Published On : 2025-03-14
Volt Typhoon is a Chinese state-sponsored hacker group that has been targeting critical infrastructure in the United States and other countries. The group is believed to be working on behalf of the Chinese government and has been accused of conducting espionage and sabotage.
Alias:
BRONZE SILHOUETTE , Dev-0391 , Insidious Taurus , UNC3236 , Vanguard Panda , Voltzite
Motivation:
Espionage, Information theft, Intelligence gathering
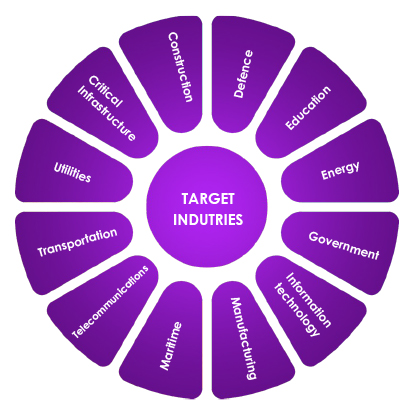
Target Technologies
Cisco, Net Gear routers, SOHO routers, firewalls & VPN, Zoho
Techniques used by Volt Typhoon
Credential Harvesting, Custom Malware Implant, Spear-Phishing, Vulnerabilities & Exploits, Living of the land
Targeted Country
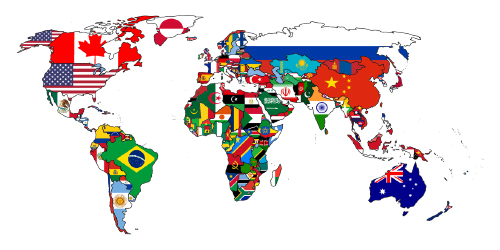
The United States of America, United Kingdom, Canada, India, Japan, Germany, Taiwan, South Korea, New Zealand, Australia, Philippines, Malaysia, and Vietnam.
Recently Exploited Vulnerabilities by Volt Typhoon
- CVE-2022-42475
- CVE-2024-21887
- CVE-2023-46805
- CVE-2021-40539
Recent TTP of Volt Typhoon
Initial Access (TA0001)
Technique: Valid Accounts (T1078)
Execution (TA0002)
Technique: Living Off the Land (LOTL)
Lateral Movement (TA0008)
Technique: Remote Services (T1021)
Collection (TA0009)
Technique: Data from Local System (T1005)
Persistence (TA0003)
Technique: Scheduled Tasks (T1053)
Privilege Escalation (TA0004)
Technique: Exploitation for Privilege Escalation (T1068)
Discovery (TA0007)
Technique: Network Service Scanning (T1046)
Exfiltration (TA0010)
Technique: Exfiltration Over C2 Channels (T1041)
Impact (TA0040)
Technique: Data Destruction (T1485)
1. Initial Access (TA0001)
Technique: Valid Accounts (T1078)
- Volt Typhoon acquires credentials via phishing, credential dumping (e.g., Mimikatz), or brute-forcing weak passwords on SOHO routers (Cisco RV320/325, Netgear ProSafe)
- Targets vulnerabilities in Fortinet FortiGuard and Versa Networks SD-WAN (CVE-2024-39717) to infiltrate critical infrastructure networks
2. Execution (TA0002)
Technique: Living Off the Land (LOTL)
- Uses native tools like PowerShell, Bash, wmic, and netsh to execute commands, avoiding custom malware and blending with legitimate traffic.
3. Persistence (TA0003)
Technique: Scheduled Tasks (T1053)
- Creates cron jobs or scheduled tasks to maintain access after reboots (e.g., schtasks /create on Windows).
- Leverages compromised SOHO routers as “silent bridges” for C2 infrastructure, rebuilding botnets rapidly after takedowns.
4. Privilege Escalation (TA0004)
Technique: Exploitation for Privilege Escalation (T1068)
- Exploits unpatched vulnerabilities in legacy systems (e.g., CVE-2020-1472 (Netlogon), CVE-2021-42278 (Active Directory)) to gain domain admin rights.
- Uses ntdsutil to extract Active Directory credentials.
5. Discovery (TA0007)
Technique: Network Service Scanning (T1046)
- Maps networks using commands like nmap, netstat, and ipconfig to identify open ports, services, and lateral movement paths.
- Reconnaissance focus: Gathers intel on ICS/SCADA systems, energy grids, and telecom networks.
6. Lateral Movement (TA0008)
Technique: Remote Services (T1021)
- Uses RDP and SSH with stolen credentials to pivot across systems.
- Example command: rdesktop -u <user> -p <password> <target_IP>
7. Collection (TA0009)
Technique: Data from Local System (T1005)
- Harvests sensitive files (documents, emails, backups) using PowerShell scripts and LOLBins like robocopy.
- Targets file types: .docx, .xlsx, .pdf, .pst.
8. Exfiltration (TA0010)
Technique: Exfiltration Over C2 Channels (T1041)
- Compresses and encrypts data (e.g., via 7-Zip) before exfiltrating through HTTPS or encrypted C2 channels.
- Uses cloud services (e.g., compromised AWS/Azure instances) for data staging.
9. Impact (TA0040)
Technique: Data Destruction (T1485)
- Deletes logs (e.g., wevtutil cl Security) and overwrites files to hinder forensics.
- Prepares for disruptive attacks by erasing backups or ICS configurations.
Volt Typhoon’s Recent Campaign Highlights and Trends
Recent Campaign Highlights
1. Botnet Resurgence and Infrastructure Rebuilding
- Botnet Revival: Despite a major FBI-led takedown of its “KV Botnet” in December 2023, Volt Typhoon swiftly rebuilt its infrastructure by exploiting outdated Cisco RV320/325 and Netgear ProSafe routers. By November 2024, the group had compromised 30% of visible Cisco RV320/325 routers within 37 days, using them as covert relay nodes.
- New Caledonia Hub: A compromised VPN device in New Caledonia acts as a critical operational hub, enabling stealthy traffic routing between Asia-Pacific and U.S. targets. This “silent bridge” facilitates undetected command-and-control (C2) operations.
2. Zero-Day Exploitation (CVE-2024-39717)
- Versa Networks SD-WAN Attack: In June 2024, Volt Typhoon exploited a zero-day vulnerability in Versa Director servers (CVE-2024-39717), used by ISPs and MSPs to manage SD-WAN configurations. The group deployed a custom web shell (VersaMem) to intercept credentials and pivot into downstream customer networks.
- Targeted Sectors: Attacks focused on U.S. and global IT, MSP, and ISP sectors, enabling large-scale supply chain compromises.
3. Long-Term Persistence in Critical Infrastructure
- Five-Year Infiltration: U.S. agencies confirmed Volt Typhoon maintained access to some victim networks for at least five years, emphasizing their focus on pre-positioning for potential disruptive cyberattacks.
- Living Off the Land (LOTL): The group relies heavily on LOTL techniques, using legitimate tools like PowerShell and compromised credentials to evade detection while targeting energy, water, transportation, and communications sectors.
Key Trends
1. Adaptive Infrastructure Resilience
- Rapid Botnet Rebuilds: Volt Typhoon demonstrates remarkable agility in rebuilding infrastructure post-disruption. After the FBI’s December 2023 takedown, the group attempted to re-exploit 2,100 NetGear ProSAFE devices within three days.
- Exploitation of Legacy Devices: The group prioritizes end-of-life (EOL) routers and firewalls (e.g., Cisco, Netgear) that lack patches or monitoring, ensuring prolonged access.
2. Strategic Geopolitical Targeting
- Critical Infrastructure Focus: Volt Typhoon’s campaigns align with China’s strategic interests, targeting sectors vital to U.S. and allied stability, including energy grids, water systems, and telecommunications.
- Shift to Disruptive Posture: Recent advisories highlight a strategic shift from espionage to pre-positioning for disruptive attacks, raising concerns about potential kinetic cyber-physical impacts.
3. Collaboration with Cybercrime Ecosystems
- Ransomware Ties: While Volt Typhoon does not deploy ransomware directly, its operations intersect with ransomware-as-a-service (RaaS) groups, which reinvest extortion profits into advanced tooling. This synergy amplifies risks to critical infrastructure.