



CVE-2025-24813 is a critical Remote Code Execution (RCE) vulnerability in Apache Tomcat, stemming from a path equivalence flaw that allows attackers to bypass security constraints and execute arbitrary code remotely.
CYFIRMA research has identified active exploitation, with PoC exploits circulating on underground forums. Attackers leverage HTTP PUT-based arbitrary file uploads, NTFS junction exploitation, and malicious deserialization to gain persistence and escalate privileges. Affected versions range from Apache Tomcat 9.0.0.M1 to 11.0.2. Immediate mitigation includes upgrading to patched versions, disabling unnecessary HTTP methods, enforcing strict access controls, deploying WAFs, and continuous monitoring for threat indicators.
CVE-2025-24813 is a newly identified critical vulnerability in Apache Tomcat, a widely used open-source servlet container and web server for Java applications. This flaw, classified as a Remote Code Execution (RCE) vulnerability, enables attackers to exploit a path equivalence issue, allowing them to bypass security restrictions and execute arbitrary code remotely. Given Apache Tomcat’s widespread use in enterprise and cloud environments, this vulnerability presents a severe risk to organizations reliant on it for web application hosting.
The vulnerability stems from the improper handling of HTTP requests, which permits unauthorized access to restricted directories and sensitive files. Exploiting this flaw can lead to privilege escalation, system compromise, and potential lateral movement within an organization’s infrastructure. Security researchers have observed active exploitation attempts, with publicly available proof-of-concept (PoC) exploits increasing the urgency of mitigation.
Key Takeaways:
Acknowledgements:
CYFIRMA Research acknowledges the collaborative efforts of security researchers, cybersecurity vendors, and the open-source community in identifying, analyzing, and mitigating the CVE-2025-24813 vulnerability. Their contributions have been instrumental in raising awareness and ensuring timely security patches to protect organizations from potential exploitation.
Vulnerability Type: Remote Code Execution (RCE) via Path Equivalence
CVE ID: CVE-2025-24813
Application: Apache Tomcat
Impact: Attackers can bypass security controls and execute arbitrary code remotely, leading to system compromise.
Severity: Critical
Affected Versions: from 11.0.0-M1 through 11.0.2, from 10.1.0-M1 through 10.1.34, from 9.0.0.M1 through 9.0.98.
Patch Available: Yes
Mitigation: Organizations should update to the latest patched versions, disable unnecessary HTTP methods, and enforce strict access controls.
CVE-2025-24813 is a critical Remote Code Execution (RCE) vulnerability affecting Apache Tomcat. The flaw originates from a path equivalence issue in the server’s request-handling mechanism, allowing attackers to bypass security constraints and execute arbitrary code remotely.
By crafting specially designed HTTP requests, attackers can gain unauthorized access to restricted resources, manipulate server configurations, and execute malicious commands. This vulnerability is particularly dangerous due to Apache Tomcat’s widespread use in enterprise environments, where successful exploitation could lead to privilege escalation, data exfiltration, and lateral movement across networks.
This issue affects Apache Tomcat: from 11.0.0-M1 through 11.0.2, from 10.1.0-M1 through 10.1.34, from 9.0.0.M1 through 9.0.98.
Is there already an exploit tool to attack this vulnerability?
Yes, public proof-of-concept (PoC) exploits for CVE-2025-24813 have been released. Security researchers have observed working exploit scripts circulating on platforms such as GitHub and underground forums, allowing attackers to leverage this vulnerability for remote code execution (RCE).
Has this vulnerability already been used in an attack?
Yes, active exploitation of CVE-2025-24813 has been observed in the wild. Threat actors are leveraging this vulnerability to gain unauthorized access to Apache Tomcat servers, execute arbitrary code, and compromise web applications. Organizations using vulnerable versions should assume they are at risk and take immediate action to secure their systems.
Are hackers discussing this vulnerability in the Deep/Dark Web?
Yes, discussions regarding CVE-2025-24813 have been identified on hacker forums and dark web marketplaces. This increases the likelihood of mass exploitation, making proactive monitoring essential.
What is the attack complexity level?
The attack complexity for CVE-2025-24813 is classified as HIGH. Exploiting this vulnerability does require significant technical expertise, making it accessible to both advanced threat actors and lower-skilled cybercriminals.
Historical Trends and Known Exploits
Remote Code Execution (RCE) vulnerabilities in Apache Tomcat have historically been high-value targets for cybercriminals. Previous Tomcat vulnerabilities, such as CVE-2020-1938 (“Ghostcat”) and CVE-2017-12617, were widely exploited in the past. The active public discussion of CVE-2025-24813 indicates that this vulnerability is likely to follow a similar threat trajectory, warranting urgent security measures.
Organizations should immediately patch affected systems, monitor for suspicious activity, and implement strict access controls to mitigate the risk.
CVE-2025-24813 is a critical remote code execution (RCE) vulnerability in Apache Tomcat, allowing attackers to upload and execute arbitrary payloads due to improper input validation and misconfigured servlet handling mechanisms. This vulnerability can be exploited by crafting HTTP requests that bypass security constraints, ultimately enabling the execution of unauthorized commands on the target server.
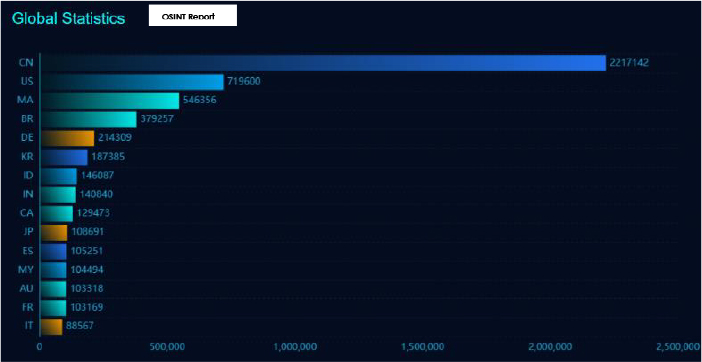
Our analysis found more than 6,611,413+ Apache Tomcat, which can be vulnerable to CVE-2025-24813.
The flaw arises from improper enforcement of security policies on file uploads. The primary weaknesses include:
The attack consists of multiple stages, each designed to manipulate Apache Tomcat’s handling of session objects and file uploads.
Identifying a Writable Target
The attacker first determines whether the target server allows arbitrary file uploads via HTTP PUT requests:

If the response code is 200 OK or 201 Created, the target is vulnerable.
Crafting a Malicious Payload
Generating a Serialized Payload
The attacker generates a malicious Java serialized payload using ysoserial, targeting deserialization vulnerabilities in Apache Tomcat’s session processing:

Creating a Java-based Payload
Alternatively, a Java payload can be used to execute arbitrary shell commands:

The payload is then compiled and converted into a JAR file:

Uploading the Exploit
The attacker attempts to upload the malicious payload into a vulnerable directory, such as the session storage folder:

Apache Tomcat mistakenly treats this file as a legitimate session object due to the directory traversal.
Triggering Deserialization and Code Execution
Once the payload is uploaded, the attacker forces Apache Tomcat to deserialize the malicious session object by sending an HTTP request that loads the session:

Upon processing, Apache Tomcat deserializes the file and executes the payload, leading to remote code execution (RCE).
Post-Exploitation and Persistence
Once the attacker gains SYSTEM privileges, they can establish persistent access through:
NTFS Junction Exploitation
On Windows, NTFS junctions allow an attacker to redirect file operations to protected locations, potentially deleting or modifying critical system files.

This redirection enables privilege escalation when Tomcat logs are cleared, as the operation now affects protected system files.
MSI Rollback Attack
The MSI rollback mechanism can be abused to replace legitimate executables with malicious ones:
Trigger an MSI installation rollback

Hijack rollback scripts to execute arbitrary code

To mitigate the risks associated with CVE-2025-24813, follow these security recommendations:
Target Geography
The impact of CVE-2025-24813 extends globally, affecting organizations and individuals utilizing Apache Tomcat for web applications. This vulnerability poses a critical risk to businesses and institutions across North America, Europe, Asia, and other regions where Apache Tomcat is widely deployed in enterprise IT infrastructures, cloud environments, and web hosting services. The prevalence of Tomcat in corporate, government, and financial sectors makes this a global security concern, with organizations of all sizes vulnerable to potential exploitation.
Target Industries
CVE-2025-24813 is a significant threat across multiple industries that rely on Apache Tomcat for hosting Java-based applications. The most at-risk industries include:
Technology & IT Services: enterprises running Java-based applications on Tomcat servers.
Financial Services & Banking: Institutions hosting secure financial applications.
Healthcare & Government: organizations with sensitive data and critical services reliant on web-based infrastructure.
Education & Research: universities and institutions using Tomcat for e-learning and administrative applications.
Cybercriminals are likely to prioritize industries handling sensitive data or mission-critical services, increasing the risk of data breaches, system compromise, and operational disruptions.
Target Technology
This vulnerability specifically affects Apache Tomcat versions 11.0.0-M1 through 11.0.2, from 10.1.0-M1 through 10.1.34, from 9.0.0.M1 through 9.0.98, leading to remote code execution (RCE) through path equivalence exploitation. Given the extensive use of Apache Tomcat across cloud-hosted environments, enterprise networks, and public-facing web applications, the threat extends to interconnected applications, APIs, and third-party services relying on vulnerable Tomcat deployments.
Currently, threat actors are actively discussing the vulnerability. However, the CYFIRMA Research team is continuously monitoring for new developments or discussions.

The case of CVE-2025-24813 highlights the critical security risks associated with improper access control and misconfigurations in widely used enterprise web infrastructure. This vulnerability underscores the importance of proactive security measures, including timely patching, strict access control policies, and continuous monitoring of publicly exposed services like Apache Tomcat.
This incident serves as a reminder that attackers continuously exploit overlooked security flaws, making regular security assessments, threat intelligence monitoring, and incident response planning essential in defending against emerging cyber threats.