



CYFIRMA Research and Advisory Team has found VanHelsing Ransomware while monitoring various underground forums as part of our Threat Discovery Process.
Designed to target Windows systems, this ransomware employs advanced encryption techniques and appends a unique file extension to compromised files. Its stealthy evasion tactics and persistence mechanisms make detection and removal challenging. This highlights the need for proactive cybersecurity measures and a robust incident response strategy to safeguard data integrity and minimize breach risks.
Target Technologies: Windows
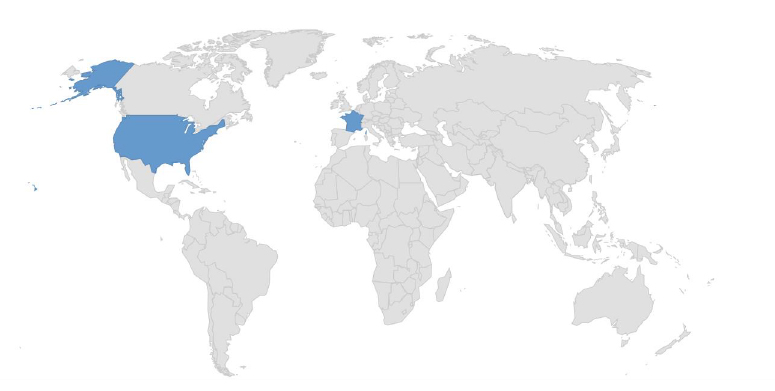
Target Geography: France, USA.
Target Industry: Government, Manufacturing, Pharma.
Encrypted file extension: .vanhelsing
Observed First: 2025-03-16
Threat actor Communication mode: Tor
Researchers at CYFIRMA have recently observed a ransomware strain identified as VanHelsing.
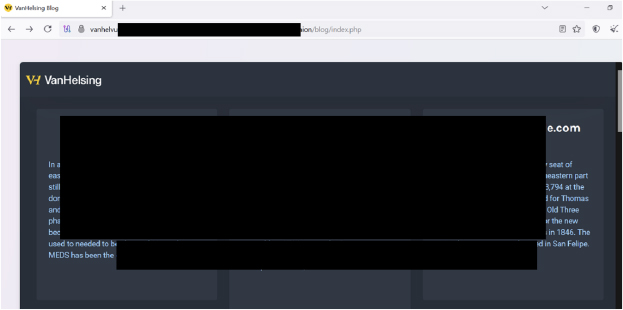
This new ransomware strain encrypts files and demands payment for decryption. It also employs double extortion tactics, threatening to leak stolen data to pressure victims into paying. Once executed, VanHelsing appends the “.vanhelsing” extension to encrypted files, modifies the desktop wallpaper, and drops a ransom note named “README.txt” on the victim’s system.
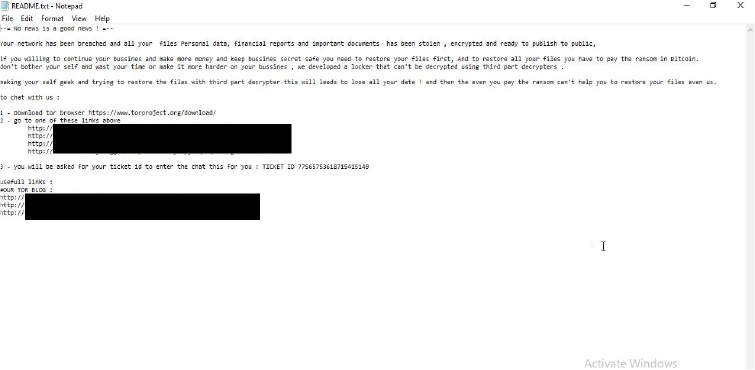
VanHelsing’s ransom note informs victims that their network has been compromised, with files encrypted and sensitive data—such as personal details, financial reports, and important documents – exfiltrated. To restore access, victims are instructed to pay an unspecified ransom in Bitcoin. The note also warns that refusal to pay will result in the leaked publication of stolen data. Additionally, it cautions against self-recovery attempts, as these may render the encrypted files permanently inaccessible.

TTPs Based on Mitre Att&ck
| Tactic | ID | Technique |
| Execution | T1047 | Windows Management Instrumentation |
| Execution | T1053 | Scheduled Task/Job |
| Execution | T1059 | Command and Scripting Interpreter |
| Execution | T1129 | Shared Modules |
| Persistence | T1053 | Scheduled Task/Job |
| Persistence | T1542.003 | Pre-OS Boot: Bootkit |
| Persistence | T1543.003 | Create or Modify System Process: Windows Service |
| Persistence | T1547.001 | Boot or Logon Autostart Execution: Registry Run Keys / Startup Folder |
| Persistence | T1574.002 | Hijack Execution Flow: DLL Side-Loading |
| Privilege Escalation | T1053 | Scheduled Task/Job |
| Privilege Escalation | T1055 | Process Injection |
| Privilege Escalation | T1543.003 | Create or Modify System Process: Windows Service |
| Privilege Escalation | T1547.001 | Boot or Logon Autostart Execution: Registry Run Keys / Startup Folder |
| Privilege Escalation | T1548 | Abuse Elevation Control Mechanism |
| Privilege Escalation | T1574.002 | Hijack Execution Flow: DLL Side-Loading |
| Defense Evasion | T1006 | Direct Volume Access |
| Defense Evasion | T1014 | Rootkit |
| Defense Evasion | T1027.002 | Obfuscated Files or Information: Software Packing |
| Defense Evasion | T1036 | Masquerading |
| Defense Evasion | T1055 | Process Injection |
| Defense Evasion | T1070 | Indicator Removal |
| Defense Evasion | T1112 | Modify Registry |
| Defense Evasion | T1202 | Indirect Command Execution |
| Defense Evasion | T1222 | File and Directory Permissions Modification |
| Defense Evasion | T1542.003 | Pre-OS Boot: Bootkit |
| Defense Evasion | T1548 | Abuse Elevation Control Mechanism |
| Defense Evasion | T1564.001 | Hide Artifacts: Hidden Files and Directories |
| Defense Evasion | T1564.003 | Hide Artifacts: Hidden Window |
| Defense Evasion | T1574.002 | Hijack Execution Flow: DLL Side-Loading |
| Credential Access | T1003 | OS Credential Dumping |
| Credential Access | T1552.001 | Unsecured Credentials: Credentials In Files |
| Discovery | T1012 | Query Registry |
| Discovery | T1057 | Process Discovery |
| Discovery | T1082 | System Information Discovery |
| Discovery | T1083 | File and Directory Discovery |
| Discovery | T1135 | Network Share Discovery |
| Discovery | T1518.001 | Software Discovery: Security Software Discovery |
| Collection | T1005 | Data from Local System |
| Collection | T1114 | Email Collection |
| Collection | T1213 | Data from Information Repositories |
| Command and Control | T1071 | Application Layer Protocol |
| Command and Control | T1090 | Proxy |
| Command and Control | T1105 | Ingress Tool Transfer |
| Impact | T1485 | Data Destruction |
| Impact | T1486 | Data Encrypted for Impact |
| Impact | T1490 | Inhibit System Recovery |
| Impact | T1496 | Resource Hijacking |
Indicators of Compromise
Kindly refer to the IOCs section to exercise controls on your security systems.
| SHA 256 | Remark |
| 86d812544f8e250f1b52a4372aaab87565928d364471d115d669a8cc7ec50e17 | Block |
STRATEGIC RECOMMENDATION
MANAGEMENT RECOMMENDATION
TACTICAL RECOMMENDATION