



CYFIRMA Research and Advisory Team would like to highlight ransomware trends and insights gathered while monitoring various forums. This includes multiple – industries, geography, and technology – that could be relevant to your organization.
Type: Ransomware
Target Technologies: MS Windows
Introduction
CYFIRMA Research and Advisory Team has found Moscovium Ransomware while monitoring various underground forums as part of our Threat Discovery Process.
Moscovium Ransomware
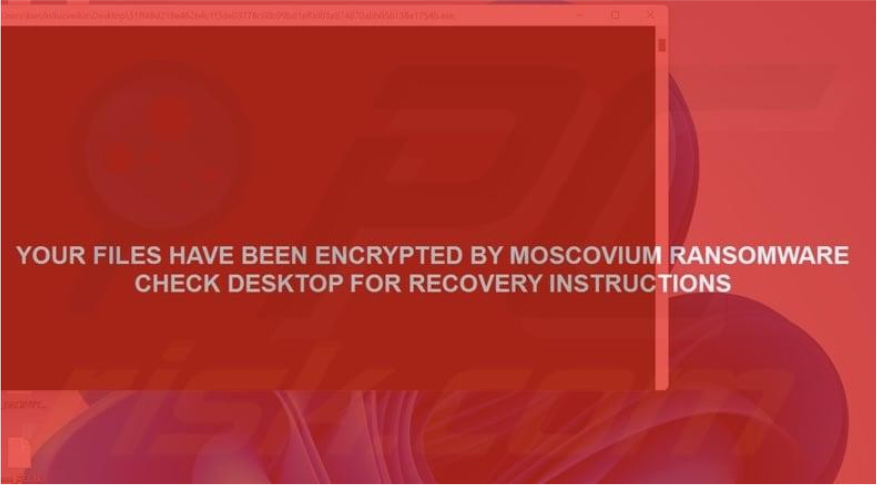
Researchers have identified a newly emerging ransomware strain dubbed Moscovium. This malware functions by encrypting user data and demanding a ransom payment in exchange for decryption. Once files are locked, Moscovium appends the “.m0sC0v1um” extension to the affected files.
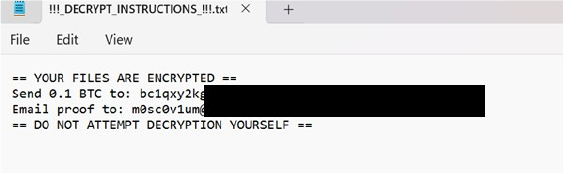
Upon completing the encryption process, the ransomware displays a full-screen notification, alerting the victim that their data has been encrypted. Additionally, it places a ransom note titled “!!!DECRYPT_INSTRUCTIONS!!!.txt” on the desktop.

The ransom note directs the victim to pay 0.1 BTC (Bitcoin) for the recovery of their files. Victims are instructed to email proof of payment to the attackers in order to receive the decryption key. The note explicitly warns users against any attempts to manually decrypt the data, implying that such actions could result in permanent data loss.
Following are the TTPs based on the MITRE Attack Framework
| Tactic | Technique ID | Technique Description |
| Execution | T1106 | Native API |
| Persistence | T1574.002 | Hijack Execution Flow:DLL Side-Loading |
| Privilege Escalation | T1055 | Process Injection |
| Privilege Escalation | T1574.002 | Hijack Execution Flow: DLL Side-Loading |
| Defense Evasion | T1027 | Obfuscated Files or Information |
| Defense Evasion | T1036 | Masquerading |
| Defense Evasion | T1055 | Process Injection |
| Defense Evasion | T1497 | Virtualization/Sandbox Evasion |
| Defense Evasion | T1562.001 | Impair Defenses: Disable or Modify Tools |
| Defense Evasion | T1574.002 | Hijack Execution Flow: DLL Side-Loading |
| Discovery | T1010 | Application Window Discovery |
| Discovery | T1082 | System Information Discovery |
| Discovery | T1083 | File and Directory Discovery |
| Discovery | T1497 | Virtualization/Sandbox Evasion |
| Command and Control | T1071 | Application Layer Protocol |
| Impact | T1486 | Data Encrypted for Impact |
Relevancy and Insights:
ETLM Assessment:
CYFIRMA’s assessment highlights that Moscovium ransomware is expected to expand globally. Ransomware strains are likely to become more stealthy and modular. We can expect increased abuse of native APIs and application-layer protocols, enabling attackers to bypass traditional defenses and exfiltrate data with greater precision while remaining undetected longer. To mitigate such threats, robust cybersecurity measures—including advanced endpoint protection, regular backups, network monitoring, and employee awareness training are essential.
Sigma Rule
title: Potentially Suspicious Desktop Background Change Via Registry tags:
– attack.defense-evasion
– attack.impact
– attack.t1112
– attack.t1491.001 logsource:
product: windows category: registry_set
detection:
selection_keys: TargetObject|contains:
– ‘Control Panel\Desktop’
– ‘CurrentVersion\Policies\ActiveDesktop’
– ‘CurrentVersion\Policies\System’ selection_values_1:
TargetObject|endswith: ‘NoChangingWallpaper’
Details: ‘DWORD (0x00000001)’ # Prevent changing desktop background
selection_values_2: TargetObject|endswith: ‘\Wallpaper’
selection_values_3:
TargetObject|endswith: ‘\WallpaperStyle’
Details: ‘2’ # Stretch filter_main_svchost:
# Note: Excluding GPO changes Image|endswith: ‘\svchost.exe’
condition: selection_keys and 1 of selection_values_* and not 1 of filter_main_* falsepositives:
– Administrative scripts that change the desktop background to a company logo or other image.
level: medium (Source: Surface web)
IOCs:
Kindly refer to the IOCs section to exercise controls on your security systems.
STRATEGIC RECOMMENDATION
MANAGEMENT RECOMMENDATION
TACTICAL RECOMMENDATION
Type: Loader | Objectives: Stealing Sensitive Information| Target Industries: Technology, Financial Services | Target Technologies: Windows OS, Browsers (Chrome, Edge, Brave, Opera)| Target Geographies: North America, Asia, and Southern Europe
CYFIRMA collects data from various forums based on which the trend is ascertained. We identified a few popular malware that were found to be distributed in the wild to launch cyberattacks on organizations or individuals.
Active Malware of the Week
This week “LegionLoader” is trending.
LegionLoader
Researchers discovered LegionLoader being delivered through a sophisticated drive-by download campaign that uses fake CAPTCHA pages and mimics Cloudflare Turnstile to deceive users. This malware ultimately aims to install a malicious browser extension without the victim’s knowledge. The campaign is part of a broader trend in which attackers target individuals searching for PDF documents on search engines, luring them with seemingly legitimate files that redirect to harmful websites or trigger malware downloads. The attacks have primarily impacted users across North America, Asia, and Southern Europe, with a strong focus on the technology and financial services sectors.
Attack Method
The attack chain begins with a drive-by download, triggered when a user searches for a specific document and unknowingly visits a malicious website. Believing they’re downloading a legitimate file, the victim is first shown a fake CAPTCHA prompt. After clicking through, they are redirected to Cloudflare Turnstile verification page, eventually landing on a site requesting permission to display notifications. This carefully crafted sequence is designed to lower suspicion while quietly setting the stage for the malware delivery.
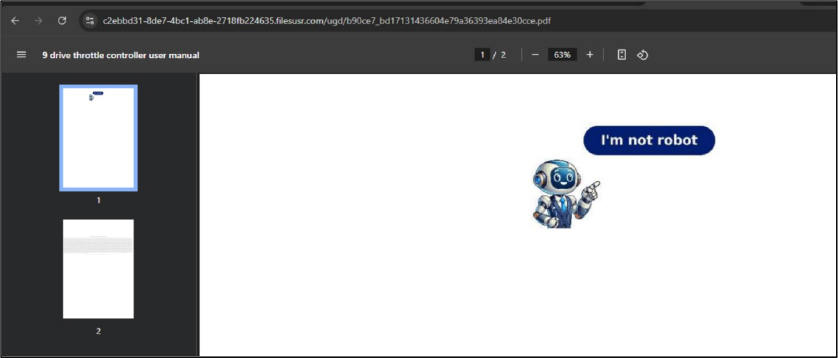
As part of the infection process, victims are prompted to enable browser notifications—an action that may seem harmless but plays a key role in allowing the attack to progress. By granting this permission, users unknowingly open the door for further malicious activity to unfold.
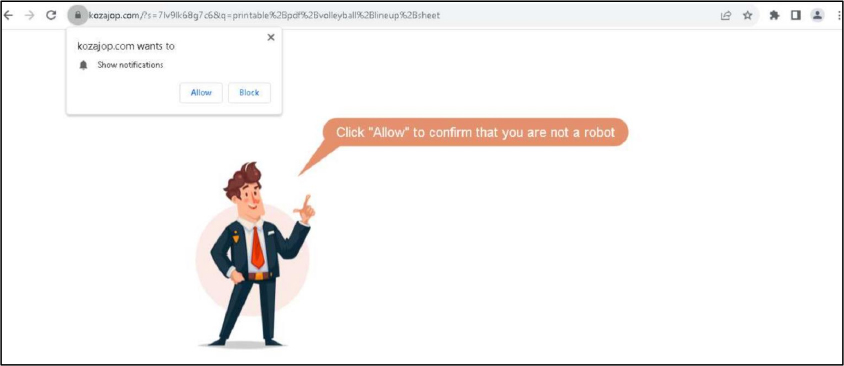
If victims choose to block the browser notification request or use a browser that doesn’t support it, they are redirected to download legitimate programs like 7-Zip or Opera. However, those who allow notifications are taken further down the infection path. After passing through another fake CAPTCHA, they arrive at a page offering instructions for downloading the document they originally searched for. The page guides them through opening the Windows Run window by pressing Win+R, pasting a pre-copied command, and executing it. This command quietly downloads an MSI file and opens its location, encouraging the victim to run it—unknowingly triggering the malware installation. The attacker’s download link is designed to work only through a specific system command, not directly through a web browser. If someone tries to open the link in a browser, they’ll see a message claiming the file has been removed for violating service rules, adding a layer of deception to hide the malware.
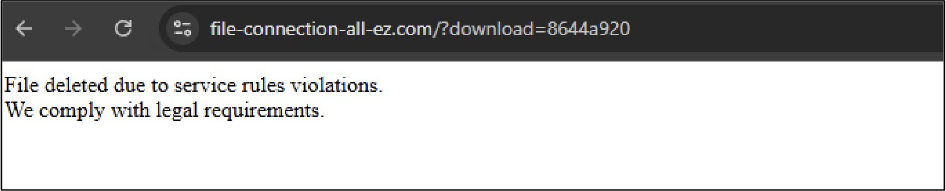
MSI analysis
When the victim runs the MSI file, it installs a program named “Kilo Verfair Tools” that carries out a series of hidden actions. To keep up appearances and avoid suspicion, one of its steps launches a legitimate PDF viewer called SumatraPDF, making it seem like the user is finally accessing the document they were looking for. Behind the scenes, however, the MSI is doing much more—it connects to an attacker-controlled site to retrieve a password, which is then used to unlock a hidden archive. A script is then executed to extract multiple components and launch a file named mksSandbox.exe, setting the stage for the next phase.
Once the mksSandbox.exe file is launched, it secretly loads a set of malicious components hidden within its folder. Among them is a disguised file pretending to be a legitimate library, which quietly kicks off the process to activate the LegionLoader malware. This process involves a series of hidden decoding steps designed not just to launch the malware but also to confuse anyone trying to analyze it. It includes unnecessary calculations and obfuscated code to further hinder analysis. As the malware progresses, it decrypts and runs a second layer of malicious code. This code cleverly mimics a legitimate system process, injecting itself into a fresh copy of “explorer.exe” to run unnoticed. From there, the malware reaches out to its server, receives an encoded PowerShell command, and executes it—setting off another chain of hidden operations. This script uses multiple decoding techniques, including character replacements, layered Base64 decoding, and XOR decryption, to quietly download the next stage of the attack.
At this point, the downloaded PowerShell script delivers a heavily encrypted payload. The script continues to unravel itself using more decryption layers, ultimately revealing and executing a final piece of malicious code. Through this multi-step approach, the attackers ensure that their malware remains concealed for as long as possible, giving them more time to carry out their objectives undetected.
Malicious browser extension
In the final stage of the attack, a decrypted PowerShell script installs a deceptive browser extension named “Save to Google Drive,” designed to mimic the legitimate version. To evade detection, the script hides key strings by storing them as byte arrays and reconstructs them at runtime. After identifying the user’s browser, the script forcefully terminates it, generates a randomly named folder, and installs the extension files. It then alters browser settings by enabling developer mode and injecting the extension’s configuration into the Secure Preferences file, ensuring the extension loads on restart.
What makes this extension particularly stealthy is its extensive access. It comes loaded with permissions that allow it to run scripts, read clipboard data, access
browsing history, extract cookies, and gather system information. The attackers don’t limit their scope—they target Chrome, Edge, Brave, and Opera alike. In addition to stealing sensitive data, the extension monitors Bitcoin activity and sends all captured information back to the attackers, all while posing as a harmless productivity tool.
INSIGHTS
ETLM ASSESSMENT
From the ETLM perspective, CYFIRMA anticipates that LegionLoader highlights a future where malware blends seamlessly into digital workflows, making it harder for employees to distinguish threats from routine interactions. As browser extensions become more powerful and deeply integrated into workplace tools, attackers may exploit them as persistent entry points, posing long-term risks to corporate data and employee privacy. The use of delayed payload activation further complicates detection, allowing malware to remain hidden until ideal conditions are met—potentially during critical business moments. Over time, campaigns like this may extend beyond their current targets and impact broader regions, especially as attackers refine their lures and language localization. This evolving threat landscape suggests that traditional defenses may no longer be sufficient, pushing organizations to adopt behavior-based monitoring and rethink browser security as a primary line of defense rather than a secondary concern.
IOCs:
Kindly refer to the IOCs Section to exercise controls on your security systems.
STRATEGIC:
MANAGEMENT:
TACTICAL RECOMMENDATIONS
Key Intelligence Signals:
From Defender to Danger: ToddyCat’s Exploitation of Security Software
Summary:
ToddyCat is an advanced persistent threat group known for its complex malware campaigns, often involving highly targeted and evasive techniques. This group utilizes multiple techniques to evade detection by common endpoint protection tools. In this case, they employed a tool called TCESB to execute their payload stealthily. The malware was detected on systems where legitimate security software was running, and it targeted systems in multiple regions, likely on a global scale.
The attack seems to be widespread and has been observed across multiple devices in different regions. The sophistication of the attack suggests that it could be aimed at high-value organizations in various sectors, likely including government, defense, and critical infrastructure.
ToddyCat’s malware tool, TCESB, used a DLL proxying technique to execute malicious code while making it appear as part of normal system processes. The malicious DLL would export functions from the legitimate version.dll library, but instead of running those functions, it would redirect the execution to the attacker’s code in the background. The tool bypassed monitoring tools by running in the context of trusted security software, which did not raise alarms. Additionally, it exploited a vulnerability in the ESET Command Line Scanner, which allowed the malicious DLL to be loaded from an insecure directory, leading to the tool’s execution.
The attackers utilized the BYOVD (Bring Your Own Vulnerable Driver) technique, exploiting a vulnerable driver (CVE-2021-36276 CVSS Score:7.8) in the system. This allowed them to modify kernel structures and disable event notification routines, thereby preventing security software from detecting the execution of malicious payloads. Once the tool was running, it checked periodically for the presence of an encrypted payload and executed it once detected, decrypting it using AES-128 encryption.
Relevancy & Insights:
In previous attacks, the ToddyCat APT group has used a variety of evasive techniques to infiltrate systems, often relying on known vulnerabilities and sophisticated methods to bypass security defenses. Their earlier tactics typically involved exploiting kernel-level vulnerabilities and leveraging legitimate system tools to execute their malicious payloads stealthily. This method is consistent with their current approach, where they use DLL proxying and the BYOVD technique to manipulate system functions without detection. The group’s ability to modify kernel structures and disable event notifications shows their continued focus on evading security monitoring tools, indicating an evolution in their use of system-level vulnerabilities. They have consistently targeted systems running trusted security solutions, such as ESET, to exploit weak points in trusted software and gain access without raising suspicion.
The regions targeted by ToddyCat in this current attack seem to align with their previous efforts. The attackers appear to target high-value entities, likely within the government, defense, or critical infrastructure sectors, like their past operations.
The global nature of the attack is implied by the detection of the malicious DLL on devices in various locations, suggesting ToddyCat’s broad targeting scope. By using sophisticated evasion techniques like exploiting vulnerabilities in security software and deploying malicious payloads through trusted security tools, ToddyCat is refining its tactics while continuing to focus on stealth and persistence in multiple regions, indicating a persistent and growing threat landscape.
ETLM Assessment:
The ToddyCat APT group is a highly skilled and persistent cyber adversary, employing advanced tactics to evade detection and maintain long-term access within compromised networks. Known for their sophisticated approach, ToddyCat often exploits vulnerabilities in trusted security tools, making it challenging for detection systems to identify their presence. Their use of complex malware like TCESB and leveraging techniques such as DLL proxying and BYOVD showcase their focus on stealth and evasion. This indicates their ability to adapt and refine their methods to bypass traditional security defenses.
ToddyCat’s attacks appear to target global regions, focusing on high-value, sensitive sectors. While specific geographic locations are not detailed in the article, the techniques suggest an intent to compromise critical infrastructure, government entities, and other industries were maintaining secrecy and avoiding detection are paramount. The group’s use of ESET Command Line Scanner vulnerabilities and the Dell DBUtilDrv2.sys driver highlights their focus on exploiting commonly used technologies in enterprise environments. ToddyCat’s malware is crafted to blend in with trusted system processes, enabling them to stealthily execute their objectives without triggering security alarms.
Strategic Recommendations:
Tactical Recommendations:
Operational Recommendations:
| MITRE FRAME WORK | ||
| Tactic | ID | Technique |
| Initial Access | T1195 | Supply Chain Compromise |
| Execution | T1059 | Command and Scripting Interpreter |
| Persistence | T1547 | Boot or Logon Autostart Execution |
| Defense Evasion | T1574.002 | Hijack Execution Flow: DLL Side- Loading |
| Defense Evasion | T1211 | Exploitation for Defense Evasion |
| Defense Evasion | T1112 | Modify Registry |
| Credential Access | T1003 | OS Credential Dumping |
| Credential Access | T1555 | Credentials from Password Stores |
| Discovery | T1083 | File and Directory Discovery |
| Collection | T1056 | Input Capture |
| Collection | T1119 | Automated Collection |
| Command and Control | T1071 | Application Layer Protocol |
| Exfiltration | T1041 | Exfiltration Over C2 Channel |
IOCs:
Kindly refer to the IOCs (Indicators of Compromise) Section to exercise controls on your security systems.
EU to fine TikTok €500 million for leaking user data to China
ByteDance Ltd., the parent company of TikTok, is facing a privacy fine exceeding €500 million ($552 million) for unlawfully transferring data of European users to China—further fuelling international scrutiny of the popular video-sharing platform. Ireland’s Data Protection Commission which is TikTok’s lead regulator in the EU is expected to issue the penalty by the end of the month. The fine follows a detailed investigation that found the Chinese firm violated the European Union’s General Data Protection Regulation (GDPR) by sending user information to China, where it was accessible to engineers, the sources said, speaking on condition of anonymity. If finalized, the fine would rank as the third-largest ever imposed under the GDPR, following previous penalties of €1.2 billion against Meta Platforms Inc. and €746 million against Amazon.com Inc. However, the final amount and timing of the decision remain subject to change.
ETLM Assessment:
The impending fine comes as ByteDance faces an April 5 deadline to find a buyer for TikTok’s US operations or see the app banned in the country. TikTok is only one facet of China’s broader information warfare strategy, which we will cover in a full report this week.
Russian hackers using drones as bait
Hackers are posing as Ukrainian drone manufacturers and government agencies to deliver information-stealing malware, according to new findings from Ukraine’s cybersecurity authorities. The campaign is primarily targeting Ukraine’s armed forces, law enforcement, and local government institutions – particularly those near the country’s eastern border with Russia. Ukraine’s Computer Emergency Response Team (CERT-UA), which has been monitoring the activity since February, has not linked the operation to any known hacking group. Instead, the threat actor is being tracked under the identifier UAC-0226. However, given the ongoing Russian war on Ukraine and the modus operandi, Russia’s involvement is clear.
The attackers used compromised email accounts, including webmail, to send phishing emails with malicious document attachments. These messages often featured subject lines or filenames referencing topics such as landmine removal, administrative penalties, drone manufacturing, or compensation for damaged property.
ETLM Assessment:
Russian hackers may be impersonating Ukrainian drone manufacturers in phishing campaigns because drones have become one of the most critical and symbolic tools in the war between Russia and Ukraine. Drones play a central role in reconnaissance, targeting, and strikes and became the most important military tool in the war while being an obscure asset just a couple of years ago. By posing as trusted drone suppliers or developers, hackers can exploit the urgency and high interest within Ukraine’s military and security forces to gain access to sensitive systems. This tactic increases the likelihood that recipients will open malicious files, believing them to contain important updates, schematics, or coordination details. With drones being such a vital asset in the conflict, especially along contested areas like the eastern border, any opportunity to disrupt their deployment or gather intelligence on their use would be a high-value objective for Russian cyber operatives. The same MO can and likely will be used on any of the countries supporting Ukraine in its defense.
The Qilin Ransomware Impacts Dhoot Transmission
Summary:
From the External Threat Landscape Management (ETLM) Perspective, CYFIRMA observed in an underground forum that a company from India; Dhoot Transmission(https[:]//www[.]dhoottransmission[.]com/), was compromised by Qilin Ransomware. Dhoot Transmission is a manufacturer and supplier of automotive components to OEMs. The company manufactures wire harness, electronics, copper wire enamelling, tooling components, stamping components, moulding components, and cable components for two-wheeler and four-wheelers. The compromised data consists of confidential and sensitive information related to the organization. The compromised data totals approximately 319.00 GB and includes 2,28,438 files.

Relevancy & Insights:
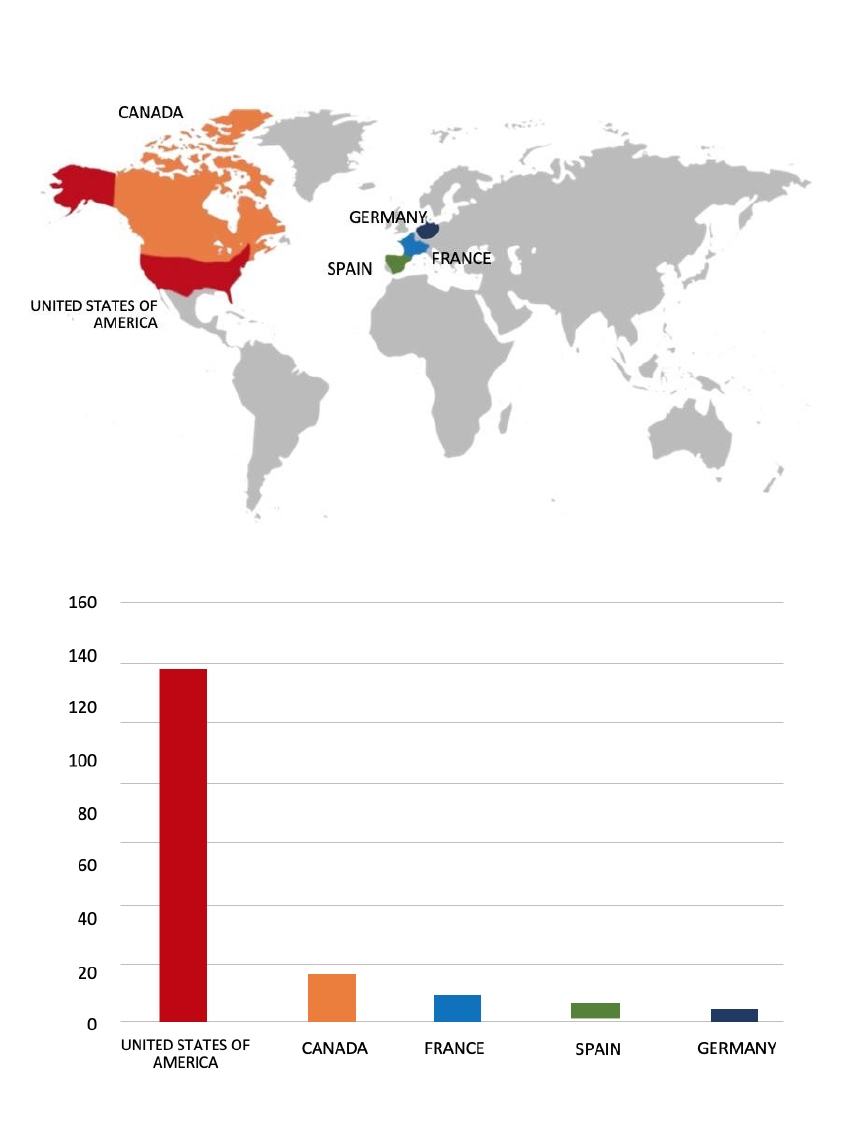
ETLM Assessment:
According to CYFIRMA’s assessment, Qilin ransomware poses a significant threat to organizations of all sizes. Its evolving tactics, including double extortion (data encryption and leak threats), cross-platform capabilities (Windows and Linux, including VMware ESXi), and focus on speed and evasion make it a particularly dangerous actor.
The Sarcoma Ransomware Impacts Fujifilm Singapore
Summary:
From the External Threat Landscape Management (ETLM) Perspective, CYFIRMA observed in an underground forum that a company from Singapore, Fujifilm Singapore(https[:]//fujifilm[.]com.sg/), was compromised by Sarcoma Ransomware. Fujifilm Singapore is a subsidiary of FUJIFILM Asia Pacific Pte. Ltd., serving as the regional headquarters for the Asia Pacific region. The company offers a diverse range of products and services across various sectors, including medical systems, graphic systems, recording media, and industrial products. The compromised data includes confidential and sensitive information belonging to the organization.

Relevancy & Insights:
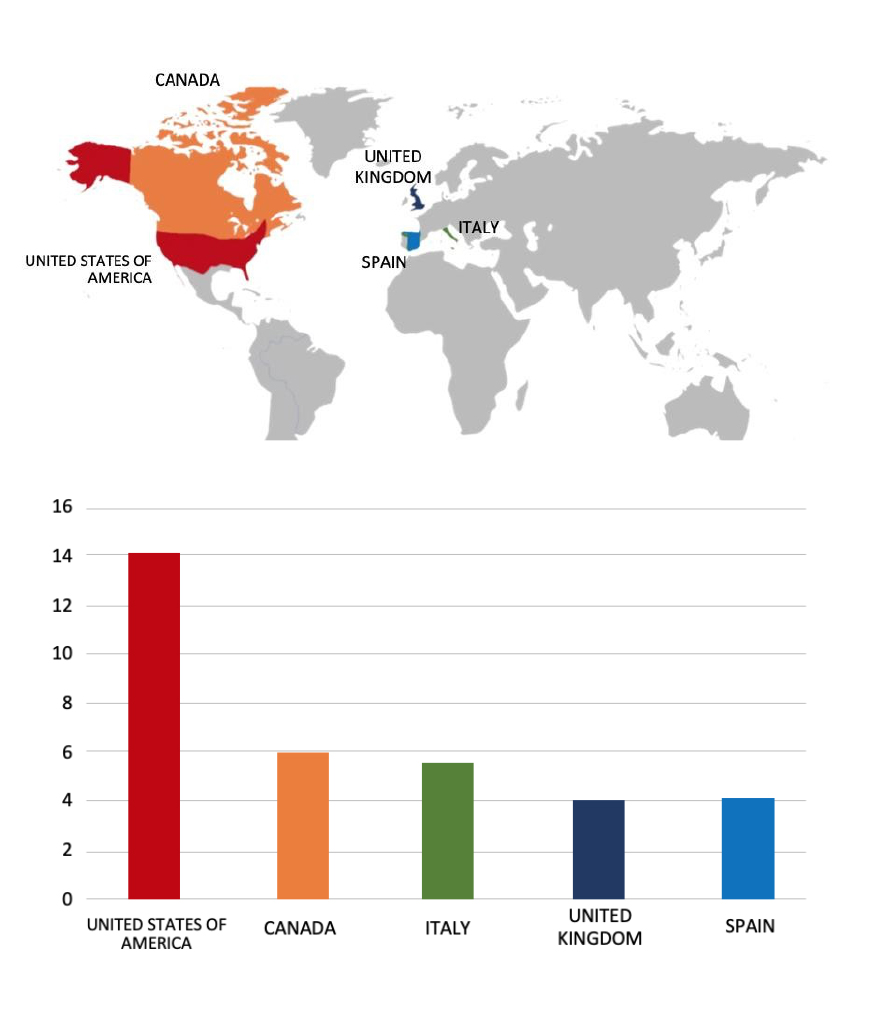
ETLM Assessment:
Based on recent assessments by CYFIRMA, Sarcoma ransomware is rapidly becoming a significant threat due to its aggressive tactics and increasing victim count. Organizations must remain vigilant and proactive in their cybersecurity efforts to mitigate risks associated with this evolving threat landscape.
Vulnerability in c-ares
Relevancy & Insights:
The vulnerability exists due to a use-after-free error within the read_answers() function.
Impact:
A remote attacker can send specially crafted ICMP UNREACHABLE packets to the application, trigger a use-after-free error, and execute arbitrary code on the system.
Affected Products:
https[:]//github[.]com/c-ares/c-ares/security/advisories/GHSA-6hxc- 62jh-p29v
Recommendations:
Monitoring and Detection: Implement monitoring and detection mechanisms to identify unusual system behavior that might indicate an attempted exploitation of this vulnerability.
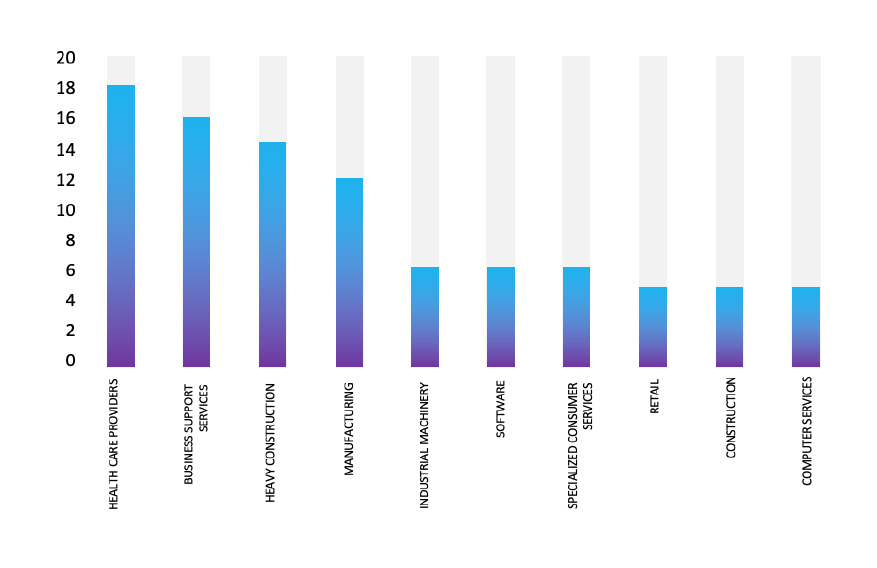
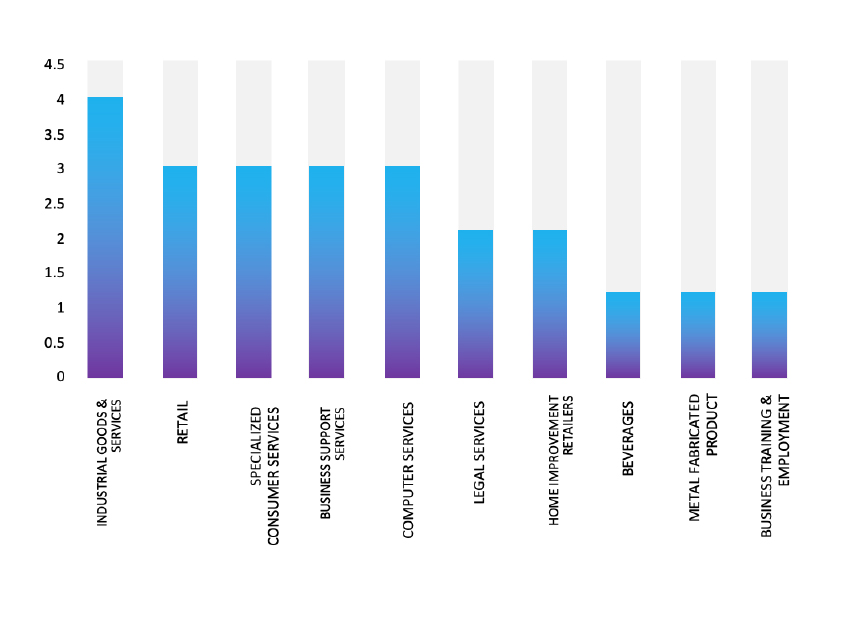
TOP 5 AFFECTED TECHNOLOGIES OF THE WEEK
This week, CYFIRMA researchers have observed significant impacts on various technologies, due to a range of vulnerabilities. The following are the top 5 most affected technologies.
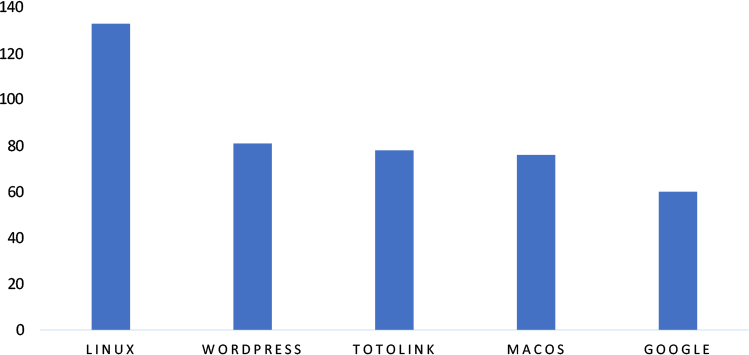
ETLM Assessment
Vulnerability in c-ares can pose significant threats to user privacy and security. This can impact various industries globally, including technology, telecommunications, finance, and beyond. Ensuring the security of c-ares is crucial for maintaining the integrity and protection of users’ data worldwide. Therefore, addressing these vulnerabilities is essential to safeguarding asynchronous DNS request handling in applications, preventing DNS-based attacks, and ensuring secure network communications across different geographic regions and sectors.
Killsec Ransomware attacked and published the data of Lupin Limited
Summary:
Recently, we observed that Killsec Ransomware attacked and published the data of Lupin Limited (https[:]//www[.]lupin[.]com/) on its dark web website. Lupin Limited, based in India, is a global pharmaceutical company that develops and sells branded and generic medicines, biotech products, and APIs in over 100 markets. The data leak, following the ransomware attack, encompasses secret health information pertaining to their clients and patients.
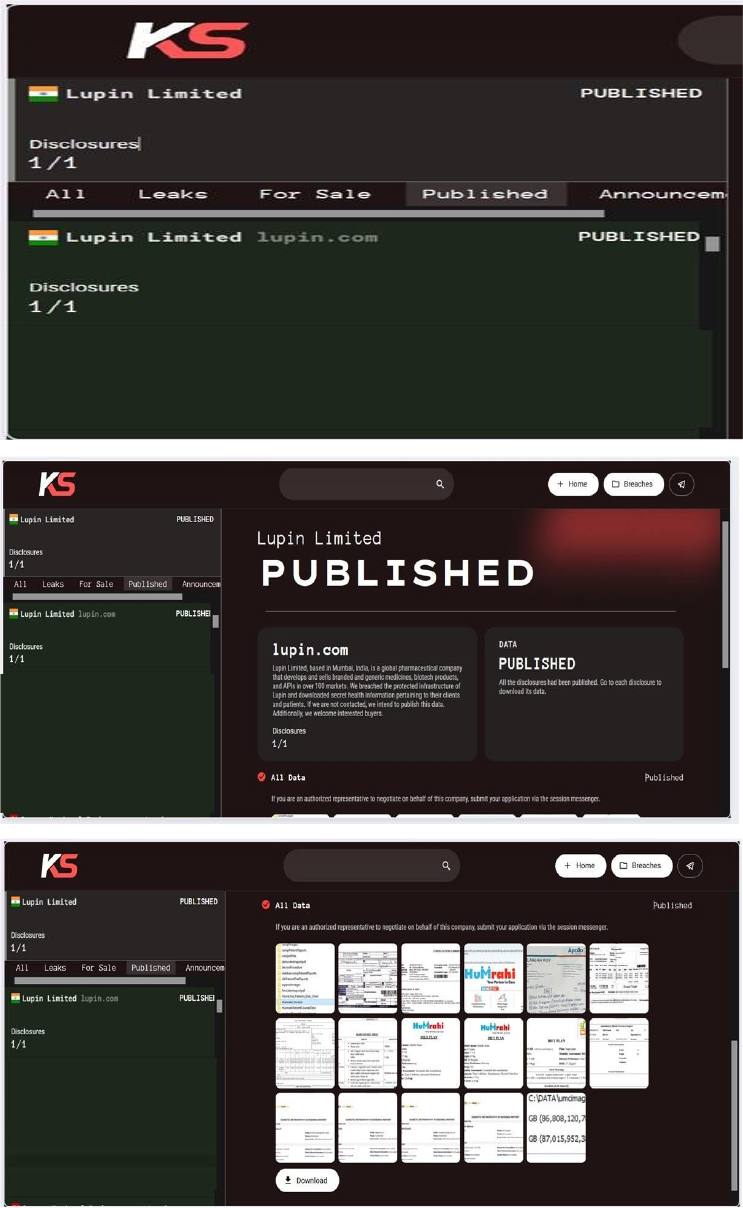
Relevancy & Insights:
ETLM Assessment:
The emergence and evolution of KillSec’s Ransomware-as-a-Service (RaaS) platform represents a concerning development in the cybercrime landscape. By lowering the technical barrier to entry, this RaaS model allows less skilled individuals to engage in sophisticated ransomware attacks, potentially leading to an increase in such incidents globally.
According to CYFIRMA’s assessment, the KillSec ransomware group is expected to continue targeting a wide range of industries worldwide. Their advanced tactics, such as exploiting website vulnerabilities and conducting credential theft, make them a significant threat to organizations with inadequate security measures in place.
Indonesian Ministry of Transportation Data Advertised on a Leak Site
Summary:
The CYFIRMA Research team observed a data leak related to the Indonesian Ministry of Transportation(https[:]//dephub[.]go[.]id/) in an underground forum. A threat actor on a dark web forum claims to have leaked the personal data of 14,271 employees of the Ministry of Transportation of the Republic of Indonesia. The post, which includes a link to a downloadable file, asserts that the data has been distributed for free as an act of defiance against the government.
According to the alleged claims, the leaked dataset is in CSV format, has a total size of 6.51MB, and is linked to the official website of the ministry. The post also includes inflammatory statements against the Indonesian government, suggesting a possible political or ideological motive behind the supposed breach. The breach has been linked to a threat actor identified as “BanyuwangiXploit.”

Thailand Post Data Advertised on a Leak Site
Summary:
The CYFIRMA Research team observed a data sale related to the Thailand Post (https[:]//www[.]thailandpost[.]co[.]th/) in an underground forum. A threat actor has allegedly claimed on a dark web forum, stating that they have obtained and are selling a database belonging to Thailand Post. The post allegedly contains sensitive customer data, including names, phone numbers, email addresses, transaction records, and other personally identifiable information.
According to the forum post, the database contains approximately 19 million records. The seller has provided a sample of the data, though they claim that many columns contain null values. The forum post states that while the dataset may not be fully populated with all information fields, it still holds a significant amount of customer data that could be exploited by malicious actors.
The threat actor has allegedly listed the stolen database for sale in CSV format and has claimed they are willing to provide the full dataset after a transaction is completed. They have also mentioned that the dataset includes information such as birth dates, addresses, membership details, and transaction histories. The breach has been linked to a threat actor identified as ” vebxpert.”
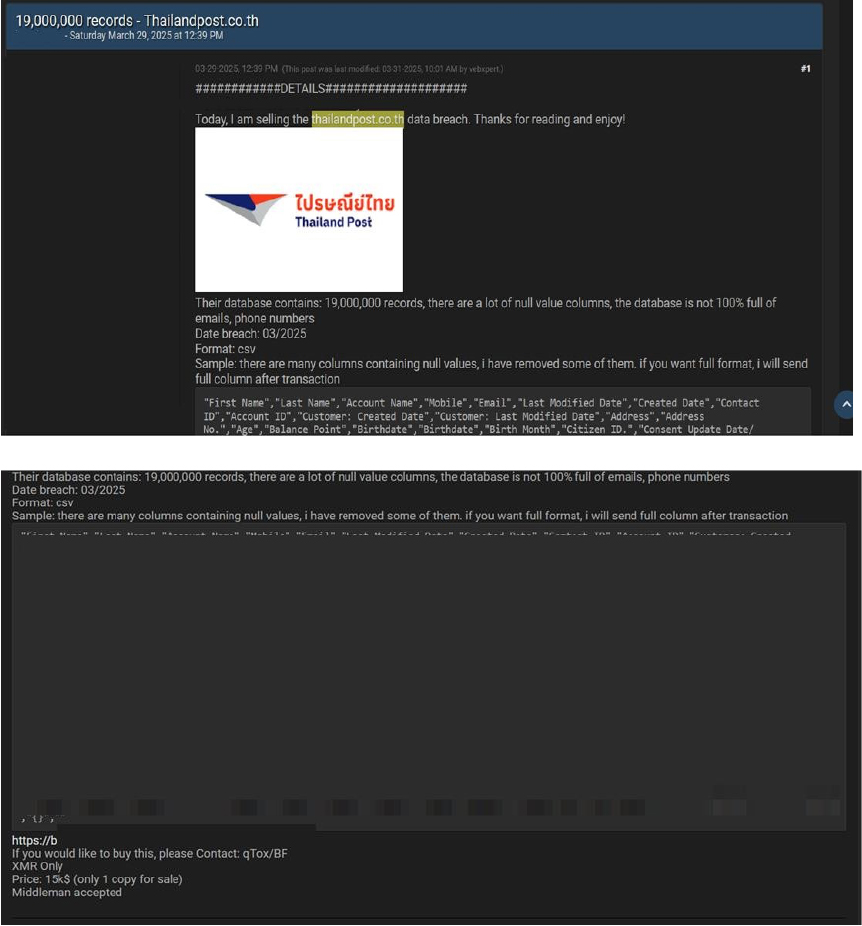
Relevancy & Insights:
Financially motivated cybercriminals are continuously scouring for exposed and vulnerable systems and applications to exploit. A significant number of these malicious actors congregate within underground forums, where they discuss cybercrime and trade stolen digital assets. Operating discreetly, these opportunistic attackers target unpatched systems or vulnerabilities in applications to illicitly gain access and steal valuable data. Subsequently, the pilfered data is advertised for sale within underground markets, where it can be acquired, repurposed, and utilized by other malicious actors in further illicit activities.
ETLM Assessment:
The threat actor known as “Vebxpert” has been associated with several data breaches, with credible indicators pointing to their involvement in unauthorized access to sensitive data and subsequent attempts to monetize this information via dark web marketplaces. The emergence and activities of “Vebxpert” highlight the ongoing and adaptive nature of cyber threats originating from underground forums. This case reinforces the critical need for organizations to maintain a strong security posture, continuously monitor for indicators of compromise (IOCs), and implement proactive threat detection and response strategies to safeguard confidential data from malicious actors.
Recommendations: Enhance the cybersecurity posture by:
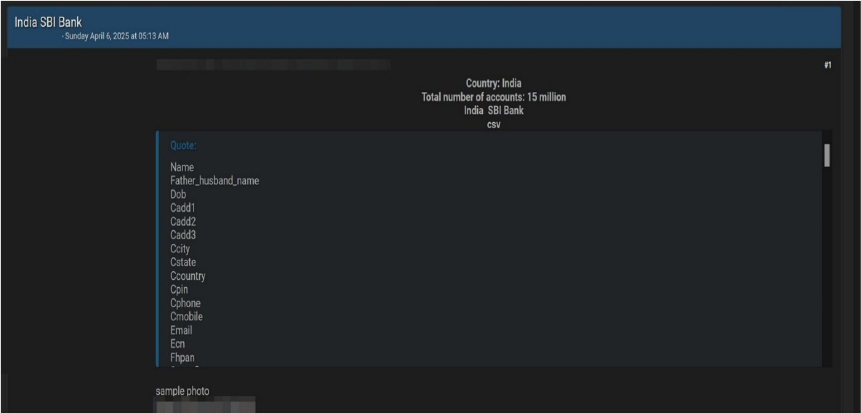
The CYFIRMA Research team observed that a threat actor claims to have leaked the sensitive personal info of 15M SBI Bank customers, including DOBs, contact info & PANs.
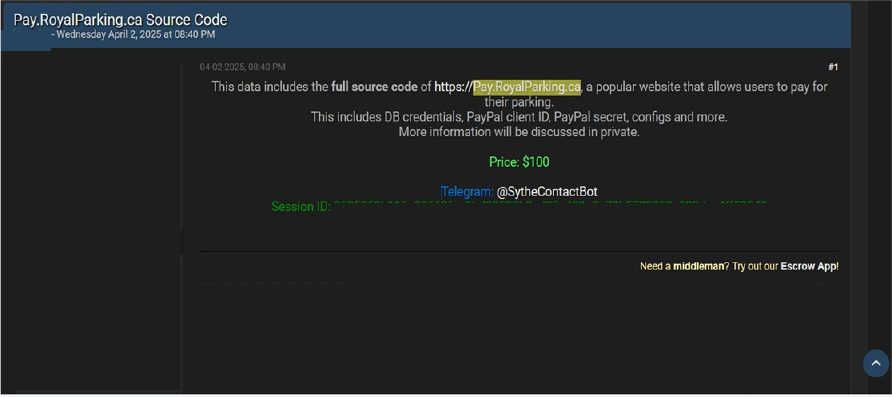
The CYFIRMA Research team observed that a threat actor has allegedly claimed to offer the full source code of a widely used platform for parking payments. The threat actor behind the post is reportedly selling the data for $100, claiming that it includes database credentials, PayPal client information, configuration files, and other sensitive details.
According to the forum post, further details about the alleged breach can be discussed privately via Telegram. While the authenticity of the claims remains unverified, the mention of PayPal credentials and database access raises concerns about potential security risks for users of the platform.
STRATEGIC RECOMMENDATIONS
MANAGEMENT RECOMMENDATIONS
TACTICAL RECOMMENDATIONS
Please find the Geography-Wise and Industry-Wise breakup of cyber news for the last 5 days as part of the situational awareness pillar.
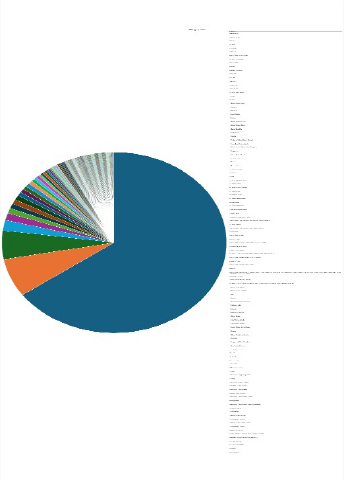
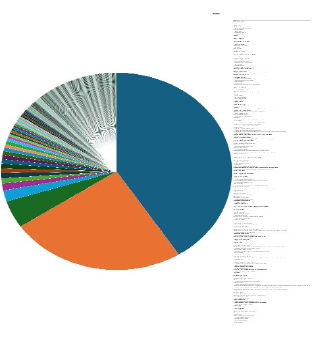
For situational awareness intelligence and specific insights mapped to your organisation’s geography, industry, and technology, please access DeCYFIR.