



Geopolitical Tensions
Cross-Strait Relations & Strategic Partnerships: Ongoing tensions with the People’s Republic of China foster persistent espionage efforts, while Taiwan’s alliances with major powers (e.g., the U.S.) further increase nation-state surveillance and interference.
Economic & Industrial Importance
High-Tech Manufacturing & Global Supply Chain Roles: Taiwan’s leadership in semiconductor and electronics production attracts industrial espionage, as compromising local firms can grant cybercriminals and foreign adversaries broader access to global partners and customers.
Intellectual Property (IP) Theft
Innovation & Advanced Processes: The country’s intensive R&D in semiconductors and electronics, combined with specialized manufacturing techniques, makes its trade secrets and IP especially valuable to threat actors seeking to shortcut innovation costs.
Financial Motivation
Wealthy Economy & Crypto/Fintech Growth: Taiwan’s robust financial sector and flourishing fintech industry provide lucrative targets for ransomware, fraud, and money laundering, especially in cryptocurrency-related platforms.
Strategic & Military Significance
Defense Infrastructure & Political Influence: Threat actors focus on stealing sensitive defense data or disrupting military operations; they also carry out influence campaigns designed to sway public opinion and undermine government stability.
Regional & Global Reach
Proximity & Technology Partnerships: Due to Taiwan’s central role in regional networks and international supply chains, compromising local entities can serve as a stepping stone to infiltrate multinational organizations and critical infrastructure worldwide.
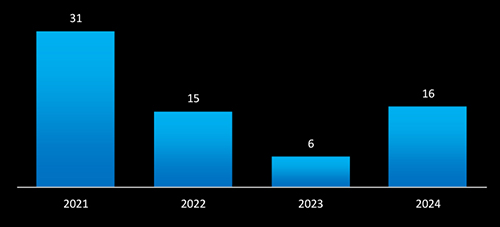
In 2024, campaigns targeting Taiwan have risen to 16 after a pause in the preceding two years, reflecting a renewed focus by threat actors. This resurgence highlights how quickly threat actors adapt to changing geopolitical and economic conditions.
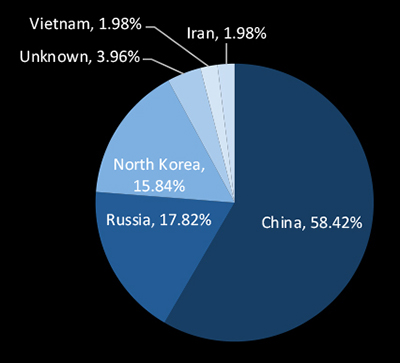
In the CYFIRMA-observed campaigns, China (58.42%), Russia (17.82%), and North Korea (15.84%) form the primary origins of threat actors targeting Taiwan. Chinese APT groups prioritize intellectual property theft and industrial espionage, leveraging stolen innovations to strengthen their global market positions. Russian actors typically focus on financially driven cybercrime and geopolitical disruption, while North Korean groups such as Lazarus pursue revenue-generating attacks to fund state objectives. This dominance of nation-state and highly organized groups underscores the strategic value of Taiwan’s industries especially semiconductors and advanced manufacturing.
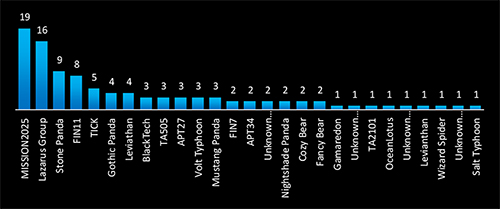
MISSION2025, Lazarus Group, Stone Panda, and FIN1 are the most active threat actors targeting Taiwan, with a mix of state-sponsored espionage and financially motivated cybercrime. The involvement of Chinese, North Korean, and Russian APT groups indicates a concerted effort to steal intellectual property, compromise supply chains, and disrupt critical operations.
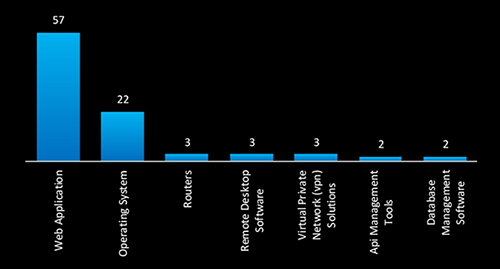
In the CYFIRMA-observed campaigns, web applications (57) and operating systems (22) remain the top attack surfaces, highlighting a persistent focus on web-facing vulnerabilities and system-level exploits. Simultaneous targeting of routers, VPN solutions, remote desktop software, and database management tools suggests deeper infiltration strategies aimed at compromising core infrastructure and credential-based access.
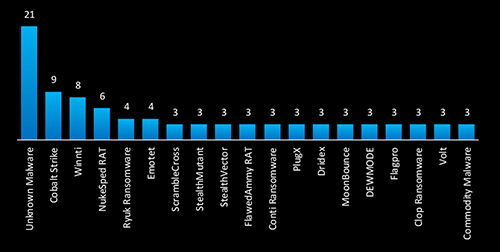
In the CYFIRMA-observed campaigns targeting Taiwan, unn known malware leads with 21 instances, indicating the use of custom or evolving threats to evade detection. The prominence of Cobalt Strike (9) suggests sophisticated adversaries leveraging offensive security frameworks for persistence and lateral movement. Winnti, NukeSpeed RAT, and Ryuk ransomware highlight a blend of state-sponsored espionage and financially motivated cybercrime, with likely involvement from Chinese and North Korean actors. Additionally, Emotet, ScrambleCross, and Conti ransomware reflect a mix of credential theft, botnet operations, and high-impact ransomware attacks. The presence of PlugX, MoonBounce, and FlawedAmmy RAT suggests a continued focus on long-term network infiltration.
Year-to-Year Elevation: High
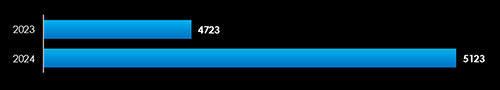
In 2023, CYFIRMA recorded 4,723 verified ransomware victims, while in 2024, the number increased to 5,123, representing an 8.5% year-over-year growth across all industries.
In early 2023, the takedown of Hive caused a temporary slowdown in ransomware activity. However, this was followed by a surge driven by Cl0p, leveraging the MOVEit vulnerability.
Similarly, the early 2024 slowdown caused by the LockBit3 takedown was short-lived, as affiliates switched to other Ransomware-as-a-Service (RaaS) and RansomHub quickly emerged to fill the void in the RaaS ecosystem.
Ransomware attacks against Taiwan remained persistent, with 26 victims in 2024, nearly matching 24 cases in 2023. This indicates that threat actors continue to target companies in Taiwan, leveraging ransomware for financial extortion, operational disruption, and data theft. Despite no significant decline, the consistent attack volume suggests an ongoing, well-orchestrated threat, likely fueled by Ransomware-as-a-Service (RaaS) operations and targeted supply chain compromises.

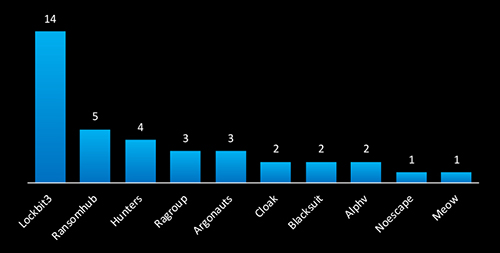
LockBit (14 victims) and RansomHub (5 victims) emerged as the most active ransomware gangs targeting Taiwan in 2024, followed by Hunters, Ragroup, and Argonauts. The presence of established RaaS operations like LockBit3 alongside emerging groups highlights a diverse and persistent ransomware threat. These attacks focus on data exfiltration, financial extortion, and operational disruption, posing significant risks to supply chains and manufacturing processes in the country.
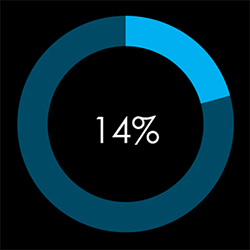
In total, 13 out of 91 gangs recorded victims in Taiwan in 2024, with a 14% participation rate.
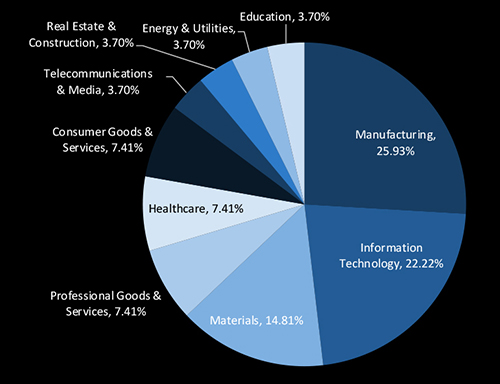
Manufacturing (25.93%) and Information Technology (22.22%) top the list of ransomware targets in Taiwan for 2024, reflecting attackers’ keen interest in disrupting critical supply chains and compromising high-value intellectual property. Materials (14.81%), along with Healthcare, Professional Goods & Services, and Consumer Goods & Services (each at 7.41%), also face a notable threat level, revealing that adversaries are broadening their focus to essential infrastructure and service sectors. Meanwhile, Telecommunications & Media, Real Estate & Construction, Energy & Utilities, and Education each account for 3.70%, indicating an ongoing expansion of targets. These findings highlight the pervasive and strategic nature of ransomware attacks targeting every industry.
State-Sponsored Espionage & Supply Chain Attacks
Ransomware Evolution & Cloud Exploits
Custom Malware & Advanced Attack Techniques
Operational Technology (OT) & IoT Risks
Social Engineering & Executive-Level Threats