



CYFIRMA Research and Advisory Team would like to highlight ransomware trends and insights gathered while monitoring various forums. This includes multiple – industries, geography, and technology – that could be relevant to your organization.
Type: Ransomware
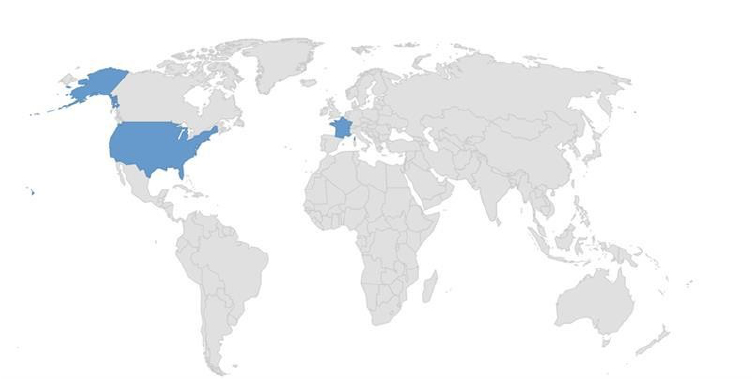
Target Technologies: MS Windows
Target Geography: France, USA
Target Industry: Government, Manufacturing, Pharma
Introduction
CYFIRMA Research and Advisory Team has found VanHelsing Ransomware while monitoring various underground forums as part of our Threat Discovery Process.
VanHelsing
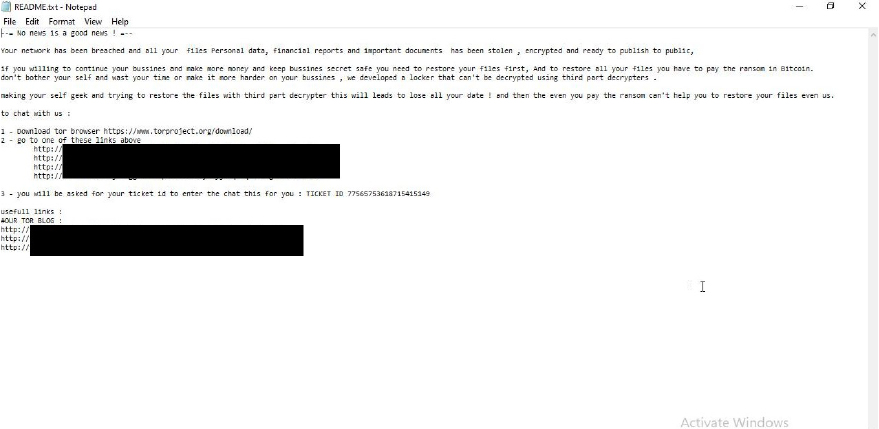
VanHelsing is a new ransomware strain that encrypts files and demands payment for decryption. It also employs double extortion tactics, threatening to leak stolen data to pressure victims into paying. Once executed, VanHelsing appends the “.vanhelsing” extension to encrypted files, modifies the desktop wallpaper, and drops a ransom note named “README.txt” on the victim’s system.

Following are the TTPs based on the MITRE Attack Framework
| Tactic | ID | Technique |
| Execution | T1047 | Windows Management Instrumentation |
| Execution | T1053 | Scheduled Task/Job |
| Execution | T1059 | Command and Scripting Interpreter |
| Execution | T1129 | Shared Modules |
| Persistence | T1053 | Scheduled Task/Job |
| Persistence | T1542.003 | Pre-OS Boot: Bootkit |
| Persistence | T1543.003 | Create or Modify System Process: Windows Service |
| Persistence | T1547.001 | Boot or Logon Autostart Execution: Registry Run Keys / Startup Folder |
| Persistence | T1574.002 | Hijack Execution Flow: DLL Side-Loading |
| PrivilegeEscalation | T1053 | Scheduled Task/Job |
| PrivilegeEscalation | T1055 | Process Injection |
| PrivilegeEscalation | T1543.003 | Create or Modify System Process: Windows Service |
| PrivilegeEscalation | T1547.001 | Boot or Logon Autostart Execution: Registry Run Keys / Startup Folder |
| PrivilegeEscalation | T1548 | Abuse Elevation Control Mechanism |
| PrivilegeEscalation | T1574.002 | Hijack Execution Flow: DLL Side-Loading |
| Defense Evasion | T1006 | Direct Volume Access |
| Defense Evasion | T1014 | Rootkit |
| Defense Evasion | T1027.002 | Obfuscated Files or Information: Software Packing |
| Defense Evasion | T1036 | Masquerading |
| Defense Evasion | T1055 | Process Injection |
| DefenseEvasion | T1070 | Indicator Removal |
| Defense Evasion | T1112 | Modify Registry |
| Defense Evasion | T1202 | Indirect Command Execution |
| Defense Evasion | T1222 | File and Directory Permissions Modification |
| Defense Evasion | T1542.003 | Pre-OS Boot: Bootkit |
| DefenseEvasion | T1548 | Abuse Elevation Control Mechanism |
| Defense Evasion | T1564.001 | Hide Artifacts: Hidden Files and Directories |
| Defense Evasion | T1564.003 | Hide Artifacts: Hidden Window |
| Defense Evasion | T1574.002 | Hijack Execution Flow: DLL Side-Loading |
| CredentialAccess | T1003 | OS Credential Dumping |
| CredentialAccess | T1552.001 | Unsecured Credentials: Credentials In Files |
| Discovery | T1012 | Query Registry |
| Discovery | T1057 | Process Discovery |
| Discovery | T1082 | System Information Discovery |
| Discovery | T1083 | File and Directory Discovery |
| Discovery | T1135 | Network Share Discovery |
| Discovery | T1518.001 | Software Discovery: Security Software Discovery |
| Collection | T1005 | Data from Local System |
| Collection | T1114 | Email Collection |
| Collection | T1213 | Data from Information Repositories |
| Command and Control | T1071 | Application Layer Protocol |
| Command and Control | T1090 | Proxy |
| Command and Control | T1105 | Ingress Tool Transfer |
| Impact | T1485 | Data Destruction |
| Impact | T1486 | Data Encrypted for Impact |
| Impact | T1490 | Inhibit System Recovery |
| Impact | T1496 | Resource Hijacking |
Relevancy and Insights:
ETLM Assessment:
Based on available data, CYFIRMA’s assessment suggests that VanHelsing ransomware, which has already impacted the U.S. and France, is emerging as a global threat. Its evolving tactics suggest expansion beyond government and manufacturing to critical industries like finance healthcare and others. The double extortion approach heightens its risk, making essential sectors worldwide more vulnerable. Strengthening cybersecurity defenses is crucial to mitigating potential attacks.
Sigma Rule
title: Shadow Copies Deletion Using Operating Systems Utilities tags:
– attack.defense-evasion
– attack.impact
– attack.t1070
– attack.t1490 logsource:
category: process_creation product: windows
detection: selection1_img:
– Image|endswith:
– ‘\powershell.exe’
– ‘\pwsh.exe’
– ‘\wmic.exe’
– ‘\vssadmin.exe’
– ‘\diskshadow.exe’
– OriginalFileName:
– ‘PowerShell.EXE’
– ‘pwsh.dll’
– ‘wmic.exe’
– ‘VSSADMIN.EXE’
– ‘diskshadow.exe’ selection1_cli:
CommandLine|contains|all:
– ‘shadow’ # will match “delete shadows” and “shadowcopy delete” and “shadowstorage”
– ‘delete’ selection2_img:
– Image|endswith: ‘\wbadmin.exe’
– OriginalFileName: ‘WBADMIN.EXE’ selection2_cli:
CommandLine|contains|all:
– ‘delete’
– ‘catalog’
– ‘quiet’ # will match -quiet or /quiet selection3_img:
– Image|endswith: ‘\vssadmin.exe’
– OriginalFileName: ‘VSSADMIN.EXE’ selection3_cli:
CommandLine|contains|all:
– ‘resize’
– ‘shadowstorage’ CommandLine|contains:
– ‘unbounded’
– ‘/MaxSize=’
condition: (all of selection1*) or (all of selection2*) or (all of selection3*) fields:
– CommandLine
– ParentCommandLine falsepositives:
– Legitimate Administrator deletes Shadow Copies using operating systems utilities for legitimate reason
– LANDesk LDClient Ivanti-PSModule (PS EncodedCommand) level: high
(Source: Surface web)
IOCs:
Kindly refer to the IOCs section to exercise controls on your security systems.
STRATEGIC RECOMMENDATION
MANAGEMENT RECOMMENDATION
TACTICAL RECOMMENDATION
Type: Spyware | Objectives: Espionage, Data Exfiltration |Threat Actor: ScarCruft (aka APT37) | Target Technology: Android OS CYFIRMA collects data from various forums based on which the trend is ascertained. We identified a few popular malwares that were found to be distributed in the wild to launch cyberattacks on organizations or individuals.
Active Malware of the Week
This week “KoSpy” is trending.
KoSpy
Researchers have identified KoSpy, an Android spyware designed to target Korean and English-speaking users. Attributed to the North Korean APT group ScarCruft (aka APT37) with medium confidence, this malware has been active since at least March 2022, with new samples still being discovered in the wild. ScarCruft, a state-sponsored cyber espionage group active since 2012, primarily targets South Korea but has also carried out operations in Japan, Vietnam, Russia, India, and several Middle Eastern nations. KoSpy is distributed through deceptive utility applications and leverages a two-stage command- and-control (C2) infrastructure, retrieving its initial configurations from a Firebase cloud database. Spyware has Korean language support with samples distributed across Google Play and third-party app stores such as Apkpure. Once installed, it can collect various data, including SMS messages, call logs, location details, files, audio recordings, and screenshots using dynamically loaded plugins.
Attack Method
KoSpy spreads through fake utility applications designed to appear legitimate, including Phone Manager, File Manager, Smart Manager, Kakao Security, and Software Update Utility. These apps mimic real functionalities to avoid suspicion. While some, like File Manager, operate as basic file browsers, others, such as Software Update Utility, simply open existing system settings to appear authentic. The Kakao Security app, however, lacks any real functionality and instead displays a fake system window while requesting extensive permissions, likely to facilitate spyware activities.
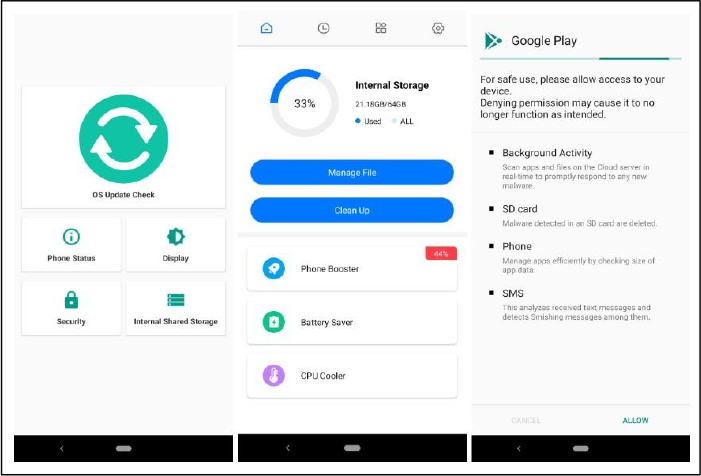
Behind the basic interface, KoSpy activates its spyware functions by retrieving an encrypted configuration from Firebase Firestore. This configuration includes an on/off switch and the Command-and-Control (C2) server address, allowing the operators to remotely enable or disable the malware or switch servers if detected or blocked. To evade detection, KoSpy first ensures that the device is not an emulator and delays execution until a predefined activation date, allowing it to remain dormant until the right time.
KoSpy communicates with its Command-and-Control (C2) server through two types of requests: one for downloading plugins and another for retrieving configuration settings related to its surveillance functions. While the plugin request is designed to receive an encrypted and compressed binary, this could not be confirmed due to inactive C2 servers during analysis. The configuration request, however, is expected to return a JSON document that defines parameters such as C2 ping frequency, user messages in Korean and English, and plugin download details. KoSpy sends data to its C2 server using HTTP POST requests, with the information formatted in JSON. Instead of encrypting the entire request, only the content is encrypted, while field names remain readable, allowing for structured data extraction by its operators. These requests include a unique victim ID based on device details, a request type indicating whether it is for configuration or code execution, and system-related information such as app version, device language, and enabled permissions.
Capabilities of KoSpy
KoSpy leverages dynamically loaded plugins to gather a wide range of sensitive information from infected devices. Its capabilities include:
KoSpy encrypts collected data using a hardcoded AES key before transmitting it to its C2 servers. During analysis, researchers identified five Firebase projects and five C2 servers associated with different KoSpy samples.
Targeting and Distribution
Researchers determined that the KoSpy campaign targeted Korean and English-speaking users, as more than half of the apps had Korean titles and supported both languages. The app’s interface displayed text in Korean when the device language was set accordingly; otherwise, it appeared in English.
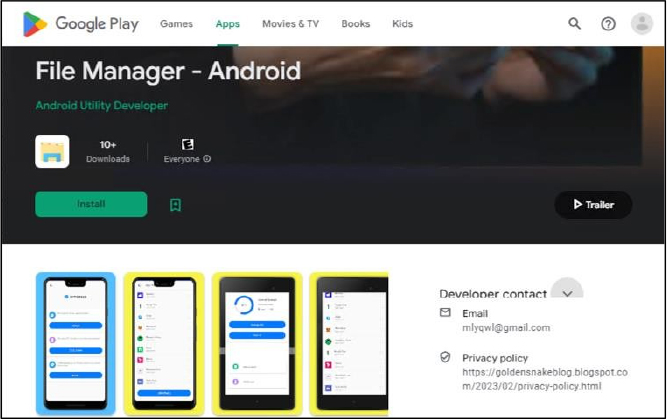
Some KoSpy samples were available for download on Google Play Store and the third-party store Apkpure, though they are no longer publicly accessible on Google Play. A snapshot of the Play Store listing for the File Manager app (com.file.exploer) revealed that it was previously available, had over ten downloads, and was linked to a developer account named “Android Utility Developer.” The listing also included a privacy policy hosted on an external blog, a developer contact email, and a promotional YouTube video uploaded to the @filemanager-android channel.
KoSpy’s Links to North Korean APTs
Researchers found that KoSpy’s infrastructure overlaps with previous malicious activities linked to North Korean threat groups APT37 and APT43. One of its C2 domains, st0746[.]net, was traced to an IP address in South Korea, which has been associated with suspicious Korea-related domains in the past. Notably, some of these domains were previously tied to Konni malware, a Windows RAT used by APT37, and Thallium’s (APT43) command-and-control infrastructure. Due to shared infrastructure, targeting similarities, and recent connections, researchers attribute this KoSpy activity to APT37 with medium confidence. The overlap in infrastructure between APT37 and APT43 highlights the challenge of attributing North Korean cyber operations, as these groups often reuse resources and tactics across campaigns.
INSIGHTS
ETLM ASSESSMENT
From the ETLM perspective, CYFIRMA anticipates that KoSpy’s discovery highlights a future where spyware becomes increasingly stealthy and difficult to eradicate. APT37’s ability to infiltrate Google Play once suggests they could do so again, likely with even more sophisticated evasion techniques. While this campaign had a small number of downloads, the real danger isn’t in the counties of who the victims are. If even one high-value individual, such as a government official or corporate executive, unknowingly installs the malware, the consequences could be severe, leading to intelligence leaks or security breaches. As mobile devices remain central to business operations, attackers may shift towards embedding spyware into trusted workplace applications, making threats harder to identify. Future variants of KoSpy could evolve to extract more sensitive data, including encrypted communications and authentication details, amplifying the risk to enterprise security. Its focus on Korean and English-speaking users hints at a broader expansion, potentially spreading through repackaged malware in third-party stores or exploiting platform vulnerabilities. With attack methods growing more deceptive, waiting to respond after an incident may no longer be an option— proactive mobile security is now a necessity.
IOCs:
Kindly refer to the IOCs Section to exercise controls on your security systems.
STRATEGIC:
MANAGEMENT:
TACTICAL RECOMMENDATIONS
Key Intelligence Signals:
The ClickFix Trick: Storm-1865’s Malware-Driven Phishing Campaign
SUMMARY
Researchers have identified an ongoing phishing campaign orchestrated by the threat actor Storm-1865, targeting organizations in the hospitality industry. The campaign, active since December 2024, impersonates the online travel agency Booking.com and employs a sophisticated social engineering technique called ClickFix. This technique manipulates users into executing malicious commands, leading to the delivery of credential-stealing malware such as XWorm, Lumma Stealer, VenomRAT, AsyncRAT, Danabot, and NetSupport RAT. The primary objective of the campaign is financial fraud and theft, with a focus on stealing payment data and credentials for fraudulent use.
Storm-1865 leverages phishing emails that impersonate Booking.com, using varied lures such as negative guest reviews, account verification requests, and promotional opportunities. These emails contain links or PDF attachments that redirect users to fake CAPTCHA pages designed to mimic legitimate Booking.com pages. The ClickFix technique then prompts users to open a Windows Run window, paste a malicious command, and execute it, resulting in the download of malware. This method exploits human problem-solving tendencies and bypasses conventional security measures by requiring user interaction. The campaign has evolved from earlier tactics used in 2023 and 2024, where Storm-1865 targeted hotel guests and e- commerce buyers with simpler phishing techniques.
The campaign specifically targets hospitality organizations in North America, Oceania, South and Southeast Asia, and Northern, Southern, Eastern, and Western Europe. These regions were chosen due to their high likelihood of interaction with Booking.com. The hospitality industry remains the primary focus, as it provides access to payment data and credentials that can be exploited for financial fraud. Previous campaigns in 2023 and 2024 also targeted similar regions, indicating a consistent geographical focus for Storm-1865’s operations.
Relevancy & Insights:
Storm-1865 has a history of conducting phishing campaigns targeting the hospitality and e-commerce sectors. In 2023, the threat actor primarily targeted hotel guests using Booking.com, employing phishing emails to steal credentials and payment data. The attacks were focused on regions such as North America, Europe, and Southeast Asia, similar to the current campaign. In 2024, Storm-1865 shifted its focus to e-commerce platforms, using phishing messages to redirect buyers to fraudulent payment pages. These campaigns also targeted the same geographical regions, indicating a consistent preference for high-traffic areas with significant financial transactions.
The current campaign (2024-2025) marks an evolution in Storm-1865’s tactics with the introduction of the ClickFix technique. While the target regions remain consistent, North America, Oceania, South and Southeast Asia, and Europe—the threat actor has refined its approach to bypass conventional security measures.
Unlike previous campaigns, which relied on simpler phishing techniques, the use of ClickFix demonstrates a more sophisticated exploitation of human behavior. This evolution highlights Storm-1865’s adaptability and persistence in achieving its objective of financial fraud and theft. The consistent targeting of the hospitality industry and overlapping geographical focus underscore the threat actor’s strategic approach to maximizing impact.
ETLM Assessment:
The threat actor Storm-1865 specializes in phishing campaigns aimed at financial fraud and theft. Active since at least early 2023, Storm-1865 has consistently targeted high-traffic regions, including North America, Oceania, South and Southeast Asia, and Northern, Southern, Eastern, and Western Europe. These regions are chosen for their significant financial transactions and interaction with platforms like Booking.com. The campaign primarily targets the hospitality industry, including hotels and travel agencies, due to their access to payment data and credentials. In 2024, the threat actor expanded its focus to include e-commerce platforms, leveraging advanced social engineering techniques like ClickFix to manipulate users into executing malicious commands via fake CAPTCHA pages and phishing emails.
The campaign delivers multiple families of commodity malware, including XWorm, Lumma Stealer, VenomRAT, AsyncRAT, Danabot, and NetSupport RAT, designed to steal credentials and financial data. The evolution of Storm-1865’s tactics, from simple phishing in 2023 to the sophisticated ClickFix technique in 2024-2025, highlights the actor’s adaptability and the growing sophistication of its attack chains.
Strategic Recommendations
Adopt a Comprehensive Cybersecurity Framework:
User Education and Awareness Campaign:
Cyber Resilience & Incident Response:
Tactical Recommendations
Enhanced Email Filtering and Detection:
Multi-Factor Authentication (MFA):
Endpoint Detection and Response (EDR):
Network Segmentation and Zero-Trust Access:
Operational Recommendations
Regular Phishing Simulations:
Intelligence Sharing and Collaboration:
Automated Phishing Detection and Response:
Review and Tighten Endpoint and Network Policies:
| MITRE FRAMEWORK | ||
| Tactic | ID | Technique |
| Initial Access | T1566 | Phishing |
| Execution | T1204 | User Execution |
| Persistence | T1053 | Scheduled Task/Job |
| Defense Evasion | T1070 | Indicator Removal |
| Credential Access | T1003 | OS Credential Dumping |
| Discovery | T1082 | System Information Discovery |
| Collection | T1113 | Screen Capture |
| Command and Control | T1071 | Application Layer Protocol |
| Exfiltration | T1041 | Exfiltration Over C2 Channel |
IOCs:
Kindly refer to the IOCs (Indicators of Compromise) Section to exercise controls on your security systems.
EU warns of rising threat from cyber privateers levering AI.
Europol, the EU’s law enforcement agency, has warned that criminal organizations are increasingly leveraging artificial intelligence to carry out attacks on behalf of hostile state actors, presenting an “unprecedented” security challenge for national governments.
In its latest report on organized crime threats, Europol highlighted how criminals are becoming proxies in hybrid attacks, such as acts of sabotage allegedly linked to Russia and China. “Geopolitical tensions have created an opportunity for hybrid threat actors to exploit criminal networks as instruments of interference,” Europol stated, noting the destabilizing impact on EU nations.
AI, alongside technologies like blockchain and quantum computing, is acting as a “catalyst” for crime, enhancing the efficiency, reach, and sophistication of criminal operations. AI-driven attacks are becoming more precise and devastating. Some incidents combine financial motives with efforts to destabilize, as they increasingly align with state interests and ideological agendas.
Cyberattacks are now more politically motivated, targeting governments and critical infrastructure rather than businesses or individuals. Criminal groups, often working for state actors such as Russia, are exploiting vulnerabilities—particularly those introduced by government contractors—to infiltrate secure systems.
The increasing use of AI marks a significant shift from Europol’s 2021 report, which mentioned AI only once. The technology is now being used to create advanced malware for cyberattacks and generate highly targeted messages designed to deceive victims. For example, AI can mimic voices, and writing styles, or even produce deep-fake videos to impersonate family and friends. AI has also accelerated online fraud, aiding criminals in accessing personal data through automated phishing attacks.
ETLM Assessment:
The Europol report echoes sentiments expressed by CYFIRMA before. Strained by the demands of an all-out war against Ukraine, Russia has increasingly outsourced cyber operations to privateers and other non-state actors. These groups, often beyond direct state control, introduce a heightened unpredictability to their activities. This trend is likely to persist, as the Kremlin grants these actors greater latitude. From Moscow’s perspective, fostering global instability serves to divert attention from its aggression in Ukraine, further stretching the resources of those who oppose it.
Europe’s telecoms sector is under pressure from foreign adversaries
Denmark’s cybersecurity agency issued a threat assessment, warning of an increase in state-sponsored cyber espionage targeting Europe’s telecommunications sector. This marks the first public warning from a European government agency indicating shared concerns with the United States over a Chinese spying campaign known as Salt Typhoon. However, Danish authorities did not explicitly mention Salt Typhoon or China.
While European governments and businesses have yet to confirm Salt Typhoon activity in the region, a senior U.S. official stated last year that European targets had been compromised by the Chinese campaign.
Raising the threat level to “high,” Denmark’s cybersecurity agency noted that “there have been several attempts at cyber espionage against the European telecommunications sector in the past few years” due to “increased interest in the sector by state-sponsored hackers.”
The Salt Typhoon campaign first came to light in the U.S. when hackers intercepted communications of senior officials from both 2024 presidential campaigns, including Donald Trump and JD Vance. Researchers have also linked Salt Typhoon to attacks on telecommunications companies in Southeast Asia.
Denmark’s threat assessment stated that “foreign states seek access to vast amounts of data on customers’ use of telecommunications infrastructure,” which “can be used to monitor communications and travel activities, as well as conduct further espionage.”
Earlier this month, Canadian intelligence warned that China was collecting “billions of data points on democratic politicians, public figures, and citizens worldwide.” This warning came after the U.S. announced dozens of criminal charges against Chinese government-affiliated hackers. These charges exposed a cyber intrusion ecosystem where commercial hacking groups sell access to networks and stolen data to China’s intelligence services.
France’s cybersecurity agency, ANSSI, reported dealing with multiple cyber incidents targeting the country’s telecommunications sector over the past two years for espionage purposes. However, it did not attribute these incidents to specific actors or issue an alert as Denmark did.
ETLM Assessment:
While some governments may lack the political motivation to publicly attribute cyber threats to China or even Russia, even if evidence suggests their involvement, researchers point out the fact that Russia and China have the technical sophistication, and are world champions in using cyber espionage as a tool of statecraft and are together responsible for the majority of cyber-attacks on Europe, both for geopolitics-driven espionage purposes and for programmes of state- organized intellectual property theft.
The NightSpire Ransomware Impacts Tohpe Corporation
Summary:
From the External Threat Landscape Management (ETLM) Perspective, CYFIRMA observed in an underground forum that a company from Japan; Tohpe Corporation (www[.]tohpe[.]co[.]jp), was compromised by NightSpire Ransomware. Tohpe Corporation is a Japanese company specializing in the manufacture and sale of paints and high-performance materials. The compromised data consists of confidential and sensitive information related to the organization. The total size of the compromised data is approximately 159 GB.
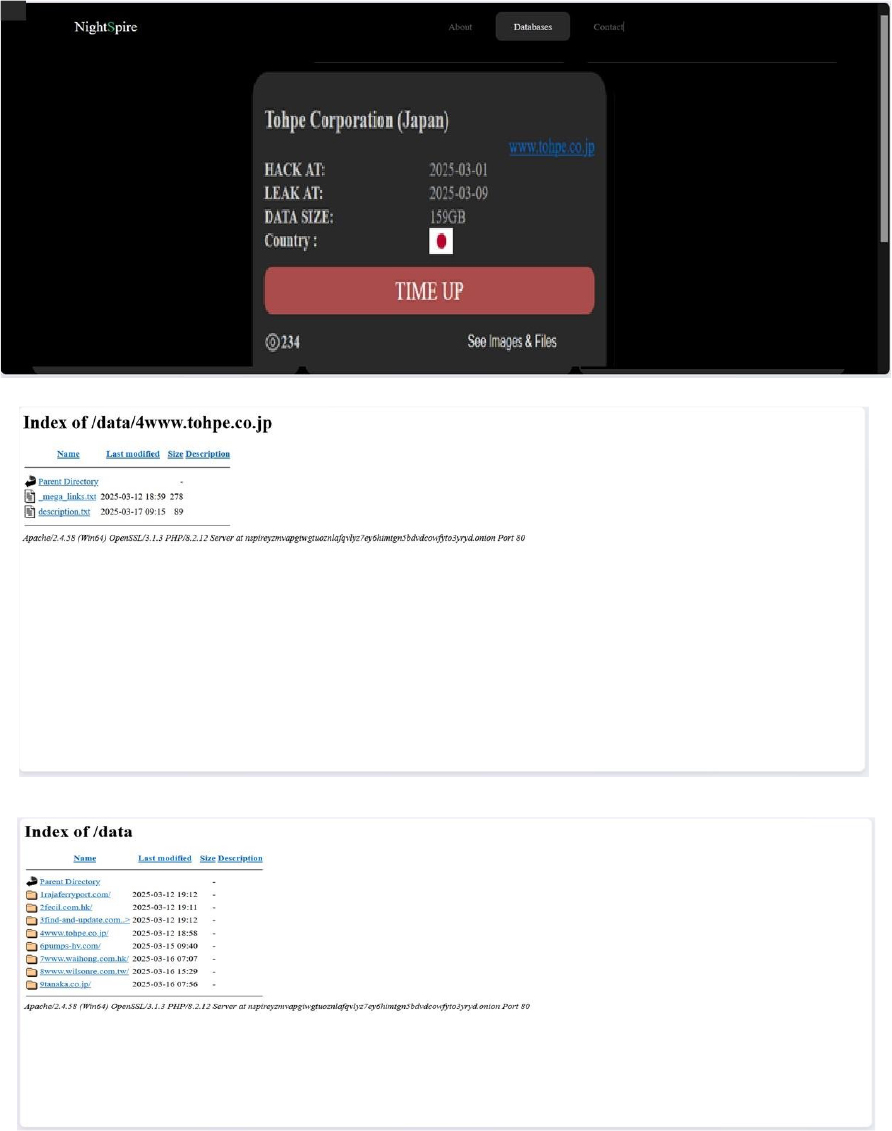
Relevancy & Insights:
ETLM Assessment:
According to CYFIRMA’s assessment, NightSpire is a new ransomware group that emerged in early 2025, marking itself as a formidable player in the rapidly evolving ransomware landscape. Despite its recent appearance, NightSpire has already gained attention for its aggressive tactics and well-structured operations.
The RansomHub Ransomware Impacts HexoSys Group
Summary:
From the External Threat Landscape Management (ETLM) Perspective, CYFIRMA observed in an underground forum that a company from Malaysia; HexoSys Group (www[.]hexosys[.]com) was compromised by RansomHub Ransomware. HexoSys is a technology company specializing in providing engineering services to high-tech industries. The company has over two decades of experience in delivering cutting-edge solutions in software development, FPGA (Field-Programmable Gate Array) design and implementation, and firmware design. The compromised data contains contracts, blueprints, Linux shares, source codes, source code tests, competitors’ research, product development data, employee data (contracts, salaries, cars, families, etc), and other sensitive data. The total size of the compromised data is approximately 336 GB.
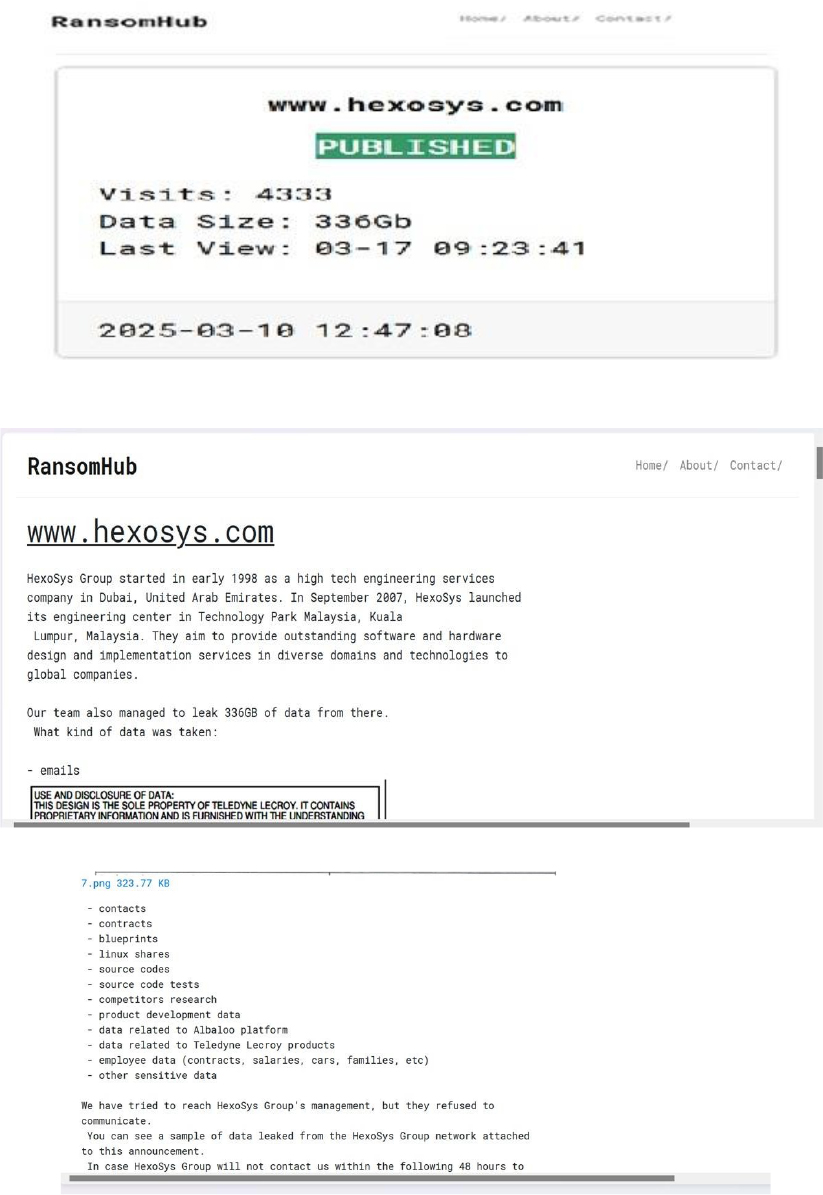
Relevancy & Insights:
ETLM Assessment:
According to recent assessments by CYFIRMA, RansomHub ransomware has rapidly emerged as a significant player in the ransomware landscape since its inception in February 2024. This Ransomware-as-a-Service (RaaS) group has gained notoriety for its sophisticated tactics and cross-platform capabilities, targeting a wide range of sectors including healthcare, finance, and critical infrastructure. RansomHub’s success can be attributed to its ability to adapt and evolve, leveraging advanced evasion techniques and exploiting vulnerabilities in enterprise infrastructure.
Vulnerability in NI Vision Builder AI
Relevancy & Insights:
The vulnerability exists due to the affected application allowing the execution of dangerous scripts without user warning.
Impact:
A remote attacker can trick a victim to open a specially crafted VBAI file and execute arbitrary code on the target system.
Affected Products:
https[:]//www[.]zerodayinitiative[.]com/advisories/ZDI-25-147/
Recommendations:
Monitoring and Detection: Implement monitoring and detection mechanisms to identify unusual system behavior that might indicate an attempted exploitation of this vulnerability.
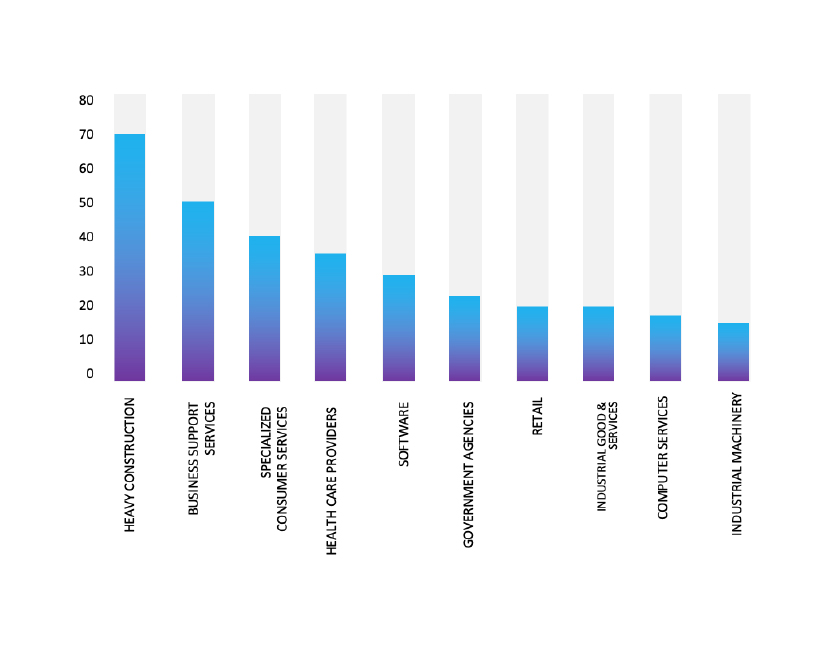
TOP 5 AFFECTED TECHNOLOGIES OF THE WEEK
This week, CYFIRMA researchers have observed significant impacts on various technologies, due to a range of vulnerabilities. The following are the top 5 most affected technologies.
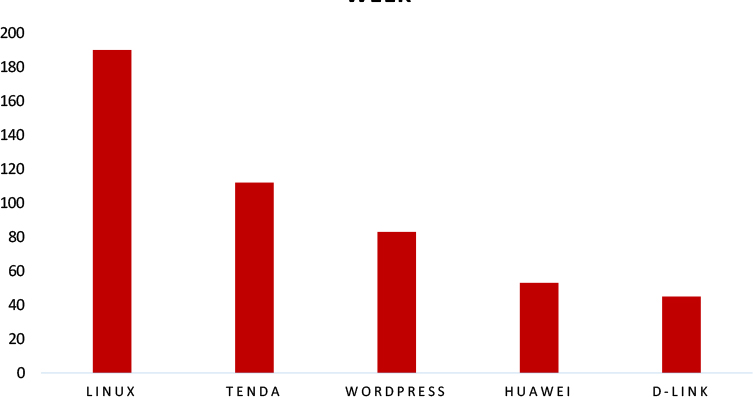
ETLM Assessment
Vulnerability in NI Vision Builder AI (VBAI) File Processing can pose significant threats to user privacy and security. This can impact various industries globally, including manufacturing, healthcare, and automation. Ensuring the security of NI Vision Builder AI is crucial for maintaining the integrity and protection of users’ data worldwide. Therefore, addressing this remote code execution (RCE) vulnerability is essential to safeguarding AI-driven vision processing systems, preventing unauthorized code execution via malicious files or web pages, and ensuring secure operations across different geographic regions and sectors.
Lynx Ransomware attacked and published the data of Indiv USA
Summary
Recently, we observed that Lynx Ransomware attacked and published the data of Indiv USA (https[:]//indivusa[.]com/) on its dark web website. INDIV has been a leading export company, supplying customers in Central America, South America, the Caribbean and Asia. INDIV, whose headquarters is located in Springfield, Missouri, USA, has production facilities in the USA, Argentina and Mexico, and regional sales offices in Colombia, Malaysia, and Venezuela, along with distributors in various other countries. INDIV develops, manufactures, and distributes complete poultry raising systems as well as helps to analyze the different technical- economical alternatives and layouts according to various investment options.
The data leak, following the ransomware attack, encompasses Contracts, HR, Financial data, Customer data, and Incidents. The total size of compromised data is approximately 36 GB.
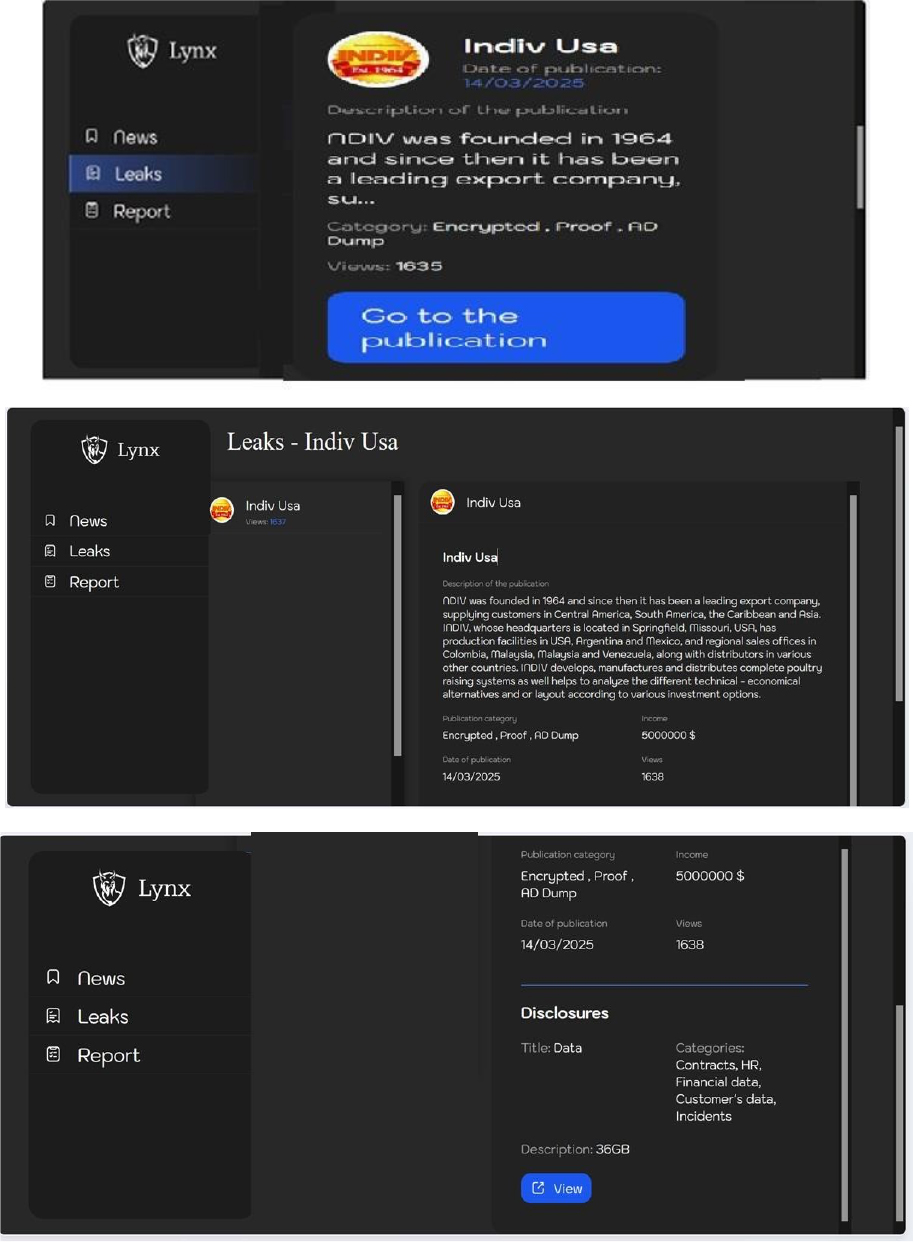
Relevancy & Insights:
ETLM Assessment:
According to CYFIRMA’s assessment, Lynx ransomware has emerged as a significant threat in the cybersecurity landscape, leveraging advanced encryption and double extortion tactics to target small and medium-sized businesses. Its structured affiliate program and versatile ransomware toolkit make it a formidable force in the RaaS ecosystem.
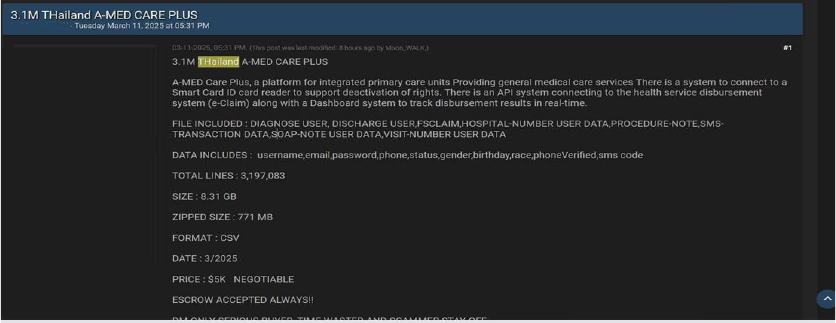
A-MED Care Plus Thailand Data Advertised on a Leak Site
Summary:
The CYFIRMA Research team observed a data sale related to A-MED Care Plus in an underground forum. A-MED Care is a digital healthcare platform developed by Thailand’s National Science and Technology Development Agency (NSTDA) to enhance the efficiency of healthcare services within the National Health Security Office (NHSO) system. The compromised files contain Diagnose User data, Discharge User data, FSClaim, Hospital Number User data, Procedure Notes, SMS Transaction data, SOAP Note User data, and Visit Number User data. The compromised data includes username, email, password, phone number, account status, gender, date of birth, race, phone verification status, and SMS code. The total size of the compromised data is approximately 8.31 GB in CSV format. The data is being offered for sale at an asking price of $5,000. The breach has been linked to a threat actor identified as “Moon WALK.”
KOPTEL Telkom Cooperative Indonesia Data Advertised on a Leak Site
Summary:
The CYFIRMA Research team observed a data sale related to the KOPTEL Telkom Cooperative Indonesia(https[:]//koptel[.]co[.]id/) in an underground forum. KOPTEL (Koperasi Telekomunikasi) is a secondary cooperative under the auspices of PT. Telkom Indonesia. It serves as a secondary cooperative within PT. Telkom Indonesia, with members comprising KOPEGTEL cooperatives across Indonesia. The compromised data includes the website’s database and source code. The source code has a total size of 97.2 MB, while the database, stored in SQL format, is 57.7 MB. The data is being offered for sale at a price of $1,000. The breach has been linked to a threat actor identified as “Lord Voldemort.”
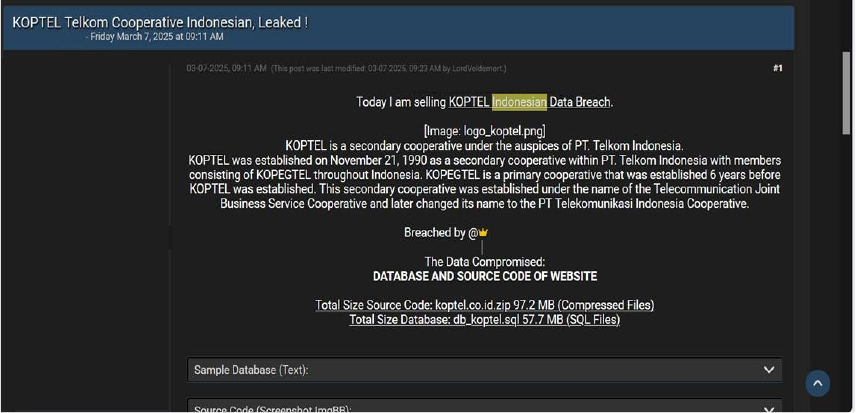
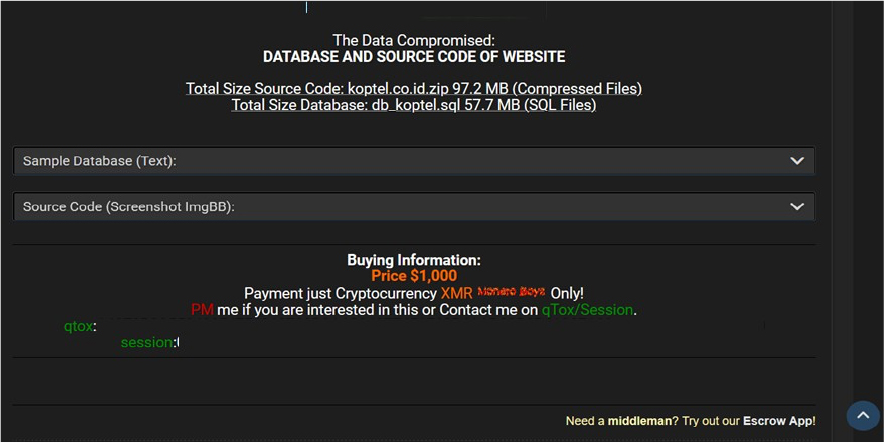
Relevancy & Insights:
Financially motivated cybercriminals are continuously scouring for exposed and vulnerable systems and applications to exploit. A significant number of these malicious actors congregate within underground forums, where they discuss cybercrime and trade stolen digital assets. Operating discreetly, these opportunistic attackers target unpatched systems or vulnerabilities in applications to illicitly gain access and steal valuable data. Subsequently, the pilfered data is advertised for sale within underground markets, where it can be acquired, repurposed, and utilized by other malicious actors in further illicit activities.
ETLM Assessment:
The threat actor claiming the alias “Lord Voldemort” is reportedly involved in acquiring and attempting to sell sensitive data on various underground forums. This activity underscores the persistent risks posed by cyber threat actors who exploit vulnerabilities and engage in data theft. To mitigate these risks, organizations should implement robust security measures, including enhanced monitoring, secure data storage, and regular vulnerability assessments to protect against such malicious activities.
Recommendations: Enhance the cybersecurity posture by:
The CYFIRMA Research team observed that a threat actor has allegedly claimed responsibility for a data breach affecting an Indonesian online student admission platform. The allegations, which surfaced on a dark web forum, suggest that personal information belonging to 13,291 users may have been compromised.
The leaked dataset reportedly contains user credentials, full names, addresses, and registration dates.
While these claims have yet to be independently verified, the alleged breach raises concerns over the security of educational institutions’ digital platforms.

The CYFIRMA Research team observed a data leak related to the UAE Ministry of Education(https[:]//www[.]moe[.]gov[.]ae/) in an underground forum. The United Arab Emirates (UAE) Ministry of Education is the federal authority responsible for shaping and implementing educational policies across the nation. The compromised dataset includes 293,468 rows, containing valuable information such as Local IDs, Names, Emails, Grade Levels, Streams, and School details. This breach primarily affects students, revealing detailed academic and contact information. The breach has been linked to a threat actor identified as “Rey.”
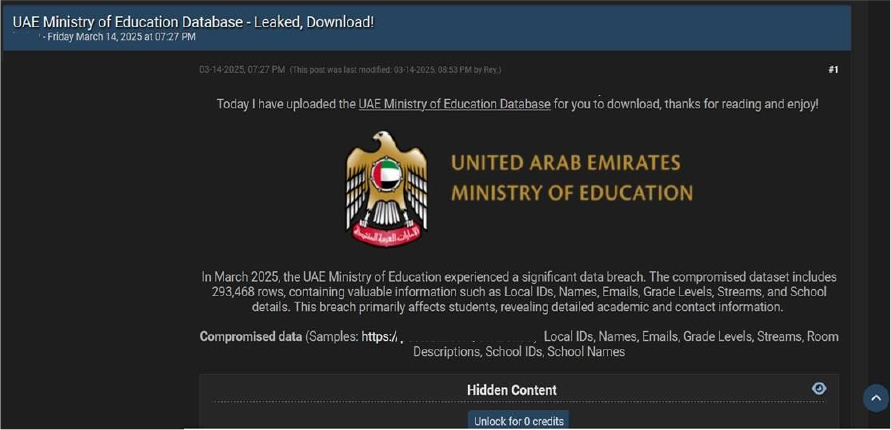
STRATEGIC RECOMMENDATIONS
MANAGEMENT RECOMMENDATIONS
TACTICAL RECOMMENDATIONS
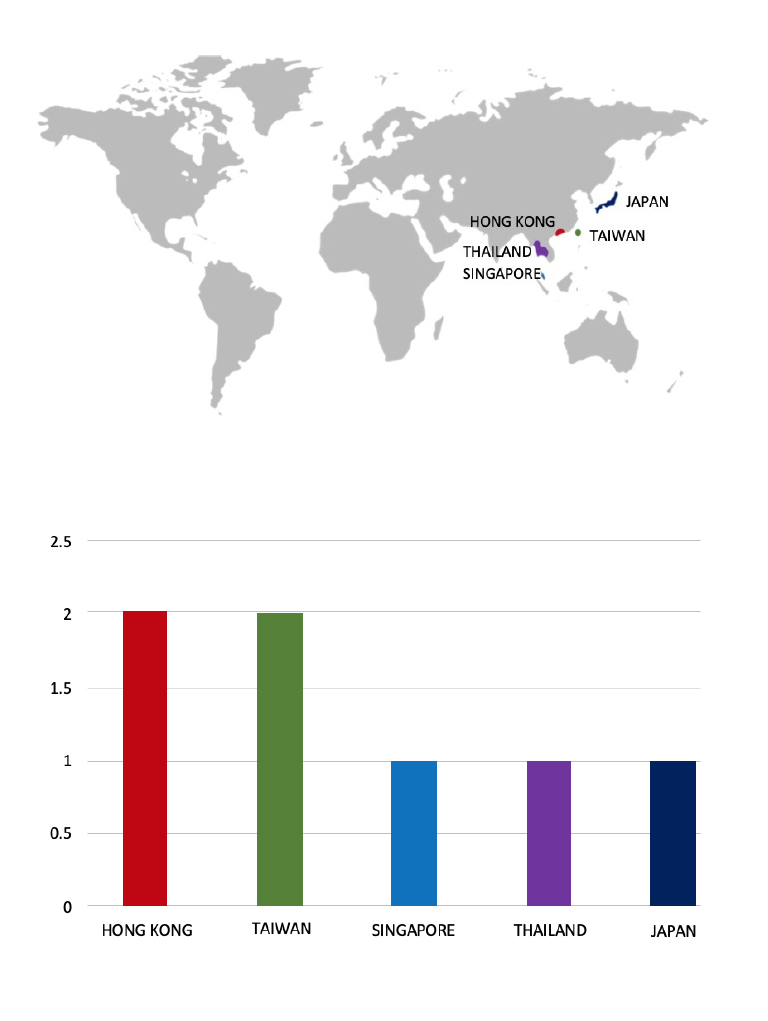
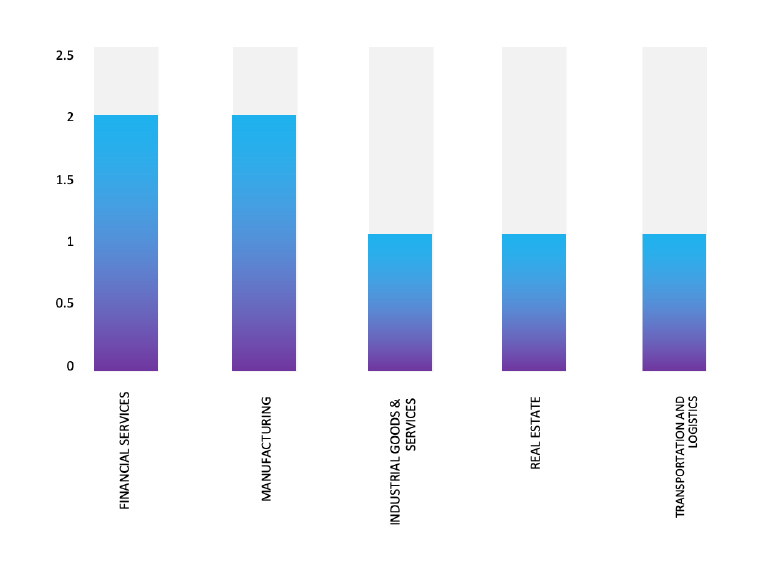
Please find the Geography-Wise and Industry-Wise breakup of cyber news for the last 5 days as part of the situational awareness pillar.
For situational awareness intelligence and specific insights mapped to your organisation’s geography, industry, and technology, please access DeCYFIR.