


CYFIRMA’s investigation uncovered a significant data leak involving Cisco, where the notorious threat actor, “IntelBroker,” claimed responsibility for the breach. On October 14, 2024, IntelBroker posted on BreachForum, revealing that a wide range of Cisco’s sensitive information had been compromised. The stolen data includes valuable assets, such as GitHub and GitLab projects, SonarQube projects, source code, hardcoded credentials, certificates, customer SRCs, confidential Cisco documents, Jira tickets, API tokens, AWS private buckets, Docker builds, Azure storage buckets, SSL certificates, and both private and public keys. Additionally, Cisco premium products were part of the breach.
This incident poses significant security and reputational risks along with a supply chain threat to Cisco and its B2B clients. This report covers a detailed analysis of the threat actor’s activity behind the breach and also highlights continued access to the Cisco system despite being blocked by the Cisco security system.
Cisco Data Breach by CyberNiggers Hacking Group
On October 14, 2024, a notorious threat actor known as IntelBroker posted on BreachForum, offering to sell sensitive data stolen from a Cisco breach that occurred on October 6, 2024. This breach, carried out in collaboration with other threat actors “EnergyWeaponUser” and “zjj,” compromised a vast array of critical assets. IntelBroker shared samples of the alleged stolen data, which included customer databases, confidential documents, and screenshots of customer management portals, raising significant concerns about the exposure of Cisco’s proprietary information and customer privacy. The sale of this data poses substantial security, reputational, and financial risks to Cisco and its clients.

Cisco Systems, Inc. is a global leader in networking, IT, and cybersecurity solutions, providing technology infrastructure that connects people, devices, and networks across the globe. Cisco’s innovative products and services spans across various industries, such as cybersecurity solutions, and cloud computing, in addition to routers, switches, and collaboration tools. The company is a critical technology provider to businesses and governments worldwide, enabling secure and efficient operations through advanced digital infrastructure.
The leak of confidential data and hardcoded credentials has potentially compromised the security of Cisco’s products and services, posing a risk to its customers and partners by exposing them to potential cyberattacks and operational disruptions.
CYFIRMA’s detailed investigation into the Cisco data breach uncovered that the notorious threat actor “IntelBroker,” in collaboration with two others, “EnergyWeaponUser” and “zjj,” was behind the attack. The hackers claimed that the stolen data was from as early as October 6th.
Additionally, the hackers leaked samples of data, including details of seven Cisco employees, revealing their names, usernames, email addresses, and hashed passwords.
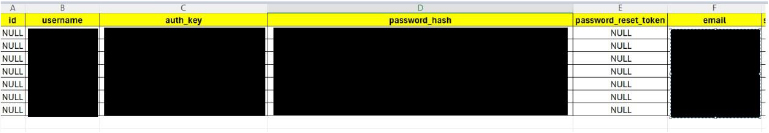
The stolen data from the Cisco breach, as posted by the IntelBroker on BreachForum, includes:
The IntelBroker confirmed his intention to sell the stolen data, stating, “If anyone is interested in buying this data, please message me on the forum or via the social apps connected to my profile”, and indicated that he is open to offers, and specifying that only Monero (XMR) will be accepted through an escrow service.
The breach was executed by IntelBroker, zjj, and EnergyWeaponUser, all of whom are affiliated with the hacking group CyberNiggers.
The hackers shared screenshots on BreachForum to validate the Cisco data breach. “Screenshots of the data included in the original post appear credible. However, since the threat actor intends to sell the stolen data and is likely seeking offers, the full extent of the breach remains undisclosed”. This raises concerns about the potential scale of the exposed information, leaving uncertainty about the total impact.
The threat actors behind the Cisco breach reportedly stole a list of over 26 production source codes, with the stolen data linked to Cisco’s business-to-business (B2B) clients.
Also, the attackers provided a list of over 1,000 impacted client names associated with the Cisco breach. However, approximately 800 unique companies have been identified, as some organizations have been mentioned multiple times due to various exposed departments.
Some prominent companies have been affected, including industry leaders, such as Apple, Google, Microsoft, Amazon’s IT center (and AWS), Citigroup, Alibaba, AT&T, Vodafone, and the Bank of China.
As part of our investigation, we contacted the hacker to request access to the sample data but have not received a response.
Interestingly before the actual leak post, on October 14, 2024, IntelBroker tweeted about an exciting breach, hinting at significant developments related to compromised data and potential implications.

On BreachForum, a hacker claimed that the breach resulted from stolen logs. Previously, a user named Emo reported that IntelBroker used stealer logs to gain access and exfiltrate data. During the investigation, EnergyWeaponUser mentioned that both IntelBroker and zjj had been expelled from Cisco, while he still retained access. He indicated that once his last access is terminated, he would disclose how they initially gained entry to Cisco.
On Oct 16th, 2 days after the breach EnergyWeaponUser posted on BreachForum that he has more propriety source codes, however, cannot share more details about it as IntelBroker will have to assess the details.

The below tweet from IntelBroker on October 16th at 7:12 PM IST reconfirms the above statement which was made by EnergyWeaponUser regarding persistent access to Cisco’s systems, despite previous efforts to block them.
The group claims to have established continued access despite being blocked by the Cisco security team by using hard-coded credentials found in earlier exfiltrated data.

Key takeaways from comments made by IntelBroker regarding his claimed continued access to Cisco Systems.
This situation highlights how dangerous hard-coded credentials can be and shows that even if attackers are temporarily removed from a network, they can regain access if such vulnerabilities are not fixed. It also highlights the need for better credential management, network segmentation, and monitoring to prevent this kind of exploitation.
Additionally, in our research, we observed one of the BreachForum users scamming on selling the data for 90K$ where IntelBroker has denied any such transaction.

IntelBroker, a black hat hacker, is affiliated with the notorious hacking group “CyberNiggers“, which operates through BreachForum. He collaborates with other threat actors, including EnergyWeaponUser, 303, and Wonder. He joined BreachForum on June 13th, 2023, and became the forum owner in August 2024, taking over from ShinyHunters and USDoD.
By June 2024, he had reportedly posted over 80 leaks and data sales on the platform, claiming to have sold data from more than 400 organizations. IntelBroker has a history of targeting various entities, including General Electric, Europol, Lulu Hypermarket, and Zscaler, with notable breaches involving prominent organizations like Home Depot, Facebook Marketplace, and Space-Eyes.
In a YouTube interview, IntelBroker claimed to be from Serbia but stated that he resides in Russia for operational safety.
In 2023 IntelBroker previously claimed to be developing the Endurance ransomware strain, which the DoD Cyber Crime Center suggested might be linked to an Iranian state entity, citing similarities between the malware and the infamous Shamoon wiping tool; however, IntelBroker denies these allegations, asserting independence and claiming to be a single individual from Serbia.

The Cisco breach represents a serious supply chain threat, with attackers gaining access to production source codes from multiple companies. Over 26 B2B clients have been identified as having their production source code compromised, and over 800 B2B clients’ data was impacted by the attack carried out by the CyberNiggers group. The stolen source codes expose critical vulnerabilities, allowing attackers to inject malicious code and disrupt services across interconnected systems. Notably, a user on BreachForum was observed attempting to sell the data for $90K, though IntelBroker denied involvement in such transactions.
Another user, Emo, reported that IntelBroker utilized stealer logs to access and exfiltrate data. At the same time, the threat actor known as EnergyWeaponUser claims to still have access to Cisco’s infrastructure as of October 16th, having posted more proprietary source code. Our research indicates that the hacker likely employed a combination of stolen credentials to continue access on the SSH server even after getting blocked by security systems.
Cisco has acknowledged the situation and confirmed that an ongoing investigation is underway to assess the breach and its impact.
Strategic Recommendations:
Operational Recommendations:
Tactical Recommendations: