



The CYFIRMA Industry Report delivers original cybersecurity insights and telemetry-driven statistics of global industries, covering one sector each week for a quarter. This report focuses on the Healthcare industry, presenting key trends and statistics in an engaging infographic format.
Welcome to the CYFIRMA infographic industry report, where we delve into the external threat landscape of the Healthcare industry over the past three months. This report provides valuable insights and data-driven statistics, delivering a concise analysis of attack campaigns, phishing telemetry, and ransomware incidents targeting the healthcare industry.
We aim to present an industry-specific overview in a convenient, engaging, and informative format. Leveraging our cutting-edge platform telemetry and the expertise of our analysts, we bring you actionable intelligence to stay ahead in the cybersecurity landscape.
CYFIRMA provides cyber threat intelligence and external threat landscape management platforms, DeCYFIR and DeTCT, which utilize artificial intelligence and machine learning to ingest and process relevant data, complemented by manual CTI research.
For the purpose of these reports, we leverage the following data from our platform. These are data processed by AI and ML automation based on both human research input and automated ingestions.
While this report contains statistics and graphs generated primarily by automation, it undergoes thorough review and enhancement for additional context by CYFIRMA CTI analysts to ensure the highest quality and provide valuable insights.
Healthcare organizations did not feature in any of the 6 observed campaigns, which is a presence in 0% of all campaigns, adrop from 1 in 9 campaigns and 11% presence in the previous 90-day period.
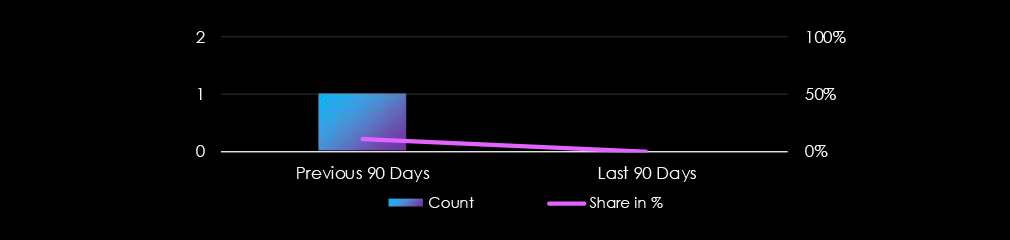
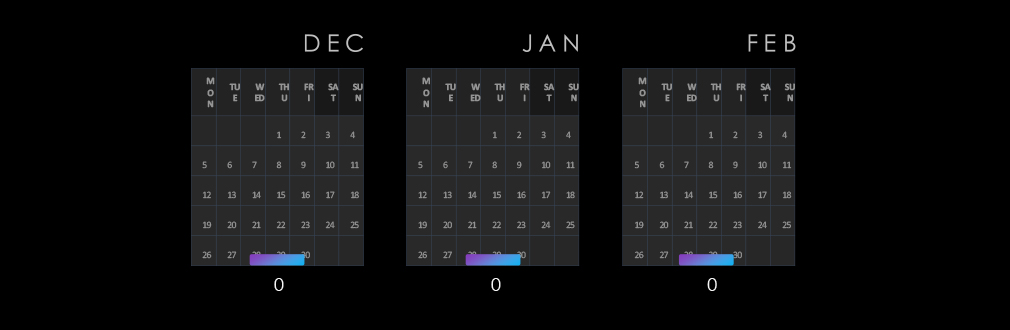
Observed campaigns are distributed intermittently and alternate between months.
In the past 90 days, healthcare organizations have not been significantly affected by advanced persistent threat (APT) campaigns.
The industry was not present in any of the observed campaigns.
Healthcare does not appear to be on the radar of latest APT groups. When it comes to nation-sponsored groups there are more pressing issues in relation to global tensions, including escalating trade war, tariffs, chipmaking race and of course hot armed conflicts.
Financially motivated threat actors largely avoid healthcare as it attracts unwanted attention. Historically Russian and North Korean groups did not shy away, but in the last 90 days, none of these groups appeared to attack healthcare organizations.
North Korea just recently got away with over a billion dollars from a crypto exchange heist.
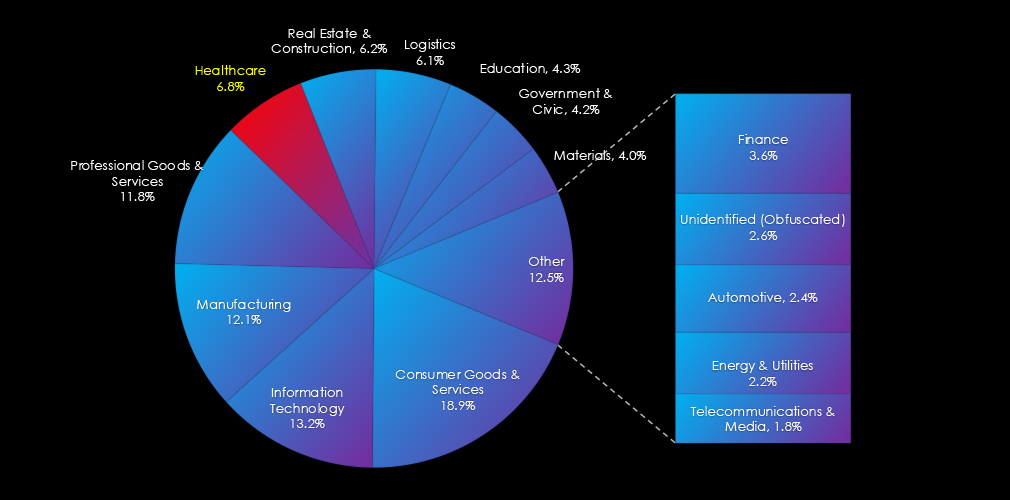
Over the past three months, CYFIRMA’s telemetry has identified 2,336 mentions of healthcare out of a total of 48,368 industry mentions. This is from a total of 652,369 posts across various underground and dark web channels and forums.
Healthcare ranked as the 8th most frequently mentioned industry in the last 90 days with a share of 4.8% of all detected industry chatter.
Below is a breakdown of 30-day periods of all mentions.
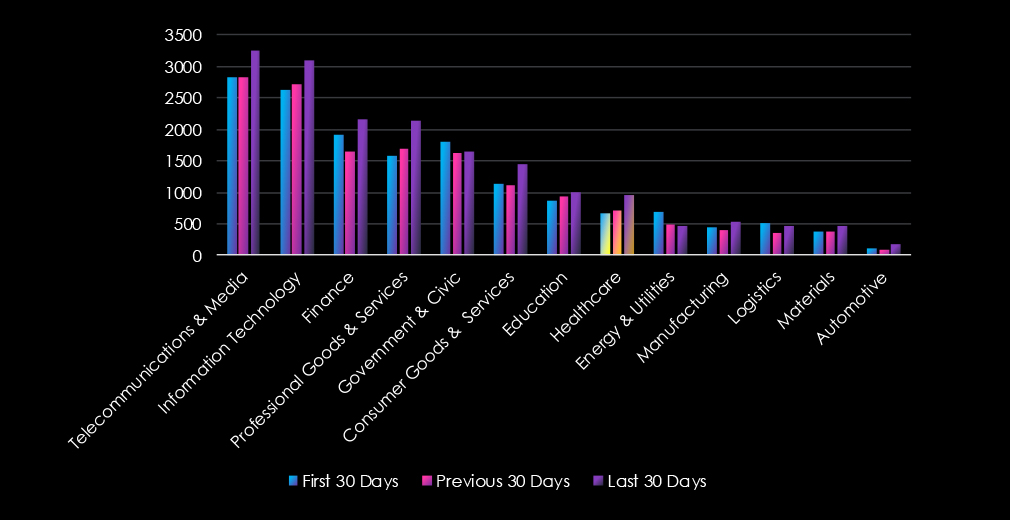
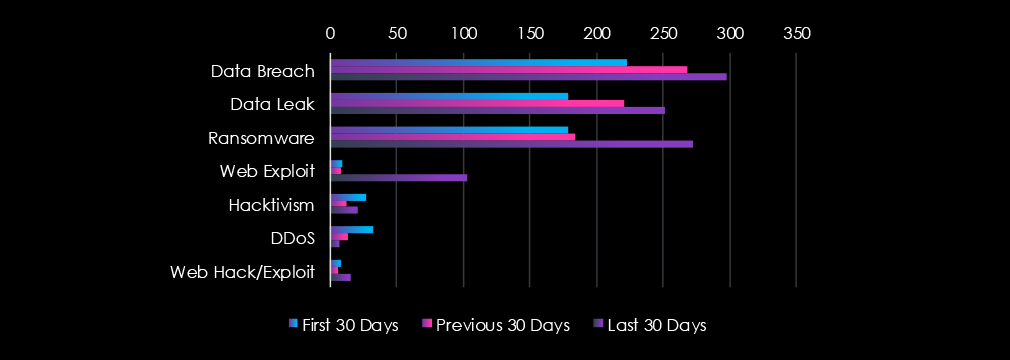
Data Breaks, Data Leaks, and Ransomware were the top 3 categories of recorded chatter for the healthcare industry. Notable is also a gradual increase over three 30-day period.
In total, healthcare comprises of 4.8% of all detected industry underground and dark web chatter in the last 90 days. It ranked as the 8th most frequently mentioned industry.
Below are observed key trends across 90 days.
Surge in Mentions (+47%)
657 (Dec) → 712 (Jan) → 967 (Feb)
Rising cyber threat discussions targeting healthcare.
Top Threats (February 2025)
Data Breach: 298 (+34%)
Ransomware: 272 (+52%)
Data Leak: 251 (+40%)
DDoS Attacks Declining
32 (Dec) → 7 (Feb)
Hacktivism Fluctuates
27 (Dec) → 12 (Jan) → 21 (Feb)
Over the past three months, CYFIRMA’s telemetry has identified 81 mentions of healthcare out of a total of 4,435 industry mentions. This is from a total of 10,409 CVEs published in 90 days.
Healthcare ranked as the 10th most frequently mentioned industry in the last 90 days with a share of 1.8% of all detected industry chatter.
Below is a breakdown of 30-day periods of all mentions.
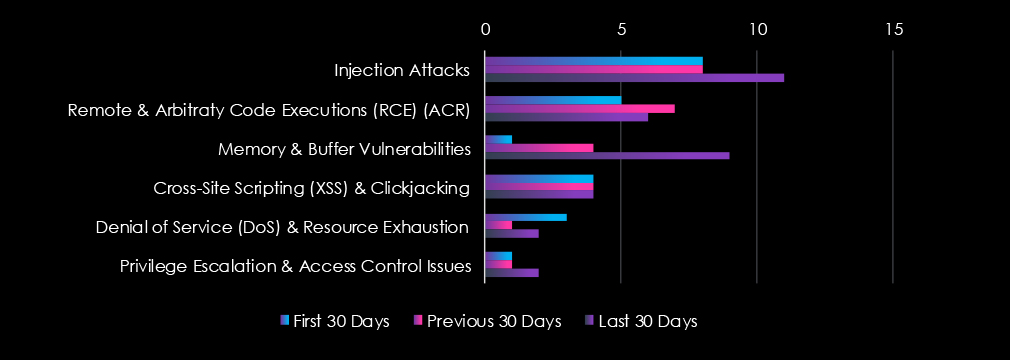
Injection Attacks, Remote & Arbitrary Code Execution, and Memory & Buffer overflow were the top 3 vulnerabilities mentioned in the context of the healthcare industry.
In total, healthcare comprises 1.8% of all detected industry vulnerabilities in the last 90 days and is ranked as the 10th most frequently mentioned industry.
Below are observed key trends across 90 days.
Steady Increase in Reported CVEs (+55%)
22 (Dec) → 25 (Jan) → 34 (Feb)
Consistent growth in vulnerabilities affecting healthcare.
Top Vulnerability Types (March 2025)
Injection Attacks: 11 (+38%)
Memory & Buffer Vulnerabilities: 9 (+800%)
Remote Code Execution (RCE): 6 (-14%)
Notable Growth in Memory & Buffer Vulnerabilities
1 (Dec) → 4 (Jan) → 9 (Feb)
Cross-Site Scripting (XSS) & Clickjacking Remains Constant
4 mentions every month → Persistent web security risks.
DDoS & Privilege Escalation Are Low but Present
DDoS: 3 (Dec) → 1 (Jan) → 2 (Feb)
Privilege Escalation: 1 (Dec) → 1 (Jan) → 2 (Feb)
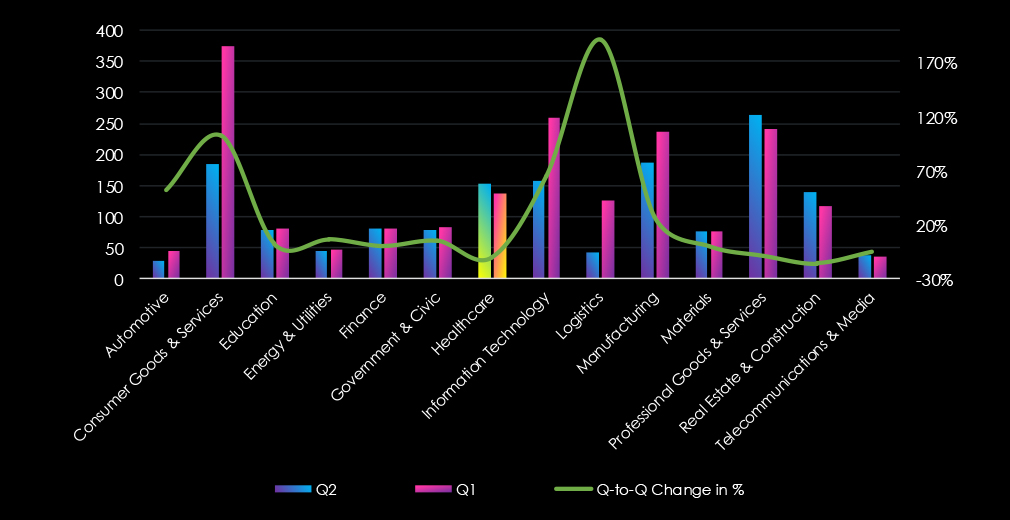
In the past 90 days, CYFIRMA has identified 135 verified ransomware victims in healthcare industry. This accounts for 6.8% of the overall total of 1,995 ransomware victims during the same period, placing the healthcare industry as 5th most frequent victim of ransomware.
Furthermore, a quarterly comparison reveals sustained interest in the healthcare industry, yet with a notable decrease of 10.4% from 154 to 138 victims. The overall share mildly declined from 9.6% to 6.8%.
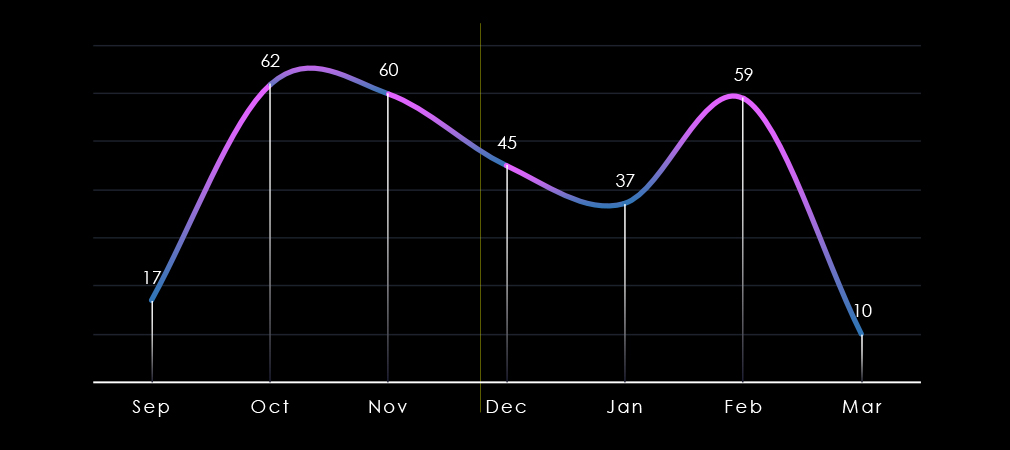
Over the past 180 days, we have observed a swinging numbers of victims month-over-month, peaking in October and then again in February.
We can attribute the December to January dip to an overall slump in ransomware activity. Activity rebounded to a similar high in February. September and March are partial months.
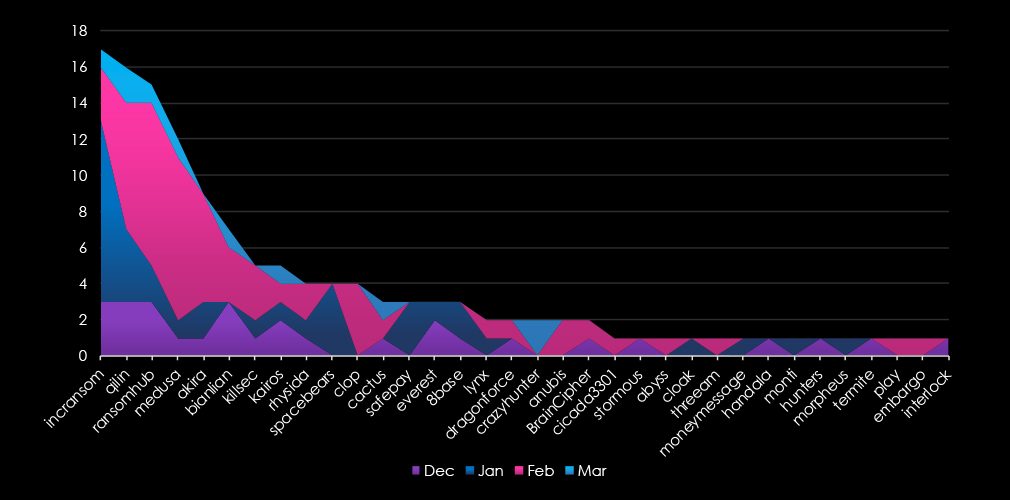
A breakdown of the monthly activity provides insights into which gangs were active each month. For example, the most active gang IncRansom has recorded the most victims in January and was very active across all months. On other hand Medusa recorded most victims in February and was barely active in the other months.
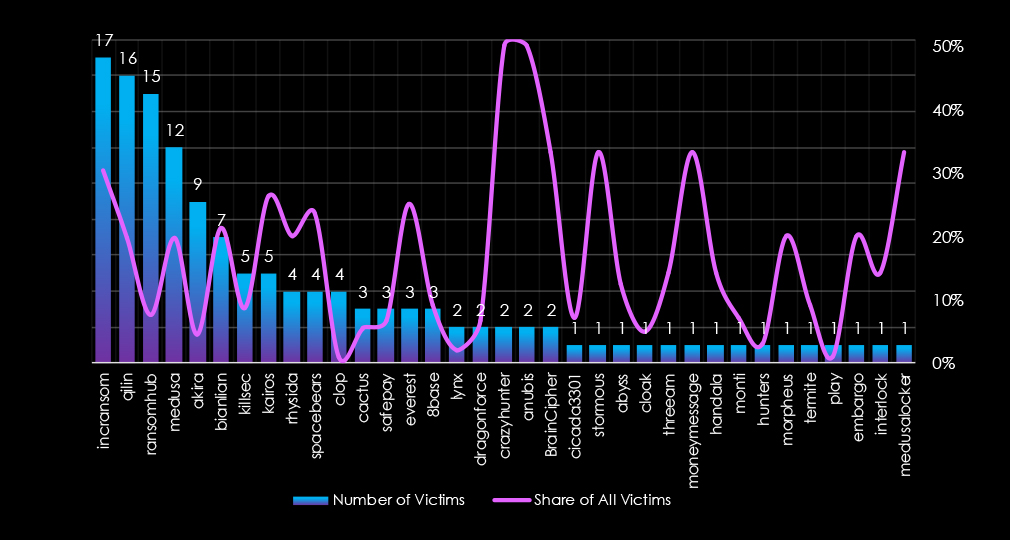
In total 35 out of 62 gangs were active in the last 90 days. IncRansom gang recorded the most victims (17), followed by Qilin (16), and RansomHub (15).
Disturbingly, the share of all victims for many gangs in this industry is very high, IncRansom 30.4%, Qilin 19.8%, and Medusa 19.7%, suggesting healthcare is their focus.
Out of the top 10 gangs only four have less than single-digit percentage. Other six gangs show very high focus on the vulnerable healthcare industry.
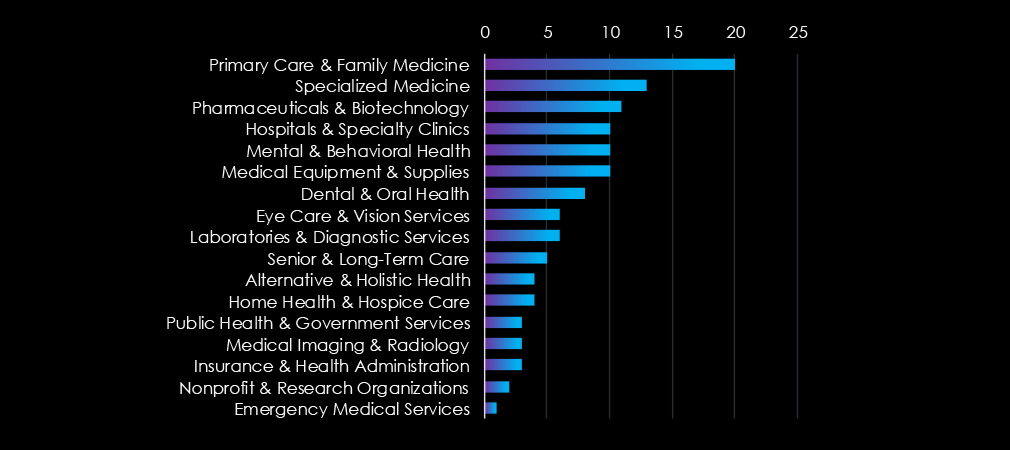
Primary Care & Family Medicine, Specialized Medicine, and Pharmaceuticals & Biotechnology are the most frequent ransomware victims in healthcare.
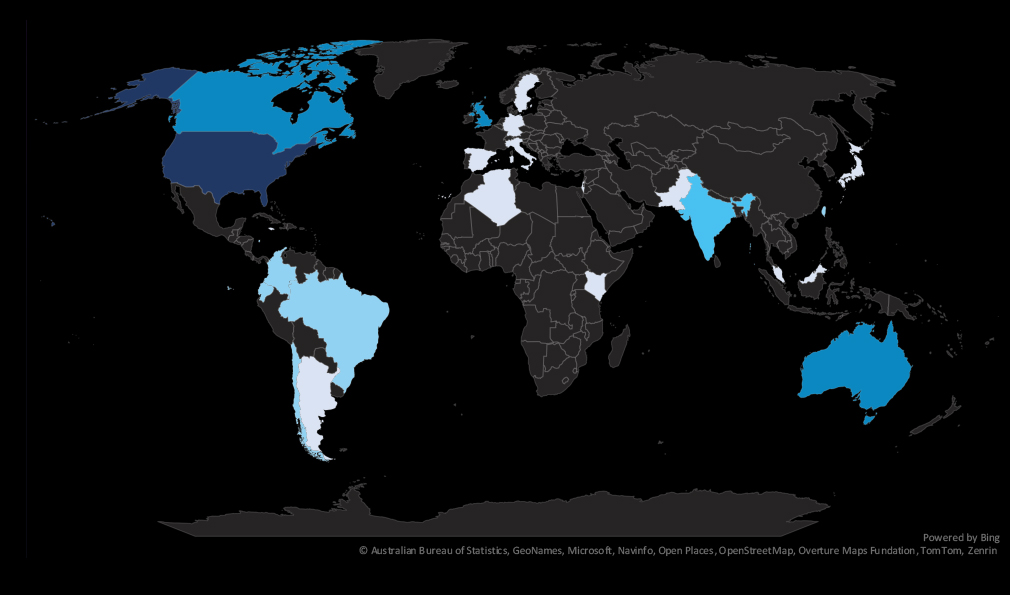
The geographic distribution heatmap underscores the widespread impact of ransomware, highlighting the countries where victims in this industry have been recorded. Notable is the growing presence in Latin America and India.
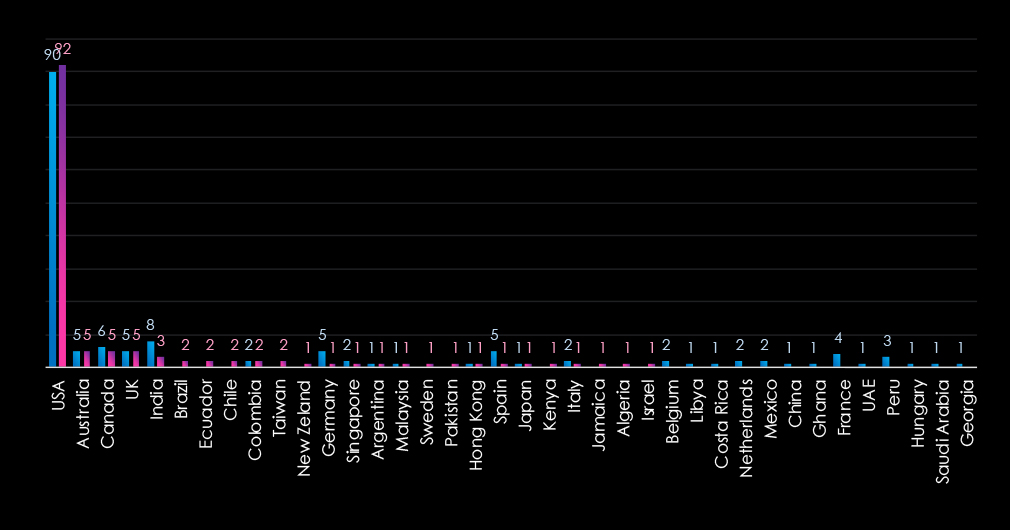
The chart shows quarter-to-quarter changes in targeted countries. Data is sorted by last 90 days and compared to the previous 90 days marked blue.
We can see the USA dominating the healthcare ransomware victimology due to the for-profit nature of the industry in the USA.
The healthcare industry is placed as the 5th most frequent victim. It faces a sustained ransomware threat yet with notable decrease of -10.4% quarter-to-quarter. Overall share also dropped from 9.6% to 6.8% of all ransomware victims.
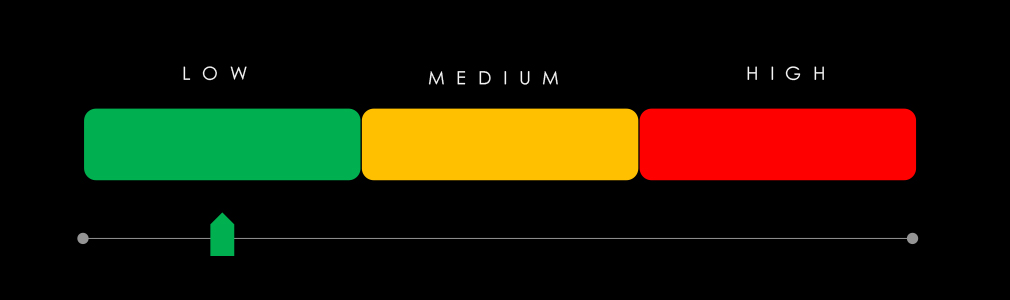
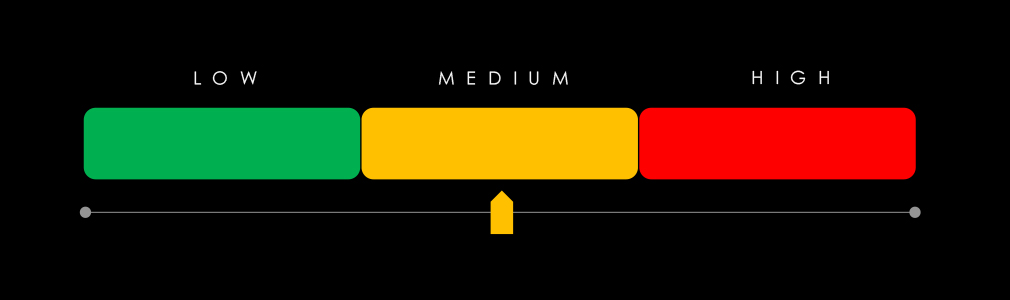
Most countries are facing low to moderate risk with the exception of the USA, where the risk factor is high.
Monthly Activity Trends
Ransomware activity in the healthcare industry swung between months recording spikes in October and February.
IncRansom was the most active overall followed by Qilin and RansomHub.
Ransomware Gangs
A total of 35 out of 62 active ransomware groups targeted this industry in the past 90 days:
IncRansom: The most active with 17 victims and 30.4% of their victims are from the healthcare sectors (17 out of 56 victims).
RansomhubThird most active with a share of only 7.6% of the victims in this industry (15 out of 197 victims), presenting a risk due to high activity.
Overall, 6 out of the top 10 gangs recorded a 19%+ share of their victims in healthcare, implying a high focus.
Geographic Distribution
The geographic distribution of ransomware victims in the healthcare industry is completely dominated by the USA (92) accounting for 68% of all victims. Australia, Canada, and the UK shared the second place with 5 victims each.
In total, 25 countries recorded ransomware victims in this industry in last 90 days, which is a small decrease from 27 countries in the previous 90 days.
For a comprehensive, up-to-date global ransomware tracking report, please refer to our new monthly “Tracking Ransomware” series here.
Over the past 90 days, healthcare organizations faced low risk from APT Campaigns, with none of the observed nation-state attacks affecting the sector. This shift indicates that threat actors—both financially motivated and state-sponsored—are currently focusing on other industries linked to ongoing geopolitical tensions and broader economic targets.
However, Underground & Dark Web Chatter and Vulnerabilities showed a notable uptick. Healthcare accounted for 4.8% of industry-related chatter, ranking as the 8th most frequently mentioned sector. Discussions around data breaches, ransomware, and data leaks increased significantly, pointing to a sustained interest in targeting healthcare for potential financial gain or data exploitation.
Meanwhile, new vulnerabilities grew by 55% from December to February, with a marked rise in memory and buffer flaws. Although overall numbers remain modest.
Despite the overall decline in healthcare’s share of Ransomware attacks—down from 9.6% to 6.8%—the industry remains the 5th most frequent victim.
Ransomware activity spiked notably in October and February, with 35 out of 62 active groups targeting healthcare. IncRansom was especially active, devoting 30.4% of its attacks to this sector.
The United States stands out as a high-risk country, accounting for 68% of all healthcare ransomware victims.