Geopolitical Tensions & Regional Influence
Vietnam’s role in South China Sea disputes and strategic alliances with the U.S., Japan, and ASEAN nations make it a key target for state-sponsored cyber espionage, particularly from Chinese APT groups seeking intelligence on defense, government policies, and critical infrastructure.
Economic Growth & Industrial Espionage
As one of Southeast Asia’s fastest-growing economies, Vietnam’s manufacturing, energy, and finance sectors are prime targets for intellectual property theft and cyber-enabled industrial espionage, with Chinese, North Korean, and Russian APT groups actively targeting its technology and telecom industries.
Expanding Digital & Financial Infrastructure
Vietnam’s rapid digital transformation and fintech growth have attracted ransomware operators, financial fraudsters, and banking malware, while its rising cryptocurrency adoption has made it a hotspot for exchange compromises, scams, and crypto-related cyber fraud.
Supply Chain Vulnerabilities
As a regional manufacturing hub, Vietnam’s supply chain is deeply integrated with global tech giants, making it vulnerable to supply chain attacks where attackers exploit third-party vendors, logistics firms, and IT service providers for espionage and disruption.
Critical Infrastructure & Energy Sector Risks
Vietnam’s energy, telecom, and transportation sectors are increasingly targeted for state-sponsored sabotage and cyber extortion, while Industrial IoT (IIoT) adoption in manufacturing and energy introduces new cyber-physical attack vectors.
Weak Cybersecurity Frameworks & Insider Threats
Despite improving cybersecurity policies, gaps in enforcement, a shortage of skilled professionals, and weak cyber maturity make Vietnam vulnerable, while insider threats, business email compromise (BEC), and targeted phishing campaigns continue to exploit organizational weaknesses.
CYFIRMA observed a rise in cyber campaigns targeting Vietnam, with nine observed in 2024, up from eight in 2023. This trend signals an intensifying threat landscape, likely driven by geopolitical tensions, financial sector vulnerabilities, and growing digital transformation.

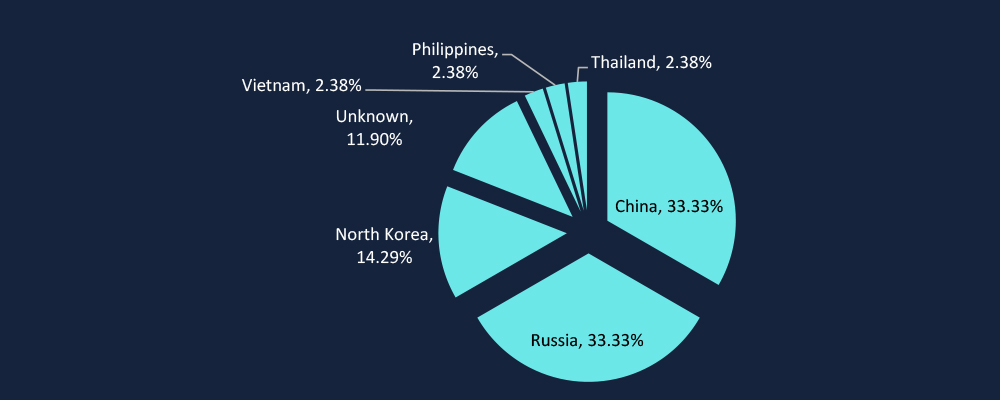
CYFIRMA’s analysis reveals that China (33.33%), Russia (33.33%), and North Korea (14.29%) are the primary origins of threat actors targeting Vietnam. Chinese APT groups prioritize intellectual property theft and industrial espionage, particularly in semiconductors and advanced manufacturing. Russian actors focus on financially motivated cybercrime and geopolitical destabilization, while North Korean groups like Lazarus conduct revenue-driven attacks to fund state objectives. Vietnam’s strategic industries remain a high-priority target, reinforcing the need for enhanced cyber resilience and proactive defense strategies.
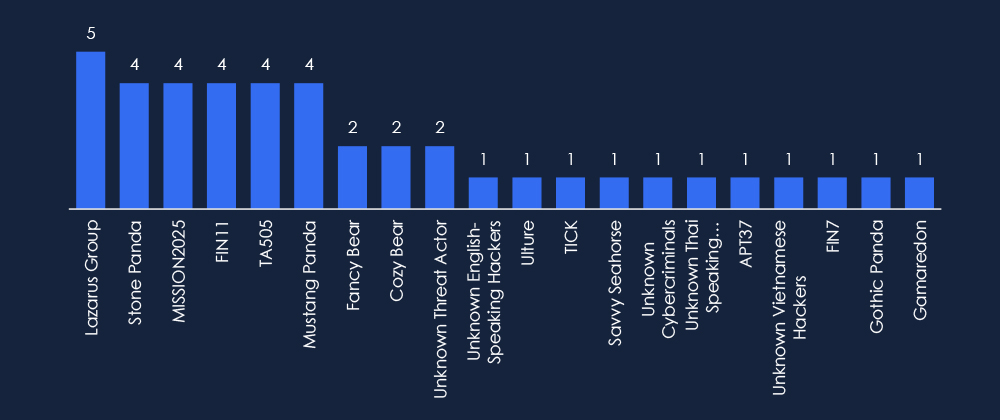
CYFIRMA’s analysis identifies a diverse set of suspected threat actors targeting Vietnam, with Lazarus Group, Stone Panda, and MISSION2025 among the most active. The presence of both state-sponsored APTs and financially motivated cybercriminals highlights the evolving risk landscape.
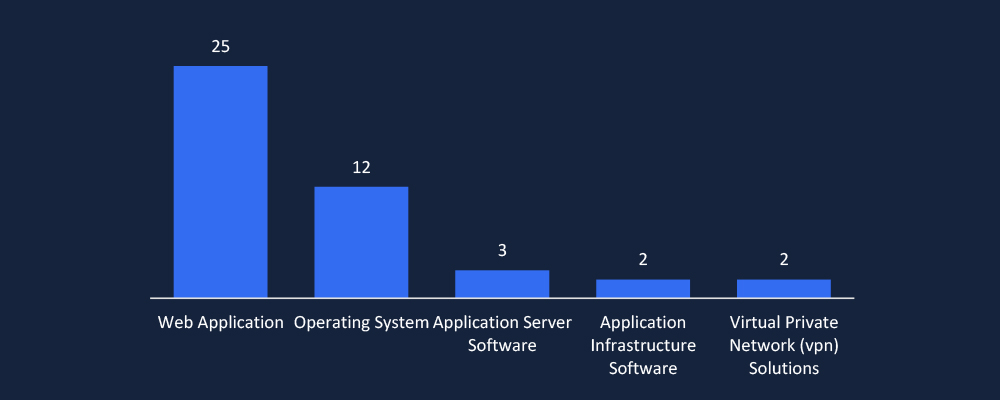
CYFIRMA’s observations highlight web applications (25) and operating systems (12) as the most targeted attack surfaces, reflecting a persistent focus on web-facing vulnerabilities and system-level exploits. The targeting of application servers, infrastructure software, and VPN solutions suggests an evolving strategy aimed at compromising core infrastructure and credential-based access, reinforcing the need for robust patch management and proactive security controls.
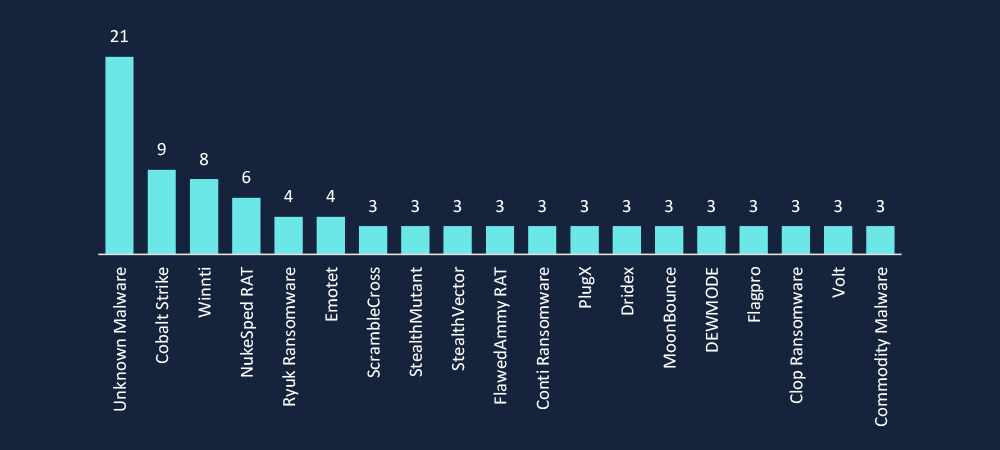
CYFIRMA’s observations indicate unknown malware (21) as the most prevalent, signaling the use of custom or evolving threats to evade detection. The presence of Cobalt Strike, PlugX RAT, and Winnti highlights advanced adversary tactics, likely used for persistence and lateral movement. The inclusion of Cl0p, and Ryuk ransomware points to an active mix of state-sponsored espionage and financially motivated cybercrime.
Year-to-Year Elevation: High
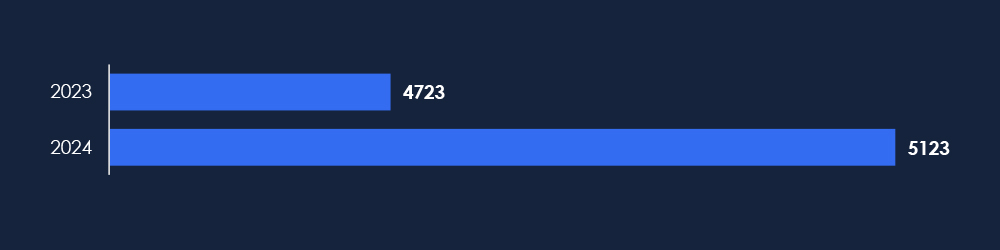
In 2023, CYFIRMA recorded 4,723 verified ransomware victims, while in 2024, the number increased to 5,123, representing an 8.5% year-over-year growth across all industries.
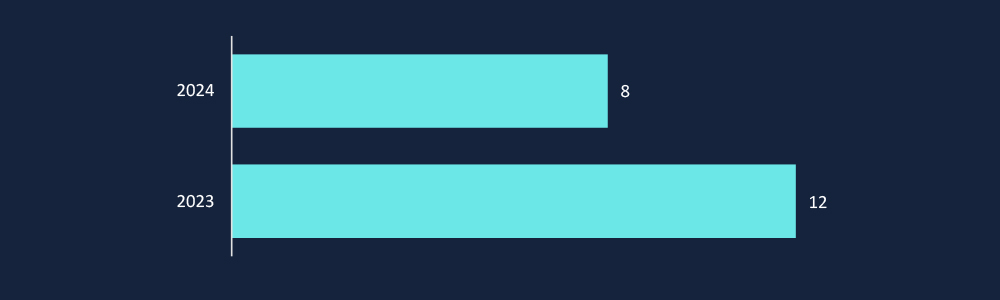
Ransomware attacks in Vietnam declined from 12 victims in 2023 to 8 in 2024, suggesting a temporary reduction in reported incidents. However, this does not indicate a diminished threat—Ransomware-as-a-Service (RaaS) operations and targeted extortion campaigns remain active. The evolving tactics of ransomware groups, including double extortion and supply chain compromises, necessitate continued vigilance and enhanced cyber resilience strategies.
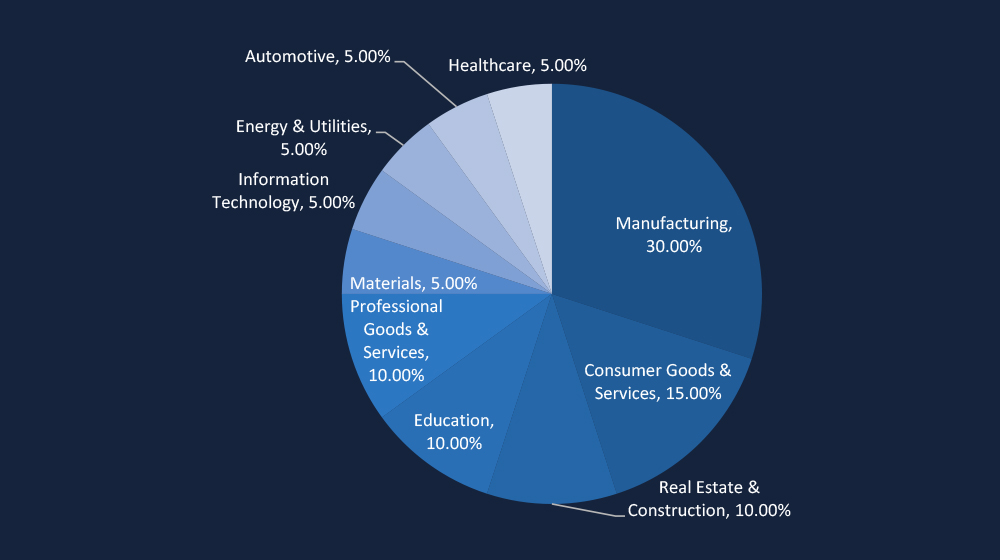
Manufacturing (30%) remains the top ransomware target in Vietnam, reflecting attackers’ focus on disrupting supply chains and stealing intellectual property. Consumer Goods & Services (15%) and Real Estate & Construction (10%) also face significant threats, highlighting the broadening ransomware focus on critical economic sectors. The targeting of education, healthcare, energy, and IT underscores an expanding risk landscape.
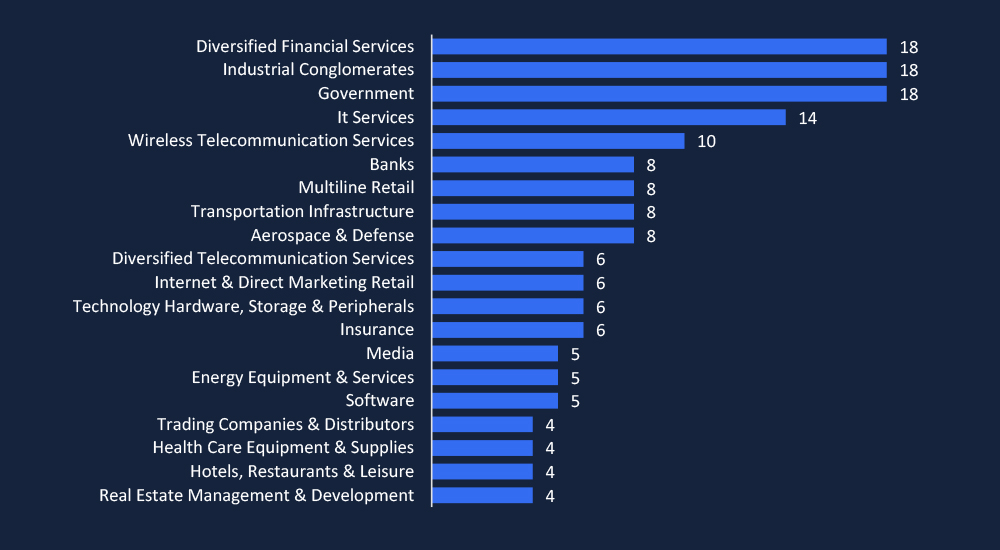
CYFIRMA’s analysis highlights financial services, industrial conglomerates, and government as the top-targeted sectors in Vietnam. IT services and telecommunications follow closely, reflecting adversaries’ focus on critical infrastructure and data-rich industries. The targeting of banks, aerospace, and transportation highlights the increasing cyber risks to Vietnam’s economic and national security sectors.
In early 2023, the takedown of Hive caused a temporary slowdown in ransomware activity. However, this was followed by a surge driven by Cl0p, leveraging the MOVEit vulnerability.
Similarly, the early 2024 slowdown caused by the LockBit3 takedown was short-lived, as affiliates switched to other Ransomware-as-a-Service (RaaS) and RansomHub quickly emerged to fill the void in the RaaS ecosystem.
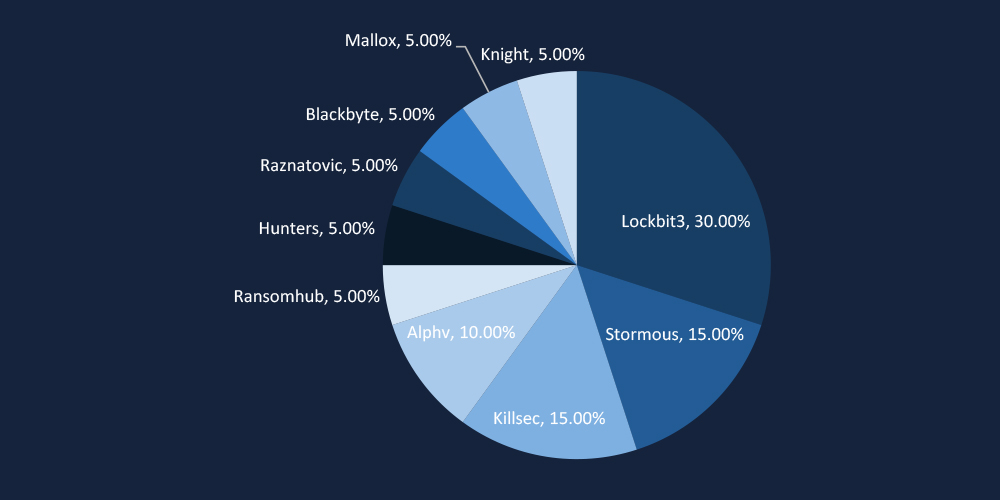
LockBit3 (30%) remains the most active ransomware group targeting Vietnam, followed by Stormous (15%) and KillSec (15%), indicating a mix of established Ransomware-as-a-Service (RaaS) operations and emerging threat actors. The presence of diverse ransomware groups, including Alphv, RansomHub, and BlackByte, highlights a persistent threat landscape focused on data exfiltration, financial extortion, and operational disruption.