



CYFIRMA Research and Advisory Team would like to highlight ransomware trends and insights gathered while monitoring various forums. This includes multiple – industries, geography, and technology – that could be relevant to your organization.
Type: Ransomware
Target Technologies: MS Windows
Introduction
CYFIRMA Research and Advisory Team has found Aptlock Ransomware while monitoring various underground forums as part of our Threat Discovery Process.
Aptlock Ransomware
Researchers have recently identified Aptlock, a newly discovered ransomware that encrypts files, appends the “.aptlock” extension, modifies the victim’s wallpaper, and delivers a ransom note titled “read_me_to_access.txt.”
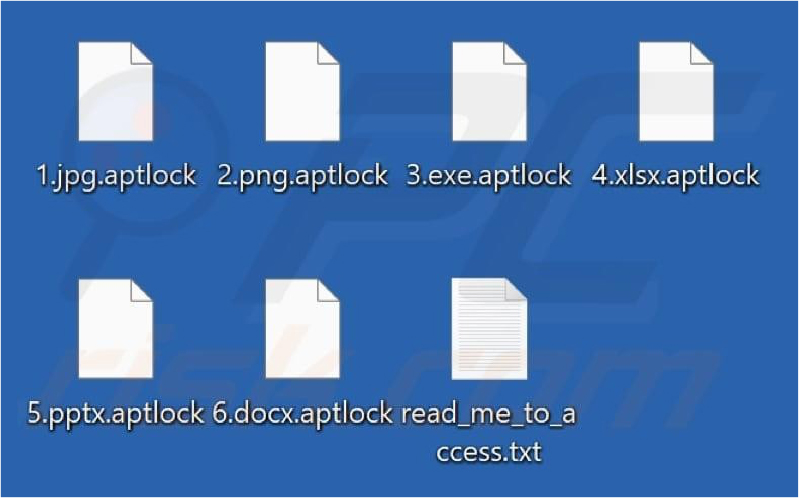
Screenshot of files encrypted by ransomware (Source: Surface Web)
The ransom note informs victims that critical data from their company’s network has been exfiltrated and transferred to the attackers’ servers. It claims that the threat actors can fully restore the affected systems and data, warning that failure to initiate contact within 72 hours will result in the release and destruction of the compromised information.
If no agreement is reached within five days, further consequences are threatened. To engage in negotiations, victims are instructed to download the Tor Browser and use provided credentials to access a secure chat. The ransom note asserts that the attackers will facilitate decryption, system restoration, and offer data security guidance in exchange for payment, further stating that compliance will ensure the breach remains confidential.
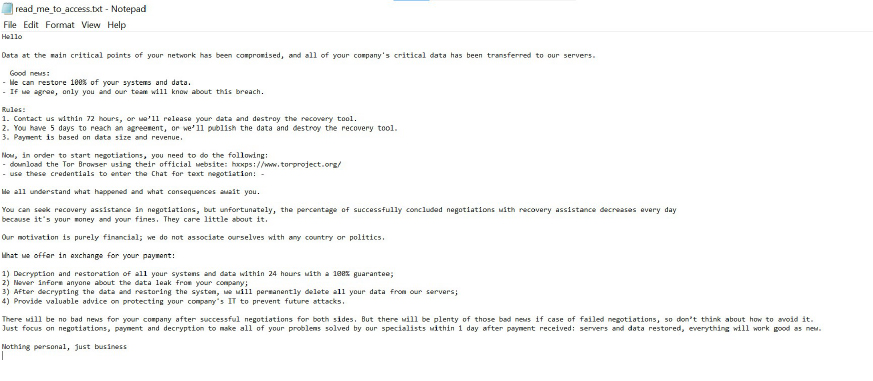
Appearence of Aptlock’s text file (“read_me_to_access.txt”):(Source: Surface Web)
Screenshot of Aptlock’s desktop wallpaper (Source: Surface Web)
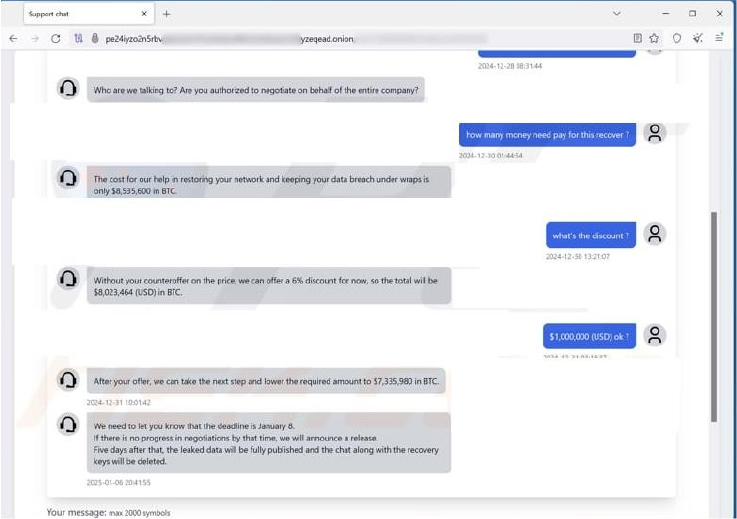
Screenshot of Aptlock’s chat:(Source: Surface Web)
Following are the TTPs based on the MITRE Attack Framework
| Tactic | ID | Technique/SubTechnique |
| Execution | T1047 | Windows Management Instrumentation |
| Execution | T1059 | Command and Scripting Interpreter |
| Execution | T1106 | Native API |
| Execution | T1129 | Shared Modules |
| Persistence | T1542.003 | Pre-OS Boot: Bootkit |
| Persistence | T1543.003 | Create or Modify System Process: Windows Service |
| Persistence | T1547.001 | Boot or Logon Autostart Execution: Registry Run Keys / Startup Folder |
| Persistence | T1574.002 | Hijack Execution Flow: DLL Side-Loading |
| Privilege Escalation | T1055 | Process Injection |
| PrivilegeEscalation | T1543.003 | Create or Modify System Process: Windows Service |
| Privilege Escalation | T1547.001 | Boot or Logon Autostart Execution: Registry Run Keys / Startup Folder |
| Privilege Escalation | T1548 | Abuse Elevation Control Mechanism |
| Privilege Escalation | T1574.002 | Hijack Execution Flow: DLL Side-Loading |
| DefenseEvasion | T1014 | Rootkit |
| DefenseEvasion | T1027.002 | Obfuscated Files or Information: Software Packing |
| DefenseEvasion | T1027.005 | Obfuscated Files or Information: Indicator Removal from Tools |
| DefenseEvasion | T1027.009 | Obfuscated Files or Information: Embedded Payloads |
| DefenseEvasion | T1036 | Masquerading |
| DefenseEvasion | T1055 | Process Injection |
| DefenseEvasion | T1070.004 | Indicator Removal: File Deletion |
| DefenseEvasion | T1112 | Modify Registry |
| DefenseEvasion | T1202 | Indirect Command Execution |
| DefenseEvasion | T1222 | File and Directory Permissions Modification |
| DefenseEvasion | T1542.003 | Pre-OS Boot: Bootkit |
| DefenseEvasion | T1548 | Abuse Elevation Control Mechanism |
| DefenseEvasion | T1562.001 | Impair Defenses: Disable or Modify Tools |
| DefenseEvasion | T1564.001 | Hide Artifacts: Hidden Files and Directories |
| DefenseEvasion | T1564.003 | Hide Artifacts: Hidden Window |
| DefenseEvasion | T1574.002 | Hijack Execution Flow: DLL Side-Loading |
| CredentialAccess | T1003 | OS Credential Dumping |
| CredentialAccess | T1552.001 | Unsecured Credentials: Credentials In Files |
| CredentialAccess | T1555.003 | Credentials from Password Stores: Credentials from Web Browsers |
| Discovery | T1007 | System Service Discovery |
| Discovery | T1012 | Query Registry |
| Discovery | T1057 | Process Discovery |
| Discovery | T1082 | System Information Discovery |
| Discovery | T1083 | File and Directory Discovery |
| Discovery | T1135 | Network Share Discovery |
| Discovery | T1518.001 | Software Discovery: Security Software Discovery |
| Collection | T1005 | Data from Local System |
| Collection | T1113 | Screen Capture |
| Collection | T1119 | Automated Collection |
| Command and Control | T1071 | Application Layer Protocol |
| Impact | T1485 | Data Destruction |
| Impact | T1486 | Data Encrypted for Impact |
| Impact | T1489 | Service Stop |
| Impact | T1490 | Inhibit System Recovery |
| Impact | T1491 | Defacement |
| Impact | T1496 | Resource Hijacking |
Relevancy and Insights:
ETLM Assessment:
CYFIRMA assesses that Aptlock ransomware’s substantial ransom demands and profit-driven objectives suggest a likely expansion across industries and regions, targeting organizations with the financial capacity to comply. Effective mitigation strategies include advanced endpoint protection, regular data backups, continuous network monitoring, and comprehensive employee cybersecurity training.
Sigma Rule
title: Delete shadow copy via WMIC threatname:
behaviorgroup: 18
classification: 0 mitreattack:
logsource:
category: process_creation product: windows
detection: selection:
CommandLine:
– ‘*wmic*shadowcopy delete*’ condition: selection
level: critical
(Source: Surface web)
IOCs:
Kindly refer to the IOCs section to exercise controls on your security systems.
STRATEGIC RECOMMENDATION
MANAGEMENT RECOMMENDATION
TACTICAL RECOMMENDATION
Type: Trojan | Objectives: Stealing financial information, Data exfiltration | Target Industries: Financial Institutions, Banks | Target Geography: Brazil | Target Technology: Windows OS
CYFIRMA collects data from various forums based on which the trend is ascertained. We identified a few popular malware that were found to be distributed in the wild to launch cyberattacks on organizations or individuals.
Active Malware of the week
This week “Coyote” is trending
Coyote
Coyote is a .NET banking Trojan designed to infiltrate financial applications and steal sensitive user data. Researchers uncovered its multi-stage attack chain, which begins with LNK files embedded with PowerShell commands that execute malicious scripts and establish connections with remote servers. Primarily targeting Brazilian users, Coyote is capable of compromising more than 70 financial applications and websites. Once activated, it can log keystrokes, capture screenshots, and deploy phishing overlays, making it a formidable threat to banking security.
Attack Method
The exact delivery method of the Coyote Trojan remains unclear. The Trojan is usually triggered by an LNK file, which runs a PowerShell command to connect to a remote server and initiate the next stage of the attack. This process involves retrieving and executing a script from an external server, which sets the stage for the malware’s further actions.
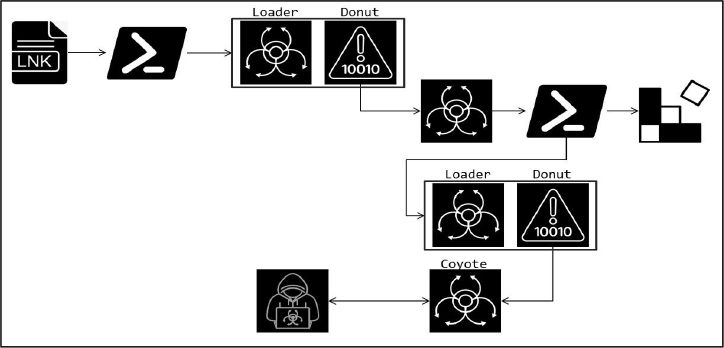
Fig: Infection chain
Researchers examined several malicious files by focusing on the “Machine ID” embedded in the LNK files. This unique identifier revealed important details about the system where the file originated. By analyzing this data, researchers were able to trace links to other malicious LNK files related to Coyote.
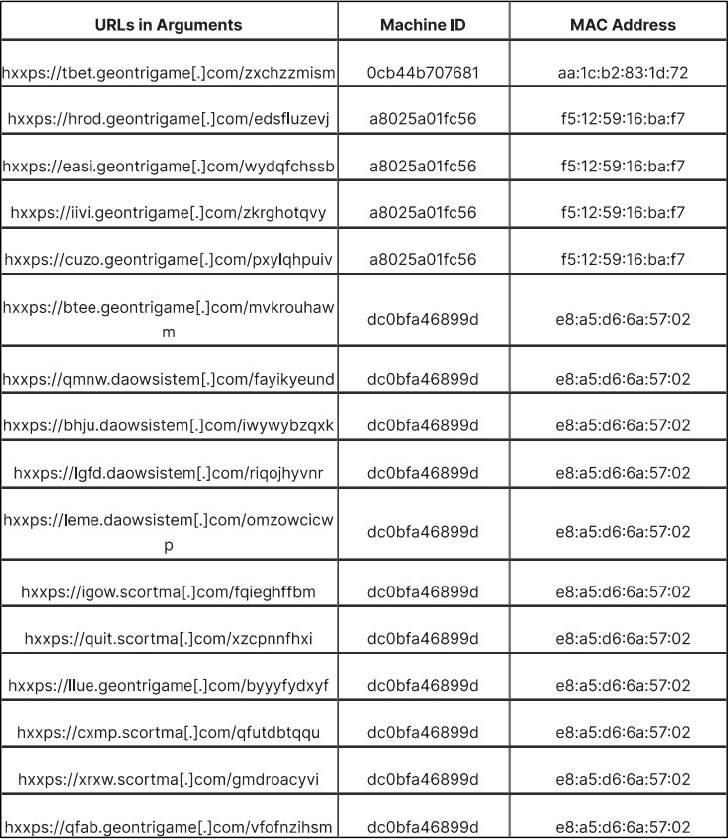
The “zxchzzmism” file contains an additional PowerShell script with two encoded data segments. The script uses specific commands to decode and execute the embedded shellcode, triggering the next stage of the attack.
Loader and Shellcode
The DLL file acts as a loader, injecting the payload into the system using specific commands. It then runs the injected code, which uses a tool called Donut to decrypt and execute the final MSIL payload. This payload establishes persistence by modifying the Windows registry to ensure it runs every time the system starts. It checks for any existing PowerShell commands in the registry and replaces them with a new command that downloads and executes a Base64-encoded URL. This URL activates the main functions of the Coyote Banking Trojan.
Once the attack is triggered, the malware collects basic system information, including machine name, username, and operating system details, and sends them to a remote server. It also identifies installed antivirus programs. The data is processed, encoded, and sent to the remote server in a unique format. Finally, the malware executes the PowerShell command added to the registry, which downloads and runs further malicious actions.
Technical Analysis
The payload used in the attack is larger than the one downloaded from the LNK file, as it contains the full Coyote Banking Trojan. After decrypting the payload from the Donut shellcode, researchers discovered it includes several functions. The Trojan first checks the username to avoid detection in test environments or sandboxes by looking for common test names. It also scans for virtual machine indicators by searching specific files in the system directory. In this version, Coyote expands its target list to include over 1,030 sites and 73 financial agents, mainly focusing on Brazilian platforms. It monitors the active window and, if a targeted site is accessed, connects to a command-and-control server. The Trojan then processes a message from the server to determine the next steps in the attack.
INSIGHTS
ETLM ASSESSMENT
From the ETLM perspective, CYFIRMA anticipates that Coyote malware is likely to evolve, posing an even greater risk to organizations and employees by refining its attack techniques and expanding its target scope beyond Brazil to a wider range of financial institutions and industries. Future variants could adopt more advanced stealth mechanisms, allowing the malware to remain undetected for extended periods, leading to prolonged data exposure, unauthorized financial transactions, and large-scale credential theft. With automated financial processes becoming more prevalent, Coyote may exploit vulnerabilities in enterprise software, infiltrating internal systems without immediate detection. Its impact could extend beyond direct financial losses, introducing greater regulatory challenges, reputational risks, and operational disruptions. As the malware continues to evolve, industries handling high-value transactions and global financial operations may face heightened risks, with employees potentially playing an inadvertent role in facilitating sophisticated cyberattacks.
IOCs:
Kindly refer to the IOCs Section to exercise controls on your security systems.
STRATEGIC:
MANAGEMENT:
TACTICAL RECOMMENDATIONS
Key Intelligence Signals:
UAC-0063: Expanding Cyber Espionage Operations Beyond Central Asia
Summary:
A cyber-espionage group, designated UAC-0063, has been actively targeting organizations in Central Asia and Europe, with a particular focus on government entities and diplomatic missions. Their operations have expanded beyond their initial region to include multiple European countries, such as Germany, the UK, the Netherlands, Romania, and Georgia. This expansion indicates an evolving threat landscape and a growing interest in high-value targets across different geopolitical areas. These emails contain malicious Microsoft Word documents that, when opened with macros enabled, trigger a multi-stage infection process. The first stage involves creating and opening a DOCX file named “SvcRestartTaskLogon,” which contains a macro that generates another file, “WsSwapAssessmentTask.” This file then executes another macro that creates a “SoftwareProtectionPlatform” file, which is identified as the HATVIBE malware. HATVIBE, an encoded VBScript, serves as a loader, facilitating the execution of additional malicious payloads.
To achieve their objectives, UAC-0063 deploys a variety of malware tools, each serving a distinct role. HATVIBE acts as the primary loader, enabling the execution of further malicious scripts. LOGPIE, a Python-based keylogger, captures keystrokes, aiding in credential theft and user activity monitoring. CHERRYSPY, also known as DownExPyer, is a Python-based backdoor that allows attackers to execute arbitrary Python code on compromised systems, enabling data exfiltration and remote control. STILLARCH, a C++-based tool, searches for and exfiltrates files from victims’ systems, including data collected by LOGPIE. Additionally, PyPlunderPlug, a USB data exfiltration tool, has been discovered on victim systems, indicating the group’s capability to extract data from removable media. The tactics, techniques, and procedures (TTPs) employed by UAC-0063 reveal their sophistication and adaptability. The group also exploits previously exfiltrated documents, weaponizing them and distributing them to new targets to establish trust. They rely heavily on scripting and scheduled tasks, using VBScript and other automation techniques to maintain persistence without user intervention. Their malware development spans multiple languages, including C++ and Python, which diversifies their toolset and complicates detection efforts. Furthermore, their tools are specifically designed for data exfiltration, targeting both system files and USB storage devices.
The ongoing operations of UAC-0063 suggest a well-maintained and actively evolving command-and-control infrastructure. The continuous creation of new weaponized documents and the expansion of their target regions indicate that their cyber-espionage activities are far from diminishing. The shift from an initial focus on Central Asia to a broader scope in Europe demonstrates their strategic adjustments and possibly new intelligence-gathering priorities. While there is a moderate confidence assessment linking UAC-0063 to a known Russian cyber-espionage group, definitive attribution remains uncertain. The use of backdoors developed in multiple programming languages is a characteristic observed in some Russian- affiliated groups, but this alone is not enough to confirm a direct connection. The lack of conclusive evidence means that while some indicators suggest a link, further analysis is required for definitive attribution.
Relevancy & Insights:
UAC-0063 has a history of cyber-espionage campaigns primarily targeting government institutions, diplomatic missions, and critical infrastructure in Central Asia. Their past attacks have consistently relied on spear-phishing tactics, often leveraging compromised documents from previous breaches to craft highly convincing lures. They have used similar infection chains involving malicious macros in Microsoft Office documents, leading to the deployment of custom malware families.
The current campaign follows the same operational patterns but exhibits notable expansions in geographic scope and tooling. While earlier incidents were confined to Central Asia, the latest attacks have extended into Europe, indicating a broader strategic focus. The deployment of new malware like CHERRYSPY and PyPlunderPlug suggests an evolution in their tactics, particularly in exfiltrating sensitive data. Additionally, the continued reliance on scripting and automation for persistence highlights their commitment to stealth and efficiency, aligning with their previously observed methods. This correlation underscores the group’s adaptability and sustained intelligence-gathering efforts.
ETLM Assessment:
UAC-0063(Fancy Bear) is a cyber-espionage group known for targeting government entities, diplomatic missions, and critical infrastructure. Initially active in Central Asia, the group has expanded its reach to Europe, including Germany, the UK, the Netherlands, Romania, and Georgia. Their attacks primarily rely on spear-phishing emails containing weaponized Microsoft Office documents.
They target Windows environments using scripting engines like VBScript and PowerShell, exploiting document macros and scheduled tasks for persistence. Previously, they used malware like LOGPIE (keylogger) and STILLARCH (data exfiltration). The latest campaign introduces CHERRYSPY (Python-based backdoor) and PyPlunderPlug (USB data exfiltration).
The evolving threat landscape suggests the group is refining its techniques for broader impact. Future assessments indicate continued targeting of diplomatic and governmental sectors, potentially leveraging more sophisticated malware variants and supply chain attacks. Organizations should enhance email security, restrict scripting execution, and monitor for indicators of compromise to mitigate risks.
Strategic Recommendations:
Tactical Recommendations:
Operational Recommendations:
| MITRE FRAMEWORK | ||
| Tactic | ID | Technique |
| Initial Access | T1566.001 | Phishing: Spearphishing Attachment |
| Execution | T1204 | User Execution |
| Execution | T1203 | Exploitation for Client Execution |
| Persistence | T1053 | Scheduled Task/Job |
| Defense Evasion | T1027 | Obfuscated Files or Information |
| Credential Access | T1056 | Input Capture |
| Discovery | T1082 | System Information Discovery |
| Collection | T1025 | Data from Removable Media |
| Command and Control |
T1071 | Application Layer Protocol |
| Exfiltration | T1041 | Exfiltration Over C2 Channel |
IOCs:
Kindly refer to the IOCs (Indicators of Compromise) Section to exercise controls on your security systems.
Norway seizes Russian-crewed ship suspected of communications sabotage
Norwegian authorities have detained the Silver Dania, a vessel with Russian crew members operating under Norwegian registration, following allegations of its involvement in damaging an underwater communications link connecting Sweden and Latvia. This marks the third vessel detained in the Baltic Sea region amid growing concerns about potential sabotage of submarine infrastructure. According to the Troms Police District, investigators are currently conducting a thorough examination of the ship, including searches, crew interviews, and evidence collection. The incident adds to recent heightened vigilance over the security of undersea communications networks in the Baltic region, with the Silver Dania joining two other vessels currently under investigation.
ETLM Assessment:
Prior to the campaign of undersea sabotage by Russian spy agencies, CYFIRMA released two reports this spring, one dealing with undersea cables and one titled Threat to Offshore Infrastructure in a Maritime-Centric Century, in which CYFIRMA concludes: “The most important evolving threat to the electric grid is associated with cybersecurity and physical security. The power grid in the US, and more so in Europe, is experiencing a transformation as the world shifts to sustainable energy: this transformation, however, is introducing new vulnerabilities to the system as offshore infrastructure is susceptible to physical and cybernetic attacks. Both the US and EU governments have aimed to bolster collaboration between critical infrastructure owners and operators as well as sector risk management agencies, but the hasty nature of the grid transformation will likely leave many openings for sophisticated cyber attackers for years to come”.
Italy and Texas block access to DeepSeek and other Chinese apps
Concerns over Chinese tech companies’ data practices are mounting across Western nations, with both European regulators and U.S. state governments taking decisive action. In Italy, the data protection authority Garante has implemented a nationwide block on DeepSeek, a Chinese AI application, after the company’s inadequate response to privacy concerns. The situation has drawn attention from other European privacy watchdogs, with French and Irish regulators also launching inquiries into DeepSeek’s data handling practices.
Meanwhile, in the United States, Texas has expanded its restrictions on Chinese- developed applications. Governor Greg Abbott has issued a comprehensive ban on several China-based AI and social media platforms, including DeepSeek, RedNote, Lemon8, Moomoo, and several others, building upon the state’s 2022 TikTok ban. The prohibition affects both government-issued and personal devices used by state employees and contractors, with Abbott citing concerns about potential Chinese Communist Party surveillance operations.
ETLM Assessment:
These parallel actions highlight growing international apprehension about data security and privacy risks associated with Chinese technology companies, particularly in government and regulatory contexts. The fact that the Chinese government prefers to exit the US market rather than cede operational oversight to US-owned entities suggests the CCP has a hidden agenda and that the Chinese intelligence services regularly access users’ data, as required by Chinese law. This topic will be a subject of a future comprehensive CYFIRMA report later this month.
US and Dutch authorities disrupt Pakistan-based cybercrime marketplace
A joint operation by U.S. and Dutch law enforcement has successfully disrupted a major cybercriminal enterprise by seizing 39 domain names linked to the notorious “HeartSender” group, led by Pakistani operator Saim Raza. This criminal organization operated a sophisticated network of online marketplaces specializing in fraudulent cyber tools and services.
The operation targeted websites that served as digital bazaars for various cybercrime tools, including phishing kits, scam pages, and email extraction software. What made this operation particularly concerning was its user-friendly approach: the group provided detailed YouTube tutorials teaching customers how to deploy these malicious tools effectively, making cybercrime accessible to even technically inexperienced criminals.
ETLM Assessment:
The cybercriminals marketed their products as “fully undetectable” by anti-spam systems, and their tools have been linked to significant financial damage. U.S. victims alone have reported losses exceeding $3 million due to phishing attacks conducted using the group’s tools. The takedown represents a blow to the cybercrime-as-a-service ecosystem, however, the ongoing democratization of cyber-attacks, where sophisticated criminal tools are made available to inexperienced actors, has fundamentally altered the scope and scale of digital threats organizations must defend against. This is a threat that all business and government entities will have to contend with in the future.
The FunkSec Ransomware Impacts Perumda Air Minum Tirta Raharja
Summary:
From the External Threat Landscape Management (ETLM) Perspective, CYFIRMA observed in an underground forum that a company from Indonesia; Perumda Air Minum Tirta Raharjai (www[.]tirtaraharja[.]co[.]id), was compromised by FunkSec Ransomware. Perumda Air Minum Tirta Raharja is a regional drinking water company in Indonesia, dedicated to providing clean and safe drinking water to its customers. The data, which has been breached, has not yet appeared on the leak site, indicating that negotiations between the affected party and the ransomware group may be underway. The compromised data consists of confidential and sensitive information related to the organization.
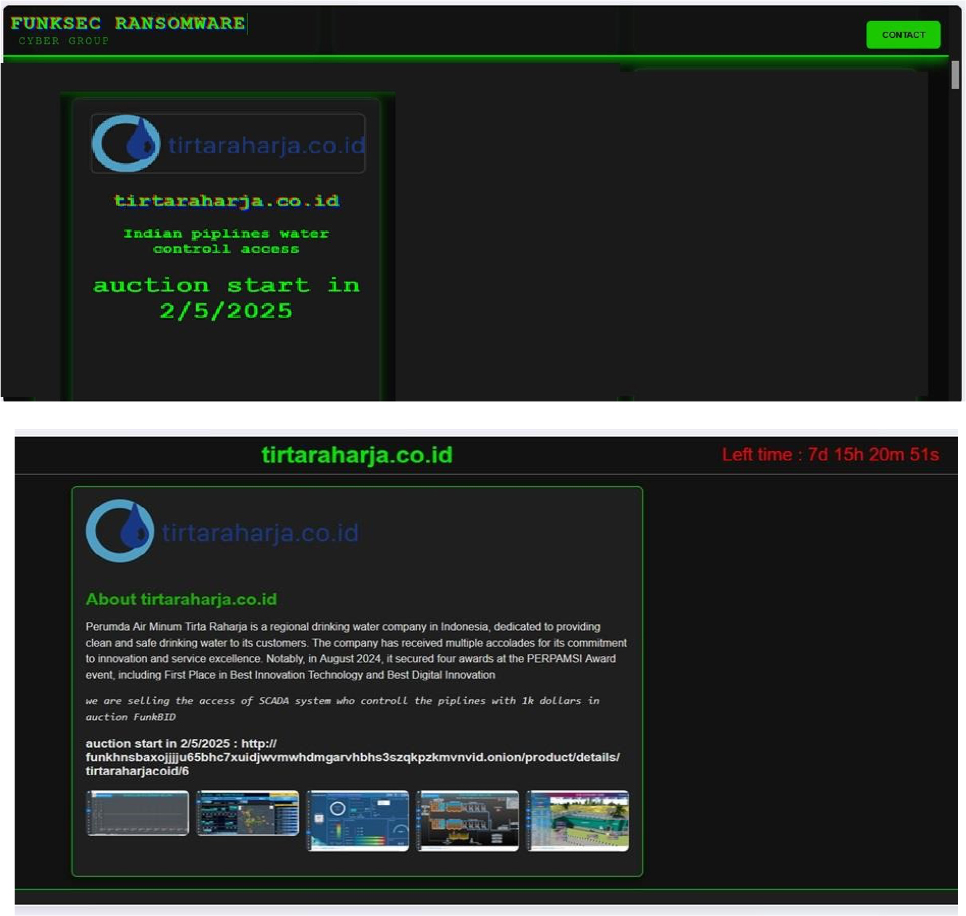
Source: Dark Web
Relevancy & Insights:
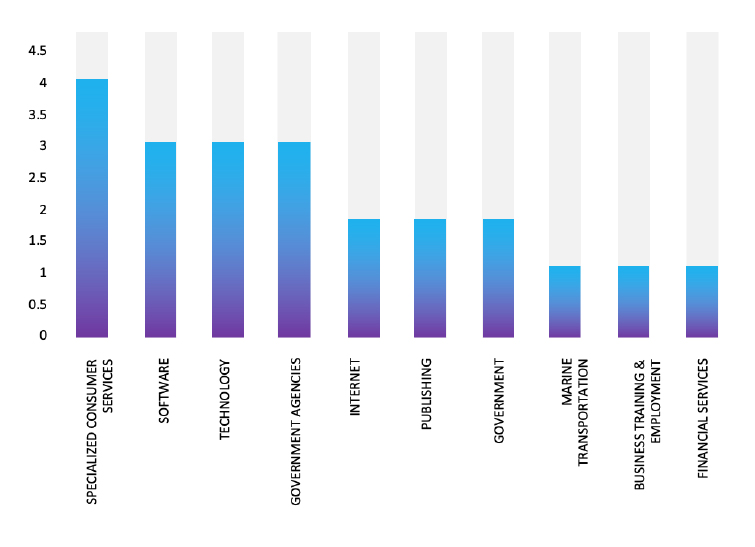
ETLM Assessment:
According to CYFIRMA’s assessment, FunkSec represents a new wave of ransomware threats characterized by the integration of AI technologies into their operations. Their rapid rise in prominence highlights the evolving landscape of cybercrime and the potential for inexperienced actors to leverage advanced tools for malicious purposes. Organizations are urged to bolster their cybersecurity defenses against such emerging threats by implementing robust incident response plans and continuous monitoring of unusual activities within their networks.
The RansomHub Ransomware Impacts Midway Metals Vietnam Co., Ltd.
Summary:
From the External Threat Landscape Management (ETLM) Perspective, CYFIRMA observed in an underground forum that a company from Vietnam; Midway Metals Vietnam Co., Ltd (https[:]//midwaymetals[.]com[.]vn/), was compromised by RansomHub Ransomware. Midway Metals Vietnam Co., Ltd. is a company specializing in the manufacturing and processing of stainless steel (inox) products. Based in the Chau Son Industrial Zone, Le Hong Phong Ward, Phu Ly City, Ha Nam Province, Vietnam, the company focuses on producing high-quality stainless-steel components for the global yachting and marine industry. Its products serve markets across South Africa, Australia, New Zealand, China, and several European countries. The data, which has been breached, has not yet appeared on the leak site, indicating that negotiations between the affected party and the ransomware group may be underway. The compromised data consists of confidential and sensitive information related to the organization. The total size of the compromised data is approximately 46 GB.
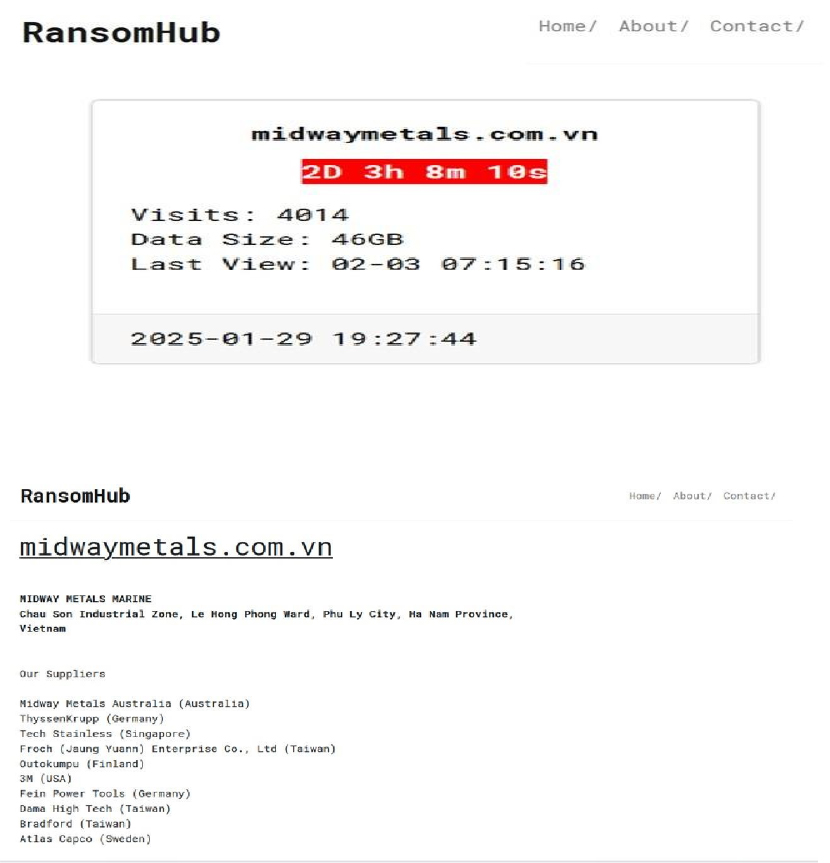
Source: Dark Web
Relevancy & Insights:
ETLM Assessment:
According to recent assessments by CYFIRMA, RansomHub ransomware is projected to escalate its activities across multiple industries globally, with a particular emphasis on the United States, Europe, and Asia. This forecast is underscored by a recent attack on Midway Metals Vietnam Co., Ltd., a leading manufacturing company in Vietnam, demonstrating RansomHub’s growing threat in Southeast Asia.
Vulnerability in VMware Aria Operations
Relevancy & Insights: The vulnerability exists due to excessive data output by the application.
Impact: A remote authenticated user can retrieve credentials for an outbound plugin if a valid service credential ID is known.
Affected Products: https[:]//support[.]Broadcom[.]com/web/ecx/support-content- notification/-/external/content/SecurityAdvisories/0/25329
Recommendations:
Monitoring and Detection: Implement monitoring and detection mechanisms to identify unusual system behavior that might indicate an attempted exploitation of this vulnerability.
TOP 5 AFFECTED TECHNOLOGIES OF THE WEEK
This week, CYFIRMA researchers have observed significant impacts on various technologies, due to a range of vulnerabilities. The following are the top 5 most affected technologies.
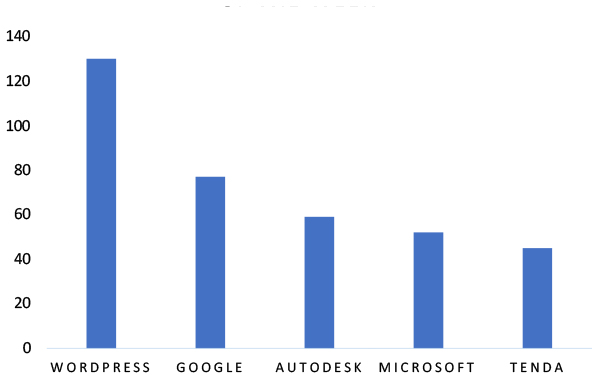
ETLM Assessment
Vulnerability in VMware Aria Operations can pose significant threats to user privacy and security. This can impact various industries globally, including technology, finance, healthcare, and beyond. Ensuring the security of VMware Aria Operations is crucial for maintaining the integrity and protection of users’ data worldwide.
Therefore, addressing these vulnerabilities is essential to safeguarding IT operations management, performance monitoring, and analytics across different geographic regions and sectors.
Killsec Ransomware attacked and published the data of Anupalan Online Private Limited
Summary
Recently, we observed that Killsec Ransomware attacked and published the data of Anupalan Online Private Limited(https[:]//anupalanonline[.]com) on its dark web website. Anupalan Online Private Limited is a leading provider of e-Compliance solutions and accounting software, designed to simplify compliance processes for businesses across more than 30 industries. The data leak, following the ransomware attack, encompasses sensitive and confidential records, originating from the organizational database.

Source: Dark Web
Relevancy & Insights:
ETLM Assessment:
The emergence and evolution of KillSec’s Ransomware-as-a-Service (RaaS) platform represents a concerning development in the cybercrime landscape. By lowering the technical barrier to entry, this RaaS model allows less skilled individuals to engage in sophisticated ransomware attacks, potentially leading to an increase in such incidents globally.
According to CYFIRMA’s assessment, the KillSec ransomware group is expected to continue targeting a wide range of industries worldwide. Their advanced tactics, such as exploiting website vulnerabilities and conducting credential theft, make them a significant threat to organizations with inadequate security measures in place.
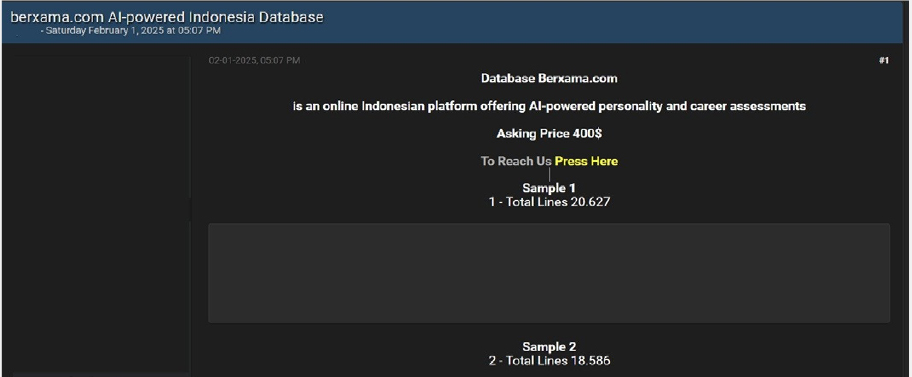
Berxama Data Advertised on a Leak Site
Summary:
The CYFIRMA Research team observed data sale related to Berxama(www[.]berxama[.]com) in an underground forum. Berxama is an online Indonesian platform offering AI-powered personality and career assessments. The leaked data includes confidential and sensitive information pertaining to the clients of the affected organization. The asking price for the data sale is $400. The breach has been linked to a threat actor identified as “r57.
Source: Underground forums
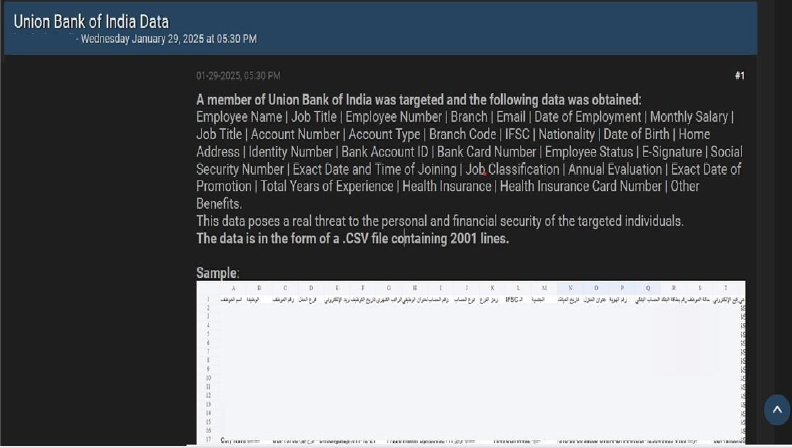
Union Bank of India Data Advertised on a Leak Site
Summary:
The CYFIRMA Research team observed a data leak related to the Union Bank of India(https[:]//www[.]unionbankofindia[.]co[.]in) in an underground forum. Union Bank of India (UBI) is a leading public sector bank in India, providing a wide range of banking and financial services. The leaked data includes Employee Name, Job Title, Employee Number, Branch, Email, Date of Employment, Monthly Salary, Account Number, Account Type, Branch Code, IFSC, Nationality, Date of Birth, Home Address, Identity Number, Bank Account ID, Bank Card Number, Employee Status, E-Signature, Social Security Number, Exact Date and Time of Joining, Job Classification, Annual Evaluation, Exact Date of Promotion, Total Years of Experience, Health Insurance, Health Insurance Card Number, Other Benefits, and other sensitive and confidential information. The compromised data is stored in a .CSV file containing 2001 lines. The breach has been attributed to a threat actor known as “Black Devil.”
Source: Underground forums
Relevancy & Insights:
Financially motivated cybercriminals are continuously scouring for exposed and vulnerable systems and applications to exploit. A significant number of these malicious actors congregate within underground forums, where they discuss cybercrime and trade stolen digital assets. Operating discreetly, these opportunistic attackers target unpatched systems or vulnerabilities in applications to illicitly gain access and steal valuable data.
Subsequently, the pilfered data is advertised for sale within underground markets, where it can be acquired, repurposed, and utilized by other malicious actors in further illicit activities.
ETLM Assessment:
The threat actor “Black Devil” has been active since late 2024, rapidly gaining attention for its aggressive tactics and operational techniques. Organizations are urged to strengthen their security posture by enforcing access controls, regular patch management, and employee cybersecurity training to mitigate associated risks.
Continuous monitoring of emerging threats like “Black Devil” is crucial for developing effective incident response strategies in the ever-evolving cyber threat landscape.
Recommendations: Enhance the cybersecurity posture by:
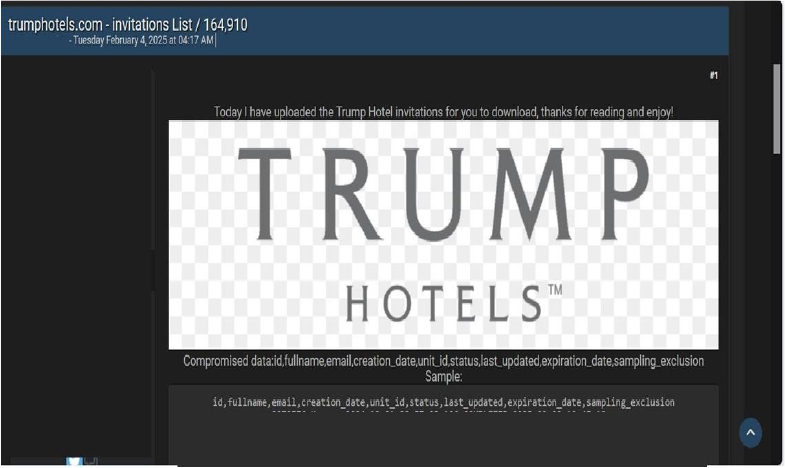
The CYFIRMA Research team observed a data leak related to Trump Hotels (https[:]//www[.]trumphotels[.]com/) in an underground forum. TrumpHotels[.]com serves as the official website of Trump Hotels, a luxury hotel collection owned and operated by The Trump Organization. The site offers detailed information on its various hotels and resorts, including accommodations, amenities, dining options, special offers, and booking services.
The compromised data includes ID, full name, email, account creation date, unit ID, status, last updated timestamp, expiration date, sampling exclusion, and other potentially sensitive information. The breach has been attributed to a threat actor known as “FutureSeeker”
Source: Underground Forums
The CYFIRMA Research team observed a data leak related to My Future Job Philippines (https[:]//www[.]myfuturejob[.]ph/) in an underground forum. MyFutureJob.ph is an online job portal dedicated to connecting job seekers with employment opportunities across the Philippines. The platform offers a comprehensive job search experience, allowing users to explore positions across various industries and locations. The Leak data includes Mobile Number, Email, Password, Address, etc. The breach has been attributed to a threat actor known as “Hagsg”
Source: Underground Forums
STRATEGIC RECOMMENDATIONS
MANAGEMENT RECOMMENDATIONS
TACTICAL RECOMMENDATIONS
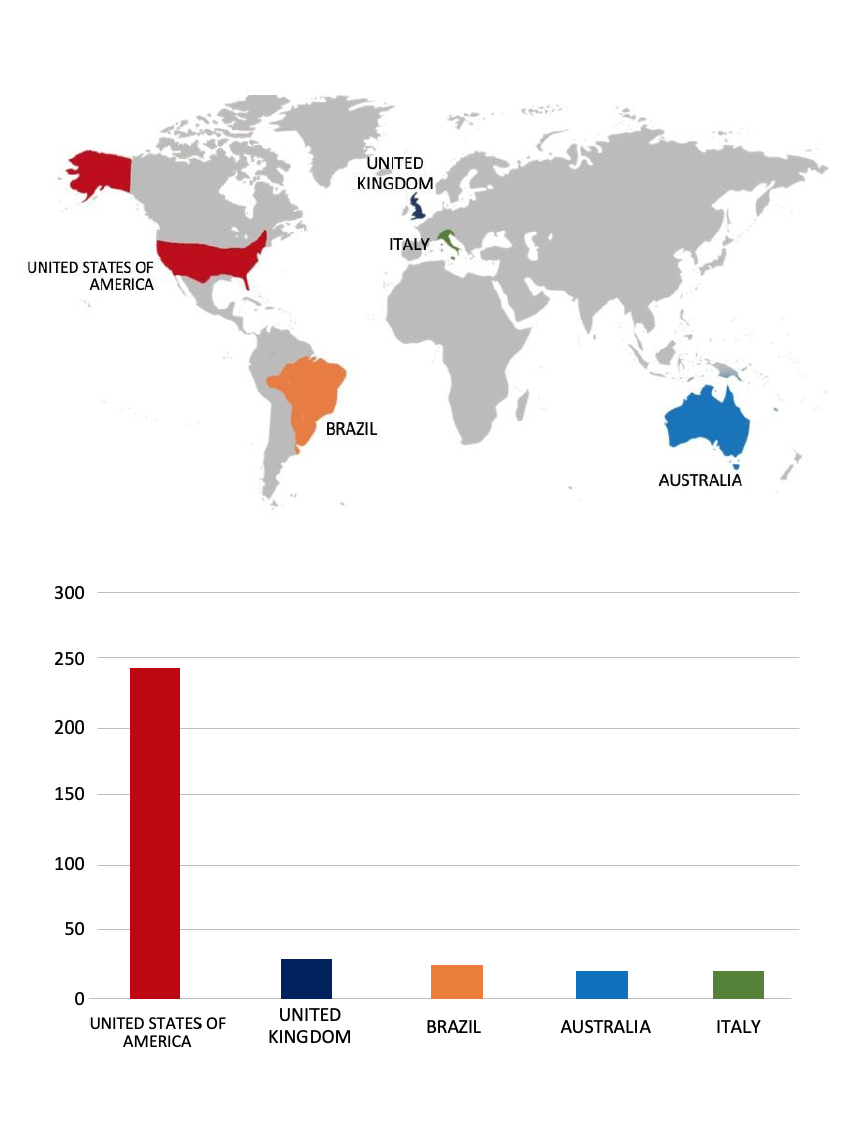
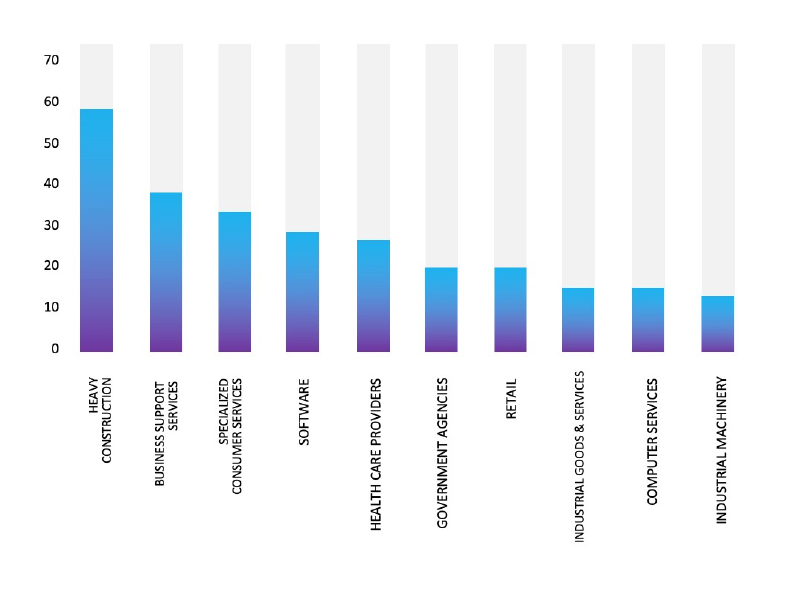
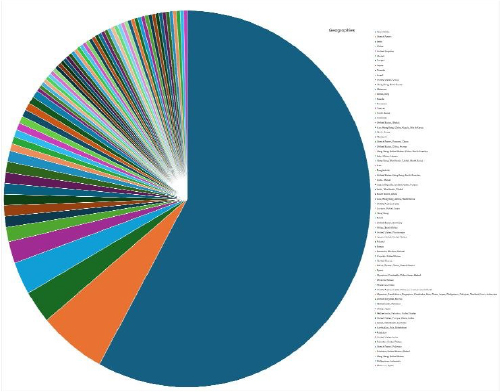
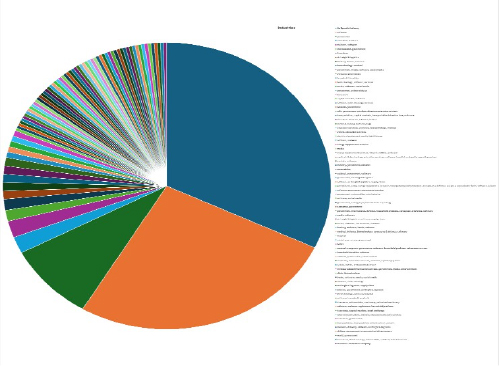
Please find the Geography-Wise and Industry-Wise breakup of cyber news for the last 5 days as part of the situational awareness pillar.
Geography-Wise Graph
Industry-Wise Graph
For situational awareness intelligence and specific insights mapped to your organisation’s geography, industry, and technology, please access DeCYFIR.