



CYFIRMA Research and Advisory Team would like to highlight ransomware trends and insights gathered while monitoring various forums. This includes multiple – industries, geography, and technology – that could be relevant to your organization.
Type: Ransomware
Target Technologies: MS Windows
Introduction
CYFIRMA Research and Advisory Team has found Pe32s Ransomware while monitoring various underground forums as part of our Threat Discovery Process.
Pe32s Ransomware
Researchers have recently discovered a new ransomware strain named Pe32s. Once it infiltrates a victim’s system, it encrypts files and modifies their names using the following pattern:
“[original_filename].[victim_ID].[format].pe32s”
This structure includes the original filename, a unique victim ID, the file format (all enclosed in square brackets), and the “.pe32s” extension. After encryption, the ransomware generates a ransom note titled “README.txt”.
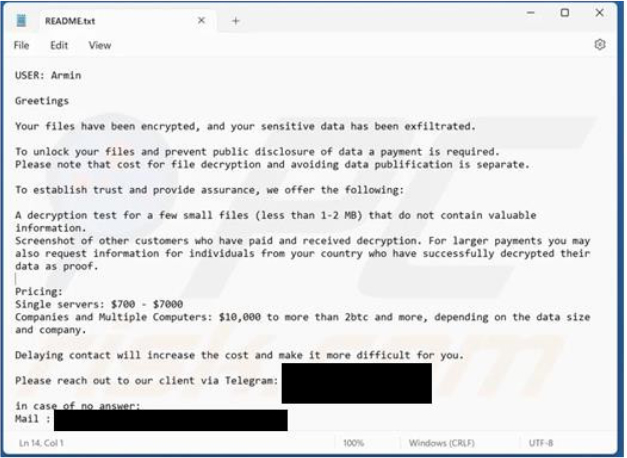
The Pe32s ransomware informs victims that their files have been encrypted and sensitive data has been exfiltrated. It demands separate payments for file decryption and to prevent data leaks.
Ransom amounts range from hundreds to hundreds of thousands of USD, depending on the number of infected systems and the scale of the targeted organization. As a demonstration, attackers offer free decryption for a few small files (1-2 MB) that do not contain valuable data before payment is made.
Following are the TTPs based on the MITRE Attack Framework
| Tactic | ID | Technique |
| Execution | T1106 | Native API |
| Execution | T1129 | Shared Modules |
| Persistence | T1574 | Hijack Execution Flow |
| Persistence | T1574.002 | DLL Side-Loading |
| Privilege Escalation | T1574 | Hijack Execution Flow |
| Privilege Escalation | T1574.002 | DLL Side-Loading |
| Defense Evasion | T1027 | Obfuscated Files or Information |
| Defense Evasion | T1140 | Deobfuscate/Decode Files or Information |
| Defense Evasion | T1562 | Impair Defenses |
| Defense Evasion | T1562.001 | Disable or Modify Tools |
| Defense Evasion | T1574 | Hijack Execution Flow |
| Defense Evasion | T1574.002 | DLL Side-Loading |
| Discovery | T1018 | Remote System Discovery |
| Discovery | T1082 | System Information Discovery |
| Discovery | T1083 | File and Directory Discovery |
| Discovery | T1518 | Software Discovery |
| Discovery | T1518.001 | Security Software Discovery |
| Collection | T1560 | Archive Collected Data |
| Command and Control | T1071 | Application Layer Protocol |
| Command and Control | T1095 | Non-Application Layer Protocol |
| Command and Control | T1102 | Web Service |
| Command and Control | T1573 | Encrypted Channel |
| Impact | T1486 | Data Encrypted for impact |
Relevancy and Insights:
ETLM Assessment:
CYFIRMA’s analysis with available data suggests that Pe32s ransomware may pose a significant threat across multiple regions, primarily targeting companies for financial gain. Industries such as manufacturing, finance, and other critical sectors face heightened risks. Future variants may adopt stronger encryption, advanced evasion techniques, and a broader attack scope. Staying vigilant and enforcing robust cybersecurity measures will be essential in countering these evolving threats.
Sigma rule:
title: Suspicious Non-Browser Network Communication With Telegram API tags:
– attack.command-and-control
– attack.t1102 logsource:
product: windows
category: network_connection detection:
selection:
DestinationHostname|contains: ‘api.telegram.org’
# Other browsers or apps known to use telegram should be added # TODO: Add full paths for default install locations filter_main_brave:
Image|endswith: ‘\brave.exe’ filter_main_chrome:
Image:
– ‘C:\Program Files\Google\Chrome\Application\chrome.exe’
– ‘C:\Program Files (x86)\Google\Chrome\Application\chrome.exe’ filter_main_firefox:
Image:
– ‘C:\Program Files\Mozilla Firefox\firefox.exe’
– ‘C:\Program Files (x86)\Mozilla Firefox\firefox.exe’
filter_main_ie:
Image:
– ‘C:\Program Files (x86)\Internet Explorer\iexplore.exe’
– ‘C:\Program Files\Internet Explorer\iexplore.exe’ filter_main_maxthon:
Image|endswith: ‘\maxthon.exe’ filter_main_edge_1:
– Image|startswith: ‘C:\Program Files (x86)\Microsoft\EdgeWebView\Application\’
– Image|endswith: ‘\WindowsApps\MicrosoftEdge.exe’
– Image:
– ‘C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe’
– ‘C:\Program Files\Microsoft\Edge\Application\msedge.exe’ filter_main_edge_2:
Image|startswith:
– ‘C:\Program Files (x86)\Microsoft\EdgeCore\’
– ‘C:\Program Files\Microsoft\EdgeCore\’ Image|endswith:
– ‘\msedge.exe’
– ‘\msedgewebview2.exe’ filter_main_opera:
Image|endswith: ‘\opera.exe’
filter_main_safari:
Image|endswith: ‘\safari.exe’ filter_main_seamonkey:
Image|endswith: ‘\seamonkey.exe’ filter_main_vivaldi:
Image|endswith: ‘\vivaldi.exe’ filter_main_whale:
Image|endswith: ‘\whale.exe’
condition: selection and not 1 of filter_main_* falsepositives:
– Legitimate applications communicating with the Telegram API e.g. web browsers not in the exclusion list, app with an RSS etc.
level: medium
(Source: Surface Web)
IOCs:
Kindly refer to the IOCs section to exercise control of your security systems.
STRATEGIC RECOMMENDATION
MANAGEMENT RECOMMENDATION
TACTICAL RECOMMENDATION
Type: Backdoor | Objectives: Infiltration, Espionage, Stealing Sensitive Information| Target Industries: Government, Defense, Telecommunications, Education, and Aviation Sectors | Target Technologies: Windows and Linux | Target Geographies: Southeast Asia and South America
CYFIRMA collects data from various forums based on which the trend is ascertained. We identified a few popular malwares that were found to be distributed in the wild to launch cyberattacks on organizations or individuals.
Active Malware of the week
This week “Squidoor” is trending.
Summary
Researchers have identified Squidoor, aka FinalDraft, a sophisticated backdoor capable of infiltrating both Windows and Linux systems. This advanced threat has been observed targeting government, defense, telecommunications, education, and aviation sectors across Southeast Asia and South America. It is designed to collect sensitive information from compromised organizations and gather details about high-ranking officials. This malware not only infiltrates critical industries but also employs stealth tactics like Pastebin abuse and LOLBAS techniques to evade detection.
Squidoor
Squidoor is an advanced backdoor designed for stealth and adaptability, allowing it to evade detection even in highly secured environments. It supports multiple modules and operates on both Windows and Linux, making it a versatile tool for cybercriminals. Once deployed, it enables attackers to maintain access, move laterally within networks, establish covert communication channels with its operators, and collect sensitive information about the targeted organizations.
One of Squidoor’s most distinctive features is its ability to communicate with its command-and-control (C2) server through multiple methods. The Windows variant offers 10 different methods of C2 communication, while the Linux version provides 9, including rarely seen techniques such as Outlook API, DNS tunneling, and ICMP tunneling. Some methods facilitate external communication with the C2 server, while others allow internal coordination between infected systems, helping attackers remain undetected. Beyond communication, Squidoor can execute various commands, such as gathering system information, running arbitrary code, and injecting or delivering additional payloads.
These capabilities make it a powerful tool for prolonged access and data collection within compromised networks.
Attack Method
To infiltrate networks, the threat actor exploited vulnerabilities in Internet Information Services (IIS) servers as an initial entry point. After gaining access, they deployed multiple web shells to establish persistent control over compromised systems. These web shells functioned as backdoors, allowing the attackers to execute commands remotely and maintain long-term access. To expand their reach, the attackers attempted to spread the web shells across different servers using curl and Impacket. They also disguised one of the web shells as a certificate and used Windows Management Instrumentation (WMI) to copy it to additional systems, enhancing their persistence. The web shells shared common decryption key structures, extensive obfuscation, and consistent code patterns. Some were stored on Bashupload, a web application that allows users to upload files via the command line and download them to another server, and later retrieved using certutil, enabling the attackers to discreetly sustain their presence.
Execution and Persistence: LOLBAS Technique
To deploy Squidoor, the attackers abused a legitimate Microsoft debugging tool, cdb.exe, a rarely used technique that helps evade detection. They delivered cdb.exe to infected systems, renamed it as fontdrvhost.exe, and used it to execute malicious shellcode in memory. This method, known as a living-off-the-land (LOLBAS) technique, leverages trusted system tools to carry out attacks while avoiding security alerts. Once executed, the renamed cdb.exe loaded shellcode from a file called config.ini, initiating Squidoor’s operations. The attackers then used LoadShellcode.x64.dll, injected into mspaint.exe, to decrypt and load another Squidoor implant from a file named wmsetup.log. This multi-step execution process helped maintain stealth and avoid detection. To ensure persistence, Squidoor created a scheduled task named Microsoft\Windows\AppID\EPolicyManager, which repeatedly executed the shellcode, allowing the malware to remain active even after system reboots. This approach ensured long-term access to compromised systems while blending in with normal Windows processes.
Once Squidoor is loaded into memory, it executes its UpdateTask function, which decrypts its hard-coded configuration. This configuration determines how the malware will communicate with its command-and-control (C2) server. A key element of Squidoor’s setup is a single-digit value (0-9) that acts as a switch, selecting one of its multiple communication methods. Depending on the variant, additional configuration fields may be included, such as domain names, IP addresses, listening ports, encryption keys, or access tokens.
Communication Methods
The Windows version of Squidoor supports 10 different methods for communicating with its command-and-control (C2) server. Each method is selected based on a predefined switch case digit within the malware’s configuration. This flexibility allows attackers to adapt their communication strategy based on the environment, ensuring continued access while evading detection.
| Switch Case Digit | Internal Class Name | Description |
| 0 | CHttpTransChannel | HTTP-based communication |
| 1 | CReverseTcpTransChannel | Reverse TCP connection to a remote server |
| 2 | CReverseUdpTransChannel | Reverse UDP connection to a remote server |
| 3 | CBindTcpTransChannel | Listen for incoming TCP connections (suspected to be used for only internal communication) |
| 4 | CBindHttpTransChannel | Listen for incoming HTTP connections (become an HTTP Server) |
| 5 | COutLookTransChannel | Communicate via an Outlook mail API |
| 6 | CIcmpTransChannel | Utilize ICMP tunneling for communication |
| 7 | CDnsTransChannel | Utilize DNS tunneling for communication |
| 8 | CWebTransChannel | Communicate via a mail client retrieved from the configuration file |
| 9 | CBindSMBTransChannel | Use named pipes for communication (only internal communication, and only on the Windows version) |
When Squidoor is configured to use COutLookTransChannel, it exploits Microsoft’s identity platform to establish communication with its operators. It logs in using a hard-coded refresh token and stores the Microsoft Graph API token in the system registry. To track infected machines, Squidoor sends an HTTP request to a specific Pastebin page, which attackers likely monitor to count active implants. It then searches the Outlook drafts folder for emails with a specific subject pattern. If no such email exists, it sends a new encoded message to attackers.
Once the initial connection is established, Squidoor continuously checks the drafts folder for messages containing instructions. If it finds a command, it retrieves the email, deletes it from the mailbox, and then decrypts its contents. This method allows it to blend in with normal Outlook activity, making detection difficult.
Decoding and Execution: How Squidoor Executes Commands
Once Squidoor retrieves an email command from its operators, it undergoes multiple layers of decoding. The malware first converts the email content into bytes, then decodes it from Base64, decrypts it using a mix of AES and XOR, and finally decompresses the data. This decoded content determines the command Squidoor should execute, which could include deploying additional payloads or executing specific actions.
Key Capabilities of Squidoor
Squidoor can receive a set of commands from its C2 server, providing attackers with various capabilities to take complete control of the compromised machine. These include:
Squidoor Code Injection
Squidoor injects malicious code into legitimate processes to evade detection. It does this through DLL injection, selecting targets like mspaint.exe or conhost.exe based on the system’s configuration. If needed, it can also inject code into an already running process chosen by the attackers.
Modular Design and Lateral Movement
The threat actor leverages Squidoor’s modular nature to execute additional payloads within multiple system processes, including taskhostw.exe and vmtoolsd.exe. These modules facilitate lateral movement using Windows Remote Management (WinRM), data theft, and remote command execution. To evade detection, the injected payloads operate entirely in memory and require a password to run, preventing easy sandbox analysis. The attackers also use these modules for advanced techniques such as:
Squidoor’s Pastebin Tactics
Squidoor’s operators used Pastebin to store critical components of their malware’s communication methods. They maintained at least two accounts, using them to store access tokens, API keys, and other critical data. One of these accounts had been active for nearly a year, with the attacker periodically updating its content. In early February 2025, the attackers deleted existing files and replaced them with new ones containing Microsoft Graph API tokens, with filenames suggesting specific targets. Additionally, they likely used these accounts to monitor the spread of Squidoor by tracking how often implants queried Pastebin.
INSIGHTS
ETLM ASSESSMENT
From the ETLM perspective, CYFIRMA anticipates that Squidoor’s advanced capabilities suggest that future malware will increasingly rely on modular architectures, allowing attackers to adapt their tools for different environments and operating systems. With its current focus on governments, defense, telecommunications, education, and aviation sectors in Southeast Asia and South America, it is likely that future variants could expand to a wider range of industries and regions.
The use of multiple communication methods, including cloud-based services and covert tunneling techniques, indicates a shift toward more resilient and harder-to-detect malware. Additionally, the reliance on legitimate services like Pastebin and Microsoft APIs points to a growing trend where cybercriminals leverage everyday digital infrastructure for persistence and stealth. As attackers refined these strategies, future threats may become even more decentralized, making traditional signature-based detection methods less effective and increasing the need for more adaptive cybersecurity defenses.
IOCs:
Kindly refer to the IOCs Section to exercise controls on your security systems.
STRATEGIC:
MANAGEMENT:
TACTICAL RECOMMENDATIONS
Key Intelligence Signals:
North Korea-Linked Threat Actor Uses RustDoor and Koi Stealer Malware to Target macOS Systems in the Cryptocurrency Sector
Summary:
The recent cyberattack campaign involving macOS malware has been attributed to North Korean threat actor Alluring Pisces. The campaign primarily targets job-seeking software developers in the cryptocurrency industry, using social engineering tactics to deploy malicious software disguised as legitimate updates. The malware identified includes a Rust-based macOS malware called RustDoor and a previously undocumented variant of Koi Stealer, an infostealer focused on cryptocurrency wallets. The attack begins with the delivery of a malicious Visual Studio project or software update, which installs RustDoor, a backdoor designed to execute various malicious actions. Upon execution, it attempts to download additional malware, steal sensitive data such as passwords from browser extensions, and exfiltrate information to command-and-control servers. One of the RustDoor variants tries to establish a reverse shell connection to further compromise the system. The second stage of the attack involves the execution of a new variant of Koi Stealer. This malware, masquerading as a Visual Studio update, seeks root privileges to install itself on the infected system. Once installed, it collects and exfiltrates a wide array of sensitive data, including system information, user credentials, browser data, and cryptocurrency wallet files. It uses AppleScript to mute the system’s volume during its operations to avoid detection, further enhancing its stealth. The Koi Stealer’s operation is similar to a Windows variant, sharing data collection techniques and communication with the same command-and-control infrastructure. Both variants exfiltrate stolen data by transmitting memory streams to avoid detection from traditional file-based analysis. The attack is consistent with previously observed activity from North Korean threat actors, utilizing tools and infrastructure linked to previous campaigns. The attack’s social engineering focus on software developers in the cryptocurrency sector and the deployment of sophisticated malware tools suggest a nation-state actor behind the operation.
Relevancy & Insights:
North Korean threat actors, particularly groups like “Lazarus” and “BlueNoroff,” have a history of cyberattacks targeting financial sectors, cryptocurrency exchanges, and tech industries. Notable incidents include the 2017 WannaCry ransomware attack, the 2016 Bangladesh Bank heist, and the targeting of cryptocurrency exchanges to steal digital assets. These groups are known for using sophisticated social engineering tactics to infiltrate organizations, often masquerading as legitimate recruiters or employers, as seen in attacks like the “Contagious Interview” campaign.
The current campaign correlates with past North Korean tactics, specifically the use of social engineering to target software developers in the cryptocurrency industry. The deployment of malware such as RustDoor and Koi Stealer aligns with North Korea’s continued focus on stealing financial data, including cryptocurrency wallets. The use of previously unseen malware variants and the infrastructure linked to past operations, such as the C2 server at apple-ads-metric[.]com, suggests a continuation of their targeted efforts in cybercrime for financial gain.
ETLM Assessment:
North Korean state-sponsored APT groups, such as Lazarus and BlueNoroff, are known for cyber espionage and financially motivated attacks. These groups primarily target cryptocurrency exchanges, software developers, and financial institutions, leveraging social engineering tactics to infiltrate victims. The current attack campaign primarily targets software developers in the cryptocurrency sector, using macOS malware like RustDoor and Koi Stealer. The malware is designed to steal sensitive information, such as cryptocurrency wallets and user credentials, and exfiltrate data to command and control (C2) servers. This aligns with past North Korean operations, including the infamous WannaCry ransomware and RedLine Stealer campaigns. The attackers often exploit social engineering (posing as recruiters), zero-day vulnerabilities, and weak authentication protocols to gain access. As North Korea’s reliance on cybercrime for financial gain grows, future threats are expected to focus on cloud services, supply chain vulnerabilities, and critical infrastructure. Organizations must remain vigilant and invest in advanced security measures.
Strategic Recommendations:
Tactical Recommendations:
Operational Recommendations:
| MITRE Framework | ||
| Tactic | ID | Technique |
| Defense Evasion | T1070.004 | Indicator Removal: File Deletion |
| Command and Control | T1071 | Application Layer Protocol |
| Command and Control | T1095 | Non-Application Layer Protocol |
| Command and Control | T1573 | Encrypted Channel |
IOCs:
Kindly refer to the IOCs (Indicators of Compromise) Section to exercise controls on your security systems.
Pentagon Denies Report of Halt in Cyber Operations Versus Russia
During the week the media broke news on alleged U.S. Defense Secretary Pete Hegseth’s order to Cyber Command to pause offensive cyber operations against Russia. However, according to a later DOD statement, Hegseth has neither canceled nor delayed any cyber operations directed against malicious Russian targets and there has been no stand-down order whatsoever from that priority.
ETLM Assessment:
The news on the heels of President Trump ordering a pause to all military assistance to Ukraine until Ukraine’s leaders demonstrate “a good-faith commitment to peace negotiations”. However, the US administration did not put similar conditions on Russia, which has shown little interest in peace, including by continuing cyber-attacks on Western governments and businesses.
Lotus Blossum targets Southeast Asia in a cyber espionage campaign
Researchers are monitoring several cyber espionage campaigns by the Lotus Blossom threat actor, targeting government, manufacturing, telecommunications, and media sectors in Vietnam, Taiwan, Hong Kong, and the Philippines.
Researchers report that the operation appears to have achieved significant success in penetrating its targets. These campaigns utilize the Sagerunex remote access tool, which is exclusively deployed by Lotus Blossom, a threat actor that has previously been linked to China.
ETLM Assessment:
These campaigns seem to be classic state-driven espionage with many similar campaigns like it probably underway at the same time. The effort is likely part of a broader Chinese strategy to gather intelligence on geopolitical developments and intellectual property.
The Lynx Ransomware Impacts Xepa-Soul Pattinson (M) Sdn Bhd
Summary:
From the External Threat Landscape Management (ETLM) Perspective, CYFIRMA observed in an underground forum that a company from Malaysia; Xepa-Soul Pattinson (M) Sdn Bhd (https[:]//xepasp[.]com/), was compromised by Lynx Ransomware. Xepa-Soul Pattinson (M) Sdn Bhd is a leading pharmaceutical manufacturing enterprise in Malaysia. The compromised data includes 500GB of internal documents, encompassing financial records, contracts, patents, HR files, and more.
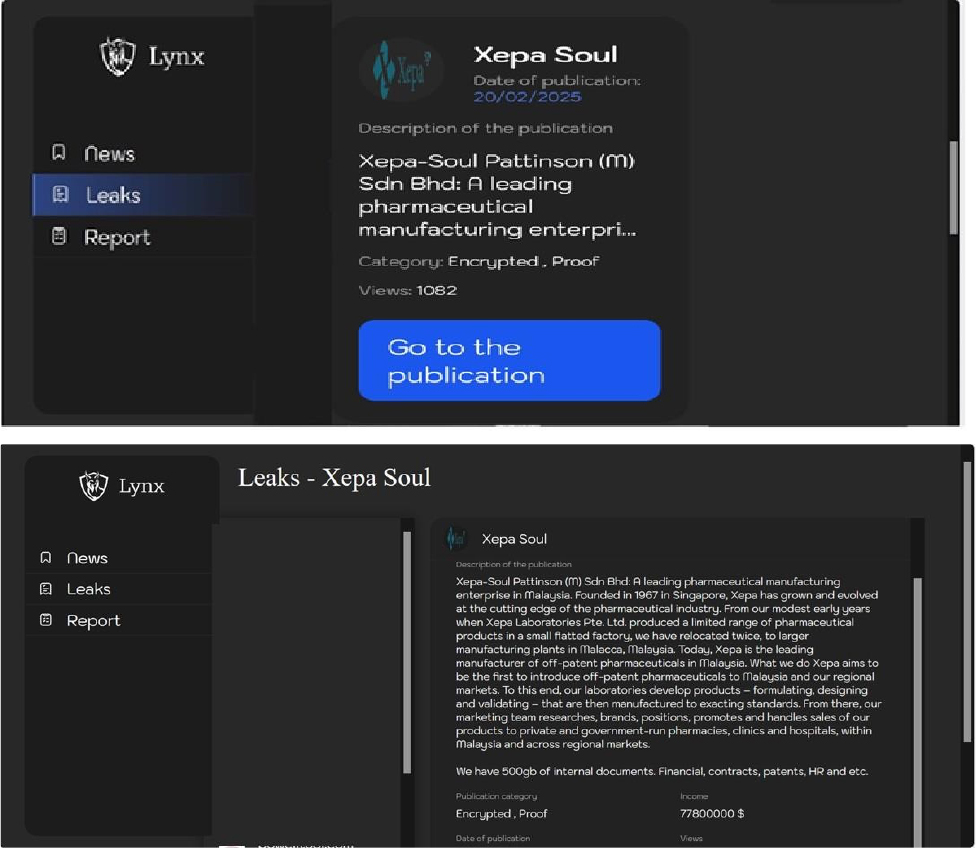
Relevancy & Insights:
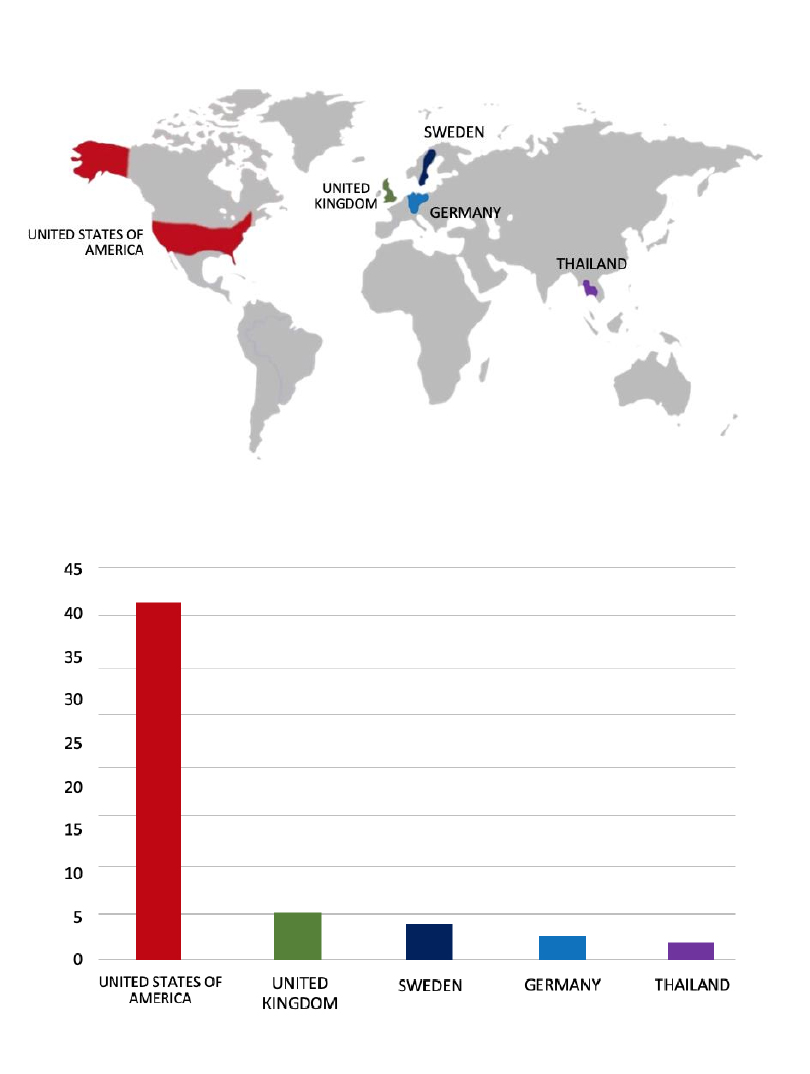
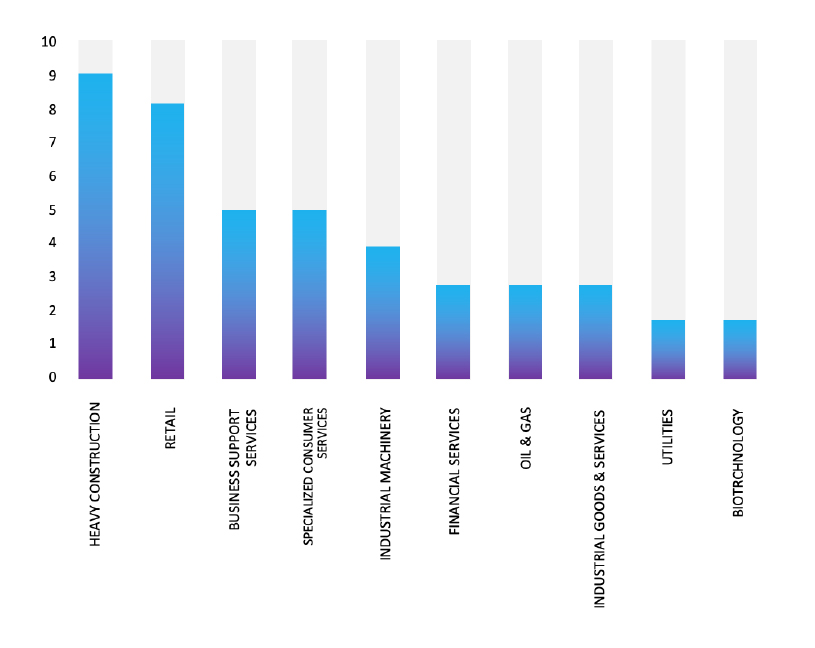
ETLM Assessment:
According to CYFIRMA’s assessment, Lynx ransomware has emerged as a significant threat in the cybersecurity landscape, leveraging advanced encryption and double extortion tactics to target small and medium-sized businesses. Its structured affiliate program and versatile ransomware toolkit make it a formidable force in the RaaS ecosystem.
The Hunters International Ransomware Impacts Nichino Ryokka Co Ltd
Summary:
From the External Threat Landscape Management (ETLM) Perspective, CYFIRMA observed in an underground forum that a company from Japan; Nichino Ryokka Co., Ltd. (www[.]nichino-ryokka[.]co[.]jp) was compromised by Hunters International Ransomware. Nichino Ryokka Co., Ltd. is a Japanese company specializing in various services related to landscaping, turf management, and horticultural supplies. The compromised data includes confidential and sensitive information belonging to the organization. The scale of the data exposure measures approximately 576.6 GB, comprising a total of 3,00,323 discrete files.
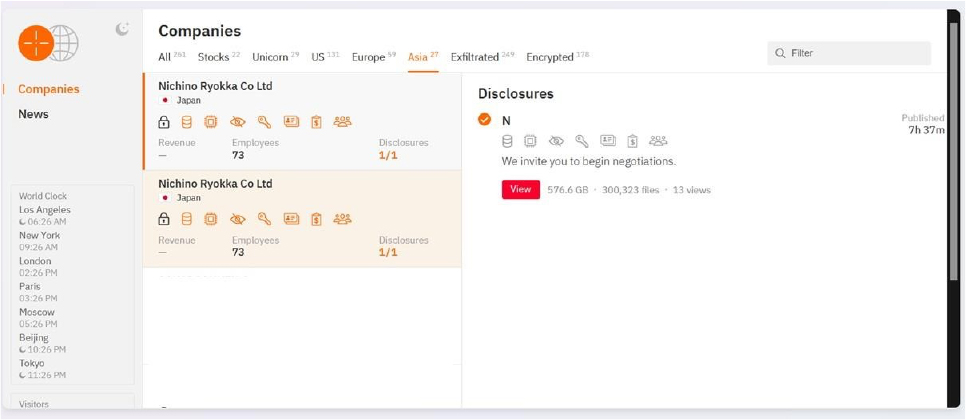
Relevancy & Insights:
ETLM Assessment:
According to CYFIRMA’s assessment, Hunters International ransomware represents a significant threat within the ransomware landscape due to its sophisticated tactics and focus on double extortion strategies. Organizations are advised to enhance their cybersecurity measures by implementing robust backup solutions, conducting regular employee training on phishing awareness, and maintaining updated security protocols to mitigate risks associated with this evolving threat actor. Continuous monitoring of Hunters International’s activities will be essential for understanding its impact on global cybersecurity efforts.
Vulnerability in VMware Fusion
Relevancy & Insights: The vulnerability exists due to a boundary condition in HGFS.
Impact: A malicious guest can trigger an out-of-bound read error and read contents of memory on the system.
Affected Products: https[:]//support[.]Broadcom[.]com/web/ecx/support-content- notification/-/external/content/SecurityAdvisories/0/25390
Recommendations:
Monitoring and Detection: Implement monitoring and detection mechanisms to identify unusual system behavior that might indicate an attempted exploitation of this vulnerability.
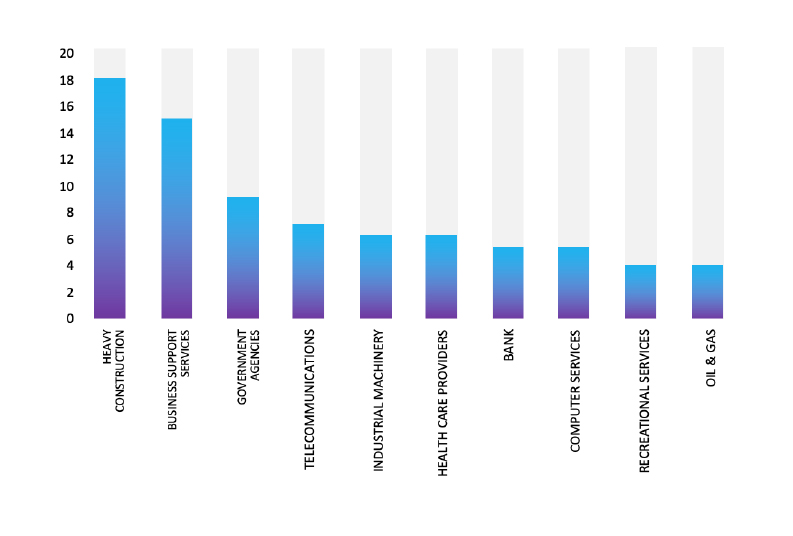
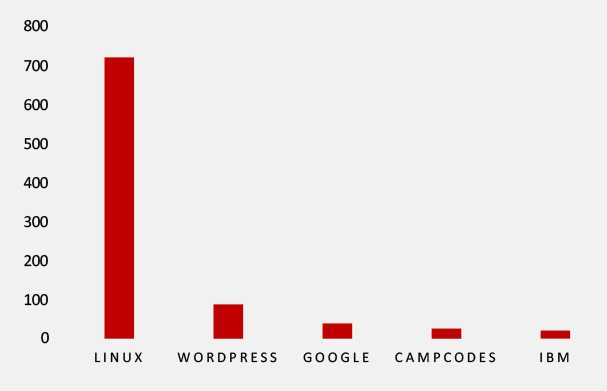
TOP 5 AFFECTED TECHNOLOGIES OF THE WEEK
This week, CYFIRMA researchers have observed significant impacts on various technologies, due to a range of vulnerabilities. The following are the top 5 most affected technologies.
ETLM Assessment
Vulnerability in VMware Fusion can pose significant threats to user privacy and security. This can impact various industries globally, including technology, finance, healthcare, and beyond. Ensuring the security of VMware Fusion is crucial for maintaining the integrity and protection of users’ data worldwide. Therefore, addressing these vulnerabilities is essential to safeguarding virtualization environments, including the secure operation of multiple operating systems on macOS, across different geographic regions and sectors.
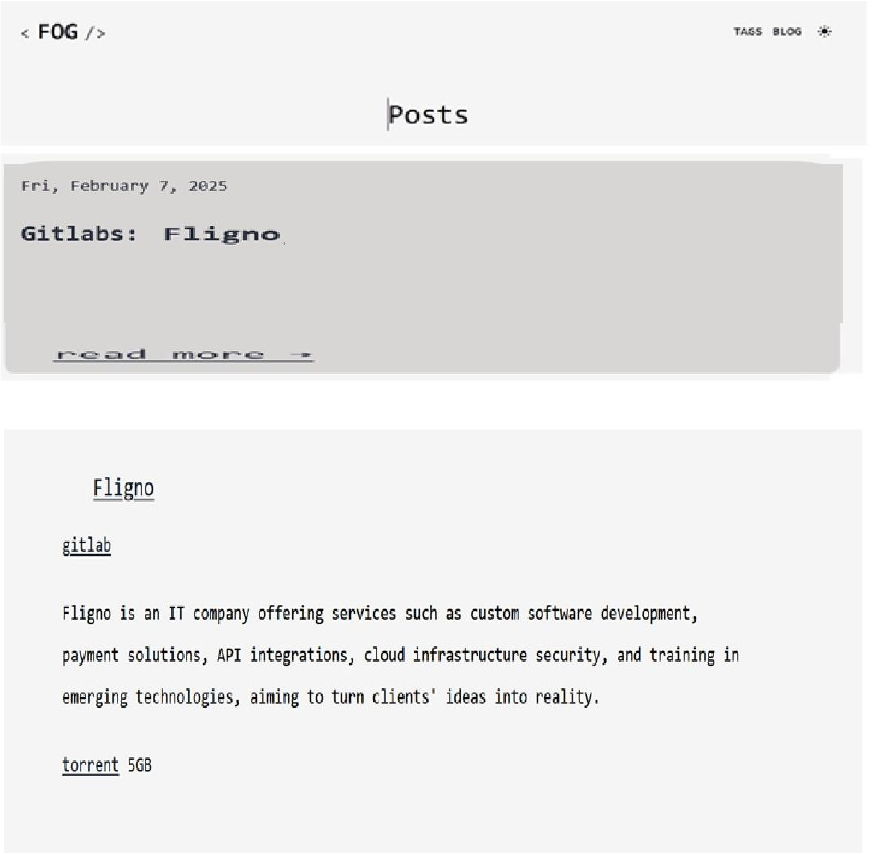
Fog Ransomware attacked and published the data of Fligno
Summary:
Recently, we observed that Fog Ransomware attacked and published the data of Fligno(https[:]//fligno[.]com/) on its dark web website. Fligno is a software development company specializing in various Information Technology services, including mobile and web-based software development, infrastructure, security, server setup and maintenance, website design, and digital marketing. The company operates primarily in the Philippines, serving clients across multiple sectors, such as retail, hospitality, education, fintech, and B2C industries. The company’s main areas of business include debt management, insurance services, credit card applications and hire purchases, corporate businesses and personal loans, assets refinancing plans, and investment portfolios. The data leak, following the ransomware attack, encompasses sensitive and confidential records, originating from the organizational database. The total size of compromised data is approximately 5GB.
Relevancy & Insights:
Fog Ransomware has been observed targeting both Windows and Linux systems, making it a versatile threat.
ETLM Assessment:
CYFIRMA’s assessment indicates that Fog Ransomware, despite utilizing advanced techniques, presents a substantial threat due to its double extortion methods and wide-ranging targets. To effectively reduce the risk of Fog Ransomware attacks, organizations should prioritize strong security measures, including regular data backups, security awareness training, vulnerability management, and comprehensive incident response planning.
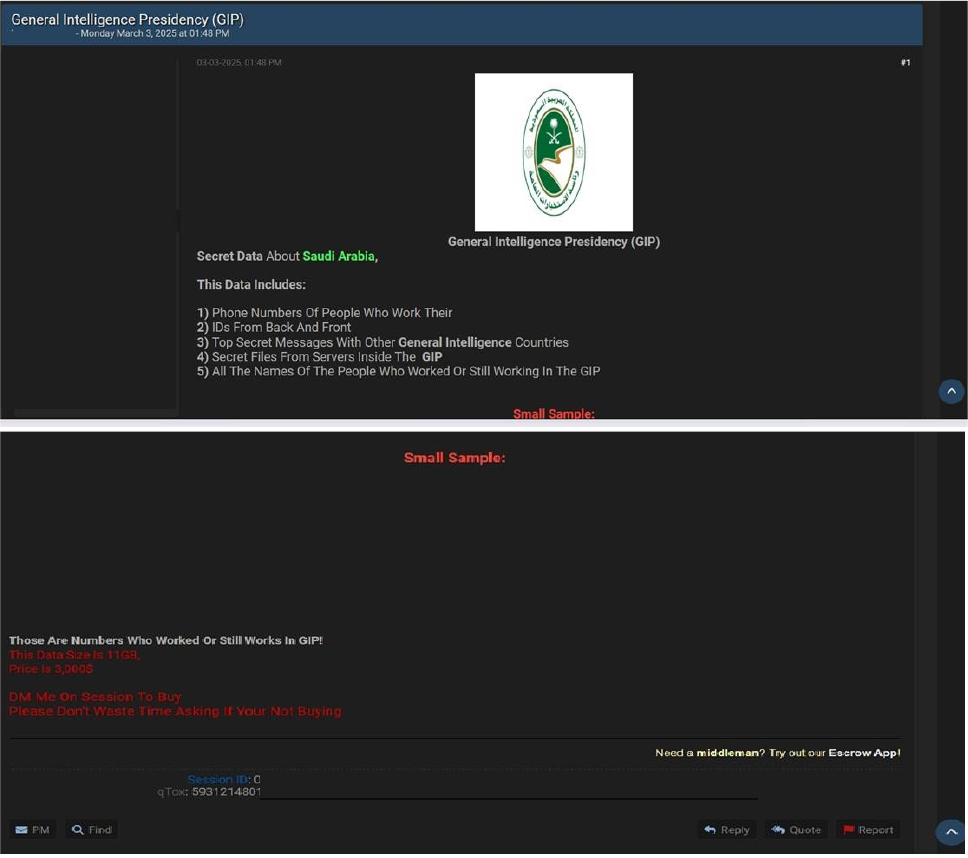
Saudi Arabia’s General Intelligence Presidency (GIP) Data Advertised on a Leak Site
Summary:
The CYFIRMA Research team observed a data sale related to Saudi Arabia’s General Intelligence Presidency (GIP) in an underground forum. Saudi Arabia’s General Intelligence Presidency (GIP) is the country’s primary intelligence agency, responsible for gathering, analyzing, and acting on national security and foreign intelligence. It operates under the authority of the King and is tasked with protecting the Kingdom from external threats, countering terrorism, and ensuring national security. The data for sale includes sensitive files, phone numbers, and secret communications. The total size of data for sale is approximately 11 GB. The asking price for data for sale is 3,000$. The breach has been attributed to a threat actor known as “The_Sn1p3r.”
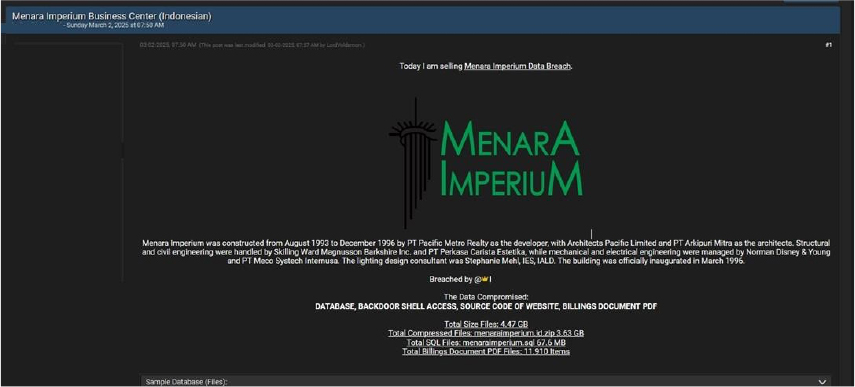
Menara Imperium Business Center (Indonesia) Data Advertised on a Leak Site
Summary:
The CYFIRMA Research team observed a data leak related to the Menara Imperium Business Center (Indonesia) in an underground forum. Menara Imperium is a prominent office building located in Jakarta, Indonesia. Menara Imperium offers office spaces with areas ranging from 100 to 1,519 square meters. The compromised data includes the database, backdoor shell access, website source code, and billing documents in PDF format. The total size of the data leak is approximately 4.47 GB. The breach has been attributed to a threat actor known as “LordVoldemort”.
Relevancy & Insights:
Financially motivated cybercriminals are continuously scouring for exposed and vulnerable systems and applications to exploit. A significant number of these malicious actors congregate within underground forums, where they discuss cybercrime and trade stolen digital assets. Operating discreetly, these opportunistic attackers target unpatched systems or vulnerabilities in applications to illicitly gain access and steal valuable data. Subsequently, the pilfered data is advertised for sale within underground markets, where it can be acquired, repurposed, and utilized by other malicious actors in further illicit activities.
ETLM Assessment:
The threat actor claiming the alias “LordVoldemort” is reportedly involved in acquiring and attempting to sell sensitive data on various underground forums. This activity underscores the persistent risks posed by cyber threat actors who exploit vulnerabilities and engage in data theft. To mitigate these risks, organizations should implement robust security measures, including enhanced monitoring, secure data storage, and regular vulnerability assessments to protect against such malicious activities.
Recommendations: Enhance the cybersecurity posture by:
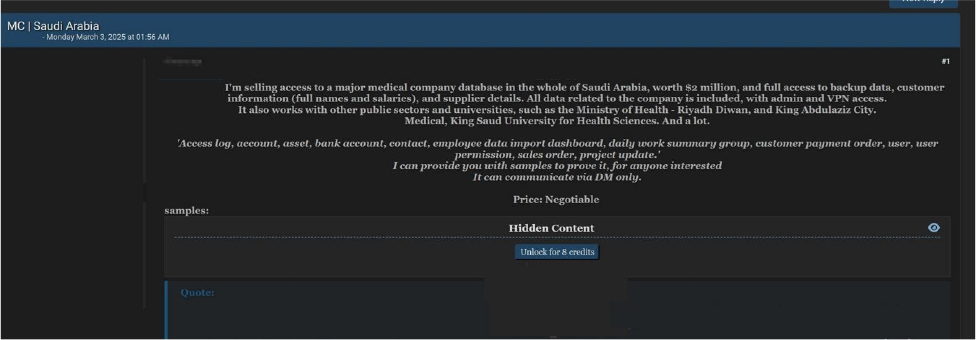
The CYFIRMA Research team observed that on a dark web forum, an alleged cybercriminal operating under the alias “Penmy” has claimed to possess and sell unauthorized access to a major medical company’s database in Saudi Arabia. The individual is purportedly offering full access to backup data, customer information— including full names and salary details—as well as supplier records.
The alleged listing further claims that the compromised entity collaborates with various public sector organizations and academic institutions, including the Ministry of Health – Riyadh Diwan, King Abdulaziz City for Science and Technology, and King Saud University for Health Sciences. According to the post, the data set for sale contains sensitive records such as access logs, user accounts, financial details, and project updates.
The threat actor has allegedly set an asking price of $2 million for the database but stated that the price is negotiable. They also claim to be open to providing samples as proof of the data’s authenticity.
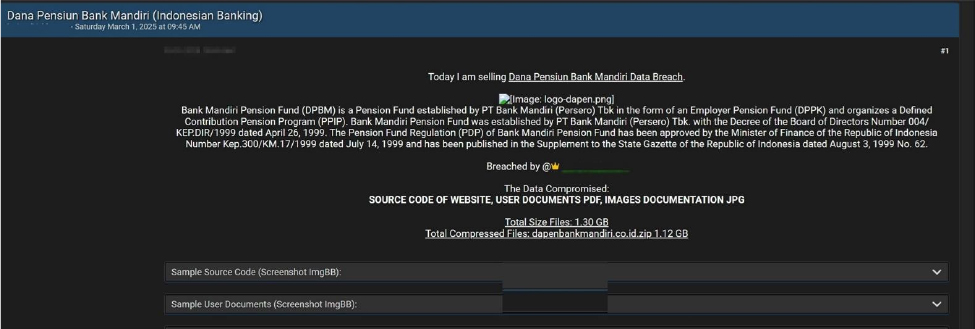
The CYFIRMA Research team observed that a threat actor claims to have compromised the Bank Mandiri Pension Fund, allegedly leaking website source code and user documents. According to the alleged post, the compromised data includes the website’s source code, user documents in PDF format, and image documentation in JPG format. The total size of the exposed files reportedly amounts to 1.30 GB, with a compressed version available for download at approximately 1.12 GB. The breach has been attributed to a threat actor known as “LordVoldemort”.
STRATEGIC RECOMMENDATIONS
MANAGEMENT RECOMMENDATIONS
TACTICAL RECOMMENDATIONS
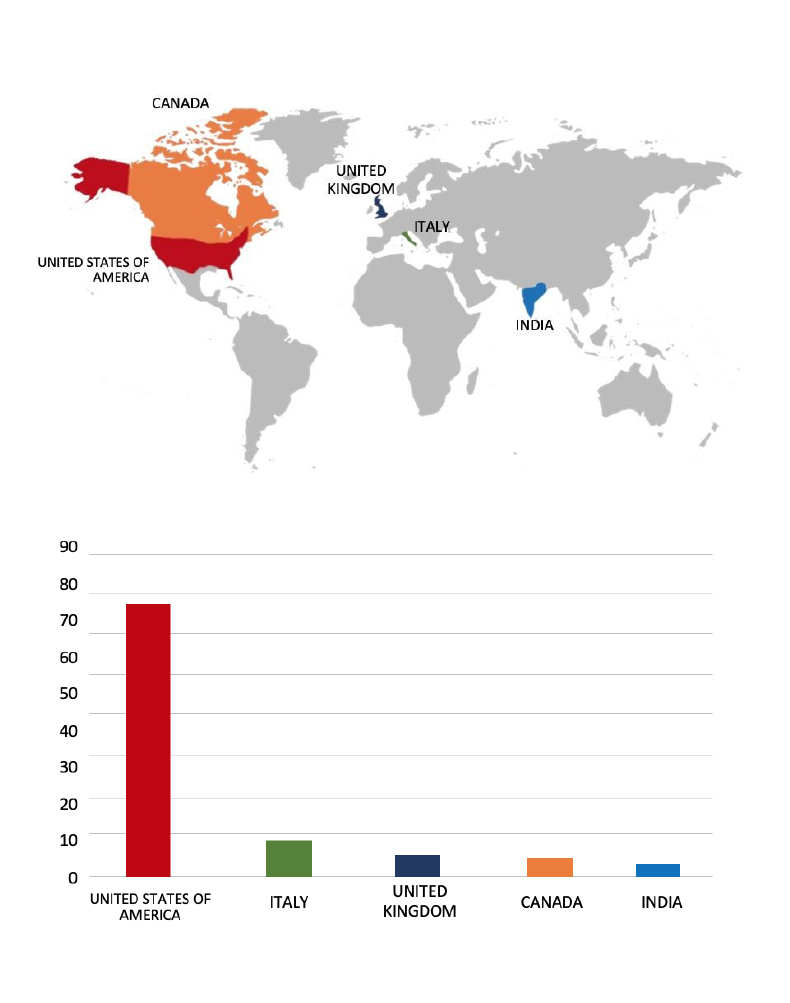
Please find the Geography-Wise and Industry-Wise breakup of cyber news for the last 5 days as part of the situational awareness pillar.
For situational awareness intelligence and specific insights mapped to your organisation’s geography, industry, and technology, please access DeCYFIR.