



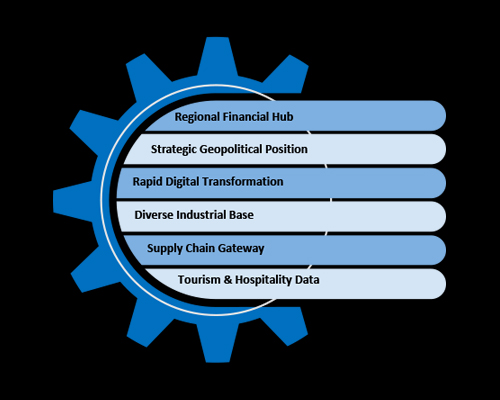
Regional Financial Hub:
Thailand’s expanding financial sector attracts cybercriminals seeking monetary gain through fraud, ransomware, and data theft.
Strategic Geopolitical Position:
As a key player in ASEAN, Thailand is targeted by nation-state actors conducting espionage and geopolitical surveillance.
Rapid Digital Transformation:
Swift digital adoption often faster than security implementation creates exploitable vulnerabilities.
Diverse Industrial Base:
High-value sectors such as energy, automotive, manufacturing, and healthcare make Thailand a ripe target for both economic and cyber-espionage attacks.
Supply Chain Gateway:
Integration in global logistics and production chains exposes Thailand to third-party and supply chain compromises.
Tourism & Hospitality Data:
Large volumes of personal and financial data from tourism fuel cybercriminal interest in identity theft and financial fraud.
U.S.-China Rivalry in ASEAN:
Thailand’s neutral stance draws cyber espionage from both geopolitical blocs aiming to influence policy and economic alignment.
Proximity to Regional Conflicts:
Instability in Myanmar and tensions in the South China Sea heighten cyber operations targeting Thailand for surveillance and disruption.
Defense and Intelligence Partnerships:
Participation in military cooperation (e.g., Cobra Gold exercises) makes Thai defense and government entities high-value cyber targets.
Domestic Political Sensitivities:
Internal unrest and digital activism create opportunities for foreign actors to launch disinformation, influence campaigns, or cyber disruptions.
Dependence on Foreign Technology Providers:
Reliance on Chinese and Western infrastructure providers increases exposure to state-sponsored supply chain attacks.
Belt and Road Initiative (BRI) Involvement:
Thailand’s involvement in China’s BRI projects raises the risk of cyber espionage targeting infrastructure, logistics, and communications.
Cyber Norms and Legal Gaps in the Region:
Variability in cyber regulations and cross-border enforcement challenges allow threat actors to operate with reduced risk in neighboring countries.
US-China Tariff War & Escalating Cyber Threats:
As trade tensions between the U.S. and China escalate, Thailand – positioned as a neutral economic hub – faces increased cyber pressure from both sides, including supply chain surveillance, IP theft, and cyber-espionage, as competing powers seek to monitor and influence regional economic flows.
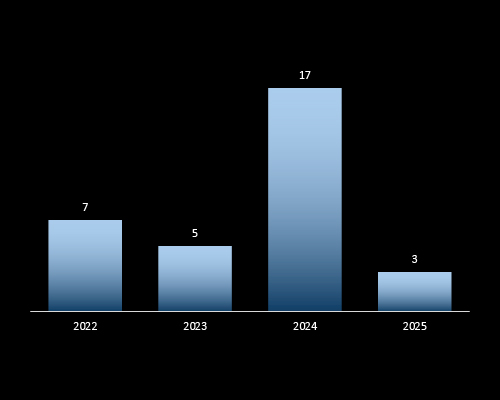
CYFIRMA observed a sharp spike in cyber campaigns targeting Thailand in 2024, with a total of 17 campaigns – a 240% increase from the previous year. This surge reflects heightened geopolitical tensions and increased targeting of Thailand’s strategic sectors. While 2025 shows fewer campaigns so far, it remains early in the year, and threat activity is expected to evolve.
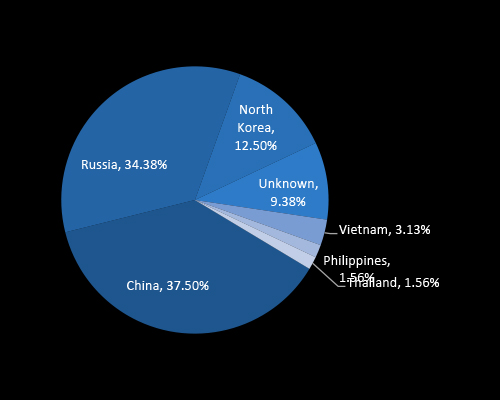
CYFIRMA’s analysis reveals that over 70% of threat actors targeting Thailand originate from China and Russia, indicating strong nation-state interest in Thailand’s geopolitical and economic posture. North Korea also contributes significantly, reflecting financially motivated cyber operations. The presence of local and regional actors highlights broad-based threats requiring strategic, multi-layered defense initiatives.
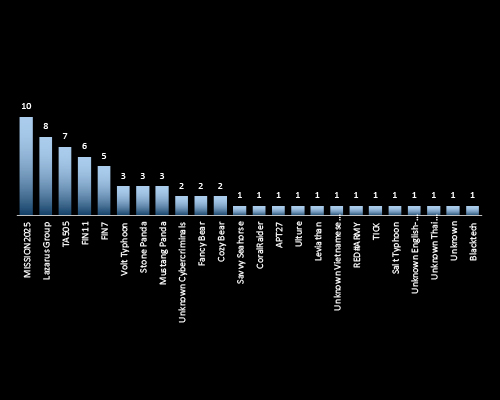
CYFIRMA identified a diverse mix of state-sponsored APTs and cybercriminal groups targeting Thailand, with MISSION2025, Lazarus Group, and TA505 leading in observed activity. The presence of Chinese, North Korean, and Russian-linked actors highlights Thailand’s strategic and economic relevance. This threat actor variety signals multi-motivated targeting ranging from espionage to financial gains, reinforcing the need for cross-sector threat visibility and executive oversight.
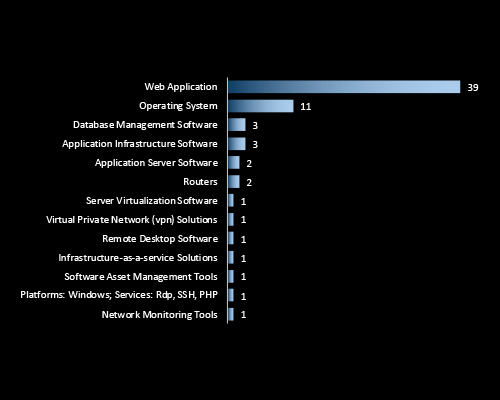
CYFIRMA’s insights reveal Web Applications as the most targeted technology, accounting for the majority of attacks exposing critical business and customer-facing assets. Operating systems and databases follow, indicating attempts to compromise core infrastructure. This trend highlights the urgent need for application-layer security, patch hygiene, and continuous threat monitoring to defend Thailand’s digital ecosystem.
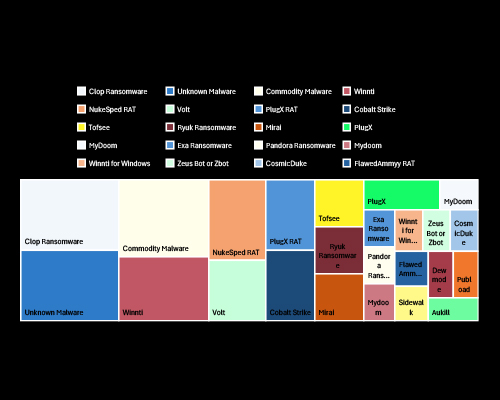
CYFIRMA observed a wide array of malware families targeting Thailand, with Cl0p Ransomware, Commodity Malware, and NukeSped RAT being the most prevalent. This mix reflects both financially motivated ransomware operations and state-linked espionage campaigns. The presence of tools like Cobalt Strike and PlugX RAT signals advanced, persistent intrusions highlighting the need for deep threat visibility and robust endpoint defense strategies.
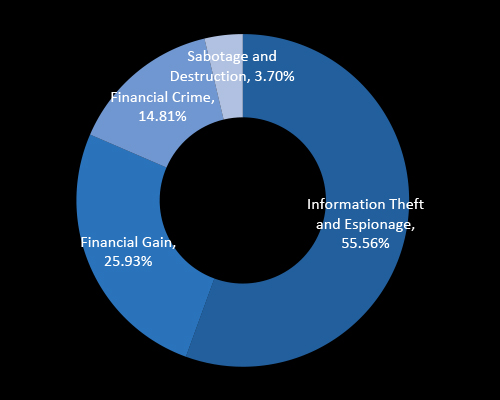
CYFIRMA’s analysis shows that over half (55.56%) of cyber attacks targeting Thailand are driven by information theft and espionage, reflecting nation-state interests in political, economic, and strategic data. Financial gain and cybercrime account for a combined 40%, highlighting Thailand’s growing digital economy as a lucrative target. This highlights the need for executive-level oversight in both national security and financial risk management.
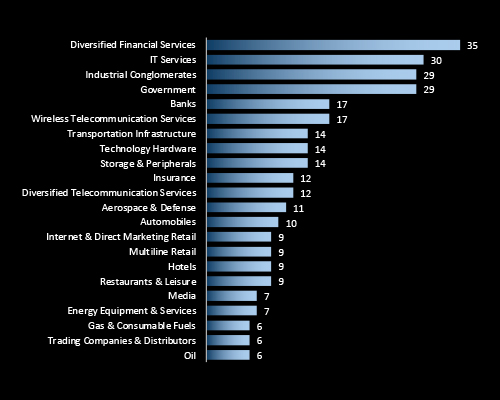
CYFIRMA’s data highlights Financial Services, IT Services, and Industrial Conglomerates as the most frequently targeted sectors in Thailand reflecting their economic significance and high digital exposure. Government and banking sectors also face sustained pressure, indicating both strategic espionage and financial motives. The broad industry spread reinforces the need for cross-sector cyber resilience at the national level.
Year-to-Year Elevation: High
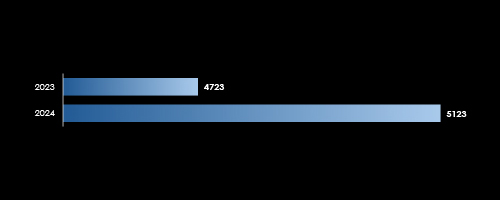
In 2023, CYFIRMA recorded 4,723 verified ransomware victims, while in 2024, the number increased to 5,123, representing an 8.5% year-over-year growth across all industries.
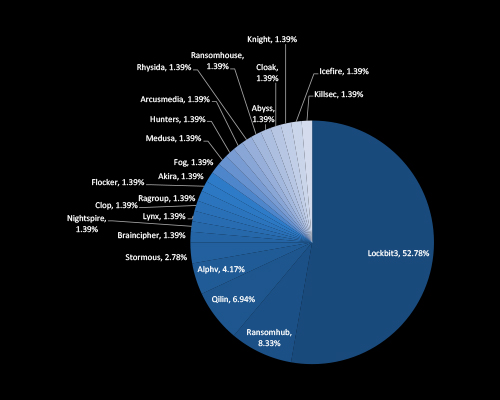
CYFIRMA’s threat intelligence shows that LockBit3 accounts for over half (52.78%) of ransomware activity in Thailand – underscoring its dominance and operational scale. Other active groups like RansomHub, and Qilin reflect the expanding RaaS ecosystem. The wide distribution of smaller players signals a fragmented but persistent threat landscape, demanding executive-level preparedness and business continuity planning.
In early 2023, the takedown of Hive caused a temporary slowdown in ransomware activity. However, this was followed by a surge driven by Cl0p, leveraging the MOVEit vulnerability.
Similarly, the early 2024 slowdown caused by the LockBit3 takedown was short-lived, as affiliates switched to other Ransomware-as-a-Service (RaaS) and RansomHub quickly emerged to fill the void in the RaaS ecosystem.
CYFIRMA data shows a sharp surge in ransomware attacks in 2023, with 35 confirmed victims, a fivefold increase from 2022. While 2024 saw a decline, the trend remains elevated, and 2025 already recorded 8 victims as of April 2025. This reflects ransomware’s persistent threat and reinforces the need for executive-level investment in incident response, recovery planning, and proactive threat intelligence.
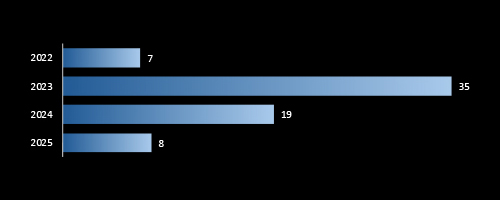
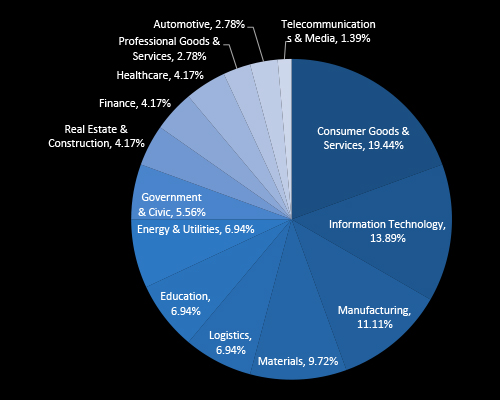
CYFIRMA data reveals that Consumer Goods & Services, IT, and Manufacturing are the most targeted industries by ransomware actors in Thailand reflecting their high digital exposure and economic importance. Sectors like Energy, Logistics, and Government also face consistent targeting, underlining a broad and cross-sector threat landscape. Executive focus on sector-specific resilience and ransomware readiness is critical to reducing operational risk.
Rise in Nation-State Espionage
Threat actors linked to China, North Korea, and Russia are intensifying campaigns targeting government, defense, and strategic industries driven by geopolitical motives.
Ransomware-as-a-Service (RaaS) Expansion
Groups like LockBit3 dominate attacks, while smaller affiliates rapidly adopt ready-made ransomware kits broadening the threat surface across sectors.
Supply Chain & Third-Party Risks
Increasing reliance on digital vendors and global logistics has introduced new vulnerabilities exploited by both APTs and cybercriminals.
Web Applications & Cloud Under Siege
Web-facing apps and cloud infrastructure remain top attack vectors, as digital transformation outpaces security investment in many organizations.
Threat Actor Localization
A growing presence of Thai-speaking and Southeast Asian-based attackers indicates evolving local threat ecosystems with knowledge of domestic targets.
Cross-Industry Targeting
No sector is immune attacks span from finance and IT to energy, logistics, and even consumer goods, pushing the need for sector-specific cyber resilience strategies.
Disinformation & Political Cyber Ops
Increasing use of influence campaigns, hack-and-leak tactics, and politically motivated defacements tied to regional and internal tensions.