



The CYFIRMA Industry Report delivers original cybersecurity insights and telemetry-driven statistics of global industries, covering one sector each week for a quarter. This report focuses on the finance industry, presenting key trends and statistics in an engaging infographic format.
Welcome to the CYFIRMA infographic industry report, where we delve into the external threat landscape of the finance industry over the past three months. This report provides valuable insights and data-driven statistics, delivering a concise analysis of attack campaigns, phishing telemetry, and ransomware incidents targeting the energy industry.
We aim to present an industry-specific overview in a convenient, engaging, and informative format. Leveraging our cutting-edge platform telemetry and the expertise of our analysts, we bring you actionable intelligence to stay ahead in the cybersecurity landscape.
CYFIRMA provides cyber threat intelligence and external threat landscape management platforms, DeCYFIR and DeTCT, which utilize artificial intelligence and machine learning to ingest and process relevant data, complemented by manual CTI research.
For the purpose of these reports, we leverage the following data from our platform. These are data processed by AI and ML automation based on both human research input and automated ingestions.
While this report contains statistics and graphs generated primarily by automation, it undergoes thorough review and enhancement for additional context by CYFIRMA CTI analysts to ensure the highest quality and provide valuable insights.
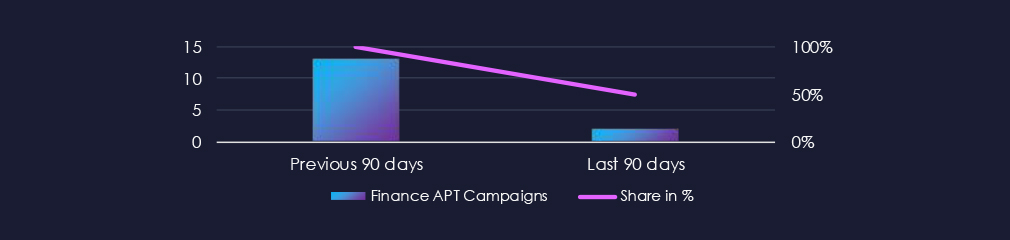
Finance organizations featured in 2 out of the 4 observed campaigns, which is a presence in 50% of all campaigns. A significant drop from 13 campaigns and 100% presence in the previous 90-day period.
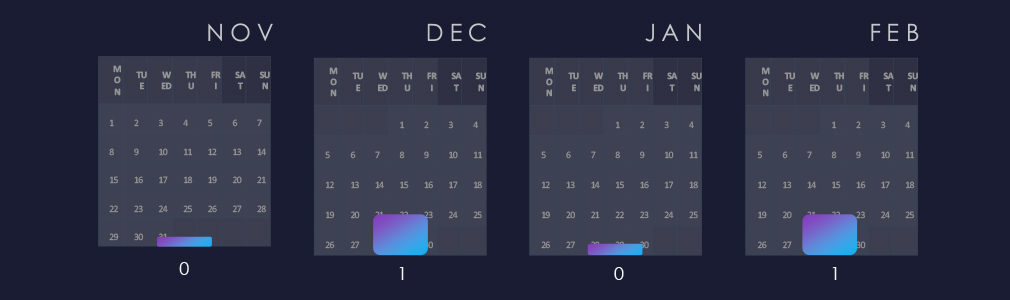
Observed campaigns are distributed intermittently and alternate between months.
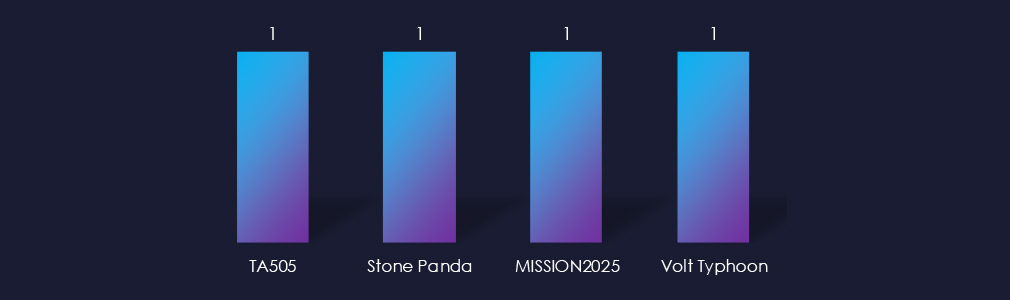
Both observed campaigns attribute to Chinese threat actors. However, in the December campaign, ransomware linked to TA505 is utilized, which complicates high-confidence attribution.
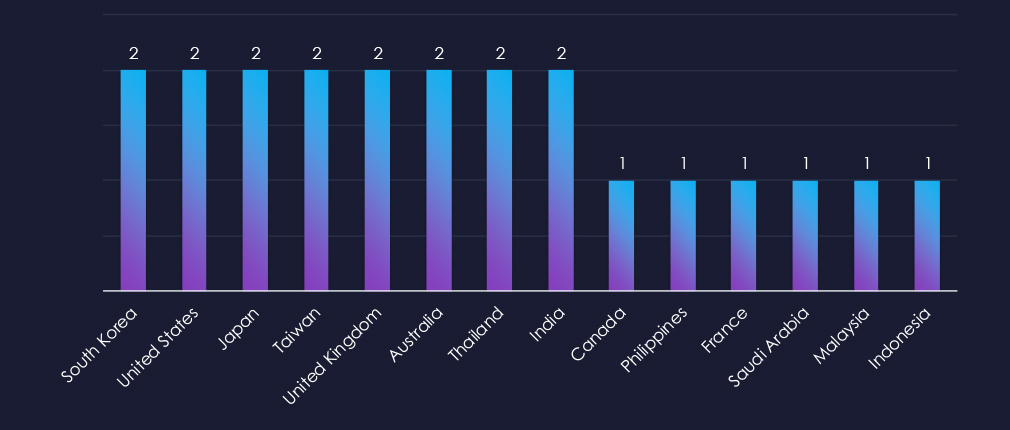
Victims of the observed attack campaigns recorded by the organization span 14 different countries. While there does not appear to be a discernible geographic pattern beyond economic size, this suggests opportunistic targeting and financial motivation rather than geopolitical considerations.
However, given the involvement of Chinese threat actors and victims within the Chinese Communist Party’s sphere of influence, it is plausible that geopolitical motivations also play a role.
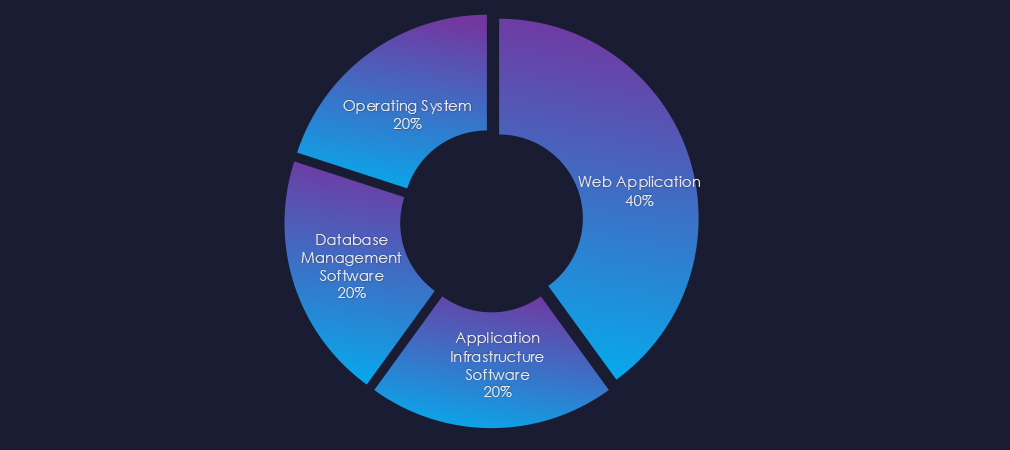
Both observed campaigns targeted web applications. In addition to the web applications, operating system, database management software, and application infrastructure software were also compromised during the December campaign.

In the past 90 days, financial organizations have been moderately affected by advanced persistent threat (APT) campaigns. Half of the observed APT campaigns targeted the finance industry, representing 2 out of 4 total campaigns.
This represents a significant decrease from the previous 90-day period when 13 out of 13 campaigns targeted the finance industry.
Monthly Trends
The observed campaigns exhibit intermittent patterns and alternate between months.
Key Threat Actors
Both campaigns are attributed to Chinese threat actors. However, the December campaign involved ransomware linked to Russian TA505.
Geographical Impact
The campaigns have affected a total of 14 countries, seemingly distributed randomly across continents. While financial motivations are suspected, some countries are also of interest to the Chinese Communist Party (CCP).
Targeted Technologies
Web applications remain the most frequently targeted technology. Additionally, database management and application infrastructure software have been compromised.
Over the past three months, CYFIRMA’s telemetry has identified 5,445 out of a total of 187,004 phishing campaigns targeting combined finance categories, representing a substantial decrease of -44.9% compared to the previous 90-day period.
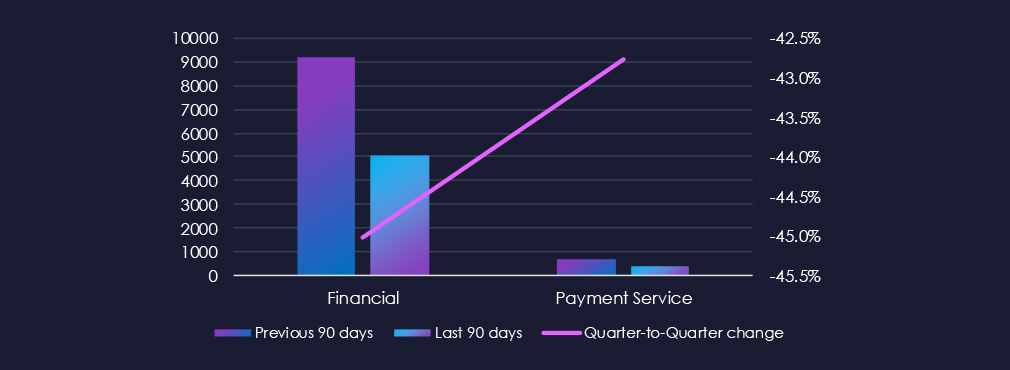
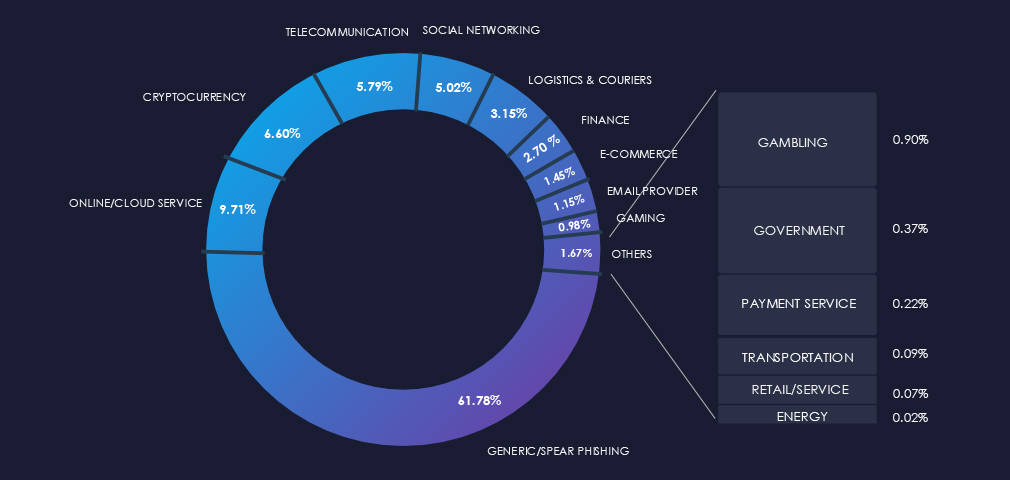
The chart below demonstrates the global distribution of observed themes. Finance and Payment Services account for 2.92% of all captured phishing attempts, representing a substantial reduction from their previous 90-day period share of 5.66%. Consequently, finance has been ranked as the sixth most frequent phishing theme.
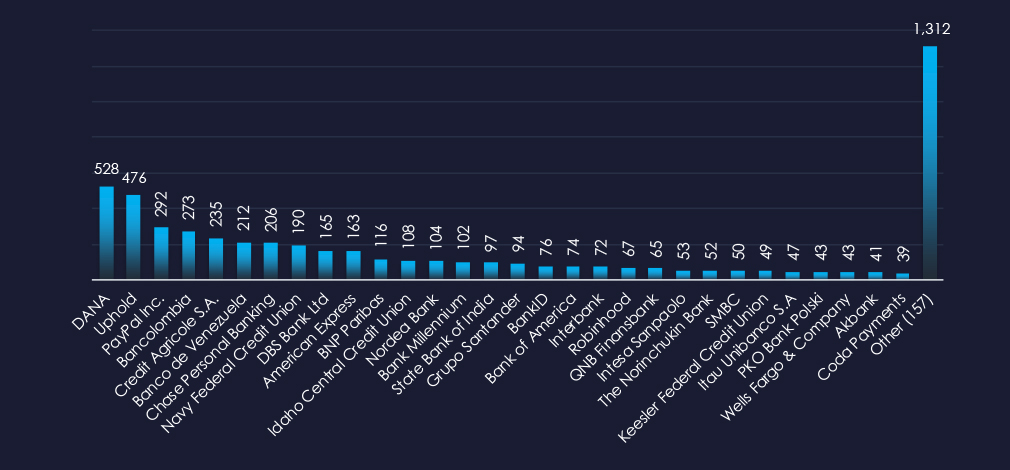
In total 187 financial organizations were impersonated in captured phishing attempts during the last 90 days. The Top victims are financial platforms DANA, Uphold, and PayPal, followed by Bancolombia, Credit Agricole, and Bank of Venezuela.
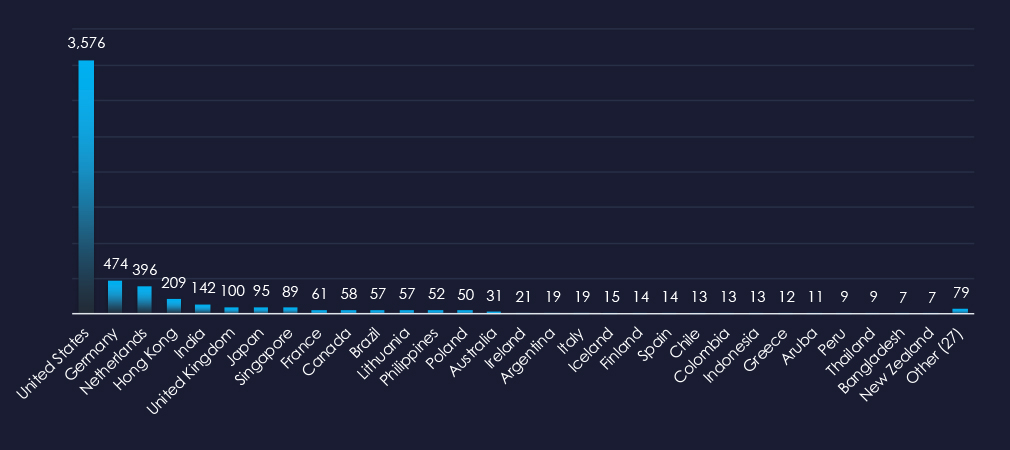
The US is a leading source of financially themed phishing, despite collectively non-US organizations being more frequently impersonated. In total 57 countries were observed as sources of relevant phishing.

The finance sector continues to be a prominent phishing target due to the direct monetization opportunities it presents for threat actors. However, the total volume of phishing attacks captured has decreased by -44.9%, and the corresponding share of financial-related phishing has decreased from 5.66% to 2.92%. This decline is primarily attributed to the increasing prevalence of unique and uncategorized Generic/Spear Phishing attacks.
Financial platforms such as DANA, Uphold, and PayPal are among the top three impersonated brands, followed by Colombian, French, and Venezuelan banks.
In total our platform recorded 187 organizations from 57 countries, including notable entities like the Commonwealth Bank of Australia (AU), State Bank of India (IN), and DBS Bank (Singapore), which collectively demonstrate the global nature of these threats.
Data originating from ASN reveals that the United States remains the leading source of phishing emails impersonating financial organizations, despite the fact that most impersonations originate from non-U.S. sources. This observation is likely attributed to the substantial number of compromised devices utilized in botnets to disseminate phishing emails. Significant activity has also been detected in the Netherlands, and Germany for similar reasons.
India ranks as the fifth most frequent target of phishing attacks. Additionally, Hong Kong and Singapore are frequently utilized by Chinese cyber criminals as proxies. Southeast Asia and Latin America are experiencing steady growth as both sources and targets of global finance-themed phishing campaigns.
The presence of phishing campaigns in both developed and developing nations underscores the opportunistic nature of these attacks and their global reach. Regional variations suggest more sophisticated attacks in high-population countries, while lesser-known regions such as Uzbekistan or Mozambique demonstrate expanding attacker capabilities.
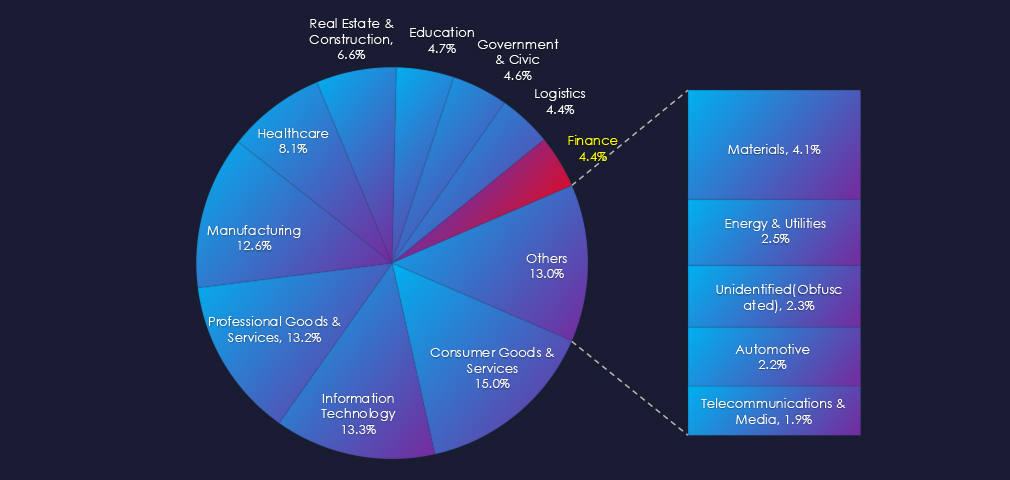
In the past 90 days, CYFIRMA has identified 79 verified ransomware victims in the finance industry. This accounts for 4.4% of the overall total of 1,812 ransomware victims during the same period. Placing the finance industry as the 10th most frequent victim of ransomware.
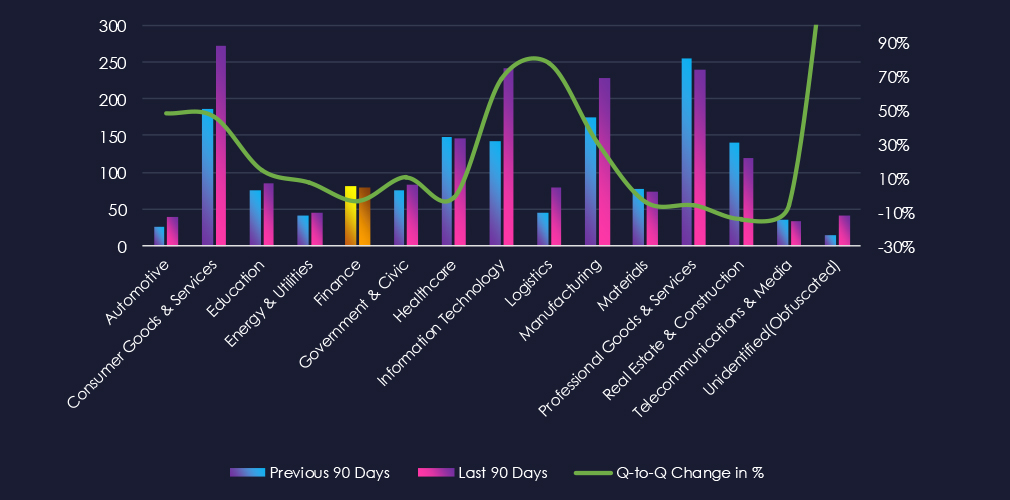
Furthermore, a quarterly comparison reveals sustained interest in the Finance industry, with only a marginal decrease from 82 to 79 victims. The overall share remains between 5.00% and 4.65%.
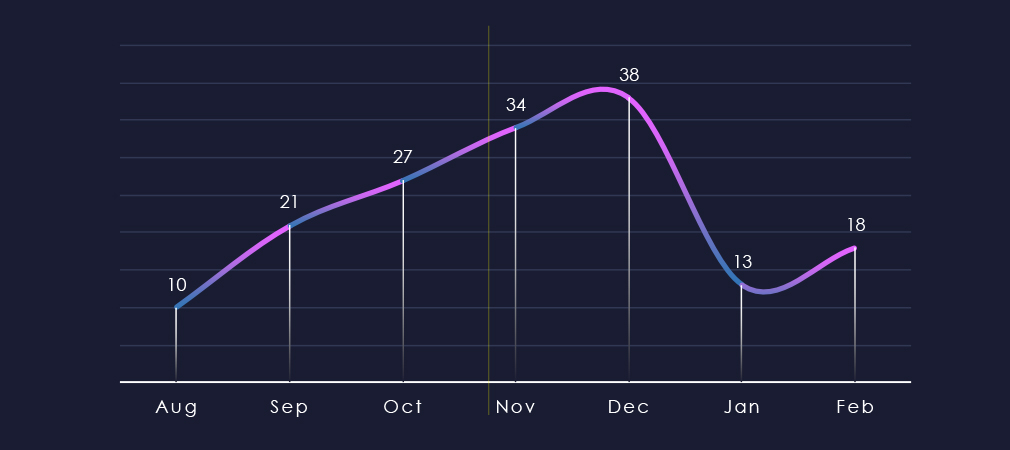
Over the past 180 days, and considering just one week of August, we have observed a consistent and gradual increase in victims month-over-month, culminating in December. Beginning from the last week of November, within the last 90 days, we have only experienced a minimal rebound from the decline observed during the holiday season in the finance industry.
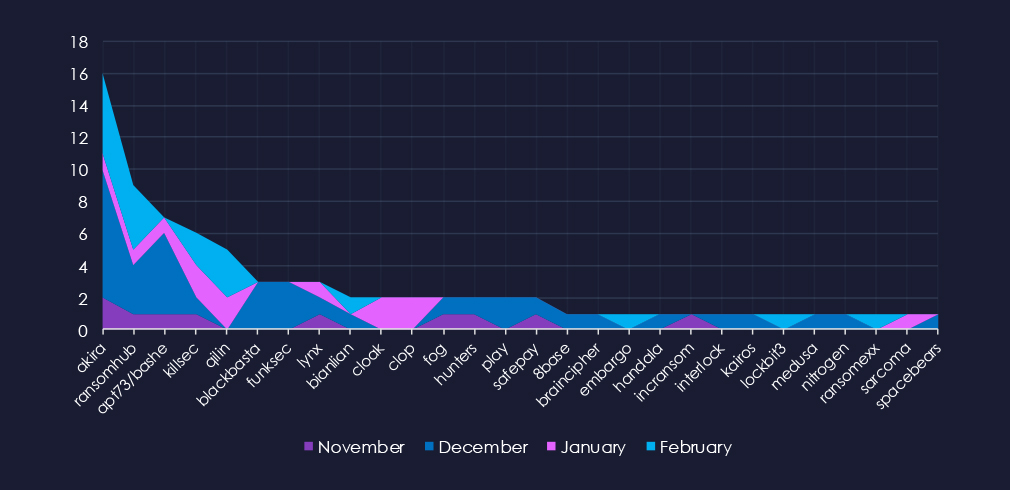
A breakdown of the monthly activity provides insights into which gangs were active each month. For example, Akira, APT73/Bashe, Blackbasta, and Killsec were most active in December, Cloak and Cl0p during January, and Qilin in February.
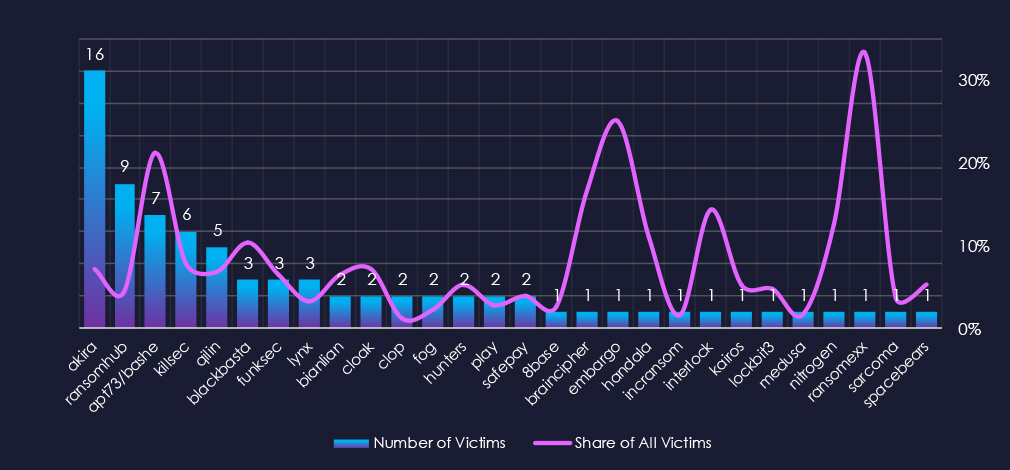
In total 28 out of 61 gangs were active in the last 90 days. Akira gang recorded the most victims (16) by a significant margin, followed by RansomHub (9), APT73/Bashe (7), Killsec (6), and Qilin (5).
APT73/Bashe has the highest share of victims in the Finance industry (21.21%) among the more active groups, followed by Blackbasta (10.34%), Killsec (7.89%), and Akira (7.08%), suggesting a high focus on this industry.
From less active gangs, Ransomexx recorded 1 in 3 victims (33%) in the Finance industry, followed by Embargo with 1 in 4 (25%), Brainchipher 1 in 6 (16.67%), Interlock 1 in 7 (14.29%).
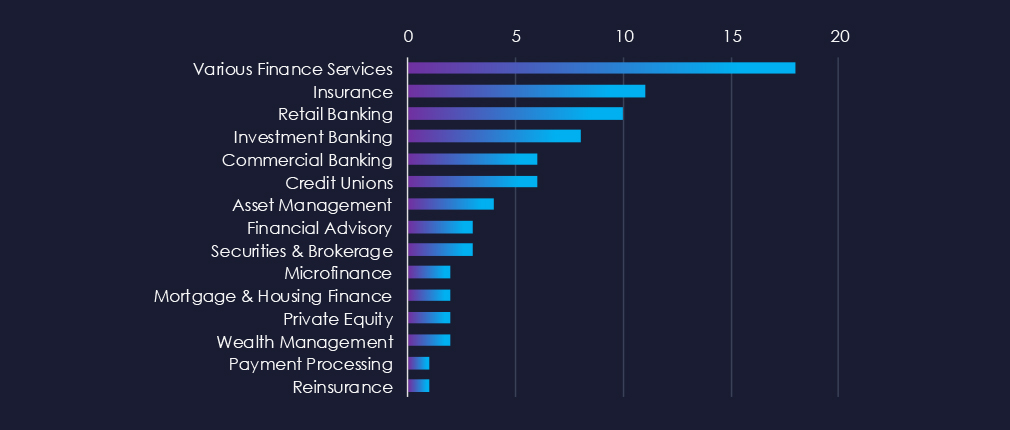
Insurance, Retail, Investment, and Commercial Banking are the most frequent victims of ransomware in the Finance industry. Various Finance Services include many services ranging from Escrow & Title services to Estate Planning and Pawn & Collateral lending.
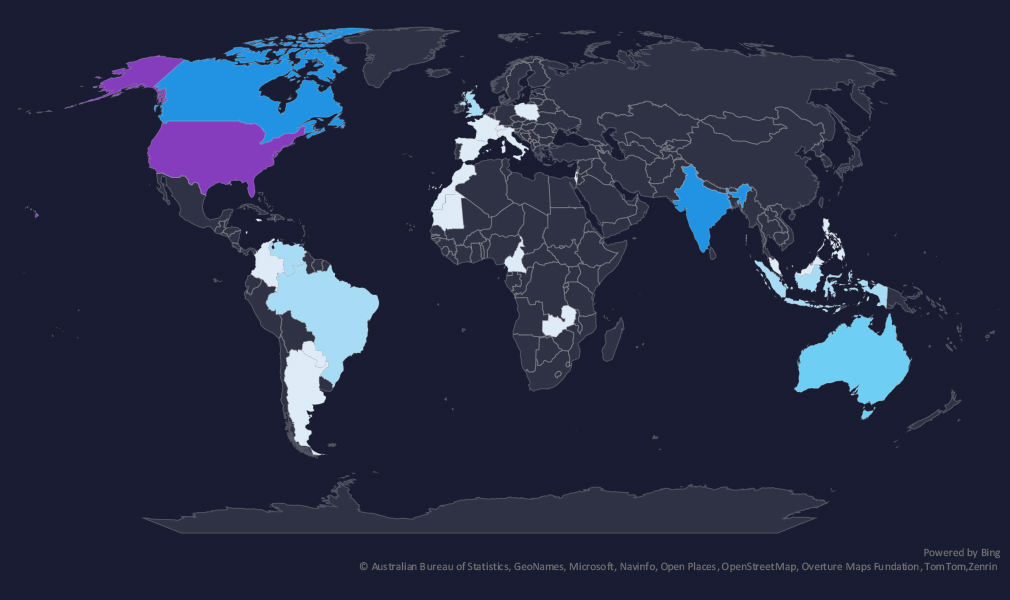
The geographic distribution heatmap underscores the widespread impact of ransomware, highlighting the countries where victims in this industry have been recorded. Notable is its growing presence in Latin America and Africa.
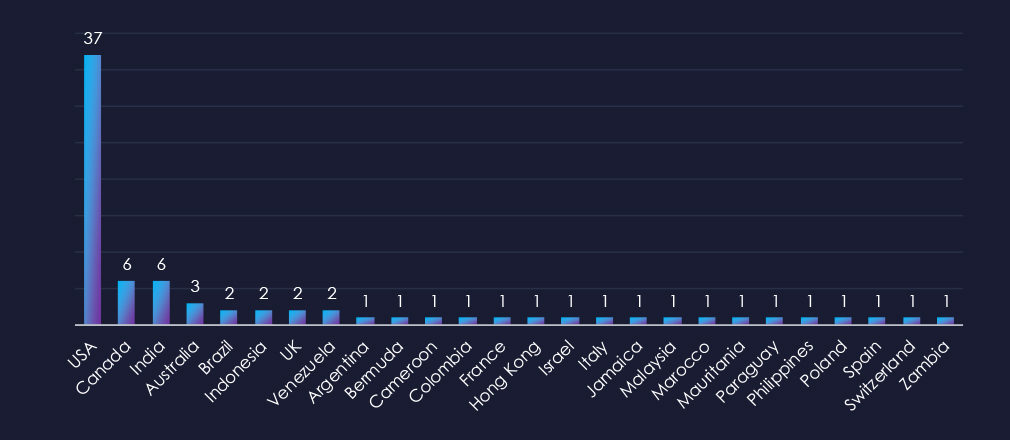
In total 26 countries recorded ransomware victims with the US alone accounting for ~47% of all victims with identified geography.

The finance industry is placed as the 10th most frequent victim. It faces a sustained ransomware threat with only a marginal decrease quarter-to-quarter. Attacks affected a wide range of sub-sectors and a broad geographic distribution.
Monthly Activity Trends
Ransomware activity in the finance industry grew steadily from August to December and then sharply fell off with only a mild recovery.
Akira was the most active overall followed by RansomHub, APT73/Bashe, and Killsec.
Ransomware Gangs
A total of 28 out of 61 active ransomware groups targeted the finance industry in the past 90 days:
Akira: The most active with 16 victims and 7% of their victims are from the finance industry (16 out of 226 victims).
APT73/Bashe: The highest share of 21.2% of victims were from the finance industry (7 out of 33 victims).
The relatively even distribution among a relatively high number of groups indicates no single gang currently dominates the ransomware landscape in the finance sector. Akira is leading due to overall high activity.
Geographic Distribution
The geographic distribution of ransomware victims in the finance industry reflects the industry’s global nature and the widespread reach of these attacks. Notable is its high presence in Latin America, and Southeast Asia and growing activity in Africa.
47% of all victims with identified geography are located in the US.
In total, 26 countries recorded ransomware victims in the finance industry.
For a comprehensive, up-to-date global ransomware tracking report, please refer to our new monthly “Tracking Ransomware” series here.
Over the past 90 days, financial organizations faced moderate cyber risks across monitored categories.
APT Campaigns (Moderate): Half of the observed campaigns (2 out of 4) targeted the finance sector—a significant drop from 13 out of 13 in the previous period. Chinese threat actors were predominant, with one December incident linked to the Russian group TA505. Attacks affected 14 countries, focusing primarily on web applications, database management, and application infrastructure software.
Phishing (Moderate): The finance sector remains a prime target for monetization, though overall phishing volume fell by nearly 45%, and finance-focused phishing declined from 5.66% to 2.92%. Platforms such as DANA, Uphold, and PayPal were most impersonated, alongside banks in Colombia, France, and Venezuela. The U.S. led as the top source of phishing emails, with the Netherlands, Germany, Southeast Asia, and Latin America also significant. India ranked fifth as a target. These attacks reflect a globally opportunistic threat landscape that spans developed and emerging markets.
Ransomware (Moderate): Ranked as the 10th most frequent victim, finance faces persistent ransomware threats across diverse sub-sectors with only a marginal decrease in quarter-to-quarter activity. Activity grew steadily from August to December before tapering off. Of 61 active ransomware groups, 28 targeted finance. Akira led in total victims, while APT73/Bashe had the highest percentage of finance victims. The U.S. accounted for 47% of identified cases, with notable activity in Latin America, Southeast Asia, and an emerging presence in Africa, totaling 26 affected countries overall.