



CYFIRMA Research and Advisory Team would like to highlight ransomware trends and insights gathered while monitoring various forums. This includes multiple – industries, geography, and technology – that could be relevant to your organization.
Type: Ransomware
Target Technologies: MS Windows
CYFIRMA Research and Advisory Team has found ETHAN Ransomware while monitoring various underground forums as part of our Threat Discovery Process.
Recently, researchers identified the ETHAN ransomware, a variant of the MedusaLocker family. Upon infiltrating a victim’s network, it encrypts files and appends the “.ETHAN” extension to filenames. After encryption, ETHAN alters the desktop wallpaper and generates a ransom note in an HTML file named “READ_NOTE.html,” demanding payment for decryption.
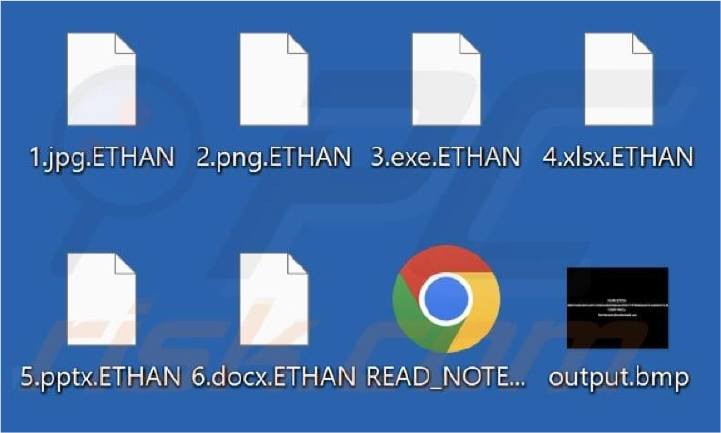
ETHAN’s ransom note informs victims that their network has been compromised, with critical files encrypted using RSA and AES algorithms. Additionally, confidential data has been exfiltrated. To regain access, victims must pay a ransom, which increases if not paid within 72 hours. Refusal to comply results in data leaks or sales. Victims can test decryption on 2-3 non-sensitive files before payment. The note warns against renaming, modifying files, or using third-party decryption tools, as this could lead to irreversible data loss.

Following are the TTPs based on the MITRE Attack Framework
| Tactic | ID | Technique |
| Initial Access | T1091 | Replication Through Removable Media |
| Execution | T1059 | Command and Scripting Interpreter |
| Execution | T1129 | Shared Modules |
| Persistence | T1542.003 | Pre-OS Boot: Bootkit |
| Persistence | T1547.001 | Boot or Logon Autostart Execution: Registry Run Keys / Startup Folder |
| Persistence | T1574.002 | Hijack Execution Flow: DLL Side-Loading |
| PrivilegeEscalation | T1055 | Process Injection |
| PrivilegeEscalation | T1134.004 | Access Token Manipulation: Parent PID Spoofing |
| PrivilegeEscalation | T1547.001 | Boot or Logon Autostart Execution: Registry Run Keys / Startup Folder |
| PrivilegeEscalation | T1574.002 | Hijack Execution Flow: DLL Side-Loading |
| Defense Evasion | T1014 | Rootkit |
| Defense Evasion | T1027.005 | Obfuscated Files or Information: Indicator Removal from Tools |
| Defense Evasion | T1036 | Masquerading |
| Defense Evasion | T1055 | Process Injection |
| Defense Evasion | T1070.004 | Indicator Removal: File Deletion |
| Defense Evasion | T1112 | Modify Registry |
| Defense Evasion | T1134.004 | Access Token Manipulation: Parent PID Spoofing |
| Defense Evasion | T1202 | Indirect Command Execution |
| Defense Evasion | T1222 | File and Directory Permissions Modification |
| Defense Evasion | T1497.001 | Virtualization/Sandbox Evasion: System Checks |
| Defense Evasion | T1542.003 | Pre-OS Boot: Bootkit |
| Defense Evasion | T1564.001 | Hide Artifacts: Hidden Files and Directories |
| Defense Evasion | T1574.002 | Hijack Execution Flow: DLL Side-Loading |
| Discovery | T1010 | Application Window Discovery |
| Discovery | T1012 | Query Registry |
| Discovery | T1016 | System Network Configuration Discovery |
| Discovery | T1018 | Remote System Discovery |
| Discovery | T1049 | System Network Connections Discovery |
| Discovery | T1057 | Process Discovery |
| Discovery | T1082 | System Information Discovery |
| Discovery | T1083 | File and Directory Discovery |
| Discovery | T1120 | Peripheral Device Discovery |
| Discovery | T1135 | Network Share Discovery |
| Discovery | T1497.001 | Virtualization/Sandbox Evasion: System Checks |
| Discovery | T1518.001 | Software Discovery: Security Software Discovery |
| LateralMovement | T1091 | Replication Through Removable Media |
| Collection | T1074 | Data Staged |
|
Command and Control |
T1071 | Application Layer Protocol |
| Command and Control |
T1095 | Non-Application Layer Protocol |
|
Command and Control |
T1573 | Encrypted Channel |
| Impact | T1485 | Data Destruction |
| Impact | T1486 | Data Encrypted for Impact |
| Impact | T1490 | Inhibit System Recovery |
| Impact | T1496 | Resource Hijacking |
Relevancy and Insights:
ETLM Assessment:
CYFIRMA’s analysis of available data shows that MedusaLocker ransomware has been actively targeting various sectors, including manufacturing, healthcare, finance, and IT services, since 2019. The emergence of ETHAN ransomware, an advanced MedusaLocker variant, indicates the use of enhanced evasion techniques to broaden its impact on individuals and enterprises. Projections suggest a continued global threat to key industries, emphasizing the urgent need for strong cybersecurity measures to combat these evolving risks effectively.
Sigma rule:
title: Shadow Copies Deletion Using Operating Systems Utilities tags:
– attack.defense-evasion
– attack.impact
– attack.t1070
– attack.t1490 logsource:
category: process_creation product: windows
detection: selection1_img:
– Image|endswith:
– ‘\powershell.exe’
– ‘\pwsh.exe’
– ‘\wmic.exe’
– ‘\vssadmin.exe’
– ‘\diskshadow.exe’
– OriginalFileName:
– ‘PowerShell.EXE’
– ‘pwsh.dll’
– ‘wmic.exe’
– ‘VSSADMIN.EXE’
– ‘diskshadow.exe’ selection1_cli:
CommandLine|contains|all:
– ‘shadow’ # will match “delete shadows” and “shadowcopy delete” and “shadowstorage”
– ‘delete’ selection2_img:
– Image|endswith: ‘\wbadmin.exe’
– OriginalFileName: ‘WBADMIN.EXE’ selection2_cli:
CommandLine|contains|all:
– ‘delete’
– ‘catalog’
– ‘quiet’ # will match -quiet or /quiet selection3_img:
– Image|endswith: ‘\vssadmin.exe’
– OriginalFileName: ‘VSSADMIN.EXE’ selection3_cli:
CommandLine|contains|all:
– ‘resize’
– ‘shadowstorage’ CommandLine|contains:
– ‘unbounded’
– ‘/MaxSize=’
condition: (all of selection1*) or (all of selection2*) or (all of selection3*) fields:
– CommandLine
– ParentCommandLine falsepositives:
– Legitimate Administrator deletes Shadow Copies using operating systems utilities for legitimate reason
– LANDesk LDClient Ivanti-PSModule (PS EncodedCommand) level: high
(Source: Surface Web)
IOCs:
Kindly refer to the IOCs section to exercise control of your security systems.
STRATEGIC RECOMMENDATION
MANAGEMENT RECOMMENDATION
TACTICAL RECOMMENDATION
Type: Information Stealer | Objectives: Credential theft, Data exfiltration| Target Industries: Cryptocurrency, Fintech | Target Technologies: Zendesk, Web Browsers (Edge,Brave)
CYFIRMA collects data from various forums based on which the trend is ascertained. We identified a few popular malware that were found to be distributed in the wild to launch cyberattacks on organizations or individuals.
Active Malware of the week
This week “Zhong Stealer” is trending.
Zhong Stealer
Researchers uncovered a phishing campaign aimed at the cryptocurrency and fintech sectors, designed to spread a previously unknown stealer malware called Zhong Stealer. The attackers disguised themselves as customers on chat support platforms like Zendesk, deceiving support agents into unknowingly downloading the malware.
Attack Method
The attackers followed a simple yet persistent strategy, beginning with fake support tickets created using newly registered accounts. These tickets contained poorly written messages in Chinese, often accompanied by ZIP file attachments claiming to include screenshots or additional details. While the phishing messages were in Chinese, it remains unclear whether the campaign specifically targeted Chinese-speaking victims or if this was a tactic to bypass detection. Since the malware checks system language settings, it could be selectively targeting specific regions. Each ZIP file contained an EXE file, concealed within Simplified or Traditional Chinese-named archives, that launched the malware upon opening. The ZIP file execution serves as the initial trigger, leading to the deployment of Zhong Stealer. Once the victim opens the archive and executes the EXE, the malware immediately initiates its attack chain.
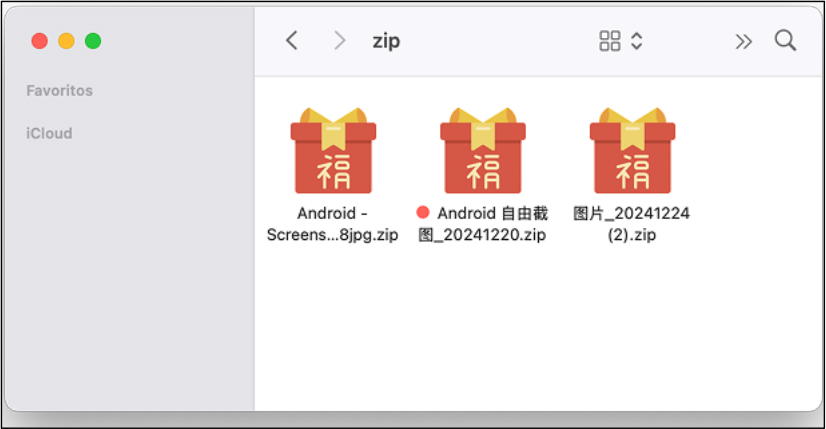
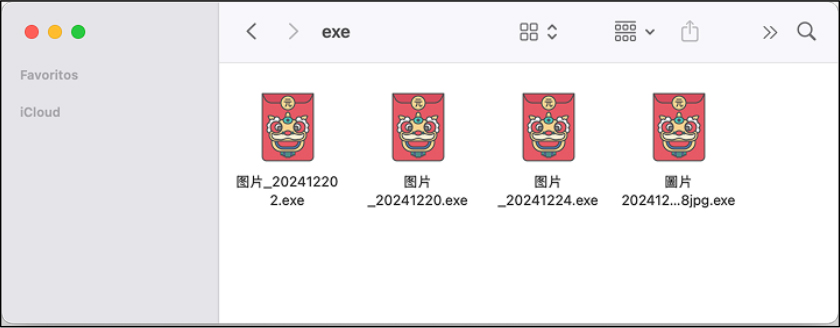
Technical Analysis
Once executed, Zhong Stealer connects to a command-and-control server in Hong Kong, initiating a multi-stage attack. It first retrieves a TXT file containing download links for additional components, including a disguised BitDefender updater signed with a revoked certificate, suggesting it was likely stolen. This deceptive approach helps the malware evade initial detection, enabling further execution.
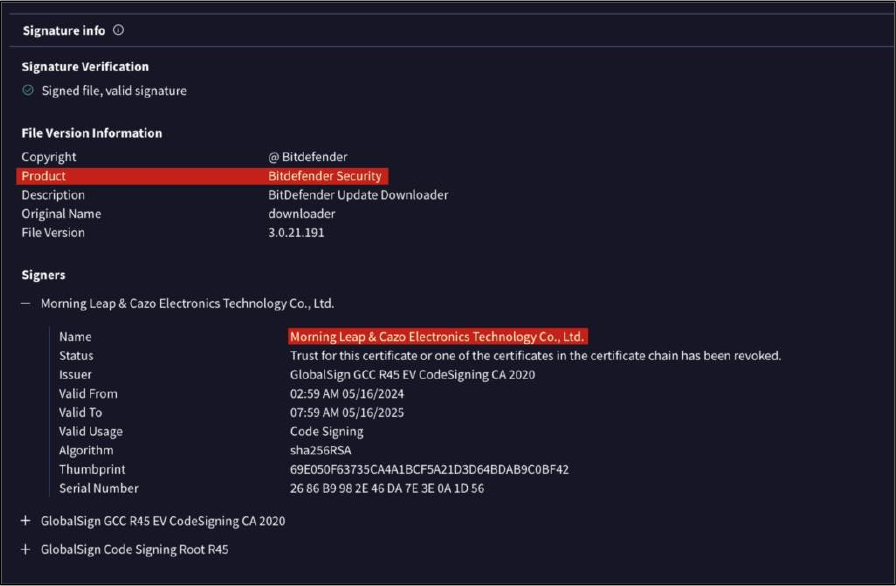
To maintain persistence, Zhong creates a BAT file that modifies system settings, hides files, and queries system languages to potentially evade certain regions. It also disables trace logs and collects system details like hostnames, proxies, and security settings. The final stage focuses on credential theft, targeting browsers like Brave and Edge. Using a registry key for persistence, Zhong then exfiltrates stolen credentials and browser data to its Hong Kong-based server on port 1131.
INSIGHTS
ETLM ASSESSMENT
From the ETLM perspective, CYFIRMA anticipates that Zhong Stealer’s campaign highlights a growing trend where cybercriminals exploit trust-based interactions to infiltrate organizations, signaling a shift toward more deceptive and persistent phishing tactics. In the future, attackers may increasingly target customer support portals, internal messaging systems, and ticketing platforms as entry points, embedding malware within seemingly legitimate communications. As these threats evolve, organizations could face a rise in highly tailored social engineering campaigns that bypass traditional security measures, making real-time detection even more challenging. The success of Zhong Stealer may also encourage attackers to develop region-specific tactics, adapting language and cultural cues to evade detection. Looking ahead, businesses will need to strengthen verification protocols and integrate advanced behavioral analysis into their security frameworks to counter these emerging threats.
STRATEGIC:
MANAGEMENT:
TACTICAL RECOMMENDATIONS
Key Intelligence Signals:
Earth Preta AKA Mustang Panda Combines Legitimate and Malicious Components to Evade Detection
SUMMARY
Earth Preta, an advanced persistent threat (APT) group, utilizes sophisticated techniques to compromise systems, evade detection, and maintain persistence. In their recent attack campaigns, the group deploys multiple files, including legitimate executables, malicious components, and a decoy PDF designed to distract victims while the payload is deployed in the background. The attack chain begins with a dropper malware (IRSetup.exe) that installs files into the ProgramData/session directory, including a combination of legitimate and malicious files. One of these files is a decoy PDF, targeted at users in Thailand, which masquerades as a government-backed anti-crime platform.
The attackers use a legitimate Electronic Arts (EA) application, OriginLegacyCLI.exe, to sideload a modified version of the TONESHELL backdoor (EACore.dll). This DLL contains a function that checks if antivirus processes (such as ESET) are running. If detected, the malware uses regsvr32.exe to register the DLL and execute its payload. The backdoor communicates with the C&C server through the ws2_32.send API call, sending system information like the computer name and a unique victim ID.
To inject malicious code into a legitimate process, Earth Preta uses the Microsoft Application Virtualization Injector (MAVInject.exe) and the waitfor.exe utility. When antivirus software is absent, the malware directly injects code into waitfor.exe via WriteProcessMemory and CreateRemoteThreadEx APIs. The malware’s persistence is further enhanced by storing the victim ID in a specific directory. Communication with the C&C server is encrypted, and the malware supports various commands, including reverse shell execution, file deletion, and movement.
The group’s ability to blend malicious actions with legitimate applications, such as Setup Factory for payload execution, makes detection more challenging. Earth Preta continues to refine its evasion techniques, demonstrating high-level expertise in its operations.
Relevancy & Insights:
Earth Preta, also known as Mustang Panda, has a history of targeting government entities, primarily in the Asia-Pacific region, through phishing campaigns. Their previous attacks have employed similar tactics, including the use of decoy documents and legitimate software for malware execution. In earlier incidents, they used spear-phishing emails with fraudulent attachments to deploy malware, often employing backdoors like TONESHELL for system compromise. These attacks have typically been aimed at high-profile sectors, with a particular focus on Taiwan, Vietnam, and Malaysia.
In the current incident, Earth Preta continues to leverage the same strategy, utilizing spear-phishing with a decoy PDF to distract victims while deploying malicious payloads in the background. The group’s use of legitimate applications, such as OriginLegacyCLI.exe and Setup Factory, for payload delivery and execution reflects their ongoing refinement of evasion techniques. The presence of shared command-and-control infrastructure and similar malware characteristics, such as the modified TONESHELL backdoor, further links the current attack to Earth Preta’s previous campaigns, reinforcing their reliance on sophisticated methods to evade detection and maintain persistence on compromised systems.
ETLM Assessment:
Earth Preta, also known as Mustang Panda, is an advanced persistent threat (APT) group primarily focused on espionage and cyberattacks targeting government entities. Their campaigns are concentrated in the South Asia-Pacific region, particularly in Taiwan, Vietnam, and Malaysia. The group has historically targeted high-value sectors, including government agencies.
Earth Preta’s attacks typically exploit legitimate software and social engineering tactics, such as spear-phishing emails with decoy documents. They have used malware like the TONESHELL backdoor, sideloaded via legitimate applications like Electronic Arts’ OriginLegacyCLI.exe, and recently adopted the Microsoft Application Virtualization Injector (MAVInject.exe) for stealthy code injection. They frequently use custom C&C infrastructure to exfiltrate data and maintain persistence.
Future threats from Earth Preta are expected to evolve with more sophisticated evasion techniques, utilizing legitimate processes and avoiding detection by security solutions. Organizations should bolster defenses with advanced monitoring, especially for anomalies in legitimate software execution and unusual network activity.
Strategic Recommendations:
Tactical Recommendations:
Operational Recommendations:
| MITRE FRAMEWORK | ||
| Tactic | ID | Technique |
| Initial Access | T1566.0 01 | Phishing: Spear phishing Attachment |
| Initial Access | T1190 | Exploit Public-Facing Application |
| Persistence | T1547.0 01 | Boot or Logon Autostart Execution: Registry Run Keys / Startup Folder |
| Privilege Escalation | T1055 | Process Injection |
| Command and Control | T1071 | Application Layer Protocol |
| Exfiltration | T1041 | Exfiltration Over C2 Channel |
Thailand will take in thousands of people rescued from Myanmar scam farms
In recent weeks, authorities from China, Thailand, and Myanmar have attempted to dismantle scam centres and illegal online operations on the border, part of a network of illegal compounds across Southeast Asia where hundreds of thousands have been trafficked by gangs.
Thailand will take in 7,000 people rescued from scam call centers in Myanmar. Most of the individuals are from China, Thailand, Vietnam, and other Southeast Asian countries, and were essentially slaves tricked into traveling to Myanmar under false promises of employment. Two Myanmar armed groups – the Karen National Army (KNA) and the Democratic Karen Buddhist Army (DKBA) – are currently holding around 7,000 former scam centre workers which should now be sent to Thailand.
ETLM Assessment:
Organized criminal gangs set up compounds in the area following Myanmar’s coup in 2021 and used them as bases to launch various online scams against victims around the world, causing billions of dollars in losses. China and Thailand have been pressuring Myanmar to crack down on these networks, but regional instability has hampered the efforts.
Southeast Asian countries have since stepped up efforts to tackle scam centres, including Thailand cutting power, fuel, and internet supply to areas linked with scam centres. Since March 2022, financial losses incurred by victims of telecom scams in Thailand alone stand at $2.4 billion according to Thai Police.
The Chinese gangs linked to scam operations in Myanmar were also believed to be linked to similar operations in Cambodia, as such criminal operations have spread in areas of the region where governance is weak.
UK warns Chinese components in ‘smart’ devices pose sabotage threat
The new chair of Britain’s cross-party Coalition on Secure Technology has warned that household items from fridges to cars that contain Chinese electronics may be at risk of being accessed remotely. The committee urged the British government to encourage UK manufacturing capacity for cellular modules used in the “Internet of Things” in order to defend against the risk of cyber-attacks.
The British government has ordered the removal of all technology made by the Chinese company Huawei from the UK 5G network by the end of 2027, citing security concerns. This month the UK Ministry of Defence ordered military chiefs to avoid conducting sensitive conversations in Chinese-made electric cars, amid fears that inbuilt microphones could record and transmit chatter.
ETLM Assessment:
Connected devices including smart meters, mobile payment terminals, electric cars, and civilian drones all formed a “soft underbelly of infrastructure” that China could target, which is increasingly apparent after the Salt Typhoon and Volt Typhoon campaigns Chinese hackers embarked upon in the past couple of years. Just three Chinese companies are responsible for more than 50 % of the global market in cellular modules used in the growing network of interconnected devices, which poses a serious risk to the future, especially should a conflict over Taiwan erupt.
Salt Typhoon continues its campaign against telecoms
Researchers warn that the Chinese state-sponsored threat actor Salt Typhoon continues to target telecommunication companies. Between December 2024 and January 2025, the researchers observed a campaign that exploited unpatched internet-facing Cisco network devices to compromise several organizations, including the US-based affiliate of a UK telecom provider and a South African telecom provider. The attacks exploited CVE-2023- 20273, a privilege escalation flaw affecting the web UI feature of Cisco IOS XE Software.
ETLM Assessment:
Salt Typhoon has attempted to exploit more than 1,000 Cisco devices globally, targeting devices associated with universities in Argentina, Bangladesh, Indonesia, Malaysia, Mexico, the Netherlands, Thailand, the United States, and Vietnam. The Chinese hackers possibly targeted these universities to access research in areas related to telecommunications, engineering, and technology, particularly at institutions like UCLA and TU Delft in a campaign that is likely part of a massive Chinese state-driven industrial espionage effort.
The Lynx Ransomware Impacts Allied Tenesis (Allied Telesis)
Summary
From the External Threat Landscape Management (ETLM) Perspective, CYFIRMA observed in an underground forum that a company from Japan; Allied Tenesis (Allied Telesis) (https[:]//www[.]alliedtelesis[.]com/), was compromised by Lynx Ransomware. Allied Telesis is a global provider of networking hardware and software, specializing in secure and reliable network solutions for various industries. The compromised data consists of confidential and sensitive information related to the organization. The total size of the compromised data is approximately 800 GB.
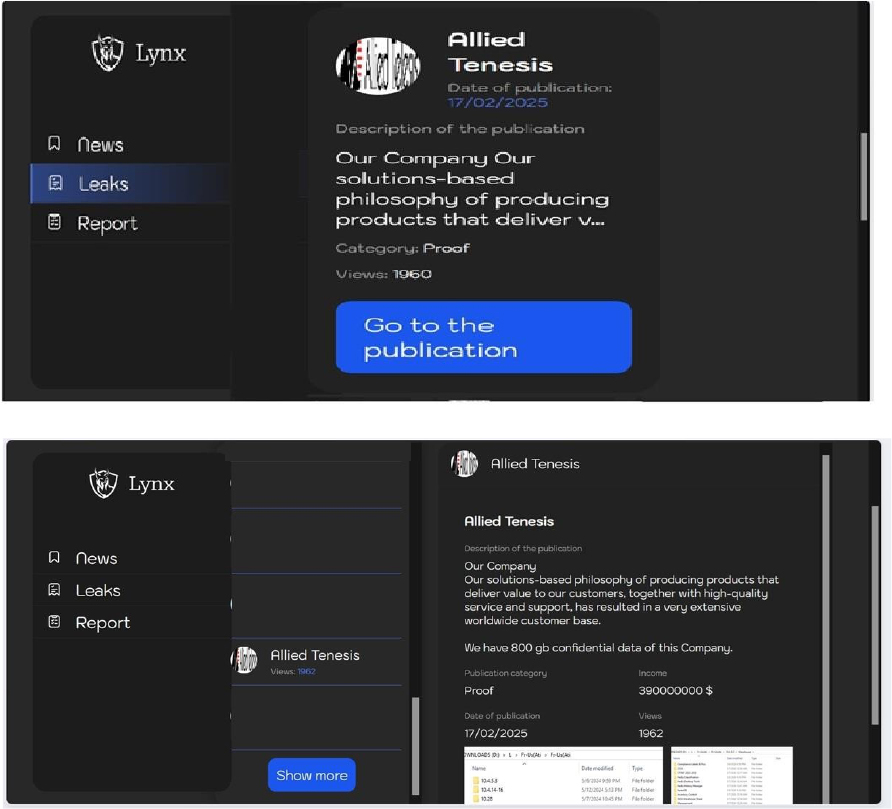
Relevancy & Insights:
ETLM Assessment:
According to CYFIRMA’s assessment, Lynx ransomware has emerged as a significant threat in the cybersecurity landscape, leveraging advanced encryption and double extortion tactics to target small and medium-sized businesses. Its structured affiliate program and versatile ransomware toolkit make it a formidable force in the RaaS ecosystem.
The Fog Ransomware Impacts Next TI (PT. NEXT Transformtech Indonesia)
Summary:
From the External Threat Landscape Management (ETLM) Perspective, CYFIRMA observed in an underground forum that a company from Indonesia; Next TI (PT. NEXT Transformtech Indonesia) (https[:]//next-ti[.]co[.]id/) was compromised by Fog Ransomware. Next TI (PT. NEXT Transformtech Indonesia) is an IT solutions company based in Indonesia, specializing in financial digital platforms for the banking and multi- finance sectors. The compromised data consists of confidential and sensitive information related to the organization. The total size of the compromised data is approximately 8 GB.
Relevancy & Insights:
ETLM Assessment:
CYFIRMA’s assessment indicates that Fog Ransomware, despite utilizing advanced techniques, presents a substantial threat due to its double extortion methods and wide- ranging targets. To effectively reduce the risk of Fog Ransomware attacks, organizations should prioritize strong security measures, including regular data backups, security awareness training, vulnerability management, and comprehensive incident response planning.
Vulnerability in Exim SQLite support feature
Relevancy & Insights:
The vulnerability exists due to insufficient sanitization of user- supplied data.
Impact:
A remote attacker can send a specially crafted email to the affected server and execute arbitrary SQL commands within the application’s database.
Affected Products:
https[:]//www[.]exim[.]org/static/doc/security/CVE-2025-26794.txt
Recommendations:
Monitoring and Detection: Implement monitoring and detection mechanisms to identify unusual system behavior that might indicate an attempted exploitation of this vulnerability.
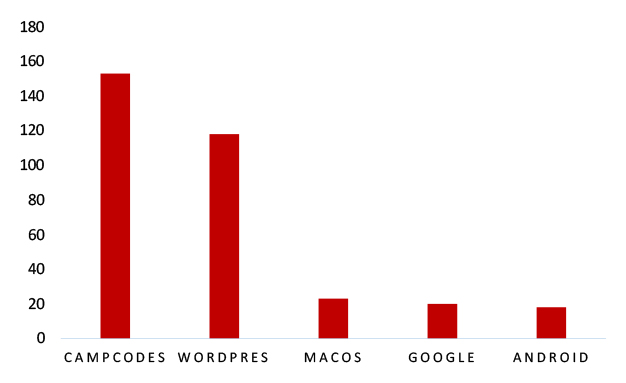
TOP 5 AFFECTED TECHNOLOGIES OF THE WEEK
This week, CYFIRMA researchers have observed significant impacts on various technologies, due to a range of vulnerabilities. The following are the top 5 most affected technologies.
ETLM Assessment
Vulnerability in Exim SQLite can pose significant threats to user privacy and security. This can impact various industries globally, including technology, finance, healthcare, and beyond. Ensuring the security of Exim SQLite is crucial for maintaining the integrity and protection of users’ data worldwide. Therefore, addressing these vulnerabilities is essential to safeguarding email communications and lightweight database management operations, across different geographic regions and sectors.
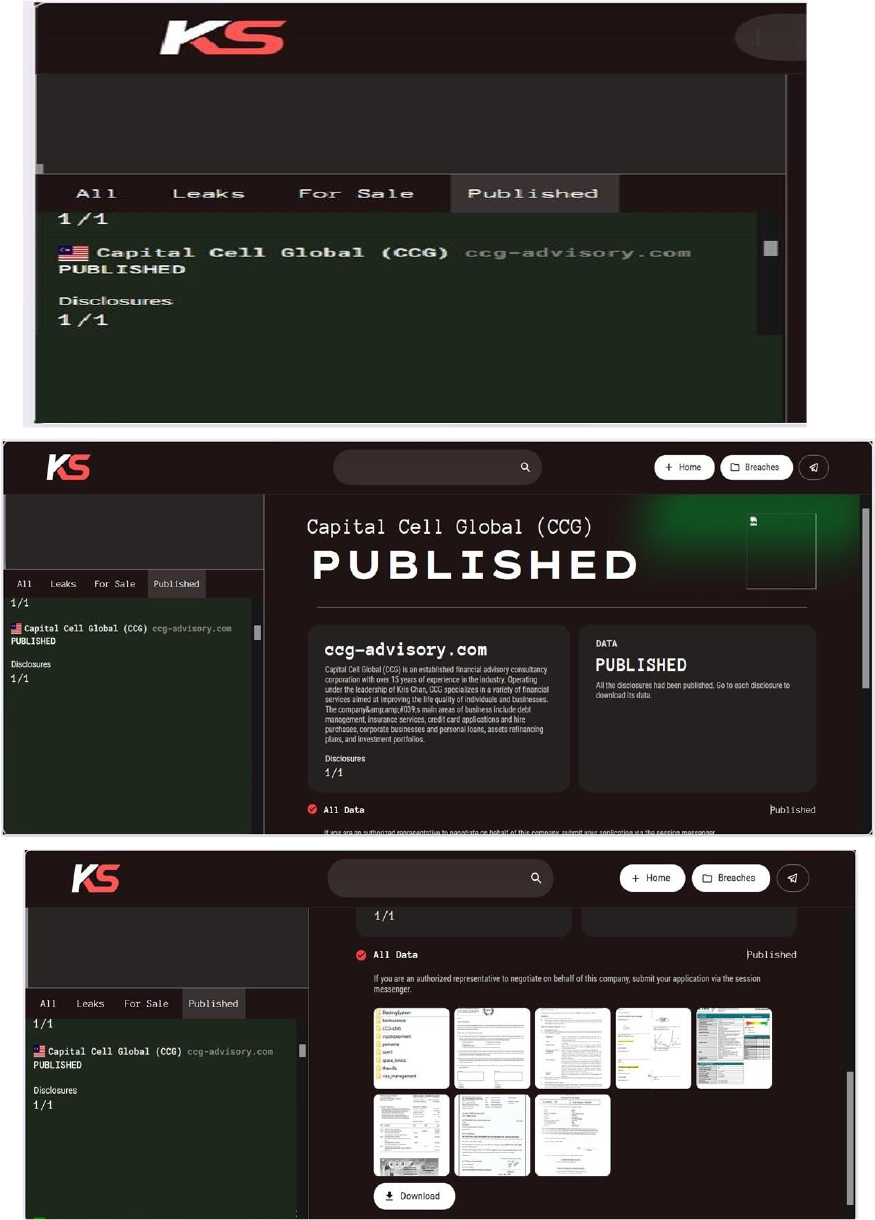
Killsec Ransomware attacked and published the data of Capital Cell Global (CCG)
Summary:
Recently, we observed that Killsec Ransomware attacked and published the data of Capital Cell Global (CCG)(www[.]ccg-advisory[.]com) on its dark web website. Capital Cell Global (CCG) is a specialized financial advisory firm based in Malaysia, offering a broad spectrum of financial services to support local businesses and individuals. The company’s main areas of business include debt management, insurance services, credit card applications and hire purchases, corporate businesses and personal loans, assets refinancing plans, and investment portfolios. The data leak, following the ransomware attack, encompasses sensitive and confidential records, originating from the organizational database.
Relevancy & Insights:
ETLM Assessment:
The emergence and evolution of KillSec’s Ransomware-as-a-Service (RaaS) platform represents a concerning development in the cybercrime landscape. By lowering the technical barrier to entry, this RaaS model allows less skilled individuals to engage in sophisticated ransomware attacks, potentially leading to an increase in such incidents globally.
According to CYFIRMA’s assessment, the KillSec ransomware group is expected to continue targeting a wide range of industries worldwide. Their advanced tactics, such as exploiting website vulnerabilities and conducting credential theft, make them a significant threat to organizations with inadequate security measures in place.
Baran Company Limited Data Advertised on a Leak Site
Summary:
The CYFIRMA Research team observed a data leak related to the Baran Company Limited (https[:]//baran[.]com[.]sa/) in an underground forum. Baran Company Limited is a leading engineering contractor based in Saudi Arabia, specializing in energy, construction, finishing, and infrastructure projects. The company offers a comprehensive range of services to esteemed EPC (Engineering, Procurement, and Construction) and OEM (Original Equipment Manufacturer) companies within the region. The breached data contains confidential and sensitive information related to the organization. The total size of breached data is approximately 22GB. The breach has been attributed to a threat actor known as “Zerodayx1.”
Library and Information Center of the National Institute of Development Administration (NIDA) Thailand Data Advertised on a Leak Site
Summary:
The CYFIRMA Research team observed a data leak related to the Library and Information Center of the National Institute of Development Administration (NIDA)Thailand(https[:]//library.nida[.]ac[.]th/) in an underground forum. The website libmod.nida.ac.th is the official platform of the Library and Information Center at the National Institute of Development Administration (NIDA) in Thailand. NIDA, the center serves as a comprehensive resource hub for students, faculty, and researchers. The compromised data includes member ID, member level, member type, member username, encrypted and decrypted member passwords, member name, member surname, member email, and other sensitive and confidential information. The breach has been attributed to a threat actor known as “Hacker levup.”
Relevancy & Insights:
Financially motivated cybercriminals are continuously scouring for exposed and vulnerable systems and applications to exploit. A significant number of these malicious actors congregate within underground forums, where they discuss cybercrime and trade stolen digital assets. Operating discreetly, these opportunistic attackers target unpatched systems or vulnerabilities in applications to illicitly gain access and steal valuable data.
Subsequently, the pilfered data is advertised for sale within underground markets, where it can be acquired, repurposed, and utilized by other malicious actors in further illicit activities.
ETLM Assessment:
The threat actor “ZeroDayX1” is reportedly involved in acquiring and attempting to sell sensitive data on various forums. This activity highlights the ongoing risks posed by cyber threat actors who exploit vulnerabilities and engage in data theft. To mitigate these risks, organizations should implement robust security measures.
Recommendations: Enhance the cybersecurity posture by:
The CYFIRMA Research team observed a data sale related to Food Delivery Services Customers PII – PH/Philippines in an underground forum. A threat actor claims to have gained access to the personally identifiable information (PII) of more than 360,000 users from a food delivery service. The dataset is allegedly being sold for $650, while admin access is priced at $1,000. The compromised information reportedly includes user IDs, email addresses, first names, and last names. The breach has been linked to a threat actor known as “Akrust.”
The CYFIRMA Research team observed a data leak related to the Saipem Taqa Al- Rushaid Fabricators Co. Ltd. (STAR) (https://www.starfab.com.sa/) in an underground forum. Saipem Taqa Al-Rushaid Fabricators Company Ltd. (STAR) is a prominent fabrication and construction company based in Saudi Arabia.
Established as a joint venture between Saipem and Taqa Al-Rushaid, STAR specializes in offshore platform design, engineering, and construction, serving the oil and gas industry. The breached data contains confidential and sensitive information related to the organization. The breach has been attributed to a threat actor known as “Zerodayx1.”
STRATEGIC RECOMMENDATIONS
MANAGEMENT RECOMMENDATIONS
TACTICAL RECOMMENDATIONS
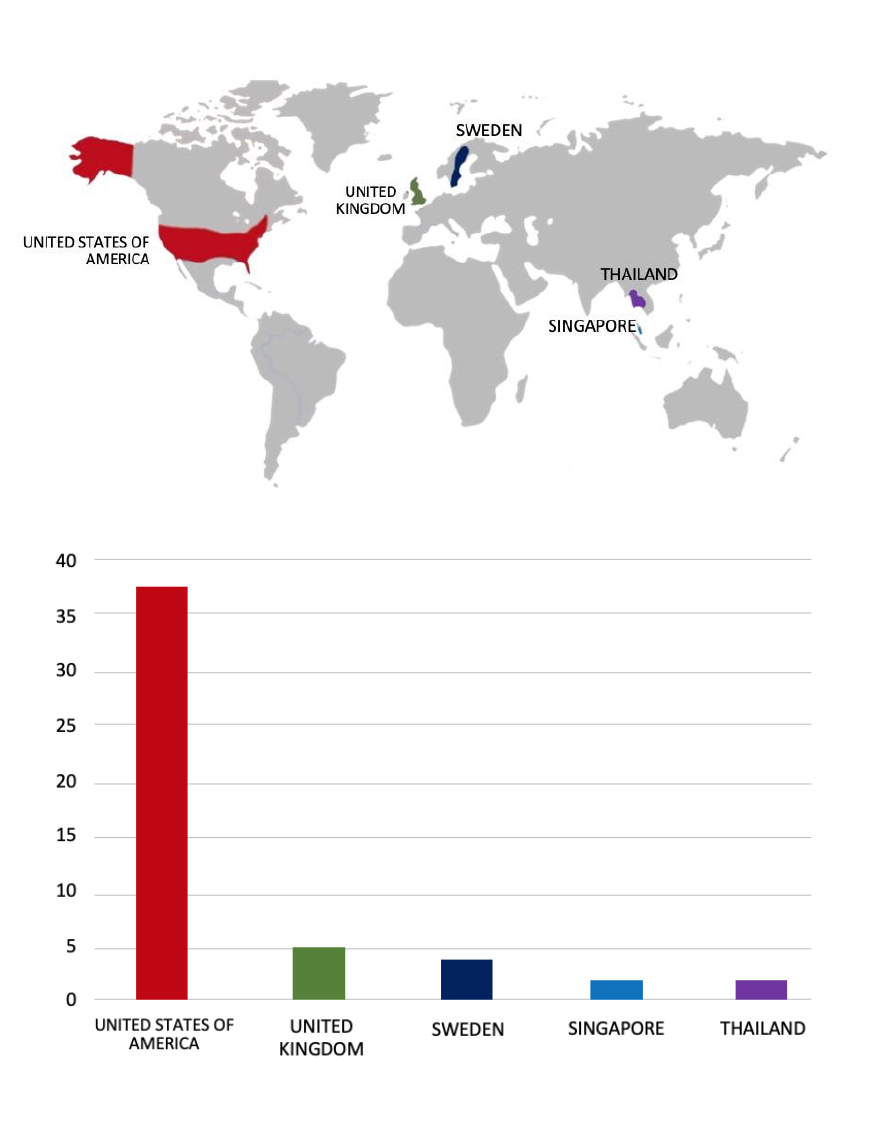
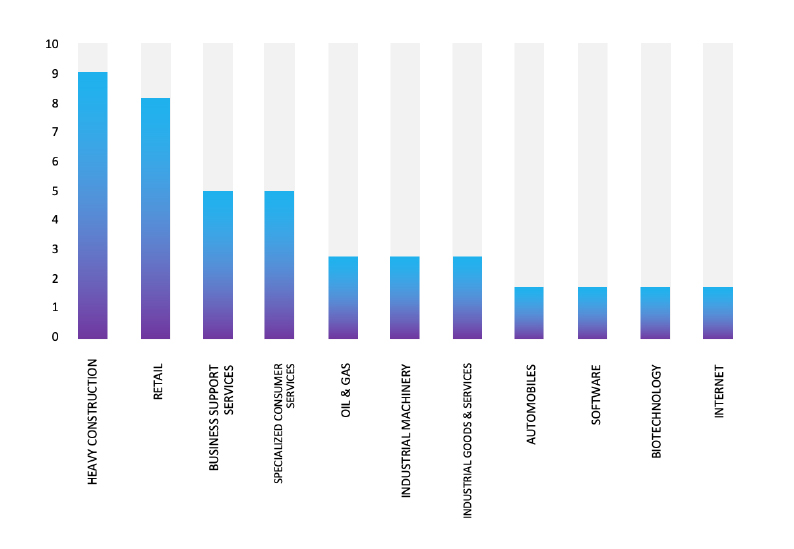
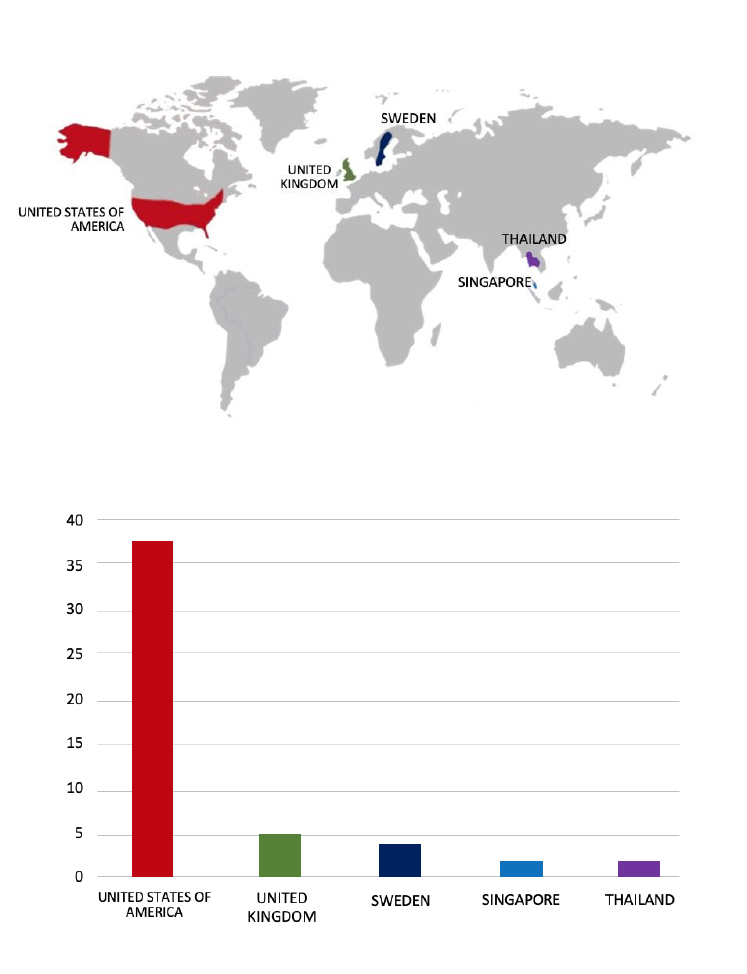
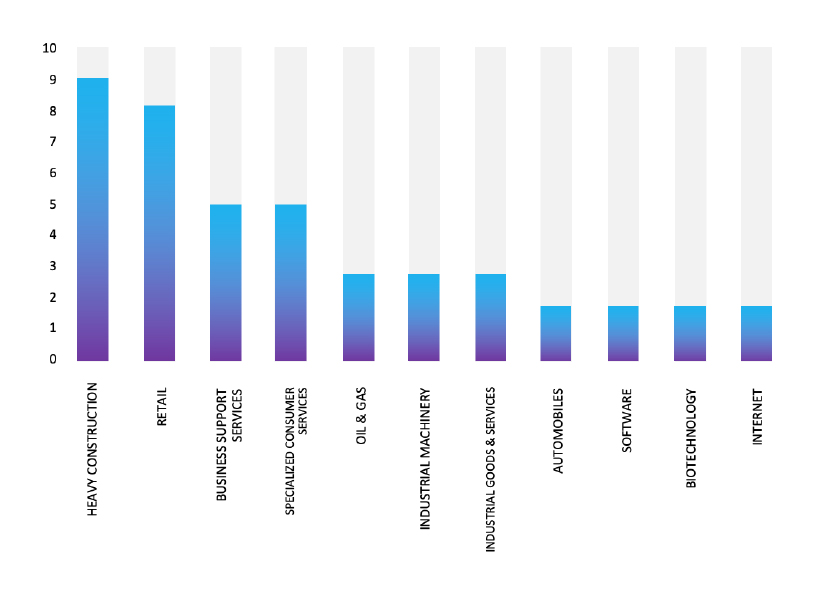
Please find the Geography-Wise and Industry-Wise breakup of cyber news for the last 5 days as part of the situational awareness pillar.
For situational awareness intelligence and specific insights mapped to your organisation’s geography, industry, and technology, please access DeCYFIR.