


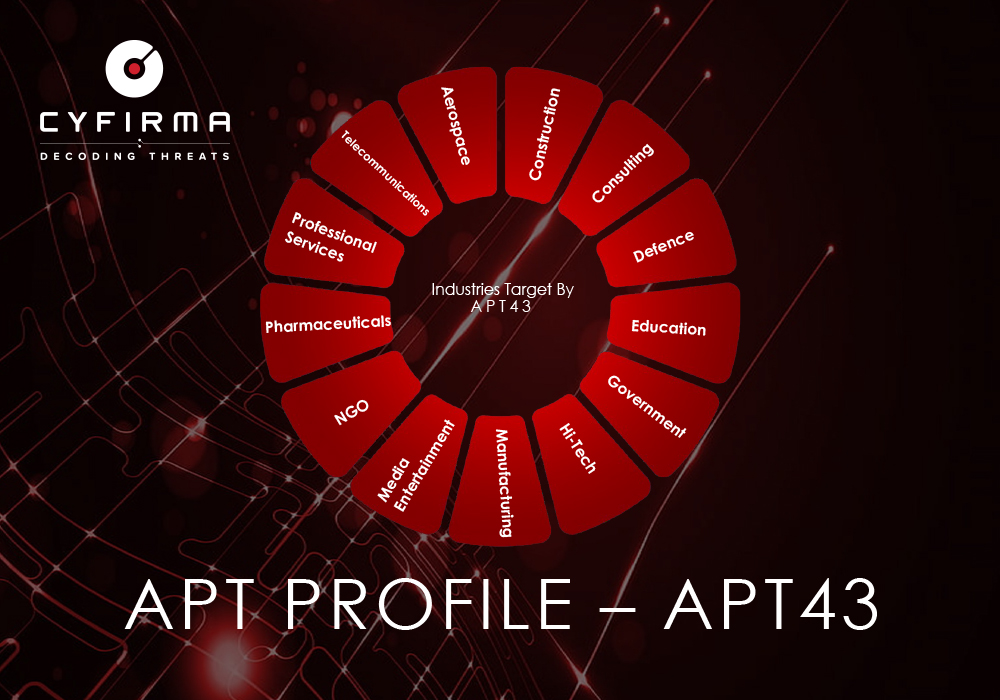
APT43, a North Korean state-sponsored cyber operator linked to the Reconnaissance General Bureau (RGB), is known for its strategic intelligence gathering and financially motivated activities.
Alias:
Black Banshee, Emerald Sleet, Kimsuki, Kimsuky, Sparkling Pisces, Springtail, TA427, Thallium, UAT-5394, Velvet Chollima
Motivation:
Espionage
Techniques Used:
Credential Harvesting, Vulnerabilities & Exploits, Social Engineering
Malware used by APT43:
RftRAT, VENOMBITE, AutoIt, DEEP#GOSU, BITTERSWEET, SmallTiger, Meterpeter,TinyNuke, AppleSeed, Amadey, SWEETDROP, SuperBear
South Korea, the United States, Japan, China, and European countries (particularly those with ties to NATO).
| Reconnaissance | Execution | Defense Evasion | Lateral Movement | Discovery | |
| T1594 | T1053.005 | T1027 | T1550.002 | T1016 | |
| T1593.001 | T1059.003 | T1562.001 | T1021.001 | T1518.001 | |
| T1593.002 | T1059.001 | T1112 | T1534 | T1057 | |
| T1591 | T1204.001 | T1036 | T1012 | ||
| T1589.002 | T1059.006 | T1055 | Collection | T1040 | |
| T1598.003 | T1204.002 | T1078.003 | T1005 | T1082 | |
| T1589.003 | T1059.007 | T1564.002 | T1114.003 | T1083 | |
| T1059.005 | T1564.003 | T1074.001 | T1007 | ||
| Resource Development | T1562.004 | T1114.002 | |||
| T1587 | Persistence | T1218.005 | T1560.001 | ||
| T1585.002 | T1505.003 | T1218.011 | T1056.001 | ||
| T1583.006 | T1543.003 | T1218.010 | T1560.003 | ||
| T1608.001 | T1176 | T1036.005 | T1557 | ||
| T1583.004 | T1133 | T1027.002 | |||
| T1588.002 | T1078.003 | T1553.002 | Command and Control | ||
| T1584.001 | T1098 | T1550.002 | T1071.001 | ||
| T1588.005 | T1053.005 | T1036.004 | T1102.002 | ||
| T1587.001 | T1136.001 | T1140 | T1219 | ||
| T1583.001 | T1547.001 | T1070.004 | T1071.003 | ||
| T1586.002 | T1546.001 | T1070.006 | T1071.002 | ||
| T1585.001 | T1055.012 | T1105 | |||
| Initial Access | Privilege Escalation | Credential Access | Exfiltration | ||
| T1133 | T1543.003 | T1111 | T1567.002 | ||
| T1078.003 | T1055 | T1555.003 | T1041 | ||
| T1566.001 | T1078.003 | T1552.001 | |||
| T1566.002 | T1053.005 | T1040 | |||
| T1190 | T1547.001 | T1003.001 | |||
| T1546.001 | T1056.001 | ||||
| T1055.012 | T1557 | ||||
Recent Campaign Highlights:
Trends: