



The CYFIRMA Research and Advisory team has found ‘Nnice’ Ransomware while monitoring various underground forums as part of our Threat Discovery Process.
The ransomware targets Windows systems with advanced encryption techniques, leaving a distinct file extension and sophisticated evasion and persistence methods, posing significant risks to data security. This ransomware highlights the urgent need for proactive defenses and comprehensive incident response strategies.
Target Technologies: Windows
Encrypted file extension: .xdddd
Observed First: 2025-01-17
Observed First By: CYFIRMA
Threat actor Communication mode: Mail
Researchers at CYFIRMA have recently observed a ransomware strain identified as Nnice.
The ransomware, once entered into the victim’s system, encrypts files appending the “.xdddd” extension to the original filenames. It leaves behind a ransom note titled “Readme.txt,” containing instructions for file recovery.
Once the ransomware encrypts the file, it changes the wallpaper as below.
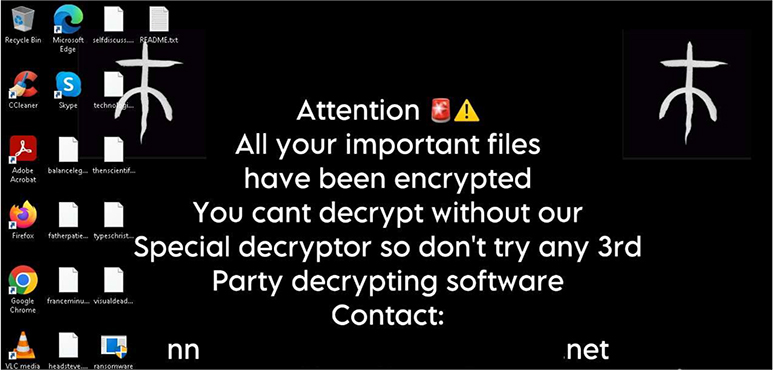
Below is the ransom note README.txt
| MITRE ATTACK TECHNIQUES | ||
| Tactic | ID | Technique/ Sub Technique |
| Execution | T1106 | Native API |
| Persistence | T1542 | Pre-OS Boot |
| Persistence | T1542.003 | Bootkit |
| Persistence | T1547 | Boot or Logon Autostart Execution |
| Persstence | T1547.001 | Registry Run Keys / Startup Folder |
| Persistence | T1574 | Hijack Execution Flow |
| Persistence | T1574.002 | DLL Side-Loading |
| Privilege Escalation | T1055 | Process Injection |
| Privilege Escalation | T1547 | Boot or Logon Autostart Execution |
| Privilege Escalation | T1547.001 | Registry Run Keys / Startup Folder |
| Privilege Escalation | T1574 | Hijack Execution Flow |
| Privilege Escalation | T1574.002 | DLL Side-Loading |
| Defense Evasion | T1014 | Rootkit |
| Defense Evasion | T1027 | Obfuscated Files or Information |
| Defense Evasion | T1027.002 | Software Packing |
| Defense Evasion | T1036 | Masquerading |
| Defense Evasion | T1055 | Process Injection |
| Defense Evasion | T1070 | Indicator Removal |
| Defense Evasion | T1070.004 | File Deletion |
| Defense Evasion | T1140 | Deobfuscate/Decode Files or Information |
| Defense Evasion | T1497 | Virtualization/Sandbox Evasion |
| Defense Evasion | T1542 | Pre-OS Boot |
| Defense Evasion | T1542.003 | Bootkit |
| Defense Evasion | T1562 | Impair Defenses |
| Defense Evasion | T1562.001 | Disable or Modify Tools |
| Defense Evasion | T1564 | Hide Artifacts |
| Defense Evasion | T1564.001 | Hidden Files and Directories |
| Defense Evasion | T1564.003 | Hidden Window |
| Defense Evasion | T1574 | Hijack Execution Flow |
| Defense Evasion | T1574.002 | DLL Side-Loading |
| Credential Access | T1003 | OS Credential Dumping |
| Credential Access | T1539 | Steal Web Session Cookie |
| Credential Access | T1552 | Unsecured Credentials |
| Credential Access | T1552.001 | Credentials in Files |
| Discovery | T1012 | Query Registry |
| Discovery | T1033 | System Owner/User Discovery |
| Discovery | T1082 | System Information Discovery |
| Discovery | T1083 | File and Directory Discovery |
| Discovery | T1087 | Account Discovery |
| Discovery | T1497 | Virtualization/Sandbox Evasion |
| Discovery | T1518 | Software Discovery |
| Discovery | T1518.001 | Security Software Discovery |
| Collection | T1005 | Data from Local System |
| Collection | T1114 | Email Collection |
| Command and Control | T1071 | Application Layer Protocol |
| Command and Control | T1095 | Non-Application Layer Protocol |
| Impact | T1486 | Data Encrypted for impact |
| Impact | T1490 | Inhibit System Recovery |
| Impact | T1496 | Resource Hijacking |
Indicators of Compromise
Kindly refer to the IOCs section to exercise controls on your security systems.
| SHA 256 | Remark |
| 4dd08b0bab6f19d143cca6f96c8b780da7f60dbf74f1c16c3442bc9f07d38030 | Block |
STRATEGIC RECOMMENDATION
MANAGEMENT RECOMMENDATION
TACTICAL RECOMMENDATION