



CYFIRMA Research and Advisory Team would like to highlight ransomware trends and insights gathered while monitoring various forums. This includes multiple – industries, geography, and technology – that could be relevant to your organization.
Type: Ransomware
Target Technologies: MS Windows
Introduction
CYFIRMA Research and Advisory Team has found Qilra Ransomware while monitoring various underground forums as part of our Threat Discovery Process.
Qilra Ransomware
Qilra is a newly discovered ransomware strain recently identified by researchers. Upon infecting a victim’s system, Qilra encrypts files, appends the “.qilra” extension to the affected files, and drops a ransom note titled “RESTORE-MY-FILES.TXT”.
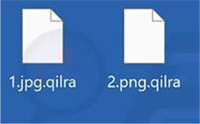
The ransom note informs the victim that their important files have been encrypted and exfiltrated. According to the attackers, only they possess the means to decrypt the stolen data. If the victim fails to comply, the decryption key will be permanently destroyed, and the stolen data will be publicly released.
The note includes an email address for contact and provides a unique decryption ID. It also offers to decrypt one file for free as proof. Furthermore, the message imposes a 72- hour deadline for the victim to initiate communication and complete the ransom payment.
Following are the TTPs based on the MITRE Attack Framework
| Tactic | Technique ID | Technique Name |
| Execution | T1059 | Command and Scripting Interpreter |
| Execution | T1129 | Shared Modules |
| Persistence | T1542.003 | Pre-OS Boot: Bootkit |
| Persistence | T1574.002 | Hijack Execution Flow: DLL Side-Loading |
| Privilege Escalation | T1055 | Process Injection |
| Privilege Escalation | T1574.002 | Hijack Execution Flow: DLL Side-Loading |
| Defense Evasion | T1014 | Rootkit |
| Defense Evasion | T1027 | Obfuscated Files or Information |
| Defense Evasion | T1027.002 | Obfuscated Files or Information: Software Packing |
| Defense Evasion | T1036 | Masquerading |
| Defense Evasion | T1055 | Process Injection |
| Defense Evasion | T1070.004 | Indicator Removal: File Deletion |
| Defense Evasion | T1070.006 | Indicator Removal: Timestomp |
| Defense Evasion | T1202 | Indirect Command Execution |
| Defense Evasion | T1497.001 | Virtualization/Sandbox Evasion: System Checks |
| Defense Evasion | T1542.003 | Pre-OS Boot: Bootkit |
| Defense Evasion | T1564.001 | Hide Artifacts: Hidden Files and Directories |
| Defense Evasion | T1564.003 | Hide Artifacts: Hidden Window |
| Defense Evasion | T1574.002 | Hijack Execution Flow: DLL Side-Loading |
| Credential Access | T1003 | OS Credential Dumping |
| Credential Access | T1552.001 | Unsecured Credentials: Credentials in Files |
| Discovery | T1057 | Process Discovery |
| Discovery | T1082 | System Information Discovery |
| Discovery | T1083 | File and Directory Discovery |
| Discovery | T1497.001 | Virtualization/Sandbox Evasion: System Checks |
| Discovery | T1518.001 | Software Discovery: Security Software Discovery |
| Collection | T1005 | Data from Local System |
| Collection | T1114 | Email Collection |
| Command and Control | T1071 | Application Layer Protocol |
| Impact | T1485 | Data Destruction |
| Impact | T1486 | Data Encrypted for Impact |
| Impact | T1490 | Inhibit System Recovery |
| Impact | T1496 | Resource Hijacking |
Relevancy and Insights:
ETLM Assessment:
CYFIRMA’s assessment, based on currently available data, indicates that Qilra ransomware is likely to evolve with heightened stealth capabilities and broader targeting of critical infrastructure sectors. Future variants may incorporate zero-day exploits or exploit supply chain channels to increase distribution efficiency. Its observed use of anti-debugging techniques, WMI abuse, and shadow copy deletion points to a trajectory of more aggressive defense evasion and persistence methods. Given its emphasis on data exfiltration, Qilra is expected to further refine its extortion strategies, posing greater risks to sensitive data.
Sigma rule:
title: Delete shadow copy via WMIC threatname:
behaviorgroup: 18
classification: 0 mitreattack:
logsource:
category: process_creation product: windows
detection: selection:
CommandLine:
– ‘*wmic*shadowcopy delete*’ condition: selection
level: critical
(Source: Surface Web)
IOCs:
Kindly refer to the IOCs section to exercise control of your security systems.
STRATEGIC RECOMMENDATION
MANAGEMENT RECOMMENDATION
TACTICAL RECOMMENDATION
Type: Trojan | Objectives: Operational Disruption | Target Technology: Linux OS | Target Geographies: Asia, Europe, and the Americas
CYFIRMA collects data from various forums based on which the trend is ascertained. We identified a few popular malware that were found to be distributed in the wild to launch cyberattacks on organizations or individuals.
Active Malware of the week
This week “XorDDoS” is trending.
XorDDoS
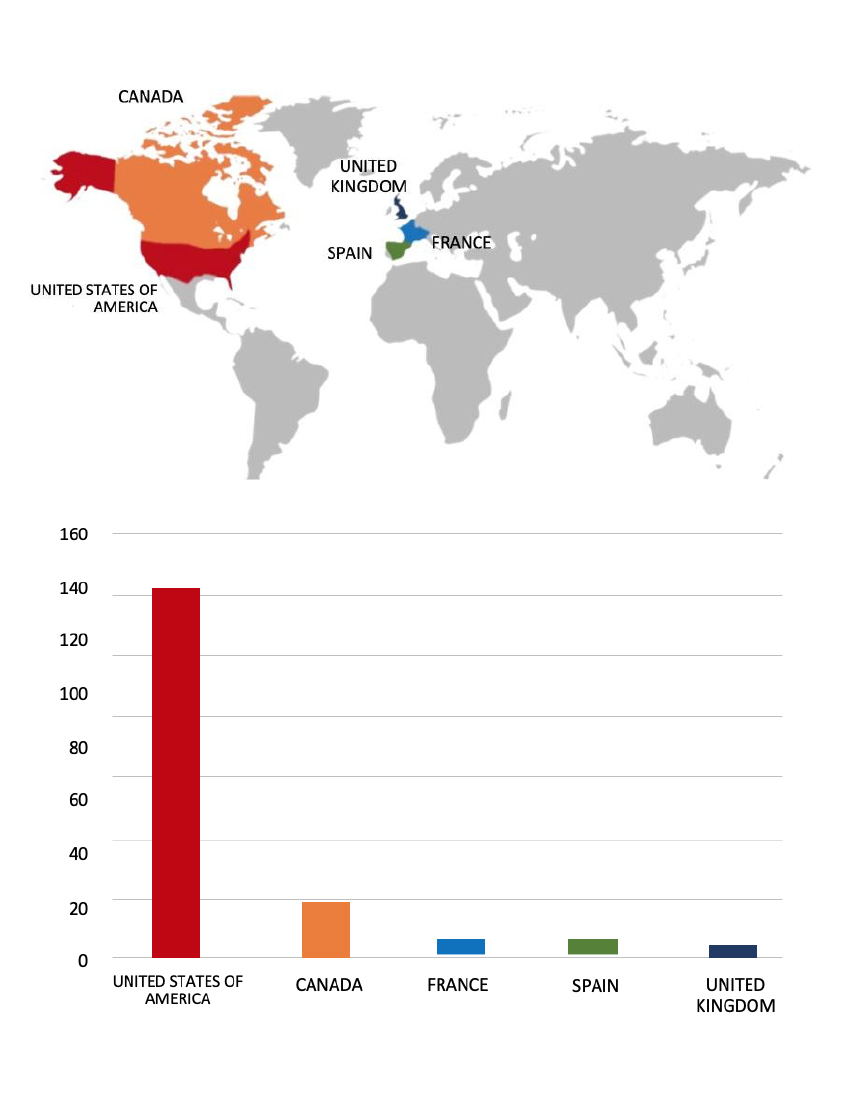
Researchers discovered that the XorDDoS malware, a known threat since 2014, has been actively spreading across the globe between November 2023 and February 2025. This Linux-targeting malware hijacks systems and turns them into bots used for disruptive DDoS attacks. A newly upgraded variant of the XorDDoS controller, referred to as the “VIP” version, has played a key role in enabling large-scale operations through an expanded botnet infrastructure. A striking detail in the latest findings reveals that more than 70 percent of these attacks were directed at the United States during this period. Still, the campaign has left its mark globally, affecting systems in countries across Asia, Europe, and the Americas. Despite its age, XorDDoS continues to be a powerful tool in the hands of its operators. Researchers strongly believe the group behind this operation is Chinese speaking, based on language indicators found within the malware’s infrastructure. As the malware maintains its momentum, organizations worldwide remain at risk from these persistent and widespread attacks.
Attack Method
XorDDoS spreads by launching brute-force attacks over SSH, targeting Linux systems with weak or default credentials. It repeatedly attempts various username and password combinations until it gains access to a vulnerable server. Once inside, the malware quickly establishes persistence by installing scripts that ensure it runs automatically every time the system restarts. These scripts are embedded within the malware itself and are designed to help it avoid detection and maintain control over the compromised machine.
After securing access and ensuring it remains active on the infected device, XorDDoS proceeds to decrypt its internal configuration using a XOR key. This step reveals a list of remote servers—either IP addresses or URLs—that the malware contacts to receive further instructions. These servers, part of the command-and-control infrastructure, play a crucial role in coordinating attacks by delivering commands and managing the botnet. The infected system then becomes part of a larger network of compromised devices, ready to be used in disruptive DDoS operations. This organized method of communication and control reflects the increasingly structured nature of these campaigns.
To expand its reach and streamline command execution, XorDDoS uses a component called the controller binder, which links individual controllers to a central control hub. By injecting into a specified process on the host machine, attackers can manage multiple sub-controllers at once, sending DDoS commands to all of them simultaneously. This centralized approach makes large-scale attacks easier to coordinate and more efficient. The central controller itself includes features that let attackers fine-tune their operations—for example, adjusting SYN packet size or launching round-robin style attacks, where each infected host takes turns sending packets. However, the tool is designed to work only with specific versions of the sub- controller, limiting compatibility with older underground variants. Notably, the developer behind this tool even embedded their instant messaging contact and references to other versions being sold, reinforcing the idea that this is part of a commercial offering aimed at other cybercriminals.
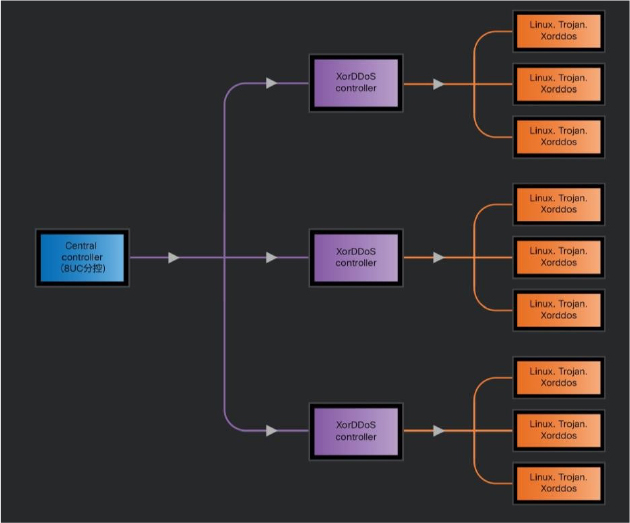
Following the control flow, a closer look at how XorDDoS operates behind the scenes reveals the level of coordination involved in its campaigns. Once the malware is installed on a compromised system, it sends encrypted “phone home” data to report back to its controller, including system details and version identifiers. This marks the start of a controlled communication loop between the infected device and the sub-controller. After the initial handshake, the sub-controller receives instructions from the main controller using a unique header that confirms the authenticity of the command. This system mirrors a basic client-server model, ensuring only legitimate commands are executed.
Meanwhile, the central controller uses a controller binder to inject itself into the sub- controller, taking full command. Once this link is active, the sub-controller returns key system information in plain text—such as IP address and hostname—back to the central controller. Every command exchanged between the controllers and the infected devices is tracked with an incrementing message ID, making it easier for attackers to coordinate tasks like launching or stopping a SYN DDoS attack or targeting specific IP addresses. This structured system not only strengthens the malware’s efficiency but also highlights how far the XorDDoS ecosystem has evolved into a well-oiled, large-scale attack network.
INSIGHTS
ETLM ASSESSMENT
From the ETLM perspective, CYFIRMA anticipates that XorDDoS represents a growing shift toward more structured and scalable attack models that could significantly disrupt organizations and employees in the near future. As these campaigns become more coordinated and commercialized, we may see DDoS attacks used not just for disruption but as cover for deeper intrusions, putting additional pressure on security teams to detect multi-layered threats. Employees across departments could face more frequent service outages, delayed operations, or tighter internal protocols, all stemming from the growing unpredictability of such campaigns. If the tools behind XorDDoS continue to circulate in underground markets, even less-skilled actors could launch impactful attacks, broadening the target pool and forcing organizations to elevate cyber resilience from a technical concern to a business-wide priority.
IOCs:
Kindly refer to the IOCs Section to exercise controls on your security systems.
STRATEGIC:
MANAGEMENT:
TACTICAL RECOMMENDATIONS
Key Intelligence Signals:
Decoding Mustang Panda’s Arsenal: ToneShell, StarProxy, PAKLOG, CorKLOG & SplatCloak
SUMMARY:
The threat actor behind this campaign is Mustang Panda, a China-sponsored espionage group well known for targeting government entities, military groups, NGOs, and minority organizations. This specific activity is focused on Myanmar, with tools discovered on machines belonging to a targeted organization within the region. However, Mustang Panda has also been observed targeting victims in East Asia and Europe. The campaign shows the group’s continued evolution and sophistication in deploying malware and evading detection.
In this operation, researchers identified several new variants of the backdoor ToneShell, along with a new lateral movement tool named StarProxy. ToneShell variants implement updates such as custom GUID creation, rolling XOR key encryption, and FakeTLS protocol spoofing to mimic legitimate TLS communication. These variants support commands for file operations, reverse shells, and DLL injection using shellcode. StarProxy, on the other hand, facilitates network proxying through compromised machines to bypass firewalls and maintain access to otherwise unreachable targets. It uses XOR-based encryption, FakeTLS headers, and custom C2 protocols for covert communication.
The group also utilizes various tactics and techniques to stay undetected. A key tactic is DLL sideloading, where malicious payloads are bundled with legitimate signed executables inside RAR or ZIP archives. These are used to load malicious DLLs like ToneShell or StarProxy without triggering endpoint defenses. The malware further employs custom encryption, command-line configurations, random seed generation, and dynamic shellcode injection to obfuscate behavior and resist analysis.
Researchers also observed two newly developed keyloggers—PAKLOG and CorKLOG—as well as a sophisticated EDR evasion driver named SplatCloak. These tools were discovered alongside previously documented Mustang Panda malware such as ToneShell and StarProxy, and share similarities in techniques, including API hashing and obfuscation methods.
Mustang Panda is known for frequently updating its malware toolkit and deploying it in targeted attacks.
The keyloggers serve different roles: PAKLOG monitors both keystrokes and clipboard data using high-level Windows APIs, encoding the data before writing it locally. It lacks built-in exfiltration capabilities. CorKLOG, on the other hand, uses RC4 encryption with a 48- character key to encrypt keylog data and achieves persistence by creating scheduled tasks or installing itself as a service depending on privilege level. CorKLOG includes a multi-stage XOR-based decryption routine for configuration data. Both keyloggers are deployed using DLL sideloading techniques via archives containing legitimate binaries.
SplatCloak, deployed by a dropper named SplatDropper, is a Windows kernel driver designed to disable kernel-level notification callbacks used by Windows Defender and Kaspersky, including routines for process, thread, and image creation. It uses techniques such as control flow flattening, mixed boolean arithmetic, and manual resolution of API addresses from system modules. SplatCloak identifies callback routines associated with security tools by analyzing their code signing certificates and disables or removes them to avoid detection.
These tools reflect Mustang Panda’s continued evolution in developing stealthy and persistent malware for targeted espionage campaigns.
Relevancy & Insights:
The recent Mustang Panda campaign demonstrates a clear evolution in both tactics and tooling compared to their previous operations. Historically, the group relied on malware like PlugX and earlier versions of ToneShell for initial access and control, primarily leveraging basic obfuscation, simple keyloggers, and standard DLL sideloading techniques. In contrast, the current campaign showcases significant advancements, including enhanced persistence via scheduled tasks and services, sophisticated keyloggers like Paklog and CorKLOG, and a powerful kernel driver (SplatCloak) capable of disabling EDR routines of security products like Windows Defender and Kaspersky. The use of custom FakeTLS communication, rolling XOR encryption, and dynamic GUID-based victim tracking indicate a strategic shift toward stealthier, more resilient intrusions. Additionally, the re-use of familiar delivery methods, such as signed binaries and RAR archives, reflects Mustang Panda’s continued reliance on tried-and-tested entry techniques while upgrading the payload sophistication.
ETLM Assessment:
Mustang Panda, a well-known China-sponsored espionage group, is attributed to this campaign based on infrastructure overlap and the reuse of malware families like ToneShell, StarProxy, and PlugX. Known for targeting geopolitical entities, Mustang Panda has historically focused on espionage operations against Southeast Asian countries, particularly Myanmar, as well as NGOs and religious groups. In this campaign, their activity aligns with previously observed behavior, aiming at surveillance and intelligence collection. The group’s consistent use of RAR archives containing legitimately signed binaries and malicious DLLs highlights their preference for DLL sideloading as an infection vector.
The threat actor’s latest toolkit demonstrates a technological escalation. Tools such as Paklog and CorKLOG (advanced keyloggers), SplatDropper (a stealthy DLL loader), and SplatCloak (a Windows kernel driver used to disable EDR mechanisms) mark a significant upgrade. These tools showcase Mustang Panda’s ability to bypass modern defenses using RC4 encryption, XOR-based obfuscation, API hashing, and privilege-aware persistence mechanisms. The use of revoked driver certificates and stealthy evasion techniques illustrates their focus on avoiding detection and maintaining long-term access in targeted environments.
Strategic Recommendations:
Tactical Recommendations
Operational Recommendations
| MITRE FRAMEWORK | ||
| Tactic | ID | Technique |
| Initial Access | T1566.001 | Phishing: Spear phishing Attachment |
| Execution | T1059 | Command and Scripting Interpreter |
| Execution | T1129 | Shared Modules |
| Persistence | T1574.002 | Hijack Execution Flow: DLL Side- Loading |
| Defense Evasion | T1574.002 | Hijack Execution Flow: DLL Side- Loading |
| Defense Evasion | T1218.011 | System Binary Proxy Execution : Rundll32 |
| Defense Evasion | T1497 | Virtualization/Sandbox Evasion |
| Credential Access | T1056.001 | Input Capture: Keylogging |
| Discovery | T1082 | System Information Discovery |
| Discovery | T1614.001 | System Location Discovery: System Language |
| Collection | T1056.001 | Input Capture: Keylogging |
| Collection | T1115 | Clipboard Data |
| Command and Control | T1071 | Application Layer Protocol |
| Command and Control | T1573 | Encrypted Channel |
| Exfiltration | T1041 | Exfiltration Over C2 Channel |
| Exfiltration | T1048 | Exfiltration Over Alternative Protocol |
IOCs:
Kindly refer to the IOCs (Indicators of Compromise) Section to exercise controls on your security systems.
Trump economic policy fallout: potential for underinvestment in cyber security
Concerns stem from unpredictable U.S. trade policies, with tariffs on Chinese goods reaching 124% as of April 12. But it’s the lack of clarity that truly rattles businesses, since most business leaders want predictability first to schedule out long term capital investments and right now, no one has a clear read on what’s coming.
The recession risk has jumped to 45%, according to a recent poll among investment firms, with most of them considering recession a given should the paused tariffs go into effect at the end of the 90-day pause. FED Chair Jerome Powell acknowledged the challenge of balancing inflation and employment, warning of a scenario where the Fed’s dual goals of keeping inflation and unemployment low are in conflict.
During COVID-19, cybersecurity rebounded quickly, driven by remote work and digital consumption. A new downturn, driven by tariffs, may not directly hit cybersecurity—many firms provide services, not goods—but tight budgets could still slow spending. Uncertainty could pressure cyber security budgets.
ETLM Assessment:
As the Trump administration rolls out a chaotic tariff policy (a subject to a future CYFIRMA report)—announcing steep tariffs only to pause most for 90 days— economists are increasingly predicting a recession within a year. Business leaders are pulling back amid rising inflation and uncertainty. Cybersecurity, however, may be more resilient. Analysts call the sector a “defensive” play, with many services mandated by regulation and risk management, yet some organizations might face hard budgetary choices with some managers preferring to cut cybersecurity first.
That would be a critical mistake, as many more cyberattacks typically occur during economic downturns and we are moving into a more chaotic geopolitical environment, where predatory states like China, Iran, or North Korea will use the resources of the state to aid their flailing business. Security should be viewed as vital for continuity and competitiveness and cutting cyber security budgets in a volatile environment (both economically and geopolitically) would be a mistake.
The Qilin Ransomware Impacts Algas Engineering Pte Ltd
Summary:
From the External Threat Landscape Management (ETLM) Perspective, CYFIRMA observed in an underground forum that a company from Singapore; Algas Engineering Pte Ltd (http[:]//www[.]algas[.]com[.]sg), was compromised by Qilin Ransomware. Algas Engineering Pte Ltd is a Singapore-based company specializing in gas pipe installation and related services for residential and commercial developments. The compromised data consists of confidential and sensitive information related to the organization.

Relevancy & Insights:
ETLM Assessment:
According to CYFIRMA’s assessment, Qilin ransomware poses a significant threat to organizations of all sizes. Its evolving tactics, including double extortion (data encryption and leak threats), cross-platform capabilities (Windows and Linux, including VMware ESXi), and focus on speed and evasion make it a particularly dangerous actor.
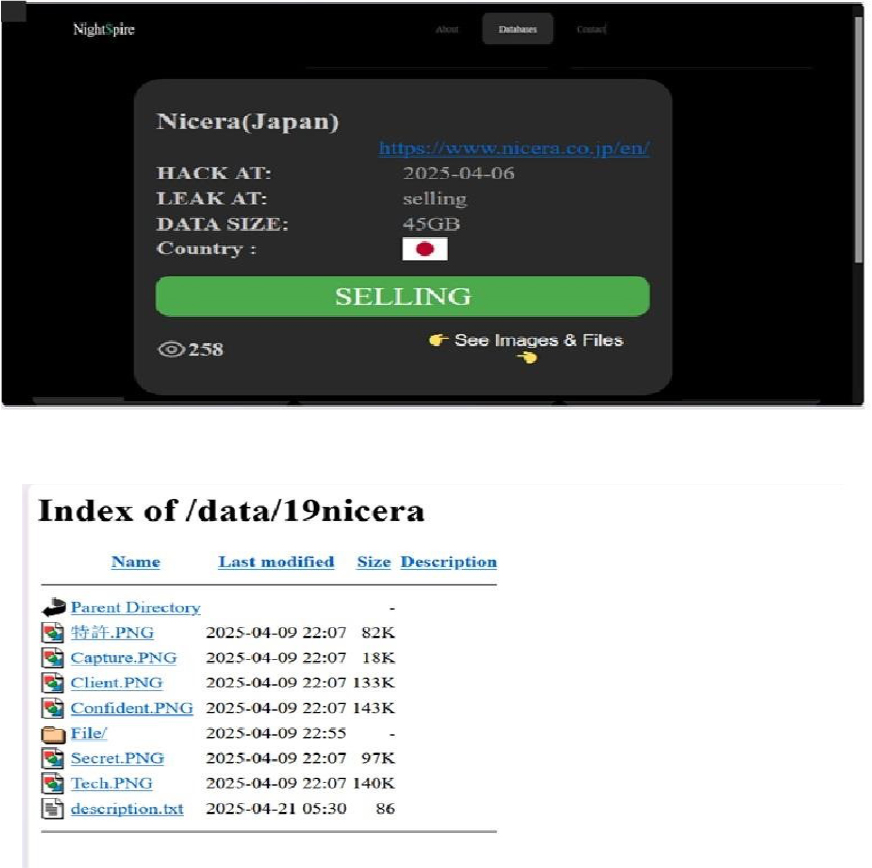
The NightSpire Ransomware Impacts Nicera
Summary:
From the External Threat Landscape Management (ETLM) Perspective, CYFIRMA observed in an underground forum that a company from Japan; Nicera (https[:]//www[.]nicera[.]co[.]jp/), was compromised by NightSpire Ransomware. Nicera specializes in the development, manufacturing, and sale of advanced ceramic products and materials used across various industries. The compromised data consists of confidential and sensitive information related to the organization. The total size of the compromised data is approximately 45 GB.
Relevancy & Insights:
ETLM Assessment:
According to CYFIRMA’s assessment, NightSpire is a new ransomware group that emerged in early 2025, marking itself as a formidable player in the rapidly evolving ransomware landscape. Despite its recent appearance, NightSpire has already gained attention for its aggressive tactics and well-structured operations.
Vulnerability in IBM i
Relevancy & Insights:
The vulnerability exists due to incorrect profile swapping in an OS command.
Impact:
A remote privileged user can use the command to elevate privileges to gain root access to the host operating system.
Affected Products:
https[:]//www[.]ibm[.]com/support/pages/node/7231025
Recommendations:
Monitoring and Detection: Implement monitoring and detection mechanisms to identify unusual system behavior that might indicate an attempted exploitation of this vulnerability.
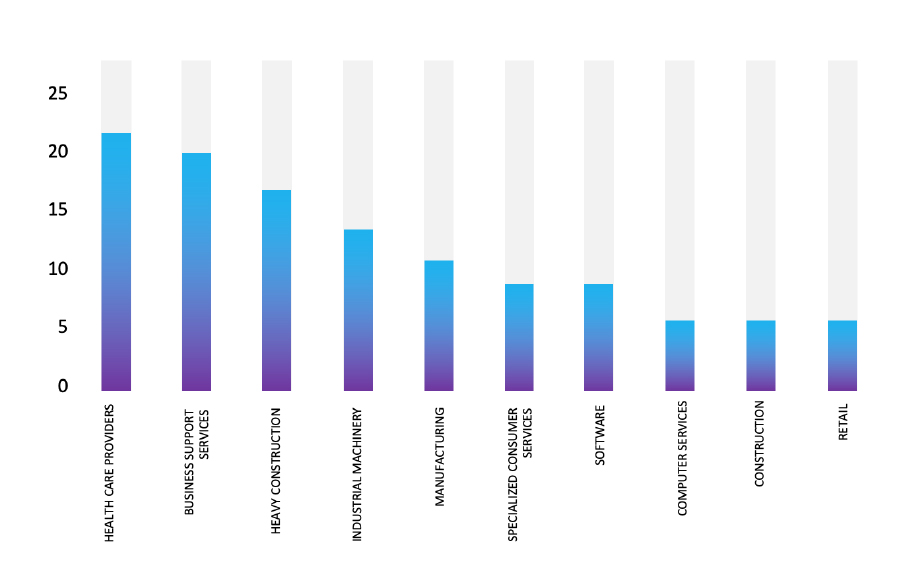
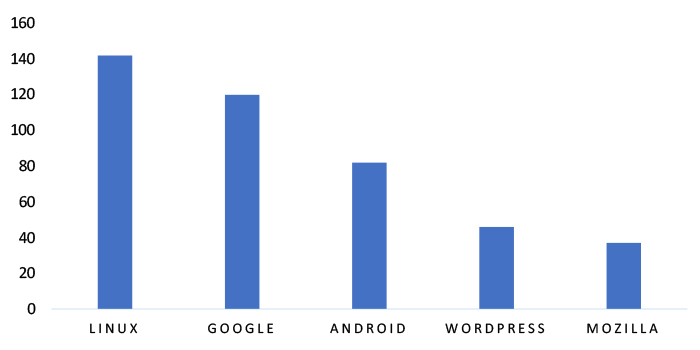
TOP 5 AFFECTED TECHNOLOGIES OF THE WEEK
This week, CYFIRMA researchers have observed significant impacts on various technologies, due to a range of vulnerabilities. The following are the top 5 most affected technologies.
ETLM Assessment
Vulnerability in IBM i can pose significant threats to user privacy and security. This can impact various industries globally, including finance, healthcare, manufacturing, and government sectors. Ensuring the security of IBM i is crucial for maintaining the integrity and protection of users’ data worldwide. Therefore, addressing these vulnerabilities is essential to safeguarding enterprise-level computing environments, including database management, application hosting, and secure transaction processing, across different geographic regions and sectors.
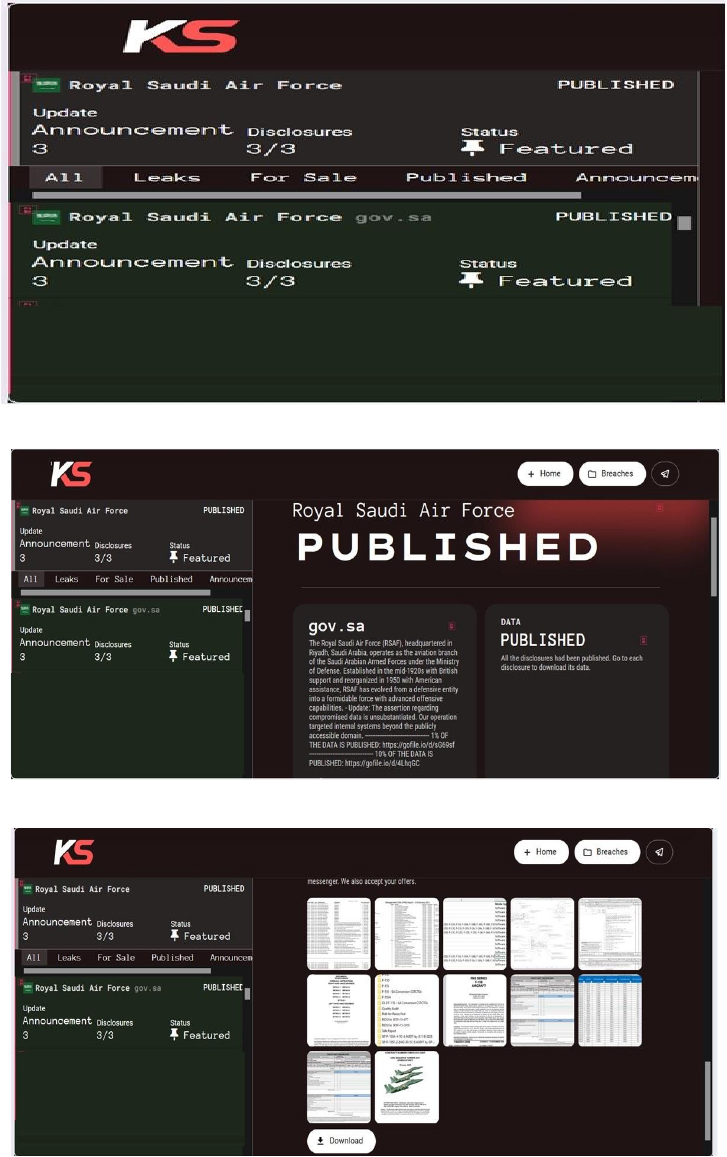
Killsec Ransomware attacked and published the data of the Royal Saudi Air Force
Summary:
Recently, we observed that Killsec Ransomware attacked and published the data of the Royal Saudi Air Force(https[:]//www[.]mod[.]gov[.]sa) on its dark web website. The Royal Saudi Air Force (RSAF) is the aerial warfare branch of the Saudi Arabian Armed Forces, operating under the Ministry of Defense. The data leak, following the ransomware attack, encompasses sensitive and confidential records originating from the organizational database.
Relevancy & Insights:
ETLM Assessment:
The emergence and evolution of KillSec’s Ransomware-as-a-Service (RaaS) platform represents a concerning development in the cybercrime landscape. By lowering the technical barrier to entry, this RaaS model allows less skilled individuals to engage in sophisticated ransomware attacks, potentially leading to an increase in such incidents globally.
According to CYFIRMA’s assessment, the KillSec ransomware group is expected to continue targeting a wide range of industries worldwide. Their advanced tactics, such as exploiting website vulnerabilities and conducting credential theft, make them a significant threat to organizations with inadequate security measures in place.
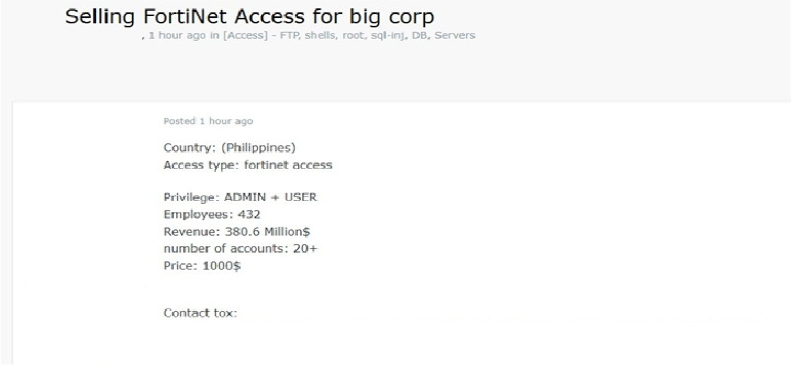
Philippines Corp Access Advertised on a Leak Site
Summary: The CYFIRMA Research team observed that a threat actor is offering Fortinet access to a major company in the Philippines. The details are as follows:
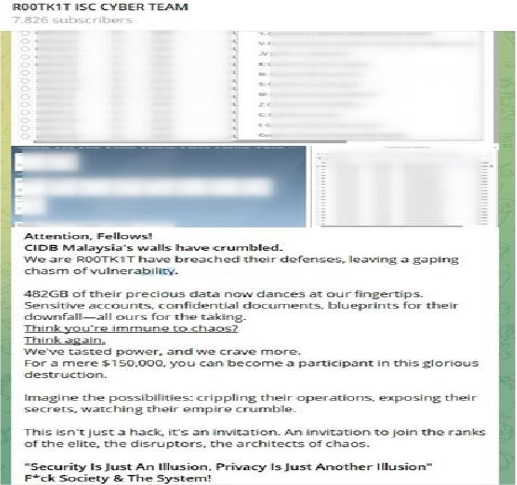
The Construction Industry Development Board (CIDB) Malaysia Data Advertised on a Leak Site
Summary:
The CYFIRMA Research team observed that the threat group R00TK1T claims to have breached the Construction Industry Development Board (CIDB) Malaysia(https[:]//www[.]cidb[.]gov[.]my/), compromising 482GB of sensitive data. The stolen information reportedly includes confidential documents, sensitive accounts, and internal blueprints.
Relevancy & Insights:
Financially motivated cybercriminals are continuously scouring for exposed and vulnerable systems and applications to exploit. A significant number of these malicious actors congregate within underground forums, where they discuss cybercrime and trade stolen digital assets. Operating discreetly, these opportunistic attackers target unpatched systems or vulnerabilities in applications to illicitly gain access and steal valuable data. Subsequently, the pilfered data is advertised for sale within underground markets, where it can be acquired, repurposed, and utilized by other malicious actors in further illicit activities.
ETLM Assessment:
R00TK1T ISC CYBER TEAM represents a significant and volatile hacktivist threat actor characterized by its public-facing operations and geopolitically motivated attacks. The group executes disruptive campaigns targeting a diverse range of sectors, including critical infrastructure (telecommunications, aviation), government entities, and multinational corporations across various geographic locations. From a defensive standpoint, R00TK1T highlights the importance of a layered security posture. Continuous monitoring of the external attack surface, prompt patching of identified vulnerabilities, implementation of strong access controls, and monitoring threat intelligence feeds for specific mentions or related TTPs are crucial mitigation strategies.
Recommendations: Enhance the cybersecurity posture by:
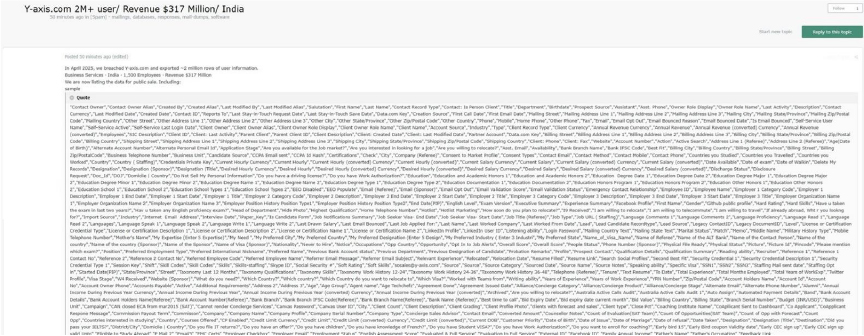
The CYFIRMA Research team observed that a threat actor claims to have breached Y-axis[.]com in April 2025 and is now offering over 2 million user records for sale, including extensive personal, employment, and immigration-related data.
Company: Y-axis[.]com
Sample Fields Include:
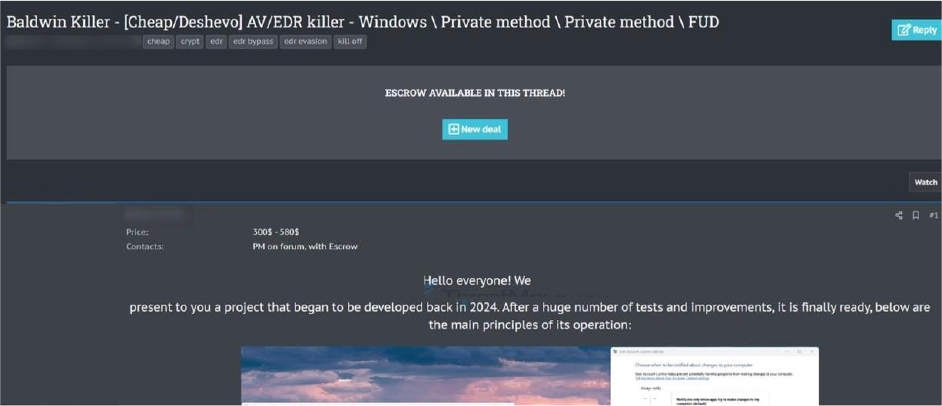
The CYFIRMA Research team observed that a threat actor has announced the release of a sophisticated malware tool called “Baldwin Killer”. The tool bypasses major antivirus and EDR solutions such as Windows Defender, Kaspersky, Bitdefender, and Avast. It allegedly features memory injection, a special UAC bypass technique, Ring0 rootkit capabilities for stealth, early boot autostart, and SmartScreen circumvention via DLL sideloading.
STRATEGIC RECOMMENDATIONS
MANAGEMENT RECOMMENDATIONS
TACTICAL RECOMMENDATIONS
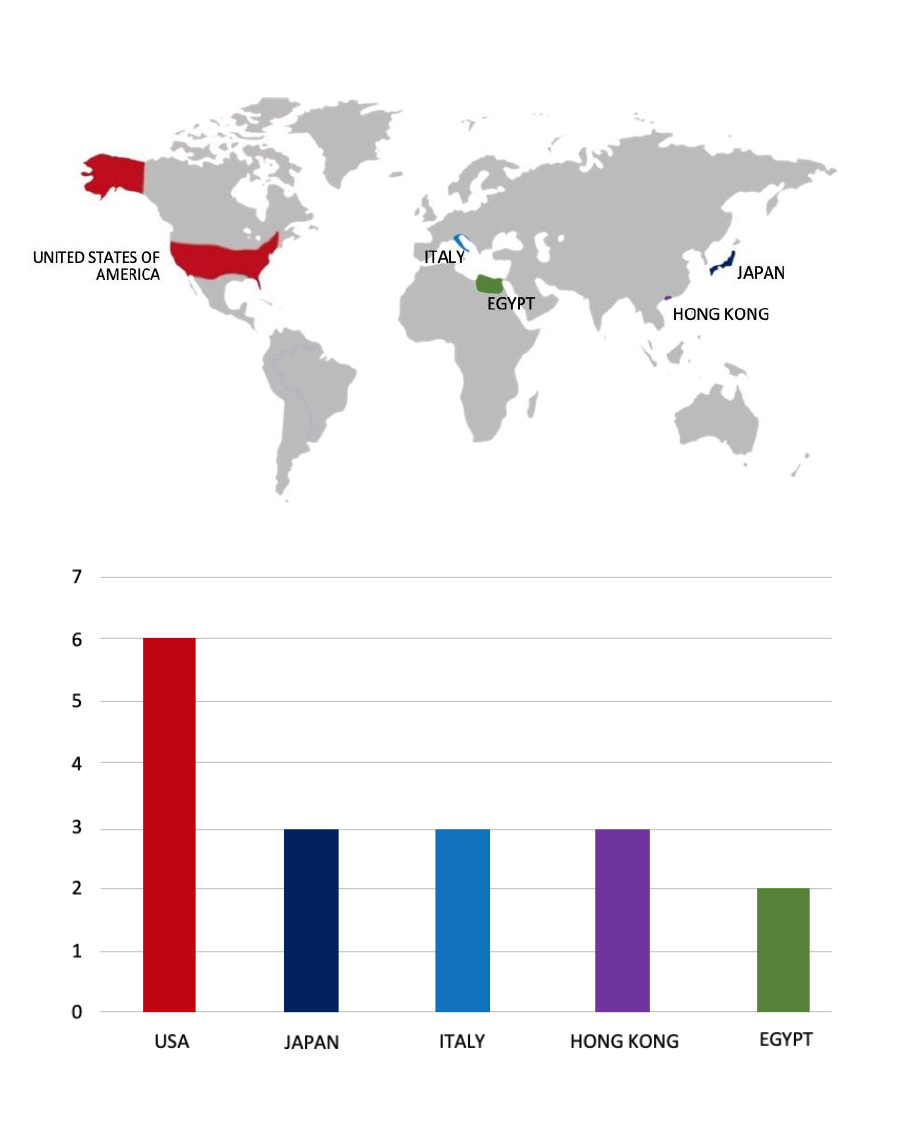
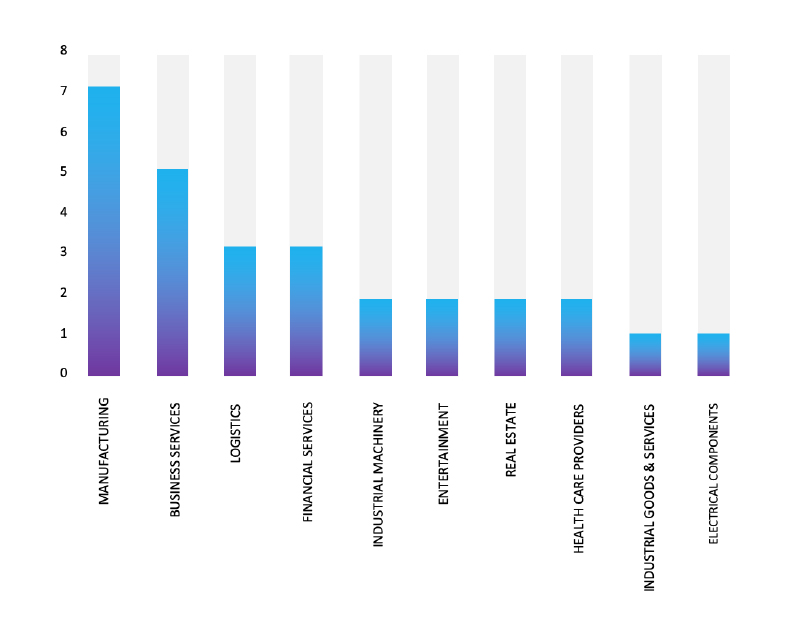
Please find the Geography-Wise and Industry-Wise breakup of cyber news for the last 5 days as part of the situational awareness pillar.
For situational awareness intelligence and specific insights mapped to your organisation’s geography, industry, and technology, please access DeCYFIR