected to continue evolving, focusing on politically sensitive regions and organizations, responding to geopolitical shifts, and maintaining its persistent operations.
Recommendations:
Strategic Recommendations
Tactical Recommendations
Operational Recommendations
| MITRE FRAMEWORK | ||
| Tactic | ID | Technique |
| ResourceDevelopment | T1583.003 | Acquire Infrastructure: Virtual Private Server |
| ResourceDevelopment | T1583.001 | Acquire Infrastructure: Domains |
| Initial access | T1566.001 | Phishing: Spearphishing Attachment |
| Initial access | T1566.002 | Phishing: Spearphishing Link |
| Execution | T1204.002 | User Execution: Malicious File |
| Execution | T1059.001 | Command and Scripting Interpreter: PowerShell |
| Persistence | T1547.001 | Boot or Logon AutoStart Execution: Registry Run Keys / Startup Folder |
| DefenseEvasion | T1574.001 | Hijack Execution Flow: DLL Search Order Hijacking |
| Defense Evasion | T1627.001 | Execution Guardrails — Geofencing |
| Defense Evasion | T1218.007 | System Binary Proxy Execution: Msiexec |
| Defense Evasion | T1140 | Deobfuscate/Decode Files or Information |
| Defense Evasion | T1036.005 | Masquerading: Match Legitimate Name or Location |
| Defense Evasion | T1036.007 | Masquerading: Double File Extension |
| Discovery | T1082 | System Information Discovery |
| Command and Control | T1573.001 | Encrypted Channel: Symmetric Cryptography |
| Command and Control | T1132.001 | Data Encoding: Standard Encoding |
| Command and Control | T1102 | Web Service |
| Command and Control | T1071.001 | Application Layer Protocol: Web Protocols |
IOCs:
Kindly refer to the IOCs (Indicators of Compromise) Section to exercise controls on your security systems
Japan attributes more than 200 cyberattacks to Chinese hackers
Japan’s National Police Agency (NPA) has linked over 200 cyberattacks in the past five years to the Chinese threat actor MirrorFace. These attacks targeted the Japan Aerospace Exploration Agency (JAXA), the Foreign and Defense Ministries, private companies, think tanks, and individuals such as politicians and journalists.
The NPA suspects the attacks aimed to steal information related to national security and advanced technology. MirrorFace reportedly gained initial access to its victims through phishing emails containing malware or by exploiting vulnerabilities in VPN systems.
ETLM Assessment:
Japan is facing unprecedented changes in the security situation in the region, under which the country faces increasingly emboldened, immediate neighbours like China and North Korea. Japan is now entering an era of remilitarization, unprecedented since the Second World War which further prompts Chinese state- backed hackers to spy on the Japanese government and all entities linked in any way to national security and defense technology.
Russian hackers target Kazakhstan
Hackers associated with the Kremlin-backed threat actor APT28 have been conducting espionage on diplomatic entities in Central Asia, with a particular focus on Kazakhstan, to collect economic and political intelligence, according to researchers. Active since at least 2021, the group has previously targeted diplomatic, nonprofit, academic, energy, and defense organizations across various regions, including Ukraine, Israel, India, and several Central Asian countries such as Kazakhstan, Kyrgyzstan, and Tajikistan.
In the recently uncovered cyber-espionage campaign, the APT deployed malware by leveraging legitimate documents — including correspondence letters, draft papers, and internal administrative notes — that are believed to have originated from Kazakhstan’s Ministry of Foreign Affairs.
ETLM Assessment:
The behaviour of the Central Asian states and Kazakhstan in particular shows a general conviction that Moscow is no longer able to play its role of enforcer and more and more eyes are directed primarily towards Beijing and partly also towards Ankara. In Central Asia, it is Beijing in particular that is facing pressure from local governments to fill the security vacuum left by Moscow. An increasing number of Central Asian soldiers and police are being trained in China, and Russian weapons are increasingly being replaced by Chinese ones. The European Union is the main regional trading partner, followed by China and Russia is only third. Hence, the effort, which is clearly a classic case of state-driven espionage, is likely part of a broader Russian strategy to gather intelligence on geopolitical developments and maintain influence in post-Soviet states.
The Lynx Ransomware Impacts SERGAS Group
Summary:
From the External Threat Landscape Management (ETLM) Perspective, CYFIRMA observed in an underground forum that a company from the United Arab Emirates (UAE); SERGAS Group(www[.]sergasgroup[.]com), was compromised by Lynx Ransomware. SERGAS Group is a leading provider of customized solutions in Liquefied Petroleum Gas (LPG), Synthetic Natural Gas (SNG), Natural Gas (NG), and Medical Gas, serving a diverse clientele across industrial, commercial, and residential sectors. Operating primarily in the Gulf region, SERGAS Group offers safe and reliable gas solutions tailored to clients’ specific needs. The compromised data includes contracts, confidential information, financial records, customer data, and human resources information.
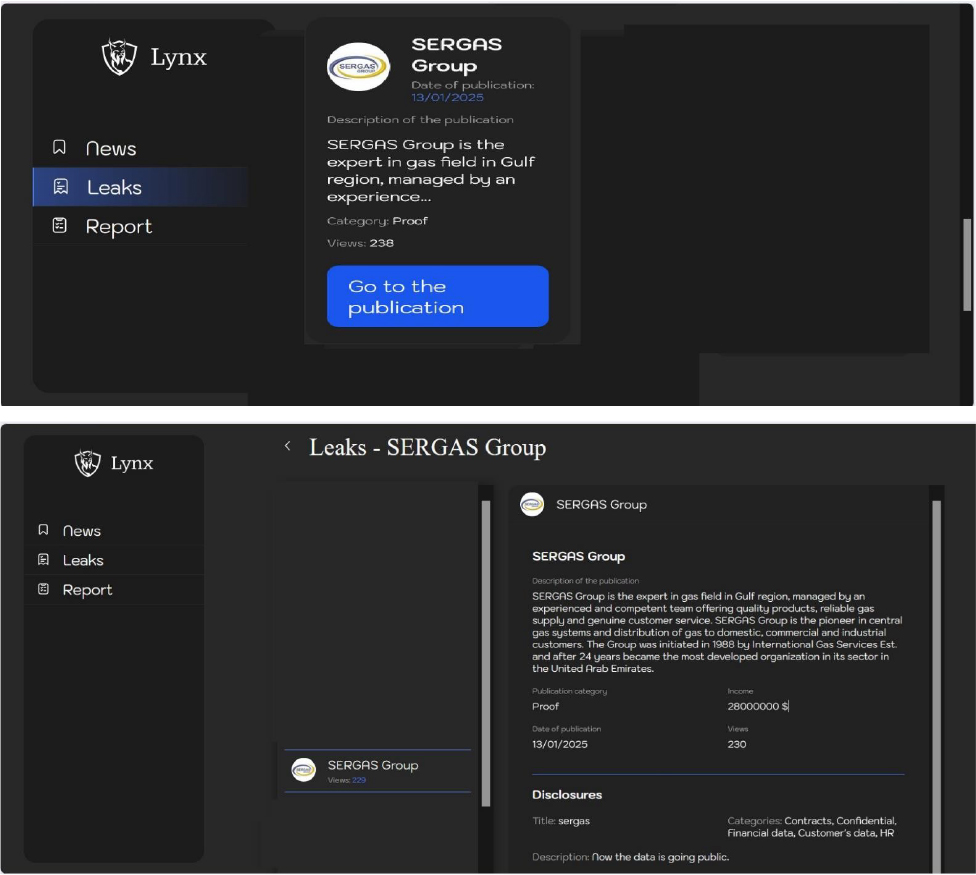
Relevancy & Insights:
ETLM Assessment:
According to CYFIRMA’s assessment, Lynx Ransomware represents a significant threat in the evolving landscape of cybercrime. Its sophisticated techniques and aggressive tactics necessitate robust cybersecurity measures from organizations to mitigate risks associated with ransomware attacks. As this group continues to operate, ongoing monitoring and analysis will be crucial for understanding their methods and developing effective defenses against them.
The RansomHub Ransomware Impacts Wise Solution and Consulting Co., Ltd.
Summary:
From the External Threat Landscape Management (ETLM) Perspective, CYFIRMA observed in an underground forum that a company from Thailand; Wise Solution and Consulting Co., Ltd. (www[.]wisesocon[.]com), was compromised by RansomHub Ransomware. Wise Solution and Consulting Co., Ltd. is a Consulting and IT infrastructure company based in Thailand. The data, which has been breached, has not yet appeared on the leak site, indicating that negotiations between the affected party and the ransomware group may be underway. The compromised data consists of confidential and sensitive information related to the organization. The total size of the compromised data is approximately 40 GB.
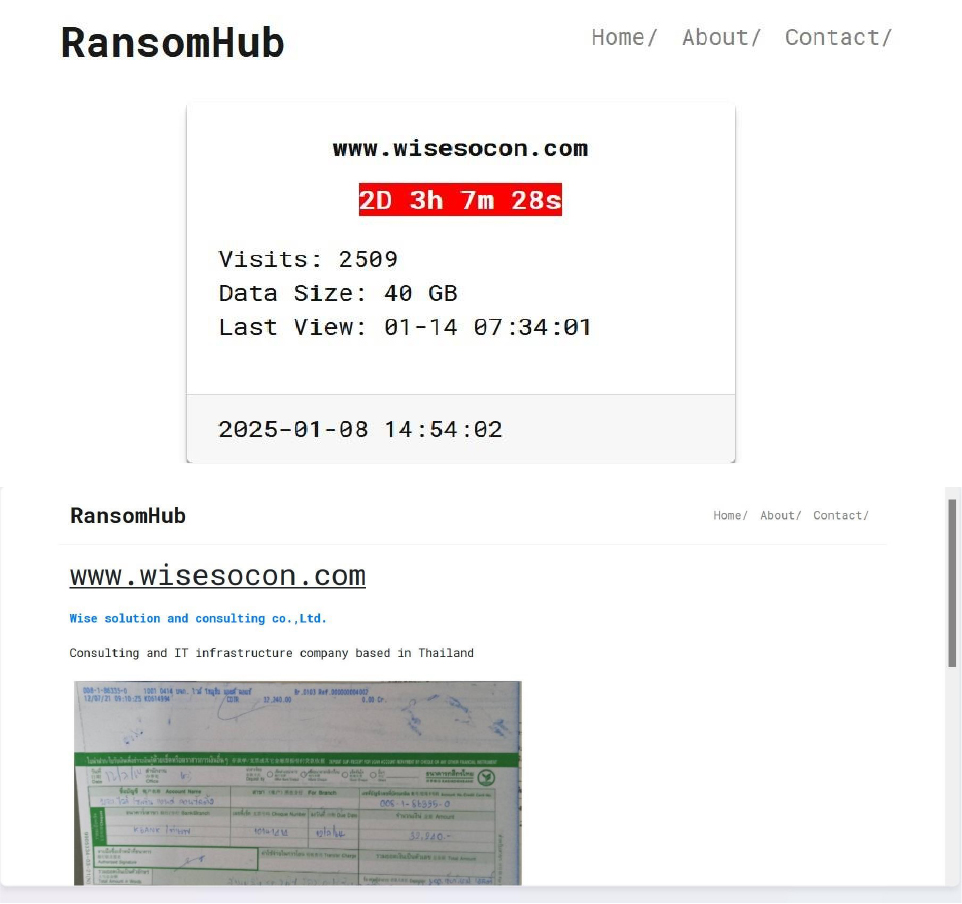
Relevancy & Insights:
ETLM Assessment:
Based on recent assessments by CYFIRMA, RansomHub ransomware is expected to intensify its operations across various industries worldwide, with a notable focus on regions in the United States, Europe, and Asia. This prediction is reinforced by the recent attack on Wise Solution and Consulting Co., Ltd, a prominent Information Technology company from Thailand, highlighting RansomHub’s significant threat presence in Southeast Asia.
Vulnerability in Veeam Backup for Microsoft Azure
Relevancy & Insights:
The vulnerability exists due to insufficient validation of user- supplied input. A remote attacker can send a specially crafted HTTP request and trick the application to initiate requests to arbitrary systems.
Impact:
Successful exploitation of this vulnerability may allow a remote attacker to gain access to sensitive data, located in the local network or send malicious requests to other servers from the vulnerable system.
Affected Products:
https[:]//www[.]veeam.com/kb4709
Recommendations:
Monitoring and Detection: Implement monitoring and detection mechanisms to identify unusual system behavior that might indicate an attempted exploitation of this vulnerability.
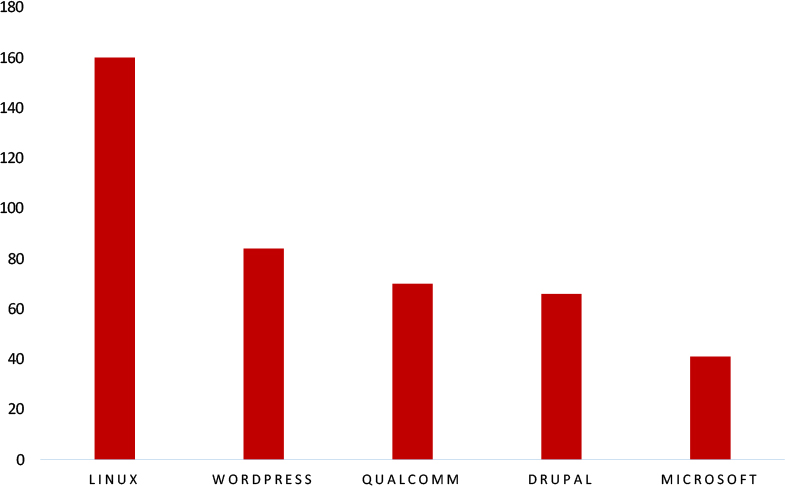
TOP 5 AFFECTED TECHNOLOGIES OF THE WEEK
This week, CYFIRMA researchers have observed significant impacts on various technologies, due to a range of vulnerabilities. The following are the top 5 most affected technologies.
ETLM Assessment
Vulnerability in Veeam Backup for Microsoft Azure can pose significant threats to user privacy and security. This can impact various industries globally, including technology, finance, healthcare, and beyond. Ensuring the security of Veeam Backup for Microsoft Azure is crucial for maintaining the integrity and protection of users’ data worldwide. Therefore, addressing these vulnerabilities is essential to safeguarding backup and disaster recovery processes, including the protection of Azure VMs, Azure SQL databases, Cosmos DB accounts, Azure Files, and Virtual Network configurations, across different geographic regions and sectors.
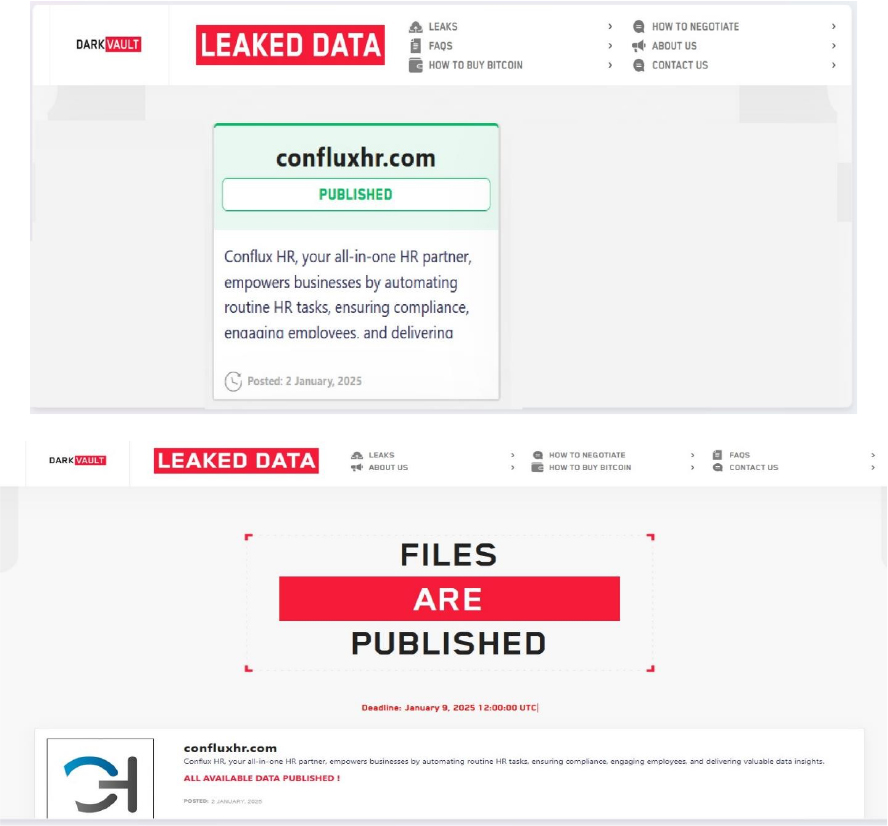
DarkVault Ransomware attacked and published the data of ConfluxHR
Summary
Recently, we observed that DarkVault Ransomware attacked and published the data of ConfluxHR (BRI)(www[.]confluxhr[.]com) on its dark web website. ConfluxHR is a comprehensive cloud-based Human Resource Management System (HRMS) designed to streamline various HR processes for organizations. Its suite of modules includes Employee Self-Service (ESS), Attendance Management, Leave Management, Payroll Management, Recruitment Management, Performance Management, and Exit Process Management. The ransomware attack resulted in a data leak containing confidential and sensitive organizational information.
Relevancy & Insights:
ETLM Assessment:
According to CYFIRMA’s assessment, DarkVault represents a significant threat within the ransomware ecosystem due to its aggressive tactics and ability to compromise diverse targets quickly. As they continue to operate and expand their victim base, ongoing monitoring of their activities will be essential for understanding their impact on global cybersecurity efforts. Organizations must remain vigilant and proactive in their defense strategies against evolving ransomware threats like DarkVault.
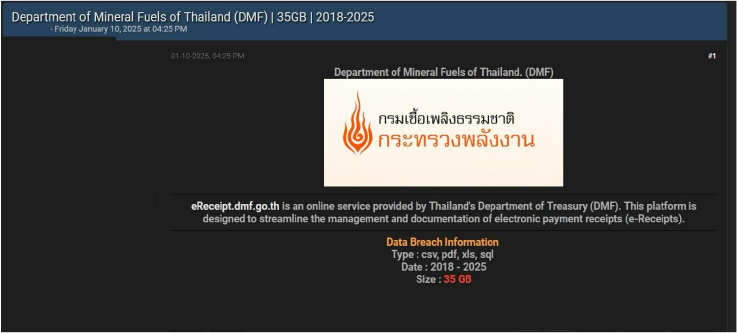
Thailand’s Department of Mineral Fuels (DMF) Data Advertised on a Leak Site
Summary: The CYFIRMA Research team has identified a data leak involving Thailand’s Department of Mineral Fuels (DMF) on an underground forum. The breach reportedly exposed 35GB of sensitive data spanning from 2018 to 2025. The leaked information allegedly includes internal documents, operational records, and potentially classified materials, underscoring significant vulnerabilities within governmental cybersecurity infrastructure.
This breach underscores the risks associated with inadequate data protection measures in government agencies, potentially exposing sensitive national resources-related information to misuse. The implications of such a breach could extend beyond privacy violations, potentially impacting Thailand’s strategic energy operations and national security.
Authorities are urged to investigate the breach comprehensively and strengthen cybersecurity protocols to prevent future incidents. Meanwhile, organizations handling sensitive data should reassess their current security frameworks to ensure resilience against evolving cyber threats. The breach has been linked to a threat actor identified as “ClaratZ.”
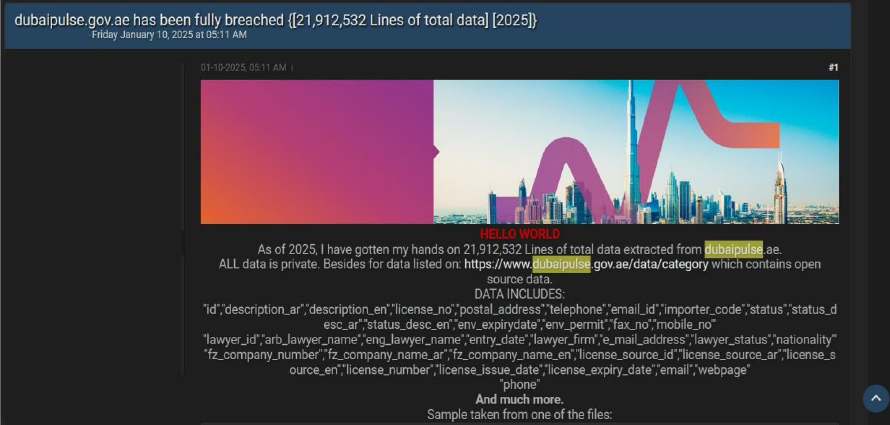
Dubai Pulse Data Advertised on a Leak Site
Summary:
The CYFIRMA Research team observed a data leak related to Dubai Pulse(https[:]//www.dubaipulse[.]gov[.]ae) in an underground forum. Dubai Pulse is a comprehensive digital platform developed by the Smart Dubai Office to enhance the city’s data-driven initiatives. It serves as a centralized hub for accessing high-quality, verified datasets from various public sector entities in Dubai. These datasets are organized by categories such as Business & Employment, Economics & Finance, Education, Entertainment, Environment, Events, and Finance, facilitating informed decision-making and fostering innovation. The compromised data includes identification details, license numbers, postal addresses, telephone numbers, and email addresses, as well as sensitive and confidential information. The breach has been linked to a threat actor identified as “Henrymans0n.”
Relevancy & Insights:
Financially motivated cybercriminals are continuously scouring for exposed and vulnerable systems and applications to exploit. A significant number of these malicious actors congregate within underground forums, where they discuss cybercrime and trade stolen digital assets. Operating discreetly, these opportunistic attackers target unpatched systems or vulnerabilities in applications to illicitly gain access and steal valuable data.
Subsequently, the pilfered data is advertised for sale within underground markets, where it can be acquired, repurposed, and utilized by other malicious actors in further illicit activities.
ETLM Assessment:
Threat actor “ClaratZ” is a notable threat actor within the cybersecurity landscape, engaging in defacement attacks and data breaches across various sectors. Organizations are encouraged to enhance their cybersecurity measures to defend against such threats by implementing robust security protocols and monitoring for unusual activity. Continuous vigilance is essential to mitigate risks associated with emerging cyber threats like ClaratZ.
Recommendations: Enhance the cybersecurity posture by:
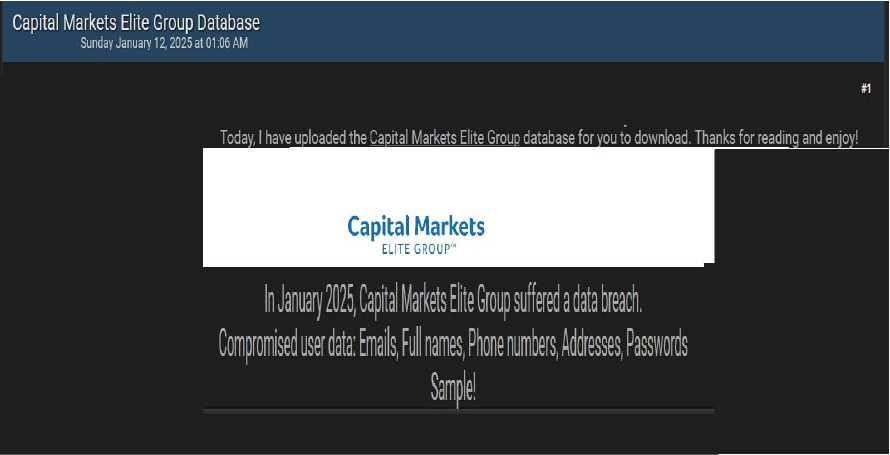
The CYFIRMA Research team has detected a data leak involving the Capital Markets Elite Group on an underground forum. Capital Markets Elite Group, an independent financial services provider, offers advanced trading platforms alongside retail, institutional, and alternative investment services. The leaked user data reportedly includes email addresses, full names, phone numbers, physical addresses, and passwords. The breach has been attributed to a threat actor operating under the alias “IntelBroker.”
The CYFIRMA Research team has identified a data leak involving TDCX on an underground forum. TDCX, headquartered in Singapore, is a global provider of customer experience and support services for major organizations. The company manages content moderation for Facebook, support services for Volvo, customer service for Visa Bank, and both customer service and purchasing assistance for Lazada. TDCX also handles customer support for Airbnb, content moderation and user interaction management for Twitter, and customer experience management for Google, particularly in digital advertising and online services. Additionally, the company enhances customer experiences for AWS Amazon, provides subscriber support for Spotify, and manages customer service for Netflix.
The leaked database reportedly contains sensitive information, including over 538,142 employee and company email addresses and more than 700,000 first and last names, exposing a significant amount of personal and corporate data.
ETLM Assessment:
“IntelBroker” represents a significant threat within the cybersecurity landscape due to its sophisticated tactics and high-profile targets. Organizations are advised to implement robust security measures such as access control, regular patch management, and employee training to mitigate risks associated with such threat actors. Continuous monitoring of emerging threats like IntelBroker will be essential for effective incident response strategies in the evolving cyber threat environment.
STRATEGIC RECOMMENDATIONS
MANAGEMENT RECOMMENDATIONS
TACTICAL RECOMMENDATIONS
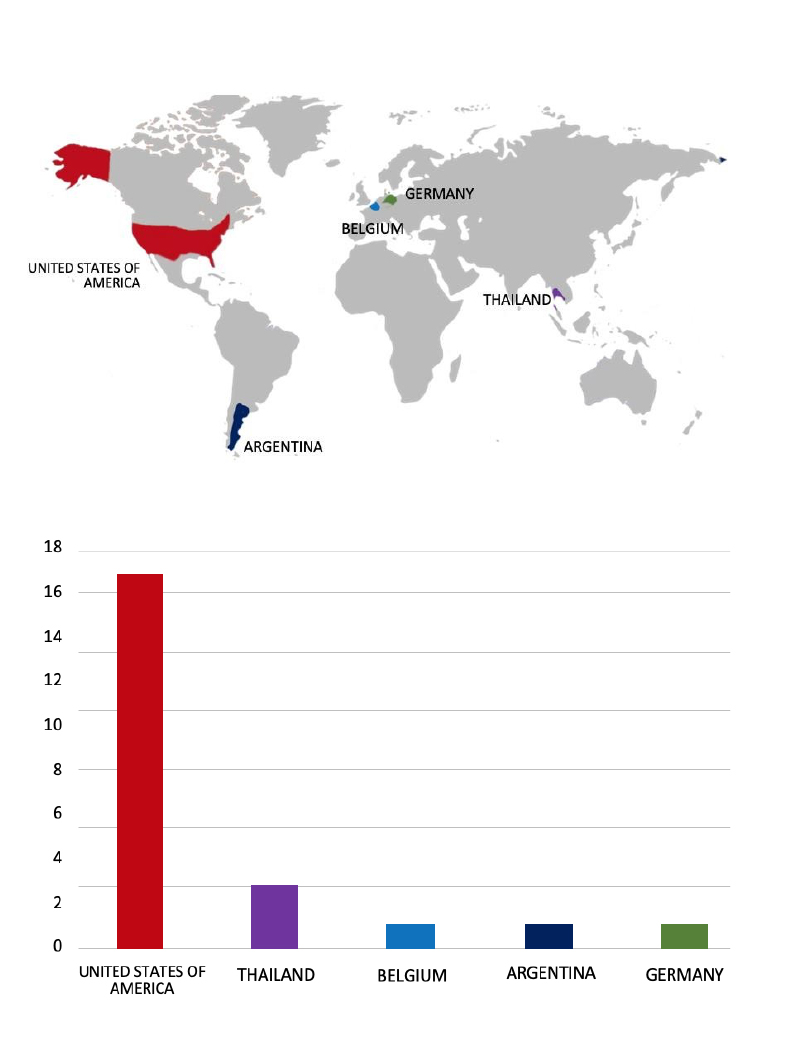
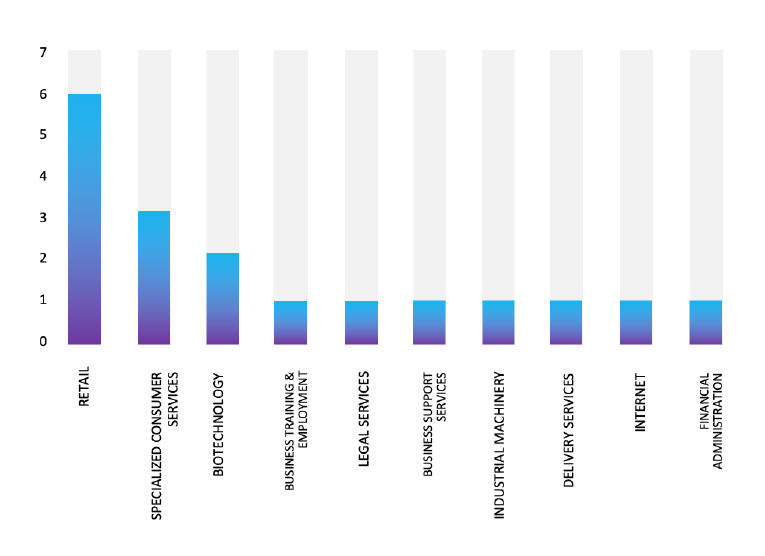
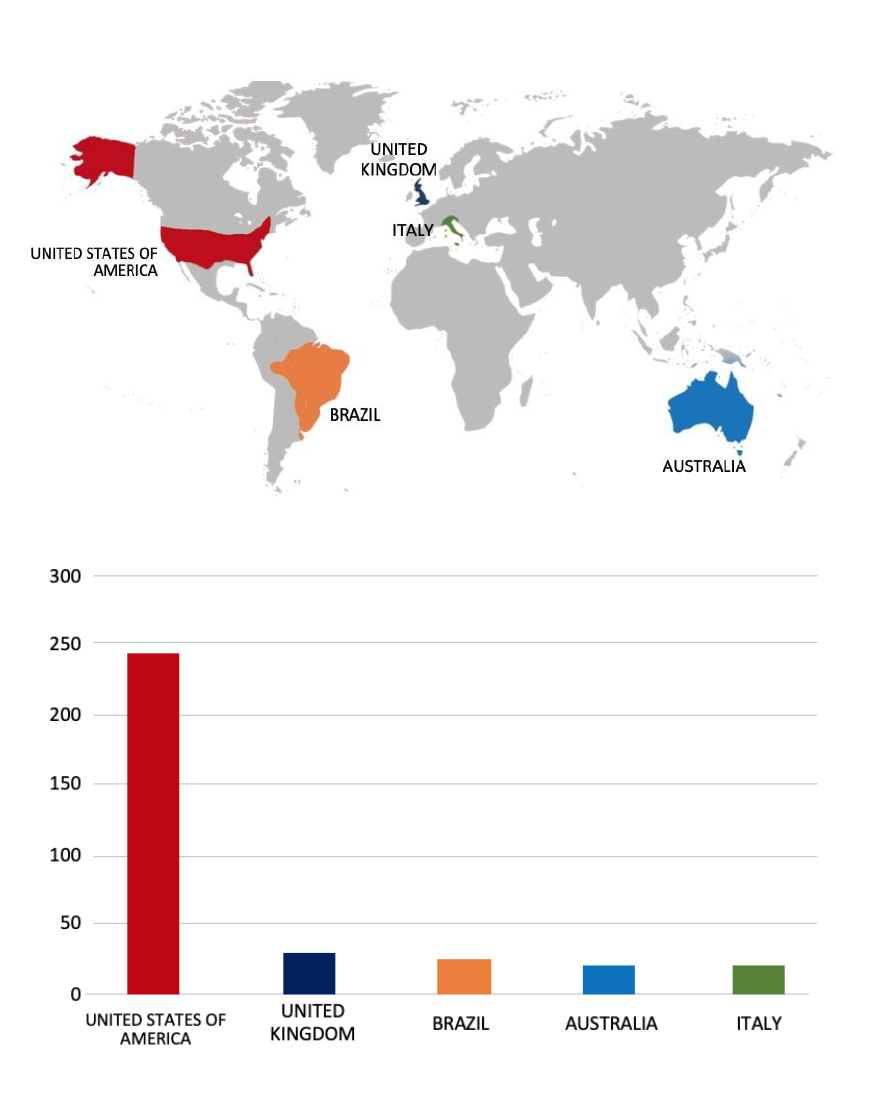
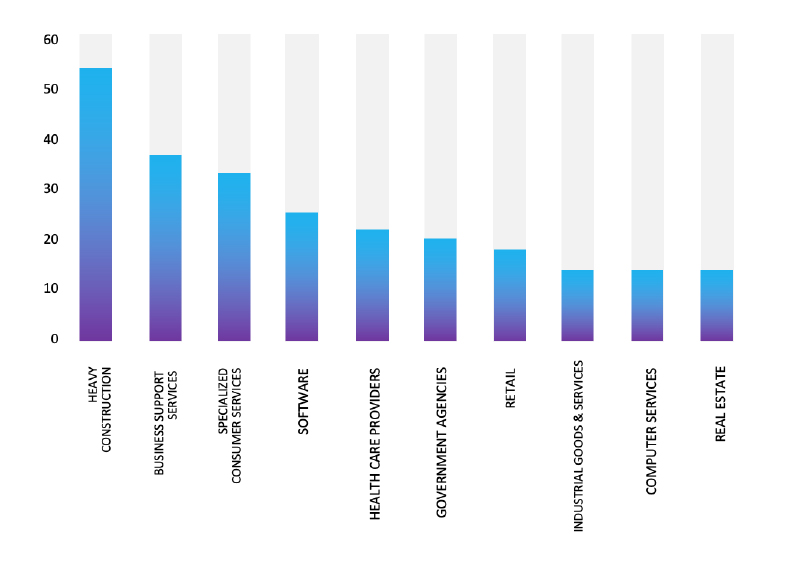
Please find the Geography-Wise and Industry-Wise breakup of cyber news for the last 5 days as part of the situational awareness pillar.
Geography-Wise Graph
Industry-Wise Graph
For situational awareness intelligence and specific insights mapped to your organisation’s geography, industry, and technology, please access DeCYFIR.