



In March 2025, ransomware attacks targeted critical industries such as Manufacturing, IT, and Healthcare. Notable groups like Black Basta and Moonstone Sleet evolved new strategies, such as automating brute-force VPN attacks and deploying ransomware-as-a-service models. The United States was the top target for ransomware, followed by Germany and Canada. Innovations like the BRUTED brute-force framework and the exploitation of IoT devices demonstrated an increasing sophistication of ransomware attacks. New groups such as Arkana and CrazyHunter emerged, further complicating the cybersecurity landscape.
This report provides an analysis of the evolving ransomware threat landscape in March 2025, focusing on the industries, geographical targets, and emerging trends in ransomware attacks. The report highlights the significant decline in ransomware incidents compared to February 2025, despite still being higher than in previous years. It also examines the development of new attack methods, such as automated brute-force tools and the exploitation of exposed devices, as well as the emergence of new ransomware groups.
Throughout March 2025, there was notable activity from several ransomware groups. Here are the trends regarding the top 5:
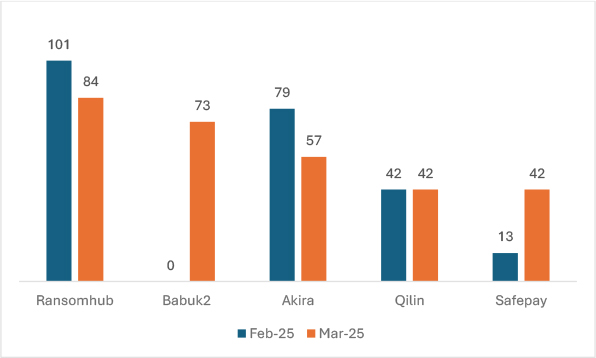
In March 2025, RansomHub saw a 16.8% decline, indicating reduced activity or successful ransom gains. Akira followed with a 27.8% drop, suggesting a downward trend. Meanwhile, Babuk2 emerged from inactivity, marking a significant surge. Qilin remained unchanged, maintaining its presence. The most dramatic rise came from Safepay, which surged by 223%, highlighting its growing threat. These shifts indicate evolving ransomware tactics and changing dominance among groups.
Some researchers suggest that Babuk2 ransomware is issuing fake extortion demands using data from old breaches. With low confidence, we assess that this may be a tactic to gain credibility and attract new affiliates by falsely claiming responsibility for major attacks, positioning itself as a formidable player in the ransomware landscape.
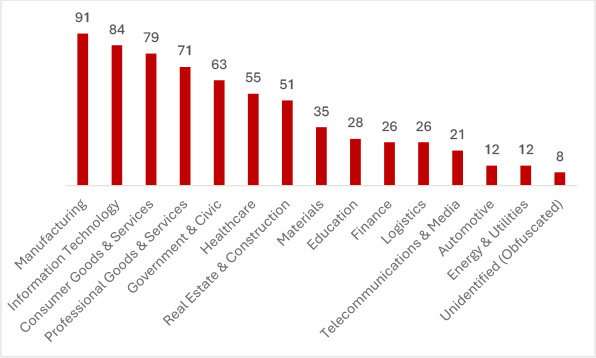
In March 2025, cyber adversaries intensified their focus on critical industries, with Manufacturing (91), IT (84), and Consumer Goods & Services (79) facing relentless attacks. Government (71) and Healthcare (55) remained high-risk zones, while threats spread to Education (28), Finance (26), and Energy (12) highlighting the widening battlefield in the ever-evolving cyber threat landscape.
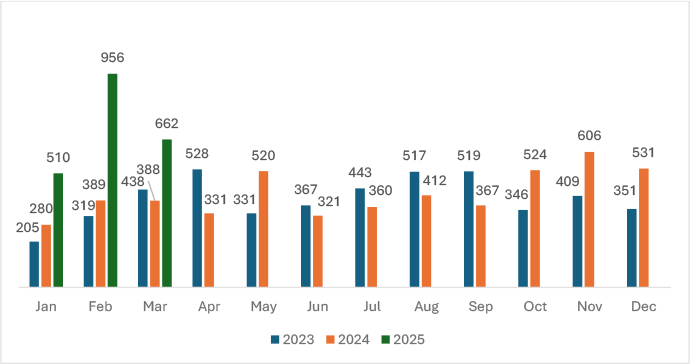
In March 2025, ransomware activity recorded 662 incidents, showing a noticeable decline from the previous month’s peak of 956 attacks in February 2025. This drop represents a 30.7% decrease month-over-month, yet the volume in March remained significantly higher compared to the same period in prior years.
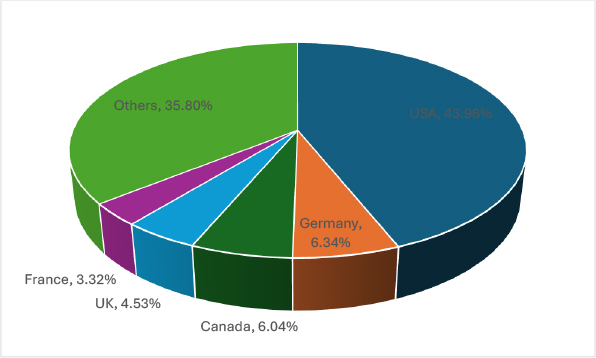
In March 2025, the United States remained the top ransomware target, with 291 victims – significantly outpacing other regions. Germany followed with 42 attacks, while Canada (40) the United Kingdom (30), and France (22) saw lower but notable ransomware activity. These regions are prime targets due to their strong economies, data-rich enterprises, critical infrastructure, and high ransom-paying potential, making them lucrative for cybercriminals.
Black Basta creates a tool to automate VPN brute-force attacks
The Black Basta ransomware group has developed an automated brute-forcing framework called BRUTED to target edge networking devices, including firewalls and VPNs. This tool enables large-scale credential-stuffing and brute-force attacks against exposed endpoints, streamlining initial access for ransomware deployment.
BRUTED specifically targets SonicWall NetExtender, Palo Alto GlobalProtect, Cisco AnyConnect, Fortinet SSL VPN, Citrix NetScaler, Microsoft RDWeb, and WatchGuard SSL VPN. The framework scans for publicly accessible edge devices by enumerating subdomains, resolving IPs, and appending common prefixes like “.vpn” or “remote”. Once identified, password candidates are retrieved from a remote server, supplemented with locally generated guesses, and executed via multiple CPU processes.
To improve efficiency, BRUTED extracts Common Name (CN) and Subject Alternative Names (SAN) from SSL certificates to generate additional password variations. The framework also uses SOCKS5 proxies to evade detection, with infrastructure linked to Russian servers.
Despite not exploiting vulnerabilities, BRUTED significantly enhances the attack surface for ransomware campaigns. Defending against it requires strong, unique passwords, multi-factor authentication (MFA), login attempt monitoring, rate-limiting, and blocking known malicious IPs.
ETLM Assessment:
Black Basta’s BRUTED framework is expected to expand globally, targeting a wider range of edge devices and integrating more advanced evasion techniques. As brute-force automation improves, ransomware groups may deploy AI-driven password cracking and leverage botnets for distributed attacks, increasing the scale and speed of network breaches across industries.
North Korean hackers seen using Qilin ransomware
A North Korean-backed group, Moonstone Sleet, has been deploying Qilin ransomware in recent attacks, marking a shift from their previously custom-built ransomware. Their operations target financial and cyberespionage sectors through trojanized software, malicious games, npm packages, and fake software firms engaging victims via LinkedIn, freelancing platforms, and email. The group has also in the past utilized FakePenny ransomware, demanding $6.6 million in BTC after successful intrusions.
Qilin ransomware, active since 2022, has attacked over 310 victims, impacting industries such as healthcare, automotive, and judiciary services. Its affiliates leveraged advanced Linux encryptors for VMware ESXi environments, intensifying its reach in late 2023. Past attacks included major disruptions, such as the Synnovis attack affecting NHS hospitals in London.
Historically, North Korean groups have been involved in ransomware campaigns, including Holy Ghost, Maui, and WannaCry. The trend suggests an evolution in tactics, integrating Ransomware-as-a-Service (RaaS) to expand their attack scope.
ETLM Assessment:
Moonstone Sleet’s use of Qilin ransomware signals an increasing reliance on third-party RaaS for financial gains. Future campaigns may expand beyond espionage to more disruptive attacks targeting critical infrastructure. Enhanced Linux-based encryptors for cloud environments and broader RaaS partnerships could lead to wider-scale ransomware incidents with higher financial impacts.
Akira encrypted network from a webcam to bypass EDR
The Akira ransomware group used an unsecured webcam to bypass Endpoint Detection and Response (EDR) and encrypt files on a victim’s network. Initially, they gained access through an exposed remote access solution, likely exploiting stolen credentials or brute-force attacks. They then deployed AnyDesk for persistence and Remote Desktop Protocol (RDP) for lateral movement before attempting to launch Windows-based ransomware. However, EDR blocked their payload.
In response, the attackers scanned for alternative network devices, identifying a Linux-based webcam that lacked EDR protection. The webcam’s vulnerabilities allowed remote shell access, enabling the attackers to mount Windows SMB network shares and execute a Linux ransomware encryptor. As the malicious SMB traffic from the webcam went undetected, Akira successfully encrypted network files despite EDR defenses.
This attack highlights the security risks posed by unmonitored IoT devices in corporate environments. The exploited webcam had available patches, meaning the attack could have been prevented.
ETLM Assessment:
Akira and other ransomware may increasingly exploit IoT and edge devices to evade detection. Future attacks could target other Linux-based systems, such as security cameras, NAS devices, or industrial control systems, to gain persistence and execute encryption. Strengthening IoT security policies, isolating networks, and monitoring non-traditional endpoints will be critical in mitigating future threats.
New Betruger ‘multi-function’ backdoor used in RansomHub operations
The newly identified Betruger backdoor has been linked to recent RansomHub ransomware attacks, highlighting a shift toward custom-built malware in ransomware operations. Unlike traditional attacks that rely on publicly available tools like Mimikatz and Cobalt Strike, Betruger consolidates multiple pre-encryption functionalities into a single payload, reducing the need for additional tools and enhancing stealth.
Betruger exhibits a range of capabilities commonly found in pre-ransomware deployment stages. It supports privilege escalation, network scanning, credential dumping, keylogging, screenshot capture, and file exfiltration to a command and control (C2) server. These features indicate its role in the preparatory phase of ransomware attacks, streamlining the compromise process while evading detection.
Attackers are deploying Betruger under filenames like mailer.exe and turbomailer.exe to disguise it as a legitimate application. Despite its name, the malware has no mailing functionality, suggesting an attempt to blend into enterprise environments. The backdoor’s design minimizes the number of tools deployed on a compromised network, making detection and mitigation more challenging.
The emergence of Betruger reflects a growing trend where ransomware groups develop tailored malware to gain initial access, establish persistence, and facilitate data exfiltration before encryption. By integrating multiple attack functions into a single payload, attackers reduce their reliance on external tools, improving operational security.
ETLM Assessment:
Future ransomware operations will likely increase reliance on custom-built malware like Betruger to enhance stealth, persistence, and automation. Ransomware groups may reduce dependence on public tools, developing all-in-one backdoors for pre-encryption tasks. Expect more sophisticated data exfiltration methods, multi-stage payloads, and targeted attacks on critical sectors, complicating defense and attribution efforts.
Albabat Evolves to Target Linux and macOS
Albabat ransomware has evolved significantly, with version 2.0 now targeting Windows, Linux, and macOS. This highlights its adaptability and expansive reach across diverse systems and infrastructures.
Version 2.0 selectively encrypts files with specific extensions such as .bat, .com, .cmd, and .cpl, while avoiding directories like Searches, AppData, $RECYCLE.BIN, and System Volume Information. Additionally, it terminates critical processes, including task manager, registry editor, and office-related applications, to evade detection and disable security measures. The ransomware connects to a PostgreSQL database for tracking infections, managing ransom payments, and facilitating data exfiltration.
A notable tactic introduced in this version is the use of a GitHub repository to store and distribute ransomware configuration files, streamlining the attack process. The repository, created in early 2024, remains active, with ongoing modifications to the configuration code. Additionally, traces of a developing version, labeled 2.5, were found, containing a configuration file referencing newly added cryptocurrency wallets for Bitcoin, Ethereum, Solana, and BNB, though no transactions have been recorded yet.
These developments indicate continuous refinement of attack methodologies, with threat actors focusing on multi-platform compatibility, stealthier delivery mechanisms, and improved ransom tracking. These updates and infrastructure modifications suggest an ongoing effort to enhance effectiveness and broaden impact.
ETLM Assessment:
The evolution of ransomware suggests a future where attacks become more sophisticated, platform-agnostic, and harder to detect. Threat actors will increasingly leverage cloud services, decentralized storage, and encrypted communication for command-and-control operations. AI-driven automation may enable faster exploitation of vulnerabilities, while ransom demands could shift towards cryptocurrency mixers for untraceable transactions. Collaboration between ransomware groups will likely grow, leading to shared access and refined extortion tactics. Organizations must prioritize Zero Trust security, proactive threat intelligence, and robust backup strategies to mitigate risks.
Medusa uses a Malicious Driver to Disable Anti-Malware with Stolen Certificates
The Medusa ransomware operation has been observed employing a BYOVD (Bring Your Own Vulnerable Driver) attack to disable security solutions. A malicious driver named ABYSSWORKER, masquerading as a legitimate security driver, is used to manipulate system processes, disable endpoint detection and response (EDR) tools, and evade detection. The driver, “smuol.sys,” is signed with revoked certificates from Chinese vendors and is capable of terminating processes, deleting files, and even rebooting machines. These actions are executed through specific I/O control codes, allowing the ransomware to gain control over infected systems while neutralizing security defenses.
Threat actors have also exploited a vulnerable driver, “vsdatant.sys,” associated with antivirus software, to gain elevated privileges and disable security features such as Memory Integrity. By leveraging this outdated driver, attackers bypass protections, establish persistent RDP access, and exfiltrate credentials for further exploitation.
ETLM Assessment:
Ransomware will continue to evolve with a focus on stealth, automation, and persistence. Threat actors will increasingly leverage BYOVD attacks, abusing legitimate drivers to bypass security measures. The rise of modular malware like Betruger suggests a shift toward all-in-one attack frameworks, reducing reliance on external tools. Ransom demands will likely include data theft and extortion, forcing victims into compliance. With adversaries improving evasion techniques, organizations must adopt zero-trust architectures, proactive monitoring, and endpoint hardening to counter these emerging threats.
Threat actors seen deploying a new ransomware
The threat actor RedCurl, historically engaged in corporate espionage, has shifted tactics by deploying QWCrypt ransomware to encrypt Hyper-V virtual machines. The attack vector begins with phishing emails carrying IMG attachments that exploit DLL sideloading through a legitimate Adobe executable. Once executed, persistence is established via a scheduled task. The attackers use living-off-the-land techniques for stealth, including a custom wmiexec variant for lateral movement and Chisel for tunneling and RDP access.
Before deploying ransomware, RedCurl disables security defenses using 7z encrypted archives and a multi-stage PowerShell process. Unlike conventional Windows ransomware, QWCrypt is designed to target Hyper-V systems via command-line arguments such as –hv (encrypt Hyper-V VMs), –kill (terminate VM processes), and –turnoff (shut down Hyper-V VMs). The malware uses the XChaCha20-Poly1305 encryption algorithm and appends .locked$ or .randombits$ extensions to encrypted files. It also supports intermittent encryption to optimize speed.
RedCurl has not established a public data leak site, raising questions about its ransomware motives. The group may be engaging in ransomware either as a monetization fallback when espionage clients fail to pay or as a smokescreen to hide data theft.
ETLM Assessment:
Ransomware attacks will increasingly target virtualization platforms and cloud environments, bypassing traditional security defenses. Threat actors will refine stealth techniques, leveraging fileless malware and intermittent encryption to evade detection. Additionally, private extortion will replace public ransom demands, with attackers directly negotiating payments to avoid exposure. The use of multi-function malware will rise, integrating ransomware, espionage, and persistence mechanisms into a single payload.
New ransomware strain seen exploiting Fortinet vulnerabilities.
A new ransomware operator, Mora_001, is exploiting two Fortinet vulnerabilities, CVE-2024-55591 and CVE-2025-24472, to gain unauthorized access to firewall appliances and deploy a custom ransomware strain known as SuperBlack. These authentication bypass flaws allow attackers to obtain super_admin privileges by sending WebSocket-based attacks through the jsconsole interface or making direct HTTPS requests to exposed firewall interfaces.
Once inside, the attacker creates persistent administrator accounts (forticloud-tech, fortigate-firewall, administrator) and modifies automation tasks to ensure account persistence even if deleted. They then map the network and perform lateral movement using stolen VPN credentials, WMIC, SSH, and TACACS+/RADIUS authentication. Before encryption, data is exfiltrated using a custom tool for double extortion.
The SuperBlack ransomware encrypts files on compromised systems, prioritizing file servers, database servers, and domain controllers. A ransom note is dropped, and after encryption, a custom wiper named WipeBlack is deployed to remove traces of the ransomware executable, making forensic analysis difficult.
Analysis suggests a strong link between SuperBlack and LockBit 3.0, as the encryptor is based on LockBit’s leaked builder, sharing an identical payload structure and encryption methods. Additionally, a TOX chat ID associated with LockBit is included in ransom notes, and multiple infrastructure overlaps have been identified. Furthermore, WipeBlack has been used by other ransomware groups like BrainCipher, EstateRansomware, and SenSayQ, which also have ties to LockBit.
ETLM Assessment:
Ransomware groups will continue exploiting firewall and network security flaws for initial access, with a growing focus on privileged persistence. Custom wipers will be increasingly used to erase traces post-encryption. Leaked ransomware builders will contribute to the emergence of new independent ransomware groups. Targeted extortion over public data leaks will become a preferred strategy, allowing attackers to maintain secrecy while maximizing financial gains.
Arkana
Arkana is a newly identified ransomware group that publicly debuted with aggressive and high-profile attacks. During the writing of this report, the group had claimed 2 victims.
CrazyHunter
CrazyHunter is a newly identified Go-based ransomware variant, derived from the open-source Prince encryptor malware family. Upon execution, it encrypts user files and drops a ransom note titled “Decryption Instructions.txt”, which closely mirrors the format used in earlier Prince ransomware deployments. Threat actors behind CrazyHunter have been observed employing a wide range of tools to facilitate their operations – including Donut for converting PE files into shellcode, the SharpGPOAbuse tool for lateral movement, and various utilities focused on defense evasion and data exfiltration, indicating a well-orchestrated and modular attack strategy.
During the writing of this report, the group had claimed 9 Victims.
NightSpire
NightSpire is a newly emerged ransomware group making its debut on the cybercrime landscape. Limited background information exists on the actor.
Positioning itself as a relentless and formidable threat, NightSpire vows to exploit every available vulnerability to compromise targeted organizations. The group’s messaging and portal structure reflects a calculated effort to instill fear, establish credibility, and drive ransom negotiations. Below is an analysis of their infrastructure and the broader implications of their activities.
RALord
RALord is a newly identified Rust-based ransomware variant observed in the wild. It encrypts victim files and appends the “.RALord” extension to the affected filenames. Upon execution, the malware drops a ransom note directing victims to communicate with the threat actors through qTox chat for further instructions. The note also includes a threat to publicly leak stolen data via a dedicated leak site if ransom demands are not fulfilled. During the drafting of this report, the group had claimed responsibility for attacks on seven victims globally.
VanHelsing
VanHelsing, a newly discovered ransomware variant by CYFIRMA is actively circulating in the wild. It encrypts victim files, appending either the .vanhelsing or .vanlocker extension. Upon infection, it drops a ransom note titled “README.txt” and alters the victim’s desktop wallpaper to reinforce the extortion message. The ransomware is designed to delete volume shadow copies, hindering recovery efforts. VanHelsing operators utilize a double extortion approach, threatening to leak stolen data if the ransom is not paid. At the time of reporting, the group had claimed eight victims worldwide.

Sam’s Club investigates Cl0p ransomware breach claims
A prominent U.S.-based retail warehouse chain is currently investigating a possible security incident following claims by the Cl0p ransomware group. Cl0p listed the company on its dark web leak site, accusing it of neglecting customer security, though no breach evidence has been published yet. The gang previously leveraged CVE-2024-50623, a zero-day vulnerability in Cleo secure file transfer software, to orchestrate widespread data theft campaigns. This software is widely adopted by global enterprises, significantly amplifying the impact. Cl0p’s activity aligns with its history of exploiting vulnerabilities in managed file transfer tools such as Accellion FTA, MOVEit Transfer, and GoAnywhere MFT. These campaigns often result in mass extortion and data leaks. In a related incident, another organization disclosed that nearly 22,000 customers were affected after Cl0p exploited a similar third-party vulnerability. Although no technical indicators were shared in this case, the incident underscores the ongoing risk posed by ransomware actors exploiting zero-day vulnerabilities in supply chain software.
Qilin Ransomware breached Ukraine’s Ministry of Foreign Affairs
The ransomware group Qilin, operating out of Russia, has reportedly breached Ukraine’s Ministry of Foreign Affairs, stealing sensitive data, including personal information, private correspondence, and official decrees. Qilin, which runs a ransomware-as-a-service operation and demands payments in cryptocurrencies like Bitcoin and Monero, claimed responsibility shortly after the incident. The group stated that some of the stolen data had already been sold. Originally known as “Agenda”, Qilin rebranded in late 2022 and has since been linked to several high-profile attacks, including healthcare disruptions. The ministry has not confirmed the breach, which comes amid escalating geopolitical tensions.
Hellcat Ransomware Group targeted the Ascom Technical Ticketing System
The ransomware group Hellcat has targeted a Swiss-based telecom provider, breaching its Jira server and exfiltrating 44GB of sensitive data, including source code, invoices, and internal project documentation. Known for exploiting credentials stolen via infostealers, Hellcat continues its campaign against organizations using Jira. The group uses phishing, public-facing app exploitation, and PowerShell-based infection chains to establish persistence, supported by SliverC2 malware infrastructure. Its ransomware payload, which encrypts files without altering extensions, shares traits with Morpheus ransomware. The incident highlights the risk of outdated credentials and the need for strong access controls, MFA, and timely revocation of third-party permissions.
Medusa seen targeting healthcare providers.
The Medusa ransomware group has claimed responsibility for a severe cyberattack on a UK-based healthcare provider, exfiltrating and encrypting approximately 50TB of sensitive data. Initially thought to involve 2TB, the breach affected multiple subdomains linked to legacy systems. Medusa provided proof files, including a domain computers list dump, confirming deep network access. The threat actors demanded a $2 million ransom by February 28, threatening data release or sale. Despite the scale of the breach, the targeted organization has remained publicly silent, while Medusa disputes official claims of minimizing the impact and insists full control over the network was achieved during the attack.
Based on available public reports, approximately 31% of enterprises are compelled to halt their operations, either temporarily or permanently, in the aftermath of a ransomware onslaught. The ripple effects extend beyond operational disruptions, as detailed by additional metrics:
Impact Assessment
Ransomware remains a serious threat to organizations and individuals, locking access to critical data and demanding payment for its release. The damage extends beyond ransom payments, often involving costly recovery processes, operational downtime, and long-term reputational harm. Victims may also face regulatory fines and market disruption, which erode stakeholder trust and financial stability. To protect against these consequences, it is essential for both the public and private sectors to adopt proactive cybersecurity strategies and strengthen their resilience against such attacks.
Victimology
Cybercriminals are increasingly focusing on businesses that manage vast amounts of sensitive information, such as personal data, financial records, and intellectual property. Sectors like manufacturing, real estate, healthcare, FMCG, e-commerce, finance, and technology are especially at risk due to their large data footprints. Threat actors often target countries with robust economies and advanced digital ecosystems, leveraging security gaps to encrypt vital data and demand high-value ransoms. These attacks are driven by the intent to maximize financial returns through highly coordinated and strategic operations.
The ransomware threat landscape in March 2025 highlights a marked shift towards more sophisticated and targeted attacks. Groups are increasingly relying on automation, exploiting exposed devices, and leveraging advanced evasion techniques to bypass security measures. The rise of new ransomware groups and the continued targeting of critical sectors, particularly in the U.S. and Europe, calls for enhanced defense mechanisms. Organizations must adopt comprehensive strategies that include multi-factor authentication, proactive threat intelligence, and robust network monitoring. As the tactics of cybercriminals evolve, so too must the resilience of cybersecurity frameworks to safeguard against these persistent and evolving threats.
TACTICAL RECOMMENDATIONS: