



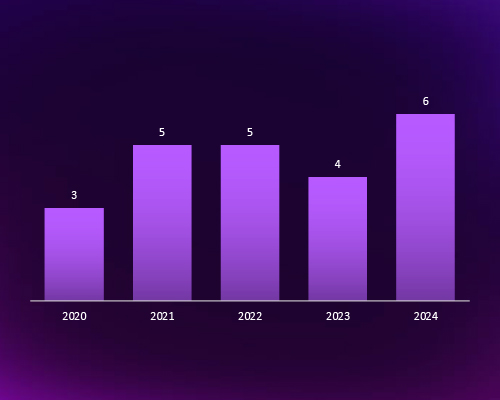
CYFIRMA observed a rising trend in cyber threat campaigns targeting Indonesia, with a peak in 2024. This escalation highlights Indonesia’s growing geopolitical and economic significance, making it a prime target for both financially motivated and state-sponsored cyber actors. The fluctuations in attack campaigns suggest evolving adversary tactics, requiring proactive intelligence-driven defenses to mitigate emerging threats.
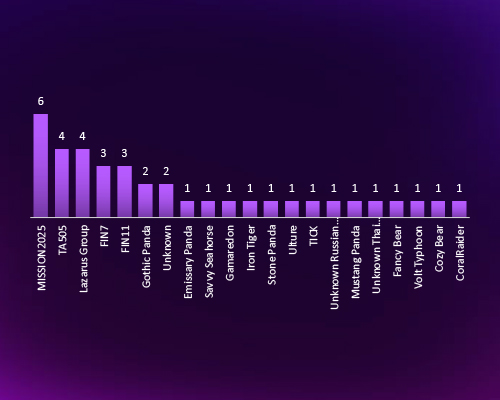
CYFIRMA’s intelligence reveals a diverse set of cyber threat actors targeting Indonesia, including state-sponsored APTs (Lazarus Group, Gothic Panda, Fancy Bear) and financially motivated groups (TA505, FIN7, FIN11). The presence of Chinese, Russian, and North Korean-linked actors suggests a mix of espionage, financial crime, and strategic cyber operations. The dominance of MISSION2025 signals a sustained, structured campaign requiring heightened vigilance.
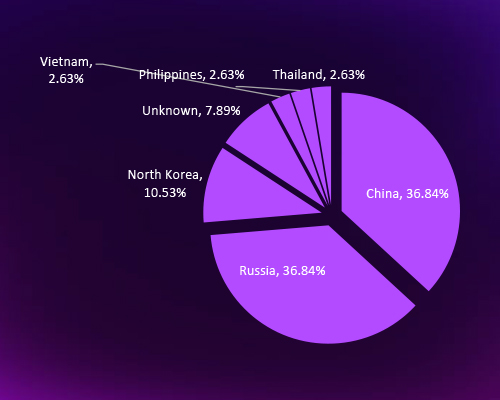
CYFIRMA’s analysis highlights that threat actors targeting Indonesia originate from diverse geopolitical landscapes, with two dominant sources each contributing 36.84% of observed campaigns. This indicates a mix of state-sponsored cyber espionage and financially motivated operations, leveraging Indonesia’s strategic position in the Indo-Pacific. The distribution of smaller threat actor clusters suggests a dynamic and evolving cyber threat environment.
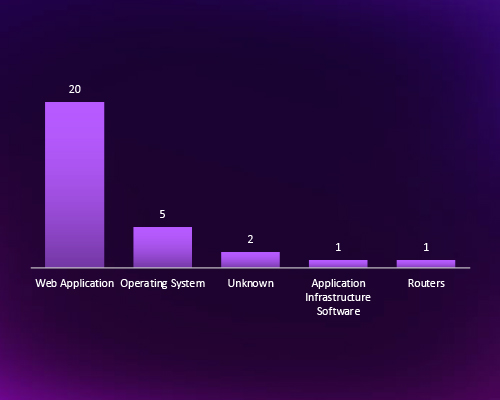
In the CYFIRMA observed campaigns web applications are the primary target for cyber threat actors, accounting for the vast majority of attacks. This highlights a critical exposure in Indonesia’s digital infrastructure, especially across finance, e-commerce, and government services. Operating systems and routers also remain key entry points, reinforcing the need for robust patching, secure configurations, and zero-trust architecture.
CYFIRMA’s telemetry shows widespread use of commodity and custom malware by threat actors targeting Indonesia, with prominent families like Emotet, Cl0p Ransomware, and Winnti observed. The mix of financial, espionage, and infrastructure-targeting malware highlights the multi-motive nature of attacks. The presence of tools like Cobalt Strike and FlawedAmmy RAT signals advanced post-exploitation activity.

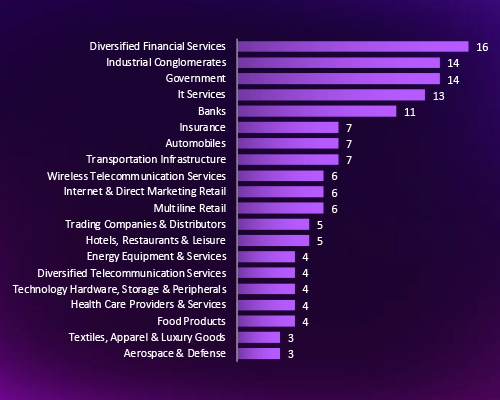
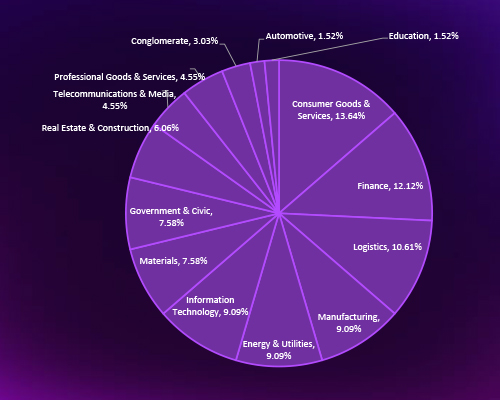
CYFIRMA’s analysis highlights that Financial Services, Industrial Conglomerates, Government, and IT Services are the most frequently targeted sectors in Indonesia, signaling adversaries’ focus on high-value, high-interconnectivity industries. The spread of attacks across critical infrastructure, energy, and defense highlights broad exposure across both economic and national security domains.
Year-to-Year Elevation: High
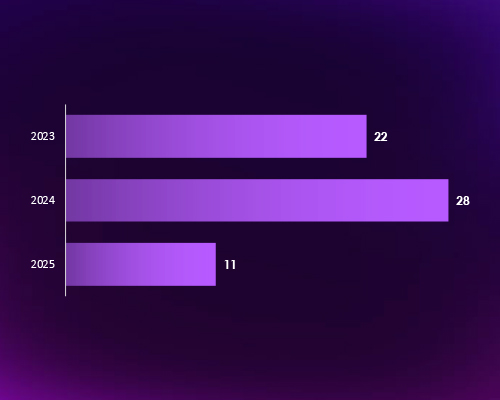
In 2023, CYFIRMA recorded 4,723 verified ransomware victims, while in 2024, the number increased to 5,123, representing an 8.5% year-over-year growth across all industries.

CYFIRMA’s analysis reveals that ransomware attacks in Indonesia are sector-agnostic but economically motivated, with the Consumer Goods, Finance, and Logistics sectors among the most targeted. Critical industries such as Energy, IT, and Manufacturing also face sustained attacks, indicating adversaries’ focus on sectors with high operational disruption impact. The targeting of government and civic sectors further highlights a strategic shift toward national infrastructure and public trust erosion.
In early 2023, the takedown of Hive caused a temporary slowdown in ransomware activity. However, this was followed by a surge driven by Cl0p, leveraging the MOVEit vulnerability.
Similarly, the early 2024 slowdown caused by the LockBit3 takedown was short-lived, as affiliates switched to other Ransomware-as-a-Service (RaaS) and RansomHub quickly emerged to fill the void in the RaaS ecosystem.
As of March 2025, 11 incidents have already been recorded — a concerning figure when viewed in the context of quarterly trends. This early activity indicates that 2025 is on track to mirror or exceed previous years if this trajectory continues.
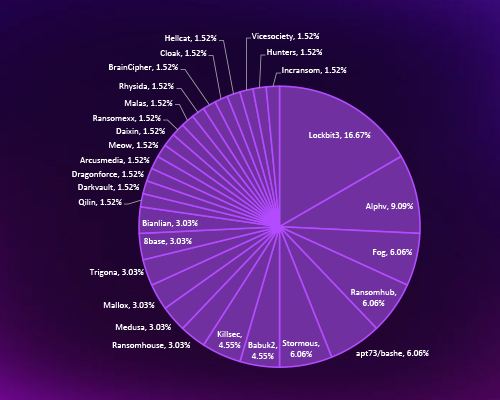
CYFIRMA’s assessment highlights that LockBit3, Alphv, and emerging groups like RansomHub are the most active ransomware operators targeting Indonesia. The presence of multiple small and mid-sized groups reflects a fragmented yet persistent threat landscape, fueled by the Ransomware-as-a-Service (RaaS) ecosystem. This diversification increases the complexity of defense.
Surge in Targeted Ransomware Attacks
Ransomware attacks are increasingly targeting key Indonesian industries, including finance, manufacturing, and government sectors — fueled by the rise of Ransomware-as-a-Service (RaaS) and affiliate diversification.
State-Backed Cyber Espionage Operations
Persistent cyber espionage activities were observed, primarily from China, North Korea, and Russia-linked groups, focusing on geopolitical intelligence, defense, and critical infrastructure sectors.
Growing Threat to Digital Supply Chains
Adversaries are exploiting third-party vendors, IT service providers, and open-source software used by Indonesian organizations, creating indirect attack paths.
Targeting of Critical Infrastructure & National Assets
Increased focus on energy, transportation, and civic sectors, indicates an adversarial shift towards nation-state-level disruption and destabilization campaigns.
Weaponization of Commodity Malware and Tools
Widespread use of off-the-shelf malware (e.g., Emotet, Cobalt Strike) and living-off-the-land techniques to bypass traditional defenses and maintain stealth.
Phishing & Credential Theft Surge
High-volume phishing campaigns and credential harvesting are targeting both citizens and corporate employees, exploiting Indonesia’s large digital population and low cyber hygiene levels.
Emergence of Data Leak Markets
The surge in data breaches and leaks of Indonesian citizen, financial, and government data on dark web marketplaces is increasing risks of fraud, identity theft, and cyber extortion.
Tactical Shift Post-Law Enforcement Actions
Ransomware and cybercrime groups adapt quickly to global crackdowns, rebranding and resurfacing under new names — indicating a resilient and evolving adversary ecosystem.