



CYFIRMA Research and Advisory Team would like to highlight ransomware trends and insights gathered while monitoring various forums. This includes multiple – industries, geography, and technology – which could be relevant to your organization.
Type: Ransomware
Target Technologies: MS Windows
Introduction
CYFIRMA Research and Advisory Team has found COBRA Ransomware while monitoring various underground forums as part of our Threat Discovery Process.
COBRA Ransomware
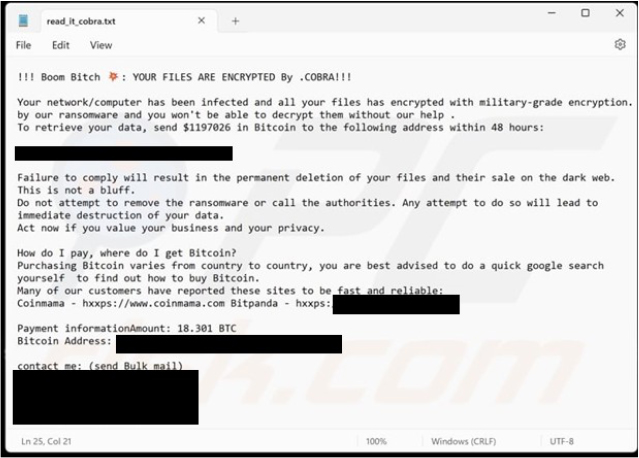
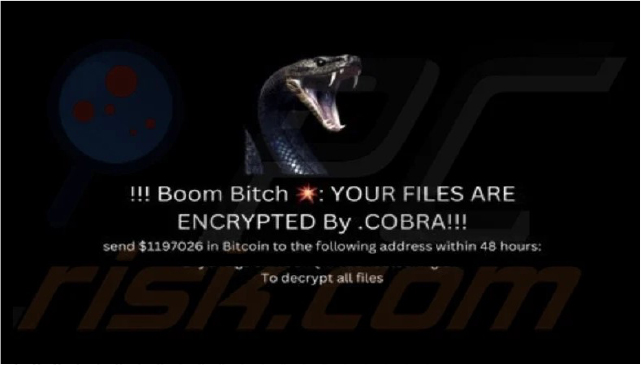
By the End of June 2024 researchers discovered a new ransomware group called COBRA, this malicious program is based on Chaos. COBRA encrypted the files and added a “.COBRA” extension to their names. It then altered the desktop wallpaper and generated a ransom note in a text file titled “read_it_cobra.txt”.

COBRA’s ransom note informs the victim that their files have been encrypted and demands
$1,197,026 in Bitcoin (BTC) within 48 hours to restore the locked data. The note also lists the ransom as 18.301 BTC, which is approximately $1,191,488 at the time of writing, though exchange rates fluctuate.
If the victim does not comply, their files will be sold on the dark web and deleted from the infected network. The same consequences will occur if the victim attempts to remove the ransomware or contacts authorities.
Following are the TTPs based on the MITRE Attack Framework
| Sr. No. | Tactics | Techniques/Sub-Techniques |
| 1 | TA0002: Execution | T1106: Native API |
| T1129: Shared Modules | ||
| 2 | TA0003: Persistence | T1176: Browser Extensions |
| T1547.001: Boot or Logon Autostart Execution: Registry Run Keys / Startup Folder | ||
| T1574.002: Hijack Execution Flow: DLL Side- Loading | ||
| 3 | TA0004: Privilege Escalation | T1547.001: Boot or Logon Autostart Execution: Registry Run Keys / Startup Folder |
| T1548: Abuse Elevation Control Mechanism | ||
| T1574.002: Hijack Execution Flow: DLL Side- Loading | ||
| 4 | TA0005: Defense Evasion | T1027: Obfuscated Files or Information |
| T1036: Masquerading | ||
| T1070.004: Indicator Removal: File Deletion | ||
| T1112: Modify Registry | ||
| T1140: Deobfuscate/Decode Files or Information | ||
| T1222: File and Directory Permissions Modification | ||
| T1497: Virtualization/Sandbox Evasion | ||
| T1548: Abuse Elevation Control Mechanism | ||
| T1562.001: Impair Defenses: Disable or Modify Tools | ||
| T1564.001: Hide Artifacts: Hidden Files and Directories | ||
| T1574.002: Hijack Execution Flow: DLL Side- Loading | ||
| 5 | TA0006: Credential Access | T1003: OS Credential Dumping |
| T1552.001: Unsecured Credentials: Credentials In Files | ||
| T1555.003: Credentials from Password Stores: Credentials from Web Browsers | ||
| 6 | TA0007: Discovery | T1010: Application Window Discovery |
| T1012: Query Registry | ||
| T1057: Process Discovery | ||
| T1082: System Information Discovery | ||
| T1083: File and Directory Discovery | ||
| T1087: Account Discovery | ||
| T1497: Virtualization/Sandbox Evasion | ||
| T1518: Software Discovery | ||
| 7 | TA0009: Collection | T1005: Data from Local System |
| T1114: Email Collection | ||
| T1115: Clipboard Data | ||
| T1185: Browser Session Hijacking | ||
| 8 | TA0011: Command and Control | T1071: Application Layer Protocol |
| 9 | TA0040: Impact | T1485: Data Destruction |
| T1486: Data Encrypted for Impact | ||
| T1490: Inhibit System Recovery |
Relevancy and Insights:
ETLM Assessment:
CYFIRMA’s assessment, based on available information, suggests that COBRA ransomware, with its demand for 18 bitcoins, is likely to target economically developed nations located in Europe, East Asia, South-East Asia, and the US, where organizations are more capable of meeting such demands. This reflects a deliberate strategy aimed at entities capable of fulfilling substantial ransom demands. Furthermore, the ransomware is anticipated to persistently target Windows OS, utilizing sophisticated evasion tactics and persistence methods. This will likely result in heightened encryption complexity and system disruption, posing considerable challenges to detection and recovery efforts across various industries. Vigilance and strong cybersecurity measures are essential to mitigate these threats effectively.
Indicators of Compromise
Kindly refer to the IOCs section to exercise controls on your security systems.
Sigma
title: Drops script at startup location threatname:
behaviorgroup: 1
classification: 7 logsource:
service: sysmon product: windows
detection: selection:
EventID: 11 TargetFilename:
– ‘*\AppData\Roaming\Microsoft\Windows\Start Menu\Programs\Startup\\*.vbs*’
– ‘*\AppData\Roaming\Microsoft\Windows\Start Menu\Programs\Startup\\*.js*’
– ‘*\AppData\Roaming\Microsoft\Windows\Start Menu\Programs\Startup\\*.jse*’
– ‘*\AppData\Roaming\Microsoft\Windows\Start Menu\Programs\Startup\\*.bat*’
– ‘*\AppData\Roaming\Microsoft\Windows\Start Menu\Programs\Startup\\*.url*’
– ‘*\AppData\Roaming\Microsoft\Windows\Start Menu\Programs\Startup\\*.cmd*’
– ‘*\AppData\Roaming\Microsoft\Windows\Start Menu\Programs\Startup\\*.hta*’
– ‘*\AppData\Roaming\Microsoft\Windows\Start Menu\Programs\Startup\\*.ps1*’
– ‘*\AppData\Roaming\Microsoft\Windows\Start Menu\Programs\Startup\\*.wsf*’ condition: selection
level: critical
(Source: SurfaceWeb)
STRATEGIC RECOMMENDATIONS
MANAGEMENT RECOMMENDATIONS
TACTICAL RECOMMENDATIONS
Type: Backdoor
Objective: Remote Access, Data Exfiltration
Target Technology: Windows OS, Web Browsers (Google Chrome) and productivity tools (Microsoft Teams)
Active Malware of the Week
This week “Oyster” is trending.
Oyster
Researchers recently identified a malvertising campaign targeting users by offering malicious installers for well-known software like Google Chrome and Microsoft Teams. These installers were actually delivering a backdoor known as Oyster (aka Broomstick and CleanUpLoader). After the backdoor was executed, researchers observed direct control activities, including commands to gather information and the deployment of more malicious software.
Initial Access
Researchers found that users were downloading fake Microsoft Teams installers from websites with URLs similar to the official Microsoft Teams site, a technique called typo- squatting. These deceptive websites appeared in search results on platforms like Google and Bing when users looked for Microsoft Teams downloads. By imitating the legitimate site’s appearance, the fake sites tricked users into believing they were downloading genuine software, but instead, they ended up downloading malicious software from the threat actors.
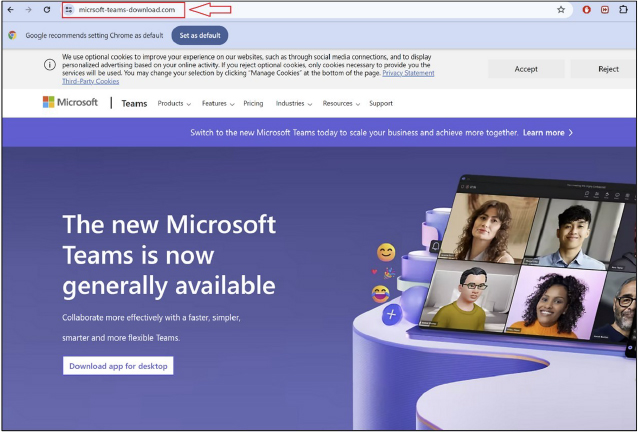
In this scenario, a user visited the URL hxxps[:]//micrsoft-teams-download[.]com/ and downloaded a file named MSTeamsSetup_c_l_.exe. Upon initial examination, it was found that the binary MSTeamsSetup_c_l_.exe had been signed with an authenticode certificate issued to ‘Shanxi Yanghua HOME Furnishings Ltd.’
Technical Analysis
Upon analyzing MSTeamsSetup_c_l_.exe, it was found that it stored two binaries within its resource section. During execution, it used FindResourceA to locate these binaries and LoadResource to access them, subsequently dropping them into the Temp folder. The binaries dropped were identified as CleanUp30.dll and MSTeamsSetup_c_l_.exe (the legitimate Microsoft Teams installer). Following the drop of CleanUp30.dll into Temp, the program executed the DLL using rundll32.exe %s,Test passed to CreateProcessA, where %s represented CleanUp30.dll. After executing CleanUp30.dll, the program then launches the legitimate Microsoft Teams installer, MSTeamsSetup_c_l_.exe, which is also stored in the Temp directory. This strategy aims to prevent arousing suspicion from the user.
CleanUp30.dll Analysis
During the execution of CleanUp30.dll, researchers observed several actions: first, the binary attempted to create a hardcoded mutual exclusion (mutex) named ITrkfSaV- 4c7KwdfnC-Ds165XU4C-lH6R9pk1, commonly used to check if the program is already running to terminate any new instances. Following mutex creation, the binary determined its execution path by using GetModuleFilenameA. This path was then used to create a scheduled task named ClearMngs using ShellExecuteExW. The scheduled task was configured to run every three hours with the command:
The purpose of ClearMngs was to execute CleanUp30.dll’s Test function using rundll32.exe. After setting up the scheduled task, the binary proceeded to decode its command-and-control (C2) server addresses using a unique decoding function. This decoding function processes an encoded string by reading each byte from the end of the string.
The encoded string is decoded using a byte map, where each byte serves as an index to retrieve the decoded byte from a predefined array. This technique helps obscure data and strings commonly used by malware authors. The decoding process involves iterating through the encoded string, swapping pairs of bytes from both ends towards the center, and reversing the originally encoded plaintext strings. To maintain accuracy, all encoded strings must have an even length. After decoding, the string is re-encoded using a similar method. Ultimately, the first decoded string reveals a list of command-and-control (C2) domains delimited by carriage return and line feed (CRLF) characters. After the binary decodes the C2 addresses, the program proceeds to fingerprint the infected machine using the following functions:
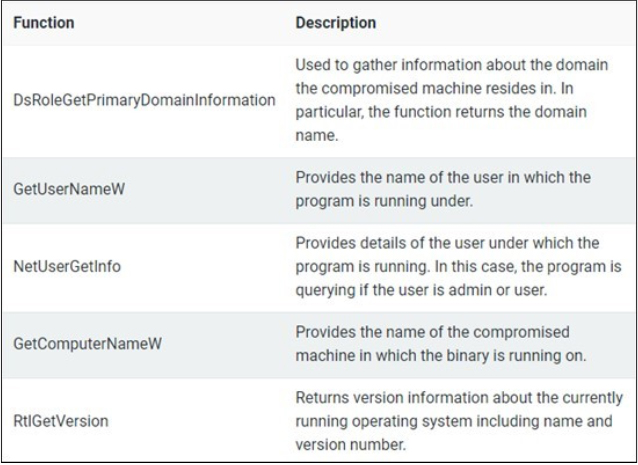
During host information enumeration, the gathered data is stored within JSON fields extracted from decoded strings. The fingerprint information undergoes encoding, following the same reversing and byte map technique, before transmission. Once encoded, it is sent via HTTP POST method to domains such as whereverhomebe[.]com/, supfoundrysettlers[.]us/, and retdirectyourman[.]eu/. Researchers found that CleanUp30.dll utilizes the Boost.Beast C++ library for communication with these command-and-control (C2) domains, supporting both HTTP and web sockets.
Follow-on Activity
In an observed incident, researchers noted the execution of a PowerShell script after another version of CleanUp30.dll, named CleanUp.dll, was executed. This variant of CleanUp.dll was initially dropped by a fake Microsoft Teams installer, TMSSetup.exe, into the AppData/Local/Temp directory. The PowerShell script’s purpose was to create a startup shortcut named DiskCleanUp.lnk in C:\Users\<User>\AppData\Roaming\Microsoft\Windows\Start Menu\Programs\Startup\.
This ensured that DiskCleanUp.lnk would execute each time the user logged in, launching CleanUp.dll using rundll32.exe and the Test export.
Following the PowerShell script’s execution, researchers observed the launch of additional payloads:
These actions were part of the broader malicious activities initiated by the malware after installation on the compromised system.
INSIGHTS
ETLM ASSESSMENT
From the ETLM perspective, CYFIRMA anticipates that the evolution of Oyster malware is expected to persist as cyber attackers refine their strategies. Deceptive tactics, including fake software installers and malvertising campaigns aimed at trusted applications like Microsoft Teams and Google Chrome, will continue to pose significant challenges. For organizations and employees relying on Microsoft Teams, the implications could be substantial. In addition to potential operational disruptions and productivity losses from compromised systems, there remains a heightened risk of data breaches and the exposure of sensitive information.
IOCs:
Kindly refer to the IOCs Section to exercise controls on your security systems.
STRATEGIC RECOMMENDATIONS
MANAGEMENT RECOMMENDATIONS
TACTICAL RECOMMENDATIONS
Key Intelligence Signals:
RedJuliett: Intensified Cyber Espionage on Taiwanese Government, Academia, and Tech Sectors
Summary:
Between November 2023 and April 2024, the researcher identified a series of cyber- espionage activities conducted by RedJuliett, a likely Chinese state-sponsored threat group. RedJuliett primarily targeted government, academic, technology, and diplomatic organizations in Taiwan. The group gained initial access by exploiting known vulnerabilities in network edge devices such as firewalls, VPNs, and load balancers.
They employed structured query language (SQL) injection and directory traversal exploits against web and SQL applications to further penetrate systems. Additionally, RedJuliett conducted reconnaissance and exploitation activities using Acunetix Web Application Security Scanners. Operating likely from Fuzhou, China, RedJuliett’s actions align with its persistent targeting of Taiwan and support Beijing’s intelligence collection on Taiwan’s economic and diplomatic relations, as well as critical technology development.
RedJuliett expanded its operations beyond Taiwan, compromising organizations in Hong Kong, Malaysia, Laos, South Korea, the United States, Djibouti, Kenya, and Rwanda. Post-exploitation, RedJuliett used open-source web shells and exploited an elevation of privilege vulnerability in the Linux operating system to maintain access and escalate their privileges within the compromised networks. They also created SoftEther VPN bridges or clients within victim networks, facilitating persistent access and data exfiltration. The group’s infrastructure was administered using SoftEther VPN, leveraging both threat actor-controlled leased servers and compromised infrastructure from Taiwanese universities.
RedJuliett’s extensive use of internet-facing devices highlights the strategic importance of these vulnerable points. They employed multiple SoftEther nodes from infrastructure geolocating to Fuzhou, reinforcing their operational base. RedJuliett’s activities suggest a comprehensive and multi-layered attack strategy, involving initial access through vulnerabilities, network reconnaissance, lateral movement, and persistence techniques.
The motive behind RedJuliett’s activities is to gather intelligence to support Beijing’s policymaking on cross-strait relations. The group’s focus on critical technology companies indicates a strategic interest in Taiwan’s technological advancements.
RedJuliett’s activities highlight the importance of comprehensive cybersecurity measures. Organizations are advised to adopt network segmentation, enhance security monitoring and detection capabilities for all external-facing services and devices, review public guidance on mitigating Chinese APT activity, prioritize patching high-risk vulnerabilities, and monitor malicious traffic to detect and respond to threats effectively. The continued exploitation of public-facing devices underscores the need for improved security protocols and regular audits of internet-facing and perimeter appliances to reduce the attack surface and detect post-exploitation activities.
Relevancy & Insights:
Flax Typhoon, also known as RedJuliett, has been actively targeting Taiwanese organizations since mid-2021. This group has primarily focused on government agencies, educational institutions, critical manufacturing, and IT sectors. Using living- off-the-land (LotL) techniques and the open-source VPN software SoftEther, Flax Typhoon exploits vulnerabilities in public-facing services such as VPNs, web applications, and SQL applications to gain initial access. Once inside, they establish persistence using the China Chopper web shell on compromised servers to execute remote code. Following initial access, Flax Typhoon relies on open-source tools like JuicyPotato and BadPotato, as well as other LotL techniques. These tactics and techniques closely resemble those reported by CrowdStrike regarding Ethereal Panda, including the use of the open-source web shell Godzilla. This persistent and strategic approach highlights the importance of robust cybersecurity measures to protect against such sophisticated cyber threats.
ETLM Assessment:
RedJuliett is a China-nexus cyber espionage group that has primarily targeted Taiwan, focusing on government, education, and technology sectors. The group exploits vulnerabilities in public-facing services to gain access and uses tools like the China Chopper web shell for persistence. Their operations, which include compromising organizations in Taiwan and other countries, align with strategic objectives likely backed by the Chinese state. RedJuliett’s activities reflect a sophisticated understanding of economic and trade policies in the targeted regions, posing a significant threat to entities within these sectors. The group has conducted reconnaissance and attempted exploitation of at least 75 organizations, mainly within Taiwan’s government, education, and technology sectors. RedJuliett is particularly interested in Taiwan’s economic and trade policies and international affairs, targeting de facto embassies from South and Southeast Asian countries, government departments focused on economic policy, think tanks researching economic policy, and a trade promotion organization. This extensive targeting underscores RedJuliett’s role in advancing Beijing’s intelligence objectives and illustrates a serious concern as threat actors adopt and integrate techniques from other sophisticated groups to enhance their attacks.
Recommendations:
IOCs:
Kindly refer to the IOCs (Indicators of Compromise) Section to exercise controls on your security systems.
Japanese aerospace agency hit by cyberattacks
Researchers have recently revealed that the Japan Aerospace Exploration Agency
(JAXA) has sustained several cyberattacks over the past year. Japanese officials stated that sensitive information related to rockets and satellites was not compromised. According to Japanese media, the attacks targeted a JAXA server for the agency’s general business operations. The Japanese government is investigating the attacks, which have now been confirmed to have originated from outside of Japan.
ETLM Assessment:
This campaign most likely constitutes a classic state-driven espionage effort enabled by cyber means. The Japanese government finds itself in a new strategic envirnemnt with many new threats rising especially from China and North Korea. Many of the limits imposed by the pacifist postwar constitution imposed by Japan’s history (and written by the Americans during the occupation) are now being relaxed or modified, and the current version of the constitution is now being reinterpreted to give the government more room to maneuver. This in return provokes the sources of the threat to Japan to conduct aggressive cyber espionage in order to keep tabs on Japanese capabilities.
The 8Base Ransomware impacts the Taiyo Kogyo Co., Ltd
Summary:
From the External Threat Landscape Management (ETLM) Perspective, CYFIRMA observed in an underground forum that a company from Japan; (www[.]taiyokogyo[.]co[.]jp), was compromised by the 8Base Ransomware. Taiyo Kogyo Co., Ltd., a leading company in the production of large-sized membrane structures, occupies a leading position in the world-class market. It operates on seven continents and has worked on numerous buildings, including stadiums, international airports, and exposition centers. The compromised data contains Invoices, Receipts, Accounting documents, Personal data, Certificates, Employment contracts, Confidentiality agreements, Personal files, and Others.
The following screenshot was observed published on the dark web:

Relevancy & Insights:
ETLM Assessment:
Based on the available information, CYFIRMA’s assessment indicates that 8Base Ransomware will continue to target various industries globally, with a significant emphasis on the United States, European, and Asian regions. The recent incident involving an attack on Taiyo Kogyo Co., Ltd, a prominent Construction company located in Japan, underscores the extensive threat posed by this particular ransomware strain in the Asia Pacific region.
The DarkVault Ransomware impacts the OExpress
Summary:
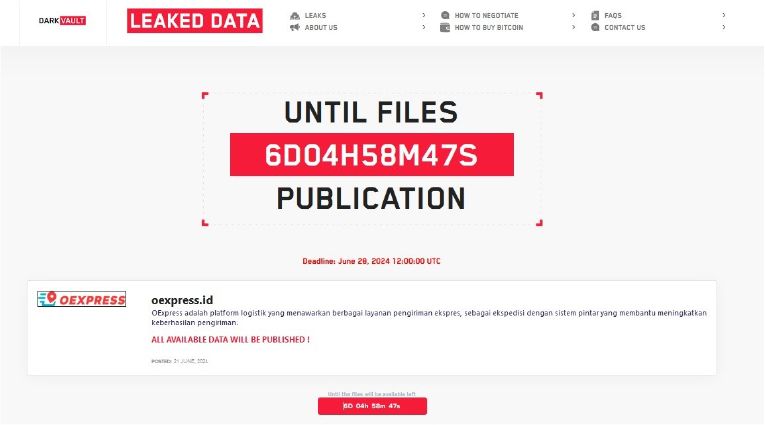
From the External Threat Landscape Management (ETLM) Perspective, CYFIRMA observed in an underground forum that a company from Indonesia; (www[.]oexpress[.]id), was compromised by the DarkVault Ransomware. OExpress is a logistics platform that offers various express delivery services, as an expedition with a smart system that helps increase delivery success. The data, which has been breached, has not yet appeared on the leak site, indicating that negotiations between the affected party and the ransomware group may be underway. The compromised data includes confidential and sensitive information belonging to the organization.
The following screenshot was observed published on the dark web:
Relevancy & Insights:
ETLM Assessment:
The DarkVault ransomware group has honed its approach to deploying ransomware by leveraging a variety of sophisticated techniques. These include phishing emails, which lure victims into clicking on malicious links or attachments and exploiting vulnerabilities in unpatched software to gain initial access to systems. According to CYFIRMA’s assessment, DarkVault is likely to continue its aggressive targeting of a wide array of industries on a global scale. Their focus is particularly intense in the United States, Europe, and Asia. A recent attack on OExpress, a leading Logistics company based in Indonesia, highlights the broad and severe threat posed by DarkVault, especially in Southeast Asia. This incident underscores the group’s capacity to disrupt operations and underscores the critical need for robust cybersecurity defenses across diverse regions and sectors.
Vulnerability in Apache StreamPipes
Summary:
The vulnerability allows a remote attacker to compromise accounts of application users.
Relevancy & Insights:
The vulnerability exists due to the usage of a weak pseudo-random number generator for recovery tokens.
Impact :
A remote attacker can use the self-registration and password recovery mechanism to take over an arbitrary user account.
Affected Products:
https[:]//lists[.]apache[.]org/thread/zqn5z48gz7bp0q8ctk96ht8bc7vd3njv
Recommendations:
Monitoring and Detection: Implement monitoring and detection mechanisms to identify unusual system behavior that might indicate an attempted exploitation of this vulnerability.
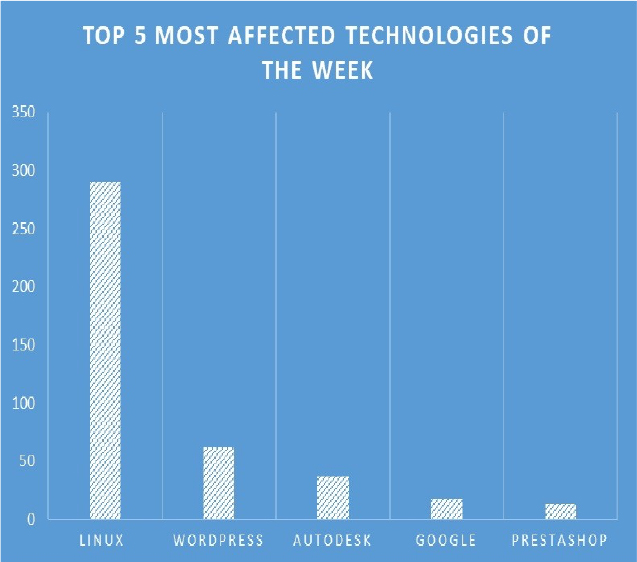
TOP 5 AFFECTED PRODUCTS OF THE WEEK
This week, CYFIRMA researchers have observed significant impacts on various technologies, due to a range of vulnerabilities. The following are the top 5 most affected technologies.
ETLM Assessment:
Vulnerability in Apache StreamPipes can pose significant threats to user privacy and security. This can impact various industries globally, including technology, finance, healthcare, and beyond. Ensuring the security of Apache StreamPipes is crucial for maintaining the integrity and protection of users’ data worldwide. Therefore, addressing these vulnerabilities is essential to safeguarding online activities, including connecting, analyzing, and exploring IoT data streams, across different geographic regions and sectors.
Spacebears Ransomware attacked and Published data of SAWA INTERNATIONAL
Summary:
Recently we observed that Spacebears Ransomware attacked and published data of SAWA INTERNATIONAL(www[.]sawainternational[.]com) on its darkweb website. SAWA International in the UAE operates primarily as a partner for telecom services, specifically focusing on providing personalized telecom plans for homes and businesses in collaboration with Emirates Integrated Telecommunications Corporation, commonly known as DU. The data leak, following the ransomware attack, encompasses Databases, Financial Reports, and other Valuable and Confidential Information, Personal Information (Photo, IDs. etc), Contracts, and Documents in multiple formats, including Excel (.xls), Word (.docx), and PDF (.pdf).
Relevancy & Insights:
SpaceBears utilizes advanced encryption methods to lock victims’ data and demands large ransoms in exchange for decryption keys. They typically employ social engineering tactics like phishing emails to gain initial access to the systems.
ETLM Assessment:
SpaceBears is an emerging ransomware group that has recently garnered attention due to several high-profile attacks. Known for its sophisticated tactics, the group is suspected to be based in Moscow, Russia, and operates with a distinct corporate-like structure, which sets it apart from many other ransomware groups. Based on the available information, CYFIRMA’s assessment indicates that SpaceBears Ransomware will continue to target various industries globally, with a significant emphasis on the United States, European, and Asian regions. The recent incident involving an attack on SAWA INTERNATIONAL, a prominent Telecommunication company located in the United Arab Emirates, underscores the extensive threat posed by this particular ransomware strain in the Middle East.

Relevancy & Insights:
SpaceBears utilizes advanced encryption methods to lock victims’ data and demands large ransoms in exchange for decryption keys. They typically employ social engineering tactics like phishing emails to gain initial access to the systems.
ETLM Assessment:
SpaceBears is an emerging ransomware group that has recently garnered attention due to several high-profile attacks. Known for its sophisticated tactics, the group is suspected to be based in Moscow, Russia, and operates with a distinct corporate-like structure, which sets it apart from many other ransomware groups. Based on the available information, CYFIRMA’s assessment indicates that SpaceBears Ransomware will continue to target various industries globally, with a significant emphasis on the United States, European, and Asian regions. The recent incident involving an attack on SAWA INTERNATIONAL, a prominent Telecommunication company located in the United Arab Emirates, underscores the extensive threat posed by this particular ransomware strain in the Middle East.
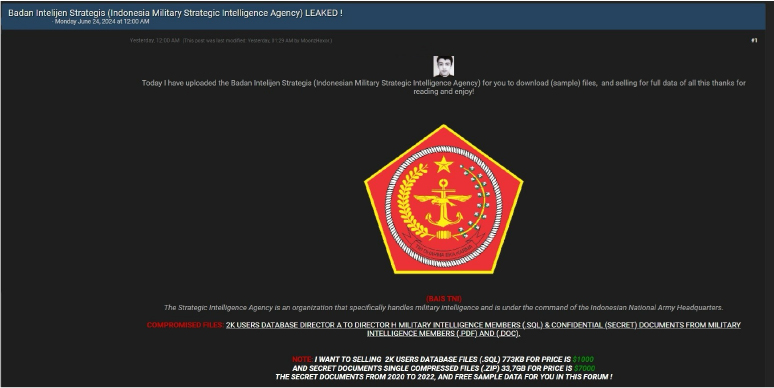
Badan Intelijen Strategis (Indonesian Military Strategic Intelligence Agency) Data Advertised on a Leak Site
Summary:
The CYFIRMA Research team observed a potential data sale related to Badan Intelijen Strategis (Indonesian Military Strategic Intelligence Agency) in an underground forum. A threat actor claims to be selling highly sensitive data from the Badan Intelijen Strategis (Indonesian Military Strategic Intelligence Agency). The data breach is allegedly claimed by the threat actor ‘MoonzHaxor’
Badan Intelijen Strategis (Indonesian Military Strategic Intelligence Agency)Data
The threat actor has allegedly posted a sample of the data for download and is offering the full dataset for sale. The Strategic Intelligence Agency is responsible for military intelligence and operates under the command of the Indonesian National Army Headquarters.
Compromised Files:
2,000 user databases (.SQL) containing data such as:
Id, name, task force, rank, username, email, password, avatar, tokens, phone number, IMEI, last seen, generation, NRP, device, manufacture, OS, app version
Confidential (secret) documents from military intelligence members (.PDF and .DOC) from 2020 to 2022
Pricing:
User database files (.SQL), 773KB: $1,000 Secret documents (.ZIP), 33.7GB: $7,000 Free sample data available on the forum The threat actor states that they are accepting payments only in cryptocurrency, specifically XMR (Monero), and can be contacted via Telegram.
INAFIS (Indonesia Automatic Fingerprint Identification System) data advertised on a Leak Site
Summary:
The CYFIRMA Research team observed a potential data leak related to INAFIS (Indonesia Automatic Fingerprint Identification System) in an underground forum. The threat actor claims to be selling data from INAFIS (Indonesia Automatic Fingerprint Identification System), which is crucial for the identification process through fingerprints and focuses on collecting authentic data on the Indonesian population. The data breach is allegedly claimed by the threat actor ‘MoonzHaxor’
Compromised Files:
INAFIS faces member images (.PNG) with email INAFIS fingerprints member images (.WSQ) with email
INAFIS SpringBoot application (.JAR) with database configuration properties Pricing:
INAFIS SpringBoot application with configuration: $1,000
Potential to access API/DB with 200+ million Indonesian ID card numbers through reverse engineering the application
The threat actor further claims that anyone interested in the INAFIS data can contact them via Telegram.
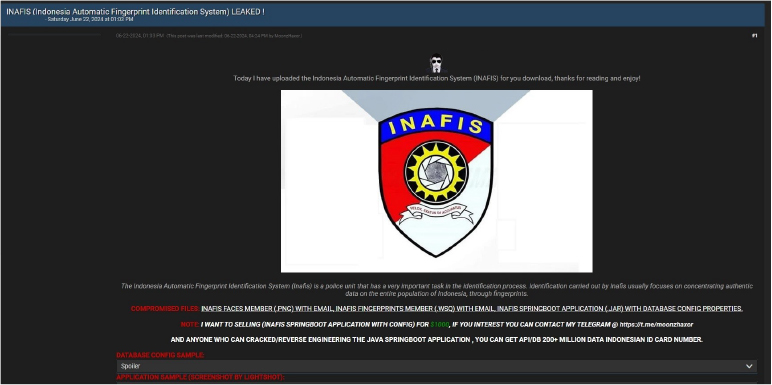
Relevancy & Insights:
Financially motivated cybercriminals are continuously scouring for exposed and vulnerable systems and applications to exploit. A significant number of these malicious actors congregate within underground forums, where they discuss cybercrime and trade stolen digital assets. Operating discreetly, these opportunistic attackers target unpatched systems or vulnerabilities in applications to illicitly gain access and steal valuable data. Subsequently, the pilfered data is advertised for sale within underground markets, where it can be acquired, repurposed, and utilized by other malicious actors in further illicit activities.
ETLM Assessment:
According to CYFIRMA’s analysis, the financially driven cybercriminal known as ‘MoonzHaxor’ presents a considerable threat to organizations across various sectors. This actor is notorious for infiltrating institutions with weak cybersecurity defenses and subsequently monetizing the stolen sensitive data through sales on the dark web and other illicit forums. ‘MoonzHaxor’ frequently targets entities that lack robust security protocols, making them susceptible to these sophisticated and opportunistic cyberattacks.
Recommendations: Enhance the cybersecurity posture by
CYFIRMA Research team observed a potential data breach related to MyRepublic Indonesia (www.myrepublic.co.id). A threat actor has announced the sale of a database allegedly obtained from a recent breach of MyRepublic Indonesia, a prominent telecommunications company known for its high-speed fiber broadband services. MyRepublic operates across several countries, offering broadband internet, mobile services, and enterprise solutions. The threat actor disclosed their intent to sell the breached database, emphasizing that it includes comprehensive customer data. They are open to using a middleman for transactions and exclusively accept payments in Monero (XMR). They urge interested parties to contact them via private message to negotiate offers. The compromised dataset reportedly contains a variety of sensitive information, including customer IDs, names, email addresses, phone numbers, residential addresses, internet and TV service plans, sales and service dates, promotional details, and more. The data breach is allegedly claimed by the threat actor ‘abyss0’.

ETLM Assessment :
Threat Actor ‘abyss0’ group has become active in underground forums and has emerged as a formidable force in cybercrime mainly for financial gains. The threat actor has already targeted Government, Industrial Conglomerates, Retail, Staffing, Business consulting, Banks, E-Commerce, Electric & Utilities industries, indicating its intention to expand its attack surface in the future to other industries globally.
STRATEGIC RECOMMENDATIONS
MANAGEMENT RECOMMENDATIONS
TACTICAL RECOMMENDATIONS
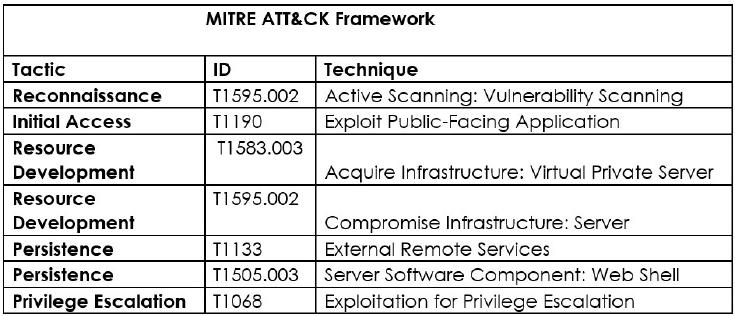
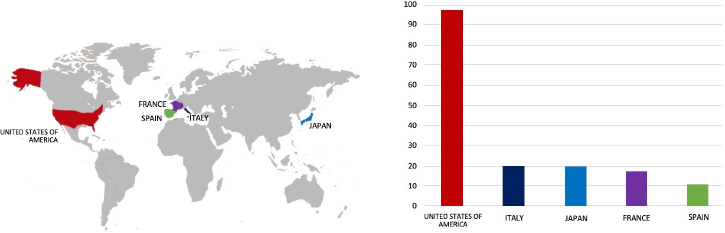
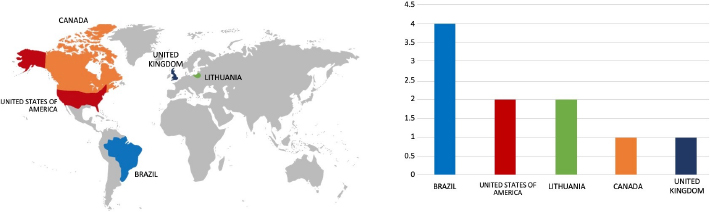
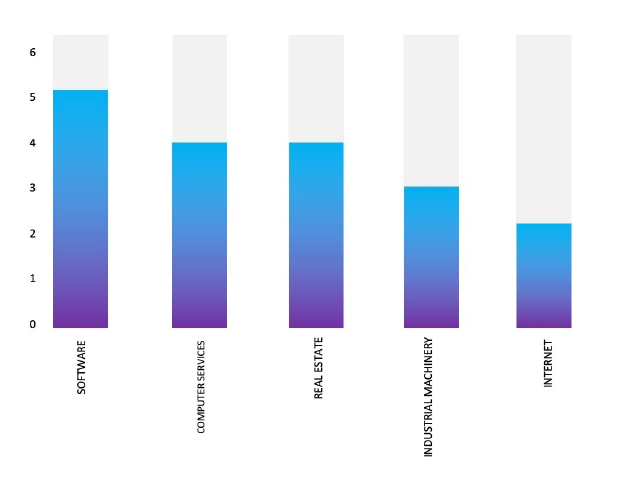
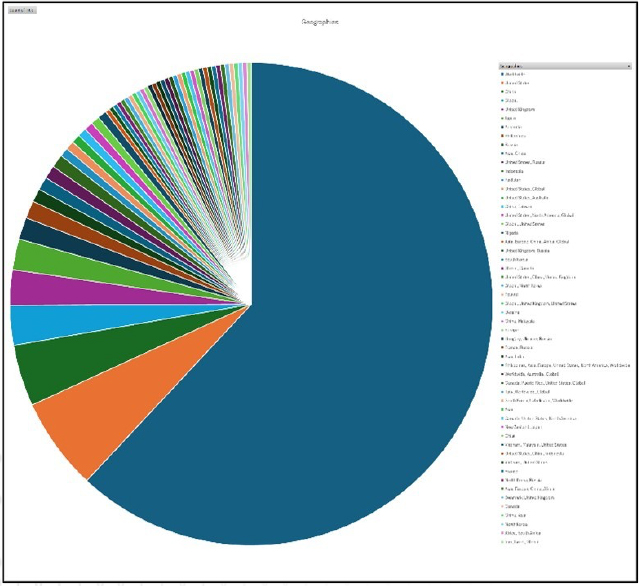
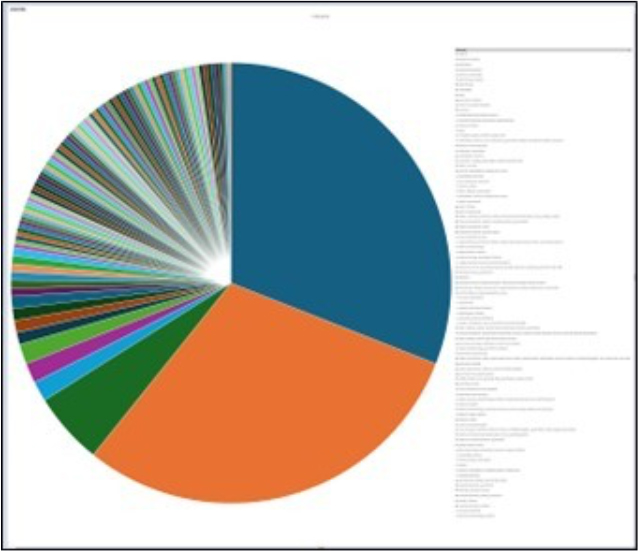
Please find the Geography-Wise and Industry-Wise breakup of cyber news for the last 5 days as part of the situational awareness pillar.
Geography-Wise Graph
Industry-Wise Graph
For situational awareness intelligence and specific insights mapped to your organisation’s geography, industry, technology, please access DeCYFIR.